Introduction
Providing security to the users of a system is among the key concerns of an operating system manufacturer. On the Windows platform, it has been observed that the use of different file systems is one approach that has been used to provide additional security.
In the Windows Server 2003 platform, the use of the NTFS files system has been maintained owing to the security features that the system supports (Weber & Bahadur 2003). With the NTFS files system files and directories are maintained as securable objects thus allowing users to set permissions that limit access to these objects.
Some of the main functions handled by an operating systems include those associated with Authentication, Authorization and Accounting. (See Figure 1) On the Windows platform, AAA provides a means for the system to identify a user, grant access to specific resources and document what actions the user took and at what time they took these actions (Reeser, Kaplan & Wood 2003).
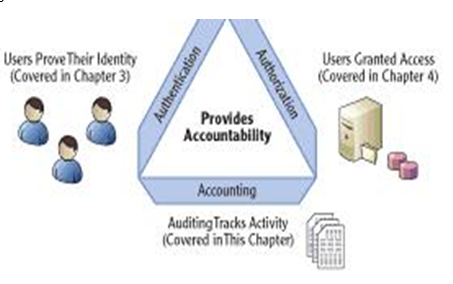
The majority of services associated with AAA on the Windows Server 2003 environment are offered by the Windows security model.
Under this security model authentication is carried out through the use of user account/password settings. Authorization is handled by discretionary access control lists managed by the system. The system caters for accounting needs using event logs and event auditing policies (Reeser, Kaplan & Wood 2003).To assist in the management of permissions when a user logs on to the system an access token is produced.
This token consists of pieces of information about the user’s account (Weber & Bahadur 2003). Through this means when a user attempts to access a file the system checks to see if the user has the security descriptor for that file.
In addition to monitoring the users of a system, the Windows Server 2003 platform allows the administrator of the system to audit activity on the system by observing the system logs. Each access attempt is logged and stored in a log file that can be viewed by the system administrators or other users with appropriate permissions (Weber & Bahadur 2003).
However, no system provides perfect security and for that reason, there are ways to go around the operating system in Windows Server 2003. The purpose of this report is to briefly discuss some of the issues with authentication, authorization and auditing (AAA) on the Windows Server 2003 platform.
Windows Server 2003 Authentication Mechanism
The Windows Server 2003 platform just like the Windows 2000 was constructed to give a wide range of control over access to its resources. As a matter of fact Windows Server 2003 is designed such that it checks access permissions for every request before granting access to system resources (Stewart, McCann and Melendez 2006).
The Windows Server 2003professional system can provide local security when used as a standalone system, in a workgroup or participate in domain security managed by a Windows server (Stewart, McCann and Melendez 2006).
Before a user is granted access to any system resources on the platform they are required to logon providing a valid user ID and password (Stewart, McCann and Melendez 2006). After successfully logon the user is granted an access token by the system. This access token includes information about the user’s identity, any permission associated with the user account and a complete list of the groups to which the user belongs.
A string of bits represents the token that is attached to every process that the user initializes until the user logs off the system (Stewart, McCann and Melendez 2006). This signifies that each time the user runs a program enters a system command or accesses some system resource a copy of that token accompanies that request.
On each occasion that a user attempts to access a resource the system automatically compares the token with a list of permissions associated with the resource. This list of permissions is referred to as the access control list (ACL) (Stewart, McCann and Melendez 2006). This list is one of the more important attributes associated with the Windows Server 2003 resources.
It guarantees that whenever a request is made the ACL and token are carefully compared and access is only granted when a match is found. The recognized permission settings in the Windows Server 2003 platform are Allow and Deny. Allow enables the user or group access to a service whereas Deny disables the same (Stewart, McCann and Melendez 2006).
Windows domain security is built on Active Directory. This is a centralized database of configuration and communication information maintained by domain controllers on a Windows network (Stewart, McCann and Melendez 2006).
