Introduction
A local area network refers to a connection of computers which are located close to each other. The region covered by this network may include a building, a school or even the network at home (Kyriazoglou, 2010). The concept of the local area network was developed after that of the wide area network and its main purpose initially was to ensure that the available resources are shared.
These resources include printers and other hardware devices. As the technology evolved, the functions of the local area networks increased and included communication between different parts of the network (Roger, 2009). Techniques such as video- conferencing and media streaming were incorporated. The sending and receiving of mails was also introduced.
The connection in these networks is made possible by the use of interconnecting devices. The devices used to serve this purpose are the hubs, switches and routers.
Hubs are used in the network to broadcast the data to different parts of the network where the data is received by the computers at those locations. On the other hand, routers are used to send data to specific points of the network and may be used to interconnect several local area networks.
The local area network suffers different types of security threats while operating. These threats may be internal or external to the network. The internal threats are those that affect the communication between different devices on the network and may affect the flow of information from one point to the other.
They may include activities such as interception of data while it is being transmitted, unauthorized access or modification of data on the network from a remote point and blocking part or all the traffic flowing through the network (Bishop, 2010). On the other hand external threats may include activities such as vandalism or theft of the network equipment. All these activities results in the disruption in the operation of the network
Therefore, control strategies have to be developed to be able to counter these effects. This is of particular importance for corporate who may have sensitive information that they may want to keep private from their competitors. The control strategies also ensure that the functions of the organization run smoothly at all times and does not suffer interruptions. The strategies may be categorized into three broad categories.
These are preventive control, detective control and corrective control (Pfleeger & Pfleeger, 2010). Preventive control is where the risk that the network may be subjected to is determined and structures are put in place to ensure that the threat does not happen. This may be achieved by the use of passwords to prevent unauthorized access to the system as one of the options.
Detective control on the other hand refers to a situation where the network is analyzed and the threat is identified. This control mechanism is mainly performed by the use of auditing software which detects the threats within the system (Pfleeger & Pfleeger, 2010). Corrective control is where the problem in the network is identified and removed to ensure that the system runs as it was intended.
The threats that may be corrected using these control strategy may include circumstances such as when the traffic has been interrupted in the network (Pfleeger & Pfleeger, 2010). The cause of the interruption in this case is identified and corrective changes are made to ensure that the system runs as it was intended.
These security threats may be brought about by several factors which may include the size of the network, ignorance or misunderstanding between the personnel running the network, the network complexity or even a problem in how the network has been programmed (Bragg, Rhodes, & Strassberg, 2010). The security controls that may be employed in the corporate LAN environments are discussed in the next section.
Security controls
This section focuses on the controls that may be employed to prevent, detect or correct the threats that may affect the corporate LAN environment. Segmentation of the network is one of the control strategies that may be employed to prevent the threats affecting the running of the entire network. This is where the network resources are not placed at one point in the network (Hruska & Keith, 2011).
They are distributed at different points of the network to ensure that incase there is an attack to one point of the network, its functionality will not be affected as a whole. This means that the network will still continues performing its tasks as corrective measures are being undertaken to rectify the problem at the affected part of the network.
Segmentation therefore reduces the number of threats and also limits the damage that would otherwise have been caused to the network. This technique allows multiple segments which each performing a specific task (Hruska & Keith, 2011).
The diagram below may be used to illustrate segmentation as a control strategy. The diagram clearly shows that the tasks have been divided to different parts of the network. One part deals with the networks applications while the other deals with the orders/inventory.
