Introduction
In the year 2003 the then president of the United States legalized a national strategy to secure the country’s cyberspace. The primary objectives for this strategy were to prevent any attacks against the United State’s infrastructures, to reduce the country’s propensity to attacks over the internet and to reduce to the lowest levels possible the damage that occurred from cyber attacks. The government at the time put in place criminal laws to allow for the investigation and prosecution of individuals suspected of partaking in cybercrime. Various institutions were set up to help with investigation of crimes that involve computers or computer networks with the United States working very closely with other nations in dealing with cybercrimes by setting up round-the-clock emergency contact networks. Other efforts aimed at a sustaining the collaborative effort between the United States and other nations included the signing of multilateral treaties such as the convention on Cybercrime. Such treaties have been heralded by the United States as very important tools in dealing with transnational cybercrime.
A study of various cyber security challenges that touch on aspects of society, from economic to societal reveals that there is a need to raise the profile of cyber security as a component that demands national priority. The challenges have a serious implication on the country’s security and as such demand that a concerted national effort in dealing with cybercrime be encouraged.
The economic sector has been most affected because of the modern-day reliance on technology for virtually all aspects of production. Information systems are vital in ensuring efficiency within the various organizations in respective through proper storage and access of data. Countries where this happens effectively gain in terms of state reputation and financial benefits. However, with rapid changes taking place in the telecommunication sector, there are bound to be even more changes in the way criminal activities happen. It is therefore mandatory that governments develop adequate legislation to help protect their citizens from cybercrime in the case of the widening cyberspace.
This report seeks to analyze the various effects of cybercrime. To this end, the report will try to adopt an interpretive paradigm to illustrate the impacts of these challenges to the control of cybercrime. In addition to the explaining the challenges, the report will also provide a brief detailing of the steps involved in the enhancement of cybersecurity.
Israel and US fingered for Stuxnet attack on Iran’s Nuclear Program
Unnamed sources at Israel’s Dimona nuclear complex said the malware was developed there over the last two years as part of a joint US-Israeli operation designed to sabotage Iran’s nuclear program. The foundations of this work were reportedly laid by American Intelligence Agencies, who identified the type of controllers Iran intended to use and their vulnerabilities back in 2008. Testing of the Siemens controllers took place at the Idaho National Laboratory as part of a larger exercise in cyber-security testing, according to the sources.
After months of confusing and occasionally conflicting statements, Iranian president Mahmoud Ahmadinejad recently confirmed that the worm had sabotaged uranium-enrichment centrifuges at Natanz. Production at the facility reportedly dropped by 30 per cent, as a result of which setting Iran’s nuclear program was set back by months. as a result.
Sophisticated attacks targeted major Oil and Gas organizations globally
Bloomberg News has identified six of the energy companies targeted in a recent series of “coordinated covert and targeted cyber attacks” and says the victims could face legal liability for choosing not to disclose them to shareholders. The roster includes ExxonMobil, Royal Dutch Shell, BP, Marathon Oil, ConocoPhillips, and Baker Hughes, according to an article the news service published on February 2011. The attackers “targeted computerized topographical maps worth ‘millions of dollars’ that show locations of potential oil reserves,” Bloomberg said, citing Ed Skoudis, founder and senior security consultant for InGuardians. The hacks were first disclosed in a report issued by McAfee, which said they resulted in the in the loss of “project-financing information with regard to oil and gas field bids and operations.”
Security giant RSA breach leaks data for SecurID two-factor authentication tokens
Attackers breached the servers of RSA and stole information that could be used to compromise the security of two-factor authentication tokens used by 40 million employees to access sensitive corporate and government networks around the world.
Attacks Attackers were able to access the seeds for specific companies, resulting in providing them with the ability to generate the pseudo-random numbers of one of its tokens, allowing them to clear a crucial hurdle in breaching the company’s security. Attackers were also able to get access to RSA’s SecurID source code that gives them the blueprint of vulnerabilities to exploit, or the theft of private cryptographic keys that might allow them to imitate RSA servers or register new employee tokens.
Iranian attackers suspected in forging Google’s Gmail credentials
Extremely sophisticated hackers, possibly from the Iranian government or another state-sponsored actor, broke into the servers of a web authentication authority and counterfeited certificates for Google mail and six other sensitive addresses, the CEO of Comodo said.
