Introduction and Agenda
- Online environment has been providing the platform for casual interactions as well as economic activities for quite a while;
- However, the lack of physical evidence of these activities makes the process of transferring legal regulations to the Internet complicated;
- Particularly, the privacy issue needs to be addressed due to numerous opportunities for data copying and abusing the rights of owners;
- An analysis of the current regulations will shed some light on possible measures to be taken in the future (Dinev, Xu, Smith, & Hart, 2013).

Video Privacy Protection Act, 1988
- Passed in 1988;
- Signed by Ronald Reagan;
- Prohibits “wrongful disclosure of video tape rental or sale records” (Legal Information Institute, 2016, par. 1);
- Aimed at keeping clients’ personal data safe.
While conveying an admittedly positive message, the regulation serves as the device for customers’ personal data storing by organizations such as Netflix and Hulu. By carrying out unclean practices, the organizations expose their users to a serious threat (Nye, 2012).

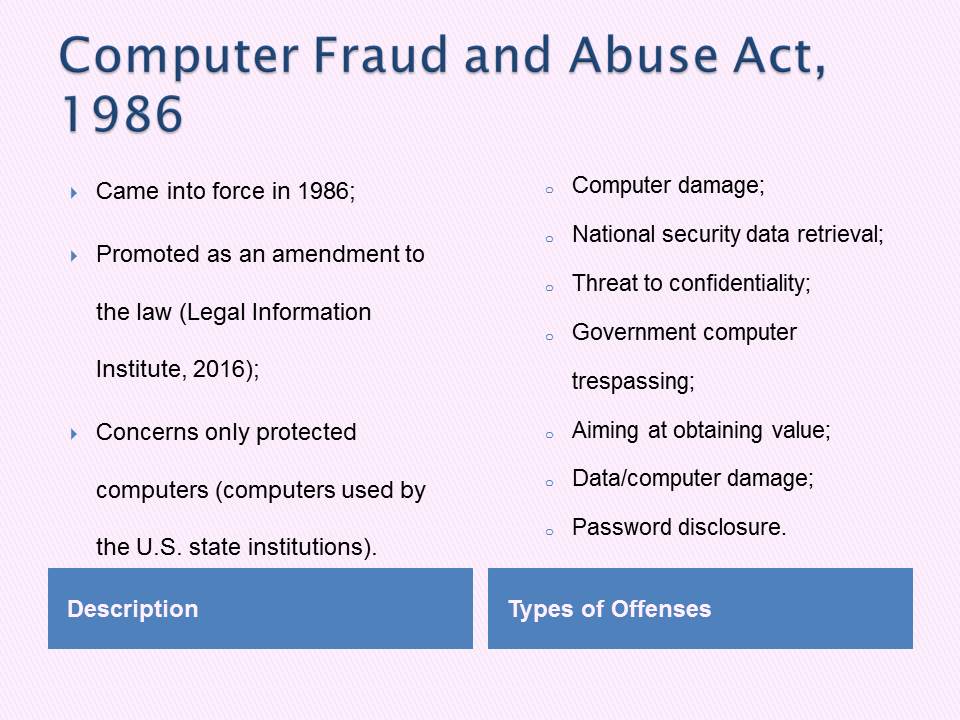
Computer Fraud and Abuse Act, 1986
Description
- Came into force in 1986;
- Promoted as an amendment to the law (Legal Information Institute, 2016);
- Concerns only protected computers (computers used by the U.S. state institutions).
Types of Offenses
- Computer damage;
- National security data retrieval;
- Threat to confidentiality;
- Government computer trespassing;
- Aiming at obtaining value;
- Data/computer damage;
- Password disclosure.
The concept provides extensive support for governmental facilities, yet offers little to no protection for average users.
Electronic Communications Privacy Act, 1986
- Adopted by the U.S. Congress in 1986;
- Initially aimed at preventing the instances of wiretapping on telephone calls;
- (With the increase in the number of Internet users) extended to electronic data transfer;
- Is fairly dated and, therefore, lacks understanding on the current processes of data acquisition, transfer, and processing;
- Promotes surveillance as the means of reducing crime rates.
The Electronic Communications Privacy Act, though having a rather sensible premise, has been viewed as quite controversial over the past few years due to poor knowledge of the contemporary information management processes (Sklansky, 2015).