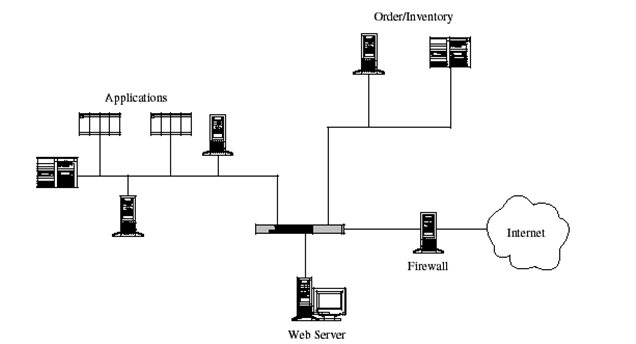
Another control that may be used is the preventive control. This is by the use of frameworks such as network redundancy, prevention of theft and prevention of virus attacks (Stallings, 2009). The use of network redundancy is one of the control strategies that serve to help in case of network failure. This is where the network functions are performed at more than one node.
For example in the figure above, the network has only one web server. Incase this server is affected then the entire network will be brought to a standstill. A better way in which the network could have been configured is using more than one server (Cook & Neil, 2009). The two servers will be configured in such a way that each runs independently but is programmed to check periodically if the other server is functioning.
Incase of failure of one of the servers, the other one performs the tasks that were being done by the other one. This is helpful since it will ensure that the network is online at all times.
Prevention of theft can be achieved by ensuring that appropriate security measures are put in place to ensure that the employees are checked when they leave the premises to ensure that they do not leave with components that are required for the running of the network.
Installation of alarm mechanisms within the network such that the components of the network are frequently checked for their availability is also another way to curb theft. Incase the components are not attached to the nodes where they are supposed to be, an alarm sounds. This may prove helpful in ensuring that the working of the network is not compromised by theft of the network components.
Virus attacks should also be controlled. Viruses attach themselves or are attached to files and when these files are opened they spread to other documents in the computer. These attacks affect the functionality of the network by slowing it down or making changes to important information and therefore should be prevented.
The use of filtering software and antivirus will prove helpful in this case (Jyoti, 2011). The emails sent through the network are first scanned for viruses before being opened to ensure that the host computer where the email attachment is being opened from is not affected by the virus.
Data encryption is also another control measure that will ensure that the data is only accessed by the intended party. This means that when the data is received it will be authentic. Encryption converts the data into a format that cannot be read and interpreted unless it is decrypted by an appropriate key. Once the data is received, the recipient therefore requires an encryption key in order to be able to view the data.
Encryption may be divided into link encryption and end-to-end encryption (Bishop, 2010). Link encryption is where the encryption is done at two host computers. It is done just before the information to be transmitted is placed on the transmission media. This means that the encryption is done at the layer 1 or 2 in the OSI model (Bishop, 2010).
This data is transmitted in the encrypted form (plain text). The decryption is done at the receiving computer just before the computer receives the data. This means that when the computer receives the data it will already be decrypted and can therefore be interpreted. The diagram below illustrates how link encryption is performed.
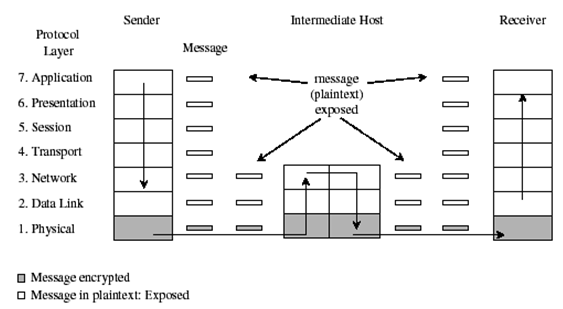
End-to-end encryption on the other hand is where encryption is between two applications. Theses applications may be installed in the host computers. The decryption of the data is done by software once the data has been received at the receiver end.
Therefore encryption ensures content integrity in the data. This is because the data cannot be altered easily without the encryption key ensuring that the data is received in the form in which it was sent.
Strong authentication is another security control that may be employed. This is where security levels are developed and access to certain information on the network is limited to certain users of the network only. Authentication is however not easy to achieve in a network. This is because of the possibility of eavesdropping within the network.