The March 15 intrusion came from IP addresses belonging to an Iranian internet service provider, and one of the purloined certificates was tested from the same country, said Melih Abdulhayoglu, whose company is the certificate authority used to validate the bogus web credentials. Other web addresses that were targeted included google.com, login.yahoo.com, login.skype.com, addons.mozilla.com, and Microsoft’s login.live.com. As a result, the attackers would be able to intercept secure communication and login information to the targeted domain names.
Israel propose a creation of elite counter-cyber terrorist unit
Israel is proposing the creation of a counter-cyber terrorism unit designed to safeguard both government agencies and core private sector firms against hacking attacks. The proposed unit would supplement the efforts of Mossad and other agencies in fighting cyber espionage and denial of service attacks. Israel is, of course, a prime target for hackers from the Muslim world.
The country’s hi-tech industries also make it an interesting target for cyber espionage from government-sponsored hackers from China and elsewhere. Spear-phishing attacks featuring targeted emails, custom malware and subsequent hacking action have been in the news over recent weeks, in the wake of cyber attacks against EU agencies and oil-prospecting multinationals, to quote just two recent threats.
US-CERT warns of critical industrial control system bug
A group collaborating with the US Computer Emergency Readiness Team is warning oil refineries, power plants, and other industrial facilities of a bug in a popular piece of software that could allow attackers to take control of their computer systems. The vulnerability in the Genesis32 and BizViz products made by Massachusetts-based Iconics could allow attackers to remotely execute malicious code on machines that run these SCADA, or supervisory control and data acquisition, programs. The programs are used to control equipment used in factories, water, wastewater and electric utilities, and oil and gas refineries.
US-CERT recommends that users of SCADA software take basic precautions to protect themselves from security breaches. The measures include isolating critical devices from the Internet and locating networks and remote devices behind firewalls.
Lockheed Martin suspends remote access after network intrusion
Lockheed Martin has reportedly suspended remote access to email and corporate apps following the discovery of a network intrusion that may be linked to the high-profile breach against RSA earlier this year. The manufacturer of F-22 and F-35 fighter planes has reset passwords in response to a “major internal computer network problem”, according to two anonymous sources and an unnamed defense official, Reuters reports. Technology blogger Robert Cringely reports that Lockheed detected the suspected breach on Sunday. He adds that an estimated 100,000 personnel will be issued with new tokens before remote access is restored, a process likely to take at least a week.
China announces the need to get into cyber warfare
Senior Chinese officers think that the People’s Liberation Army (PLA) needs to make more of an effort on cyber warfare. Reuters reports on an essay written by PLA colonels Ye Zheng and Zhao Baoxian in the Party-run China Youth Daily. The two officers, who are strategists at the PLA’s Academy of Military Sciences, argue that China “must make mastering cyber-warfare a military priority”.
The essay goes on to say:
Just as nuclear warfare was the strategic war of the industrial era, cyber-warfare has become the strategic war of the information era, and this has become a form of battle that is massively destructive and concerns the life and death of nations.
US forced to redesign secret weapon after cyber breach
The United States may be forced to redesign an unnamed new weapon system now under development – because tech specs and plans were stolen from a defense contractor’s databases.
Reuters and Aviation Week report on the revelation by US Deputy Defense Secretary William Lynn, made in the course of announcing beefed-up cyber defenses intended to put a stop to such intrusions. Lynn said that a “foreign intelligence service” was behind the theft of the secret weapon’s blueprints in March – apparently amounting to 24,000 files – but declined to specify which nation had carried out the attack.
“It is a significant concern that over the past decade, terabytes of data have been extracted by foreign intruders from corporate networks of defense companies,” Lynn said. “In a single intrusion this March, 24,000 files were taken.”
Global Threat Landscape
Key Highlights
- 105,536 unique web malware were encountered in March 2011, a 46% increase from January 2011.
- Malicious webmail represented 7% of all web-delivered malware in March 2011, a 391% increase from January 2011.
- 45% of all malicious webmail resulted from Yahoo! Mail, 25% from Microsoft Live/Hotmail, and only 2% from Google’s Gmail.
- Search-engine-related traffic resulted in an average of 9% of all web malware encountered in 1Q11.