The Active Directory is used to support everything from authentication of users to accessing shared resources on the network. However, when used as a standalone system or part of a domain Windows Server 2003 does not use Active Directory but uses the registry and internal security systems to control access to resources.
The Windows Server 2003 logon is compulsory to allow access to resources on the system. There are two types of logons available on Windows Server 2003 namely the classic and Windows Welcome (Stewart, McCann and Melendez 2006). When a Windows Server 2003 system is a member of a domain the classic system can be used.
However, when the system is a standalone or member of a workgroup either classic or welcome logon can be used (Stewart, McCann and Melendez 2006). The logon on process is typically made up of two components namely identification and authentication. The identification part requires that the user provide a valid account name and in cases where a domain is involved a valid account name.
Authentication requires that a user provide a valid means of verifying their identity to the system (Stewart, McCann and Melendez 2006). Possession of the proper password for an account is considered to be appropriate authentication.
The Windows Server 2003 system also supports the use of third-party authentication procedures such as the use of biometric procedures (Stewart, McCann and Melendez 2006). These procedures include the use of systems that check fingerprints, retinal scans and the use of smart cards to verify identity of the user.
Upon a successful login to the system, the user is provide a token which includes the user Security identity (SID) and SIDs for each of the groups the user belongs. The access token thus includes the unique SID associated with the account, a list of groups to which the user belongs and a list of rights and privileges associated with that user account (Stewart, McCann and Melendez 2006) (See Figure 2).
Access to system resources is granted only after the user receives an access token. Each access token is created for one-time use and is discarded after the user logs off the system (Stewart, McCann and Melendez 2006). Once constructed the access token is attached by the system to the user’s shell process. This shell process defines the environment in which the user executes programs or spawns other processes.
In the Windows Server 2003 system resources are controlled by the system at an object level. Each object in the system has a unique access control list that defines users and groups that have permission to access the specific resource (Stewart, McCann and Melendez 2006). In this regard therefore everything in the Windows Server 2003 environment is an object.
This includes all files, folders, printers, processes, users, requests, etc. An individual object is identified by its type, which will define the permitted range of contents and operations which may be performed on the object (Stewart, McCann and Melendez 2006).
All objects in the Windows Server 2003 system are logically divided into three sections namely, a type identifier, a list functions or services and a list of attributes that may or may not have associated items (Stewart, McCann and Melendez 2006).
The object identifier is used to describe the type of entity associated with the object. A service is used to define the procedure to follow when manipulating an object. Whereas, the attributes are its named characteristics such as the file name or whether the file is hidden or read-only (Stewart, McCann and Melendez 2006).
Windows Server 2003 Authorization Mechanisms
The Windows Server 2003 operating system is built with a number of features to help protect selected files and applications from unauthorized use (Russel & Crawford 2009). The system offers its users a variety of features from protection and third-party software that can allow the user manage or configure the system.
These features assist administrators by provision of powerful and flexible structures for controlling the access to resources and the network.
Every user within an organization serves a specific role and purpose. For the users to successfully perform their tasks within an organization the system needs to allow access to required resources (Russel & Crawford 2009). The employees who work in the accounting departments are not allowed to make changes but only make use of different files and documents. It is right, as all the control should be done by the directors of the company.
There is a special department that is in the control of those specific documents used by the employees. The personnel department controls the access that may be given to corresponding specific people that are allowed to look through and to make use of the document.
The Windows Server 2003 system performs its authorization function by adhering to several key underlying principles. As mentioned earlier the Windows Server 2003 system considers all entities as objects. A security principal is one of these objects that the system identifies with. “Any entity that can be authenticated by the Windows Server 2003 system is considered a security principal” (Russel & Crawford 2009).
Each security principal has an account and all local accounts are managed by the local Security Accounts Manager (SAM). If an account is in another Windows domain it is managed by Active Directory (Russel & Crawford 2009).