The authentication also needs to be done at both ends of the network where communication is taking place. The use of passwords for authentication in a network may also be problematic. This problem however may be solved by the use of a password token. This device is used to generate passwords that are used for authentication.
The advantage of this system is that each user in the network is given the token. When one wants to log in to the system, the password token generates the password for authentication and the user enters this value to the computer interface. This means that the password is different each time it is used. This technique is also referred to a one-time password use.
Firewalls may also be used to do the screening of data before it is received by a network. There are two types of firewalls that can be employed. These are the static and the dynamic firewall. The static firewall may be default permit or a default deny.
When under default permit, the firewall allows all traffic except that which has been blocked by the administrator while when the firewall is under default deny, it denies all the traffic except that which the administrator has configured to be allowed to pass through the firewall (Donald, 2010).
This means that the firewall performs one task at a given time. The dynamic firewalls on the other hand allow the permit and deny operations to run concurrently.
The firewall administrator has the task of setting the rules that determine the data and information that will be allowed to pass through the firewall and that which will be denied access to the network. The firewall therefore performs tasks such as limiting the flow of packets between networks, allowing authorization testing by giving access and also acting as a control point when the network an external connection.
Proxies may also be used in the network to achieve the control of the traffic within the network. The control of traffic within any network is very important as hackers may use it as a way to affect how the network operates. For example if a hacker gets into the network, he/she may sabotage the functionality of components in the network.
For the case of a printer, he/she may send a large amount of data to the printer within a short period of time. This affects the functionality of the printer as it can be able to process a particular number of instructions at one time.
Another security control that can be employed is the use of honeypots in the network. This is a computer system that has computer devices and data (Jyoti, 2011). It is used to make the data visible to the attacker and attract hin/her. Once the attacker gains access to this data, you are able to monitor all the actions that he/she is performing.
The monitoring is done carefully to ensure that the attacker does not notice that he/she is being monitored. This system does not have a firewall to enable the attacker to be able o gain access to the data. The honeypot is important as it will enable the administrator of the network to learn about new attacks that the attacker may be intending to perform.
This knowledge gives the administrator an upper hand as it ensures that he/she is able to prevent such an attack before it happens to the actual system.
The honey pot also ensures that the attacker is diverted from the actual system and therefore the harm that may otherwise have been subjected to the system is prevented from occurring. It therefore allows the administrator to stop the attacker while at the same time being able to protect the system.
Conclusion
The explanations above show that any network and in particular the corporate local area network may be subjected to different types of threats. To ensure effective and efficient running of these networks, these threat must be identified. Incase the system is already affected; measures should be put in place to eliminate the threats.
Preventive mechanisms should also be employed to ensure that the system is not vulnerable to these threats. The implementation of these security controls will ensure the smooth running of the system. If the system is used to transmit sensitive data, the integrity of this data will be upheld if controls such as encryption of the information are performed.
References
Bishop, M. (2010). Computer Security. Boston: Pearson.
Bragg, R., Rhodes, M., & Strassberg, K. (2010). Network Security. New York: McGraw Hill.
Cook, B., & Neil, W. (2009). Computer Peripherals. London: Edward Arnold.
Donald, E. K. (2010). Art of Computer Programming. Salt Lake: Addison-Wesley.
Hruska, J., & Keith, J. (2011). Computer Security Reference Book. Ohio: Butterworth-Heinmann.
Jyoti, S. (2011). Computer Peripherals and Interfacing. New Delhi: Laxmi Publications.
Kyriazoglou, J. (2010). It Strategic and Operational Controls. London: IT Governance Publishing.
Pfleeger, C. P., & Pfleeger, S. L. (2010). Security in Computing. Upper Saddle River: Prentice-Hall.
Roger, T. (2009). Schaum’s Outline of Computer Networking. New York: McGraw-Hill.
Stallings, W. (2009). Network Security Essentials. Upper Saddle River: Prentice-Hall.