- 33% of search engine encounters were via Google search engine results pages (SERPs), with 4% each from Yahoo! and Bing SERPs.
- SERPs and webmail encounters are impacted by the popularity of a particular service and are likely not indicative of any heightened risk specific to that service.
- Likejacking increased significantly during the first quarter of 2011, from 0.54% of all web malware encounters in January 2011 to 6% in March 2011.
- At 13%, Miley Cyrus–themed likejacking scams beat out all other celebrities and events in March 2011. Likejacking themes for Indian actress Nayantara were at 7%, while Charlie Sheen was at 3%, Justin Bieber at 2%, and Lady Gaga at 1%.
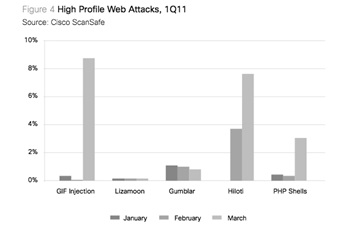
- At 4% of all web malware encounters in 1Q11, website compromises that attempted to download the Hiloti Trojan were the most frequently encountered, followed by malicious GIF injections (3%). Website compromises related to the Lizamoon series of SQL injection attacks represented just 0.15% of web malware encounters for the quarter.
- Though far less successful than in years past, SQL injection attempts continued to be the most prevalent event firing (55%) observed by security researcher and analysts around the world in 1Q11.
- Malware activity related to the MyDoom worm was the 10th most frequently observed IPS event in 1Q11, demonstrating that legacy malware can still pose a threat to unprotected systems.
- As expected, Rustock activity declined significantly over 1Q11, but, interestingly, the sharp decline commenced weeks prior to the botnet takedown.
- Following 4Q10 declines, global spam volume increased and then subsequently decreased during 1Q11, but levels remained above that of December 2010.
- With an increase of 248%, Indonesia overtook the United States as the top spam-sending country in 1Q11.
Web Threats Trends and Analysis
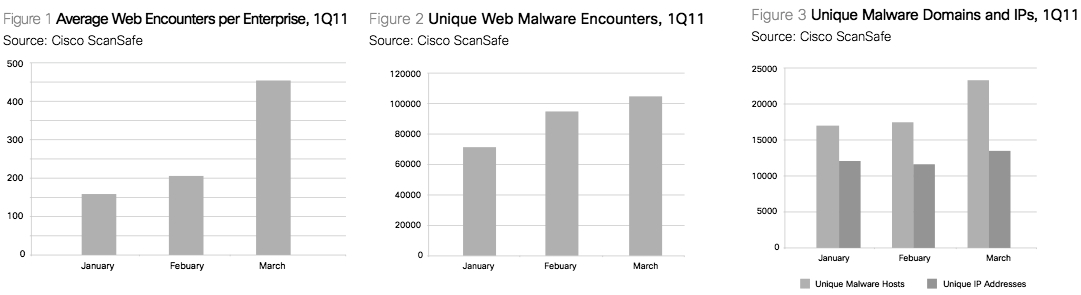
Enterprise users experienced an average of 274 web malware encounters per month in 1Q11, a 103% increase compared to 2010. Unique web malware encountered also increased (46%) in 1Q11, from 72,294 unique web malware in January 2011 to 105,536 in March (Figures 1-3).
Though web malware continues to increase, far fewer large-scale compromises are occurring compared to previous years. Instead, compromises are more focused on the “long tail” of the web, with fewer compromises per attack but a far larger number of separate attacks. As Figure 4 demonstrates, the largest outbreak occurred in March 2011 with a series of GIF injection attacks targeted at popular Pakistani news sites.
Web searches resulted in 9% of web malware encounters in 1Q11, with an average of 33% resulting from Google search engine results pages (SERPs) and 4% each from Yahoo! and Microsoft Bing SERPs. The majority of web search encounters (58%) occurred via smaller search engines and/or searches performed on non-search-engine websites (Figure 5).