Another important concept that is used in authorization mechanisms is that of the security identifier (SID). This is a unique value monitored and stored on the system for identification of user, groups, etc., within an organization (Russel & Crawford 2009).
Upon creation of an account, a unique SID is issued by the system. Windows Server 2003 uses the SID to manage access control rather than the name of the object within the system.
Another concept that is used in management of authorization is that of the security context. This refers to information that pertains to a particular user on the system and their capabilities (Russel & Crawford 2009). This requires that the system assess all users in a single department or location to maintain similar security permissions across the entire group.
To perform this task the Windows Server 2003 system makes use of a security descriptor. This is “a data structure containing information associated with the object to be secured” (Russel & Crawford 2009).
The security descriptor is used to identify an object owner using the SID. In case something has been already done for the issue, “the security descriptor contains discretionary access control list (DACL)” (Russel & Crawford 2009). This DACL will contain a list of users and groups that are allowed or denied access to the object in question (Russel & Crawford 2009).
In case a specific objects as already been created for use, the corresponding documents of the control should be created by the company representatives such as security descriptors. This SACL controls how the sub-system will audit access attempts to the object (Russel & Crawford 2009).
As mentioned earlier authorization makes use of an Access Control List (ACL), that should be ordered in advance and contains the needed information about people who are allowed to make use of the documents and its abilities in this or that process (Russel & Crawford 2009).
“Each access control entry in the list identifies a security principal and specifies a set of rights denied, audited or allowed for that security principal” (Russel & Crawford 2009). In addition to the above-mentioned approaches the system also offers security settings which are applicable to individual computers.
These settings can be locally configured through the use of the Local Security Policy Administration tool (Russel & Crawford 2009). In addition to that the security policy can be configured using the Microsoft Management Console. “If the computer is a member of an active directory domain the analysis snap-in tool can be used through the Security Settings Extension to Group Policy” (Russel & Crawford 2009).
Other concepts that are used by Windows Server 2003 systems in managing authorization include discretionary access to securable objects. This concept suggests that the owner of an object has overall control over who uses the object and in what way (Russel & Crawford 2009).
Different people may be given various types of access by the owners of the companies. of users. This suggests the owner of an object is allowed to allocate Read and Write permissions to specific categories while denying Write permissions to other categories of users.
Detailed Description of Authentication, Authorization and Auditing on Windows
Another concept that is used to control authorization in the Windows Server 2003 system is that of inheritance of permissions. This can be realized by “allowing objects create a container inherit properties of the container” (Russel & Crawford 2009). For example, the NTFS file system allows subfolders and files to inherit properties of their parent containers.
Another principle used in the management of authorization is that of rights and permissions. “Access control basically involves the configuration of rights and permissions to objects on the local computer or network and the potential users of those objects” (Russel & Crawford 2009). In this respect, a right is an authorization to perform an action. Rights are granted by the administrator and can also be withdrawn.
The system administrator views rights from two perspectives namely, logon rights and privileges. Permission is the authorization to perform an action on an object (Russel & Crawford 2009). The system reserves the right to grant permissions to the owners of an object.
An example of permission is the liberty to perform an operation such as opening a file. It should not be forgotten that the permission may be denied sooner or later in case of rule violation. For example, a user permits members of a group Read and Write access to a file. This suggests that if you are not a member of the group then permission has been denied.
In addition to this the Windows 2003 system allows for the provision to deny permission explicitly (Russel & Crawford 2009). Russel & Crawford say that “the same object owner is allowed to deny a specific member of the group Read and Write access to the file” (2009).
To achieve the goal of authorization the Windows Server 2003 system maintains that all operations must be performed within the context of a user. Upon accessing the system crucial information about the user is recorded in a unique access token created by the system (Russel & Crawford 2009).
Each application that is launched on the system operates as a process that may contain several threads being executed. Before any thread is run it must identify itself to the operating system by providing the access token information. Once it has been identified access is granted within stated parameters.