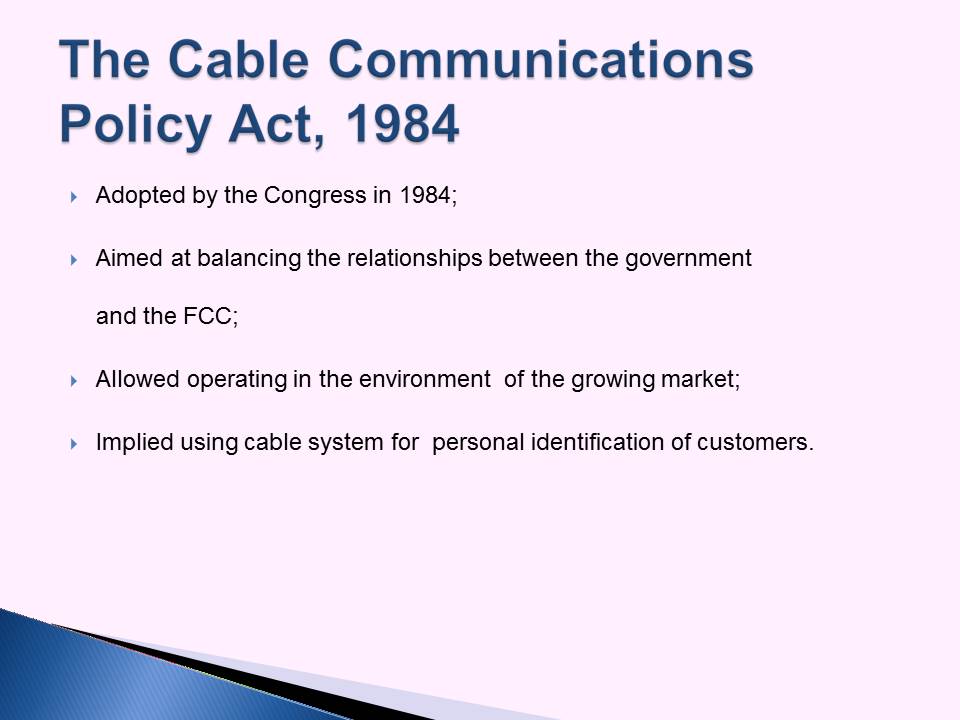
The Cable Communications Policy Act, 1984
- Adopted by the Congress in 1984;
- Aimed at balancing the relationships between the government
and the FCC; - Allowed operating in the environment of the growing market;
- Implied using cable system for personal identification of customers.
Designed to make sure that the needs of the key stakeholders (i.e., cable companies, the government, and the public) are met and that the rights of the parties are maintained, the legislation served as the foundation for enhancing the data management process (Meyerson, 1985).
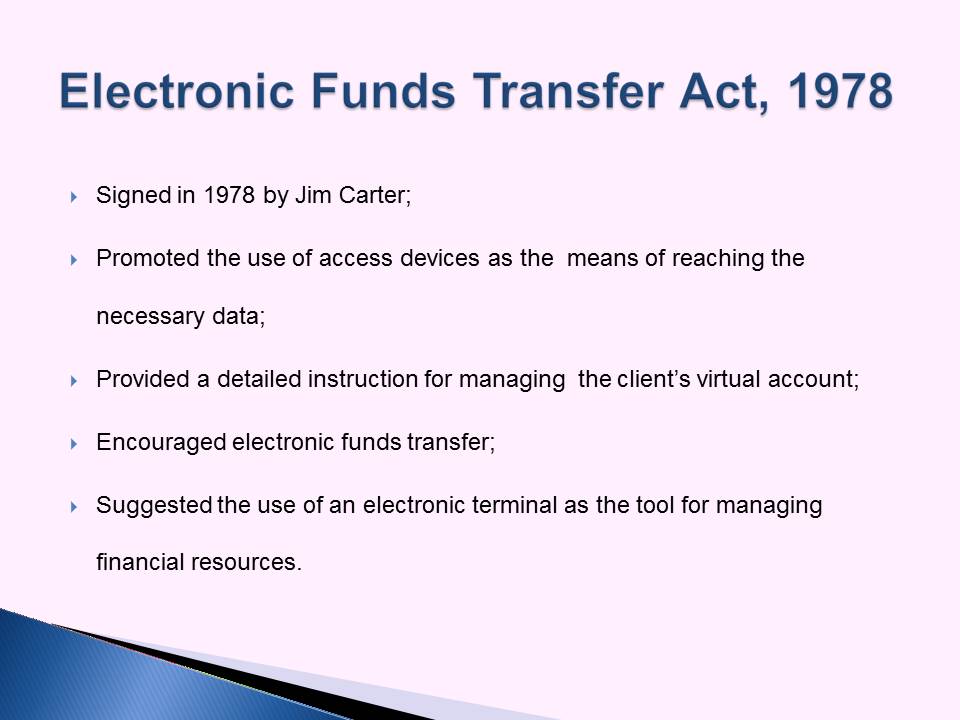
Electronic Funds Transfer Act, 1978
- Signed in 1978 by Jim Carter;
- Promoted the use of access devices as the means of reaching the necessary data;
- Provided a detailed instruction for managing the client’s virtual account;
- Encouraged electronic funds transfer;
- Suggested the use of an electronic terminal as the tool for managing financial resources.
The regulation can be viewed as the prerequisite for the development of the current online funds transfer services.
Family Educational Rights and Privacy Act, 1974
- Adopted in 1974;
- Guards the personal and education-related records of American students;
- Grants parents access to their children’s education-related information;
- Contains controversy regarding concealing the data that is not related to education;
- Fails to identify medical records as the type of personal information.
The obvious controversy of the legislation makes it necessary to reconsider its concept of personal data.