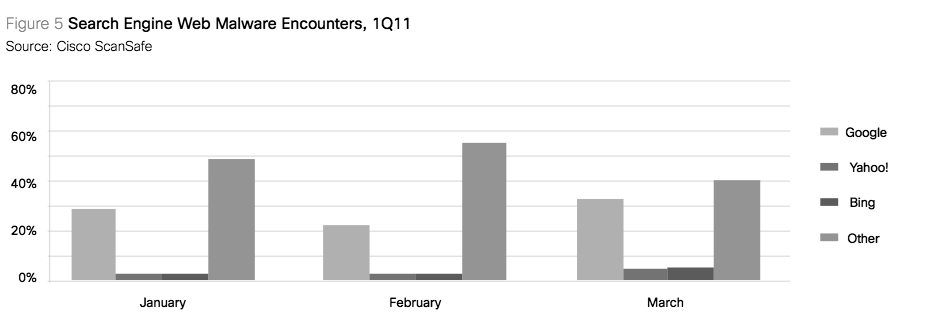
It is important to note that search-related malware encounters are not reflective of any underlying risk with a particular search engine; rather, these encounters are due to the popularity and thus increased usage of a particular search service.
Email Threats and Analysis
The 2011 takedown of segments of Rustock, combined with multiple spam botnet takedowns in 2010, had a positive impact on overall spam volume. However, spam volume in 1Q11 remained above the lowest point recorded in December 2010. Figure below reflects the global spam volume as reported through Cisco SensorBase Network participants.
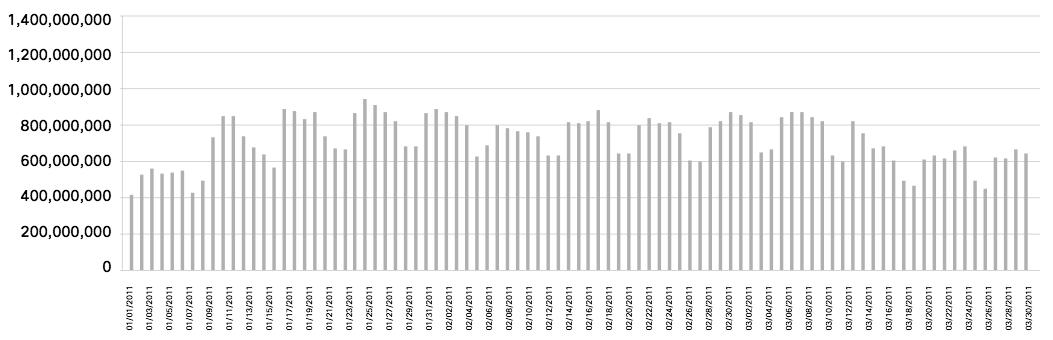
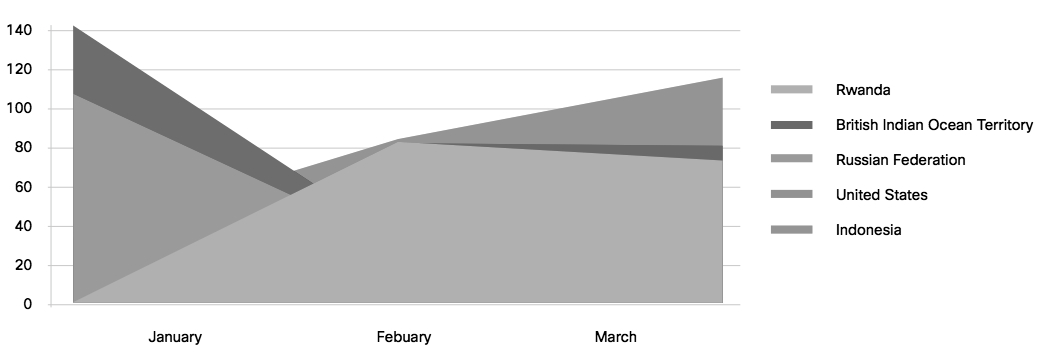
Interestingly, while the takedown efforts had the most positive impact on spam originating from the United States and Russia, spam originating from other countries is rapidly increasing.
Although they represent a relatively small percentage of overall spam, phishing attacks pose a serious risk to security, both from a financial and sensitive information disclosure perspective. In 1Q11, attackers increasingly turned their attention toward phishing Twitter accounts (Figure below). This interest in Twitter credentials is likely due in part to Twitter users’ acceptance of shortened URLs. By compromising Twitter accounts, attackers can take advantage of shortened URLs to entice followers to visit malicious links the users might ordinarily view as suspicious. Such attacks are further fueled by the trust engendered through social networking in general.