Windows Server 2003 Auditing Mechanisms
As with most operating systems, the Windows Server 2003 systems provide administrators with an easy way to track activities on the system (Gibson 2011). The system allows one to track user access files, shut down systems, create or modify accounts and much more.
Although the system monitors several events by default it is crucial that one knows what is required within the organization (See Figure 3). It is important to know how to enable auditing of different events to meet organizational needs (Gibson 2011).
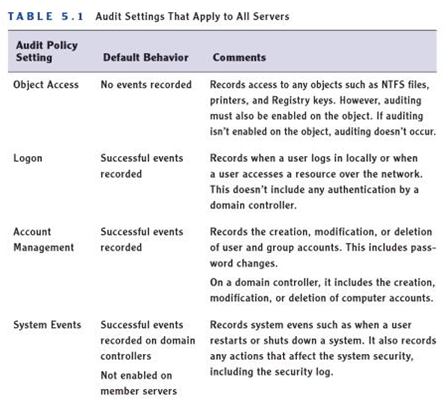
The Microsoft Windows Server 2003 system records all auditable events in the event log and these can be viewed by using the event viewer. In addition to this, there is the Microsoft Baseline Security Analyzer (MBSA) which provides a different type of auditing.
This feature allows a user or administrator to audit computers on a network for a wide range of vulnerabilities (Gibson 2011). This is a free tool that can be downloaded and installed on a single machine on the network.
The MBSA can then be used to perform vulnerability scans on any other Windows systems running on the network and perform audits on them for compliance. To achieve this software compares their security status against known security vulnerabilities.
Auditing within a Windows environment is relatively easy to implement based on the fact that it is possible to enable an audit policy for an entire domain using group policy or for a server using Local Security Policy (Gibson 2011).
The Windows Server 2003 system allows the administrator to enable auditing to manage both success and failure events. For example, if you enable Full auditing access for a folder the system would create an entry in the security log that includes user and file-specific details (Gibson 2011). If someone attempted to delete the file but lacked the necessary permissions to do so a failure event would be created in the security log.
This log would also contain the necessary file and user information associated with the event. Failed events are monitored as they provide a good point to begin identification of potentially malicious activity (Gibson 2011).
The Windows Server 2003 system makes it relatively easy to enable security settings for auditing. However, the main difficulty lies in identifying what requires auditing before enabling it using the settings within the system (Gibson 2011).
It should be noted that if one enabled everything the log would be filled with many unnecessary details. These details and processes will consume crucial system resources and make the process of identifying important events even more difficult.
The audit policy includes two account settings that both deal with logging on to the system. The first one is Account Logon which creates an event any time a user or computer is authenticated with an Active Directory account (Gibson 2011). The other option is the Logon setting which creates an event each time a user logs on locally (Gibson 2011).
Redirect Flow of Running Process
These attacks also referred to as redirection attacks can be described as tier-one attacks due to the fact that there is a direct link between the attacker and the victim (Zou, Dai & Pan 2008). This attack exposes the attacker to discovery which in many cases they desperately attempt to avoid. One method to avoid this problem is to add a layer between the attacker and the user.
This can be accomplished by taking advantage of TCP/IP characteristics. In this approach, the attacker will craft packets that can be used to turn intermediate systems into attack-launching platforms (Zou, Dai & Pan 2008). This process makes the tracing of an attacker difficult.
These attacks can be achieved by ICMP redirects. The Internet Control Message Protocol (ICMP) is used by the system to provide diagnostic messages concerning packet delivery. Among the common messages of this type are the echo request/reply messages which focus on the ability of one system to communicate with another (Zou, Dai & Pan 2008).
Another type is the ICMP redirect which when accepted modifies a systems routing table allowing messages to be sent via a shorter route. These attacks work by altering the path that a victim host should use to reach its default gateway to an invalid path (Zou, Dai & Pan 2008). Thus the victim is unable to communicate with all systems except those present on the local subnet.
