Definition
Electronic commerce refers to an electronic mediated business or any business conducted using electronic as the media, it involves buying and selling of products or services using electronic systems such as the internet and other computer networks. Most companies have been forced by the digital economy to embrace electronic commerce due to the shift of value creation for consumers from physical goods to an economy that favor service, information and intelligence as the source of value.
Electronic commerce is categorized into four parts depending on parties involved in the transaction:
- Business to Business which refers to transaction between organizations and it includes purchasing, procurement, supplier management, services and support.
- Business to Customer refers to exchange between business and a consumer, this type is gaining popularity due to its convenience, an example is the Amazon.com.
- Consumer to Consumer refers to exchange of transactions between and among consumers.
- Consumer to business: this happens when consumers come together and present themselves as buyers.
Electronic commerce is said to be widely embraced by the young generation due to increased exposure to internet and they are using the technology as a new marketing and sales channel, a fact attributed to techno-economic paradigm (Freeman & Soete, 1994).
Electronic commerce involves a series of steps before a transaction is fully executed, these series of steps is what is referred to as electronic commerce cycle. The cycle may vary from one company to another but mostly it involves the following steps:
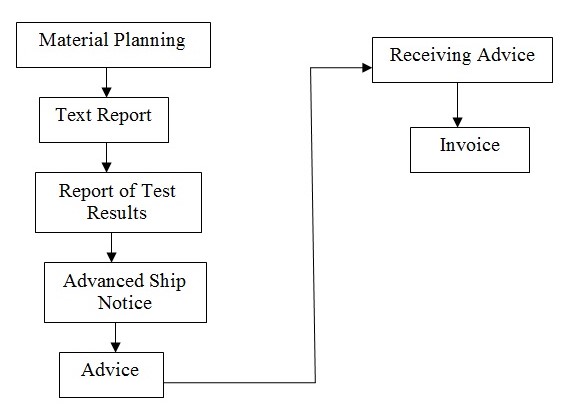
A flow Chart Showing Various Steps Involved in E – Commerce.
Material Planning: this is analogous to physical walk in by a customer to place orders over the counter, the company conducting the business receives material planning releases which mostly identify customer requirements like order of books, jewels, groceries, or even on huge deals like real estate, either on daily basis, weekly or even monthly basis depending on customer specifications and preferences. This step marks the first agreement and commitment by the customer and constantly provides information necessary to update the company’s internal systems on customer preferences.
Text Report: this can be in the form of a text indicating that, goods ordered are ready to be picked up and acts as a confirmation to the customer that his/ her request has been acted up on.
Report of Test Results: before any material is shipped or transported to the customer, it is always noble to carry out the necessary tests to ensure the quality ordered is the quality delivered. With electronic commerce it is always not easy to return goods once received probably due to high costs involved, the more the reason this step is necessary. The materials ordered are packed or loaded into units of transportation and a bill of lading prepared. The report of test results ascertaining on quality is send at this step.
Advanced Ship Notice: This notice serves to notify the customer on the details of shipment and further confirms on accuracy and time. It is in this notice the customer is made aware on what to expect, when and where.
Advice: this is also referred to as the application advice and it provides a report on the result of an application by the consumer, it is normally used to edit consumer requirements or specifications in the transacting company systems.
Receiving Advice: This notifies receipt of ordered good or services.
Invoice: receipt of ordered goods or services by the customer triggers invoice process, payment sometimes would depend on the customer, some may prefer to do it on receiving the advanced ship notice or opt to wait until they receive their orders.
For an effective business communication each party should ensure information communicated is accurate, timely, complete and closely verified and also be able to receive and send business documents via a certain electronic media, for example; EDI, FAX, Email and so on.
Assumptions for Use
For any transaction to be executed both the client and the host company should be well connected to allow communication between the two such that they are able to receive and send business documents via EDI, E-Mail, Fax or WEB; must have access to internet.
The host company should have the capability to receive payments, for example needs to have an operational bank account accessible to all online subscribers.
The host company should be able to deliver the item or products to customers and provide after sales service, this improves timely delivery.
The consumer has the capacity to receive, retain and print the electronic contract so as to ensure he/she has a proof of the transaction and it can easily be produced in cases of a bleach of contract by the seller.