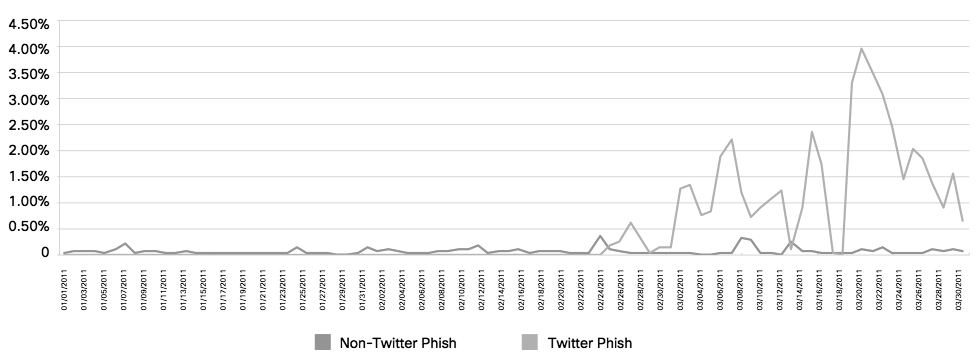
In summary, while global spam volumes have increased, the malware encounter rate via webmail has substantially increased. Further, social networking scams involving both Facebook and Twitter also increased throughout the first quarter. Web-delivered malware is also at an all-time high and the rate of encounters with unique new malware continues to increase
Showcase: The Digital Nuclear Attack against Islamic Republic of Iran
The earliest cybercriminals specialized in casting a wide net to find targets for their schemes. Poorly written spam messages, sent out by the millions, were aimed at any and all possible email addresses. Spam filters now catch most of these messages, but a small fraction of recipients will still click through to download malware unwittingly or decide to order non-existent pharmaceuticals.
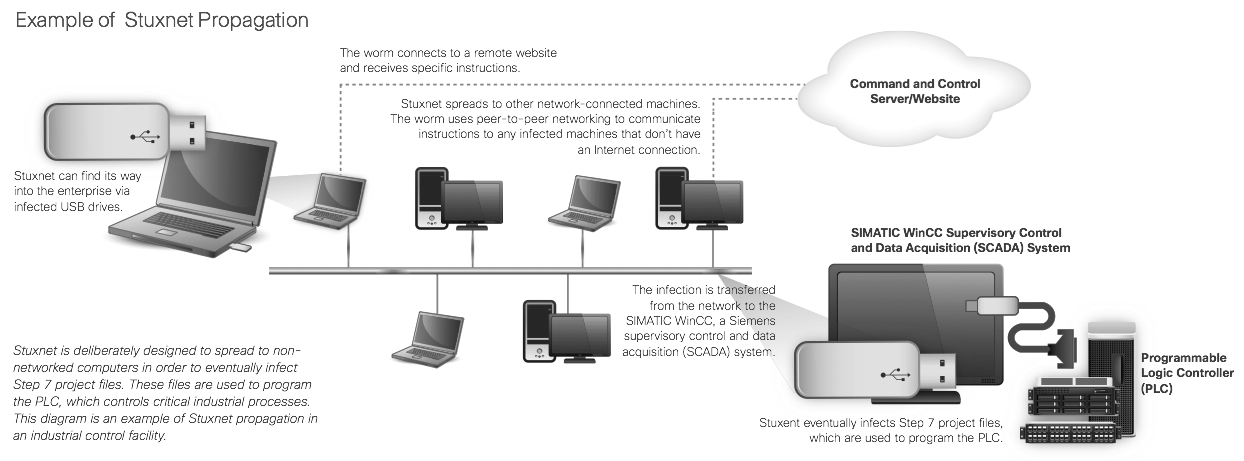
While broadly aimed spam still appears to be an effective tool, cybercriminals are seeing value in fine-tuning their efforts so that their malware reaches a single high-profile target or performs a specific function. The newest twist in “hyper targeting” is malware that is meant to disrupt industrial systems—such as the Stuxnet network worm, which exploits zero-day vulnerabilities in Microsoft Windows to infect and attempt to tamper with very specific industrial systems, such as supervisory control and data acquisition (SCADA) systems.
While components of Stuxnet date back to 2009, the worm in its complete form was initially detected in June 2010. The first known copy of the worm was discovered in a plant in Germany. A subsequent variant led to a widespread global outbreak.