Another attack that falls under this category is the Smurf attack. It is reported that every TCP/IP subnet has a special address known as a broadcast address. Packets sent to this address are processed by all the systems on that subnet (Zou, Dai & Pan 2008). One of the common uses for this address is the Address Resolution Protocol (ARP). This is a concept used to map IP addresses to MAC ones within the subnet.
When launching a smurf attack, the attacker selects a random network and Echo-Request ICMP (ping) packet to that subnet’s broadcast address (Zou, Dai & Pan 2008). Normally each system on the network will send a response to this message but the attacker also spoofs the source address to be that of the victim. In so doing, each system sends its ICMP Echo-reply packet to the attacker (Zou, Dai & Pan 2008).
There are two advantages of such an attack. First is the fact that the actual packets the attacker sends are not received by the victim, making it more difficult to track the origin. Second is that the network also serves as an attack amplifier due to the fact that a single ICMP echo request may result in hundreds of reply packets directed at the victim (Zou, Dai & Pan 2008).
Another type of attack is known as the Chargen attack. The charge is a special service bound to port 19 that typically is used to test network capacity (Zou, Dai & Pan 2008). When a connection is made to this port it responds with a string of characters. When launching this kind of attack, the attacker must first locate the system’s active charge service.
Once located the attacker sends a UDP echo request to port 19 after spoofing the source IP address as that of the victim. This results in the intermediate host sending a string of characters to the Echo service port of the victim (Zou, Dai & Pan 2008). As protocol dictates the victim will respond by sending that string in response to the received message.
The end result is an endless loop where the process is repeated until the victim’s system fails. In many cases, one system is not enough to guarantee failure thus a number of intermediate systems may be used as described in the Smurf attack.
Conclusion
In the course of the report, the various mechanisms used to provide AAA services on the platform have been briefly discussed. It has been observed that authentication is carried out through the use of user account/password settings. Authorization is handled by discretionary access control lists managed by the system. The system caters for accounting needs using event logs and event auditing policies (Reeser, Kaplan & Wood 2003).
It has also been noted that due to the system used for authentication, the system can easily be exposed to attacks by unwanted outsiders.
This is because based on the mechanism for authentication, once a user is authenticated the system hands over control of specific resources to them (Stewart, McCann and Melendez 2006). Unfortunately in a networked environment, this is risky as it allows for man-in-the-middle attacks that could cripple the entire system.
However, this should not be taken to mean the system is not worth further consideration as there is no system that guarantees perfect security. The above point just goes a step further to identify potential weak points in the system. The system has also been applauded for the convenience it offers to users through the use of workgroups (Stanek & Bhardwaj 2007).
As the number of connected computers increases so too does the number of workgroups. Workgroups are small groupings of computers running the operating system. The operating system allows the users to form small groups and share resources without the need for intermediary servers and administrators.
References
Gibson, D. (2011). Microsoft Windows Security Essentials. Indiana: Wiley Publishing Inc.
Reeser, T., Kaplan, S., & Wood, A. (2003). Citrix MetaFrame Access suite for Windows Server 2003: the official guide. California: McGraw-Hill/Osborne.
Russel, C., & Crawford, S. (2009). Microsoft Windows XP Professional Resource Kit. USA: Microsoft Press Books.
Stanek, W. R., & Bhardwaj, P. K. (2007). MCSA on Windows Server 2003 Core exams in a Nutshell. California) O’Reilly Media Inc.
Stewart, J. M., McCann, B., & Melendez, A. (2006). MCSE Guide to Microsoft Windows XP Professional. Boston: Course Technology.
Weber, C., & Bahadur, G. (2003). Windows XP Professional Security. USA: McGraw-Hill Inc.
Zou, X., Dai, Y. S., & Pan, Y. (2008). Trust and security in collaborative computing. Singapore: World Scientific Publishing Co. Pte. Ltd.