The electronic contract is presented to both parties in such a way that it cannot be changed or in a way that rules out any kind of alterations after it has been received.
Electronic signatures are authentic and can reasonably be linked to the contracting parties, this is to ensure the consumer is protected, especially when the transaction involves business and a consumer such that any loss as a result of unforeseen irregularities falls on the merchant.
Existence of secure communication such that any dealing between the parties is private and no one can eavesdrop and probably modify the conversation; this can be achieved by developing a world wide infrastructure for identity determination and to be able to associate network presence with individuals (Rooney, 1992).
Evaluation
Electronic commerce has made it possible to many people all over the world to have access to the world wide market; this casts the level of conducting business and initiates variety to consumers.
Electronic commerce has led to minimal sales cost to most companies which have embraced the technology; this is because it cuts out a series of steps involved in seeing a transaction through like to and fro transport costs of meeting the customer, reduced telephone costs and so on.
The technology has opened up companies to compete on global scale with large and other multinational companies; competition mostly brings out quality services to the consumers which would in turn increase purchases ultimately improving market value for companies.
The fact that a consumer can be able to find items or products that are rare to get from their locations improves the market value for companies carrying out the transactions due to wider coverage ultimately translating to high sales volumes implying high profit margins.
Traditionally every transaction was carried out physically implying the premises and the buildings had to be impeccable, electronic commerce disregards big offices and other buildings such that one can even opt to carry out transactions from the house, thus reduced costs of operation. The money which would otherwise be spend on constructions can now be spend on improving sales or in any other profitable way thus improving on market value.
Electronic commerce allows for use of online catalogue which would allow for automated cost comparison, this ensures the merchants are always aware of price fluctuations and are able to adjust appropriately to maximize on profits and rule out losses which would otherwise be accrued.
With electronic commerce one is able to track purchases and use the data as a marketing strategy to recommend to other customers, ultimately increasing sales volumes which will in turn have a positive impact on the market value of the company.
With electronic commerce the store is always open contrary to traditional physical way of doing business where there would times of closure, this ensures more customers are able to access goods and services at their convenient times ultimately increasing sales volumes.
Implications
Considering that electronic commerce allows for a 24hour economy it would mean more convenient means of conducting business thus facilitating a faster nationwide economic growth.
The rise of internet accelerates the decrease in cost of information, this implies an increased access by people to internet, improving the levels of transactions.
“Electronic commerce provides the environment for new forms of markets, such as electronic matching of sellers and buyers, or enabling a direct exchange between sellers and buyers” (Buxmann and Gebauer, 1998).
According to (Cornford, Gillespie, & Richardson, 1996), electronic commerce will have a great impact on the services economy, this is so due to the fact that goods in this category are high order ones with a relatively high price and high information content, examples are art and antiques or even jewelers.
Electronic Commerce will have a great impact on time spend on marketing or even shopping, a clear indication that consumers don’t only base their use of market channels on transaction cost but also on other factors like convenience (Bailey and Baikos, 1996).
Electronic commerce will have an enormous impact on auction markets since it offers online auction market thus eliminating the need to attend auctions but rather do it from the comfort of one’s office or house; this eliminates the need to travel in order to obtain market information, or even attending physical auctions ultimately reducing the costs of time consuming perambulations (Flynn, 1997).
References
Bailey, J. P., Baikos, Y. (1997). An exploratory study of emerging role of electronic intermediaries. International journal of electronic commerce, 1, (3), pp. 7 – 20.
Buxmann, P., & Gebauer, J., (1998). Internet based intermediaries: the case of real estate market. CMIT working paper 98-WP-1027, Web.
Cornford, J., Gillespie, A., & Richardson, R. (1996). Regional development in the information society: A review and analysis, paper prepared for European High Level Expert Group on the social and Societal Aspects of the Information Society/CEC DGV. Curds. Newcastle.
Flynn, T. (1997). No surfing with sharks. Antique Trade Gazette, 30.
Freeman, C., & Soete, L. (1994). Work for all or mass employment? Computerized technical change into the 21st century. London. Pinter publishers.
Rooney, P. (1992). “PC document management catches eye of big business”, PC week, 1992, Vol. 9 p. 45.