The appearance of Stuxnet is sobering for several reasons, not the least of which is the worm’s potential to severely disrupt critical infrastructure. Stuxnet seems to have been designed to deflect remediation and response actions from security professionals. Operators believed that a default Siemens password (which had been made public on the web some years earlier) could not be corrected by vendors without causing significant difficulty for customers. The SCADA system operators may have been laboring under a false sense of security that since their systems were not connected to the Internet, they would not be prone to infection.
Stuxnet’s built-in features exploit both technical and operational trusted relationships—for instance, the malware used stolen security certificates, fooling other systems into believing it was a legitimate piece of programming. Stuxnet has already been studied extensively, and much has been revealed about its inner workings—providing a blueprint of sorts for future such campaigns, and educating criminals on how exactly to create these exploits themselves.
“Stuxnet showcases the determination, resources, and dangerous intent of today’s cybercriminals,” reports Mary Landesman, senior security researcher at Cisco. “Stuxnet raises the already alarmingly high bar of data and intellectual property theft to an entirely new level— sabotage of our critical infrastructure.”
Showcase: Operation “AntiSec”, a perfect example for Cyber Hacktivism
Conclusion
The aim of any country is to attract attention to the services/goods it produces and to ensure sustainability by maintenance of efficient working systems. Information and communication technology (ICT) is a crucial component of any country’s growth. It plays a key role in the management of state and private venture operations by ensuring that all members involved are within contact distance from each other as well as assist in proper organization of company records. The world is indeed becoming a global village with business exchange and educational activities being carried out through the internet and via satellite systems. In this way, information systems help provide the link between business and technology because the more efficient an organization’s operations are, the more its economic benefits.
However, and has been illustrated in this report, cyber security has been an issue of concern primarily because everyday there are individuals whose main aim is to infringe on the integrity of networks and databases. It is recommended that more concerted effort be effected in developing a coordinated and collaborative approach for cyber security research. All government agencies need to develop innovative approaches for handling cyber security. In addition, legislative and policy frameworks need to be assessed and analyzed with the consideration of reviewing them to include measures against new forms of cybercrime. Finally, more training needs to be conducted in order to increase capacity for handling cyber-security related criminal activities.
Various countries depending on their sizes adopt suitable information systems that help make sensible managerial frameworks. These information systems are vital in ensuring efficiency within the various organizations in respective through proper storage and access of data. As a result, gains are made both in terms of country reputation as well as financial benefits. However, with rapid changes taking place in the telecommunication sector, there are bound to be even more changes in the way criminal activities happen. It is therefore mandatory that governments develop adequate legislation to help protect their citizens from cybercrime in the case of the widening cyberspace. The research was based on secondary data collection. Data was extracted from various online publications. The criteria for literature selection were the relevance to the research topic and the currency guided by the year of publication. Both public and private libraries as well as online libraries were visited to access the data.
Empirical data was collected from recent studies and numbers and figures used to show the impact of cybercrime legislation in the particular regions of study and how they could effectively be used to help make internet networks secure. Like with any other professional field of study, Information Technology research has to be conducted in such a way that the offer credibility to the practitioner. In such a scientific field, the strength of any report lies in the figures provided to support theoretical data and particularly the numbers obtained from real life scenarios to support collected evidence.
References List
Chan Jay et. al. Cisco 1Q11Global Threat Report Featuring Data from Cisco Security Intelligence Operations. (1005R) C02-640572-00 1/11.
Leyden, John. “Israel and US fingered for Stuxnet attack on Iran”. The register. Web.
Goodin, Dan. “Exxon, Shell, BP outed as mystery hack attack victims”. The register. Web.
Goodin, Dan. “’Iranian’ attackers forge Google’s Gmail credentials”. The register. Web.
Goodin, Dan. “RSA breach leaks data for hacking SecurID tokens”. The register. Web
Goodin, Dan. “CERT warns of critical industrial control bug”. The register. Web.
Leyden, John. “Israel mulls creation of elite counter-cyberterrorist unit”. The register. Web.
Leyden, John. Lockheed Martin suspends remote access after network ‘intrusion’”. The register. Web.
Page, Lewis. “Chinese army: We really need to get into cyber warfare”.The register. Web.