Fair Credit Reporting Act, 1970
- Adopted in 1970;
- Allows managing the credit information of citizens;
- Promotes fairness in personal information usage;
- Permits maintaining privacy;
- Coordinates the use of private information by credit reporting agencies (Hoofnagel, 2013).
The legislation can be viewed as the foundation for the existence of the consumer protection system.

Digital Millennium Copyright Act 1998
- Incorporates two 1996 treatises;
- Focuses on restricting online piracy and illegal use of copyrighted content;
- Exempts intermediaries from any liability;
- Prevents from making computer software copies;
- Focuses on the study of opportunities for distant education online (DMCA: The Digital Millennium Copyright Act, 2016).
The act (DMCA) focuses on the prevention of copyright infringement in the virtual environment. Unfortunately, the act is still imperfect and, therefore, allows for the abuse of users’ rights by monopolies such as YouTube (Tamburro, 2016).

Conclusion
- Despite numerous regulations being introduced to the Internet environment, users are still exposed to numerous threats;
- Privacy, identity, and personal and financial data of the users remain the subjects of a major threat;
- The existing rules not only fail to protect users, but may also be used to abuse their rights;
- Carrying out an awareness campaign should be viewed as the solution;
- Laws must be aimed at reducing the threat, not limiting users’ opportunities.
Although the present-day regulations can be deemed as fairly sensible, most of them are quite dated. Therefore, it is imperative to reconsider some of the principles of managing data in the context of the Internet environment. As soon as the corresponding tools are designed, a rapid improvement in the quality of customer protection and a drop in the number of biases can be expected.

Reference List
Dinev, T., Xu, H., Smith, J. H., & Hart, P. (2013). Information privacy and correlates: an empirical attempt to bridge and distinguish privacy-related concepts. European Journal of Information Systems, 22(3), 295-316.
DMCA: The Digital Millennium Copyright Act. (2016). Web.
Eastton, C., & Taylor, J. (2011). Computer crime, investigation, and the law. Boston, MA: Course Technology, Cengage Learning.
Feder, J. (2013). The Family Educational Rights and Privacy Act (FERPA): A legal overview. Web.
Hoofnagel, C. J. (2013). How the Fair Credit Reporting Act regulates big data. Web.
Legal Information Institute. (2016). 18 U.S. Code § 2710 – Wrongful disclosure of video tape rental or sale records. Web.
Meyerson, M. (1985). The Cable Communications Policy Act of 1984: A balancing act on the coaxial wires. Georgia Law Review, 19(3), 543-622.
Nye, J. (2012). Netflix customers’ ENTIRE movie rental history to be shared with Facebook… including all your guilty pleasures. Mail Online. Web.
Sklansky, D. A. (2015). Two more ways not to think about privacy and the Fourth Amendment. The University of Chicago Law Review, 82(1), 223-242.
Tamburro, P. (2016, February 27). YouTube’s CEO says the company is “listening” to its critics. Crave. Web.
Whitman, M. E., & Mattord, H. (2011). Reading & cases in information security: Law & ethics. Boston, MA: Course Technology, Cengage Learning.