Access, Install, Setup, and Run Wireshark
Wireshark is a security tool that was initially developed at the end of the 20th century. It was regularly upgraded, and the last release became available a little bit more than a month ago. It is a packet analyzer that can be easily accessed by Internet users. The tool can be downloaded for free from the official website. For users not to waste time trying to find out how Wireshark works, a special guide was created. In addition to that, it can be obtained in several formats so that people have an opportunity to find the one that meets their needs and requirements (“Wireshark”, 2017).
The tool runs on Unix-like systems, Microsoft Windows, Linux, and macOS, allowing the users to see all traffic visible on the interface. So it is significant to install an appropriate version of Wireshark. (“Installing Wireshark under Windows”, 2017). The users just need to open a file to start the installation. It will end automatically. This tool can be updated about once in six weeks. The process is the same as the installation, and personal settings do not change, which is rather convenient.
A guide can help the users to set up a capture with no difficulties. It is critical to:
- Ensure that policies and laws allow capturing packets.
- Ensure that it is allowed to change the network (if needed).
- Obtain root/administrator privileges.
- Have a capture driver installed.
- Check time zone settings.
- Start a capture.
- Select an appropriate interface to run the tool (“How to set up a capture”, 2017).
Value for a Cybersecurity Expert
Wireshark ensures network security and allows us to maintain a bit of forensic analysis, which is critical for an expert. If there is a possibility that the system was affected by a virus or a worm, the user may block packet sniffers or limit their effects. With the help of port mirroring, packets can be captured from the targeted system (see Fig. 1). Each packet can be checked then to see if it reveals any important data.
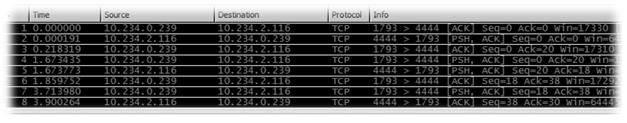
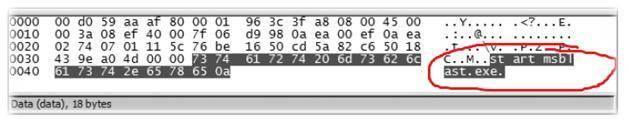
If something suspicious is found, an expert can try to protect a system. For example, Figure 2 shows that it is possible to start the blaster worm (Karthik, 2011).
Lessons Learned and Best Practices
Wireshark has already proved its benefits for sniffing practices. In addition to that, a long history of its usage provided the professionals with the opportunity to discuss how it should be operated to reach its potential (Griffor, 2016). This tool allows us to solve connectivity issues and analyze traffic activity.
Problems can be faced when selecting a static channel, locating the channel number, and dealing with wireless traffic sniffing. However, they can be eliminated if appropriate frequencies are used, and the area between the capture station and the transmitter is checked. It is also critical to put wireless cards into monitor mode, which can hardly be maintained with Windows drivers. But this issue can be overcome using a combination of software and AirPcap (SearchNetworking, 2012).
Post about Wiki
A wiki page provided in this work allows the Internet users to get to know the most critical information about a security tool known as Wireshark. It briefly outlines how to install this product and work with it safely and securely, allowing people to save the time needed to read a guide if they are not sure whether Wireshark is a thing they need or not. It also provides illustrated examples of the way a cybersecurity expert can use this tool. Finally, the most frequent challenges and the way to avoid them are outlined. Thus, using this wiki page, people will be able to utilize Wireshark immediately and secure their network with no difficulties, which is extremely beneficial.
References
Griffor, E. (2016). Handbook of system safety and security. Amsterdam, Netherlands: Elsevier.
How to set up a capture. (2017). Wireshark. Web.
Installing Wireshark under Windows. (2017). Web.
Karthik, R. (2011). This Wireshark tutorial will familiarize you with Wireshark’s advanced features, such as analyzing packets and undertaking packet level security analysis. Web.
SearchNetworking. (2017). Wireless sniffing best practices using Wireshark. Web.
Wireshark. (2017). Web.