- Introduction
- Main body
- Workshop 3A: Analysis of System Parameters:
- Repeat Task 1 with the instance profile
- With Extended Maintain ace
- Repeat with advanced editing. (Extended Maintenance)
- Workshop 4B: User Administration
- Workshop 5B: System Monitoring (ADVANCED)
- Workshop 6. Client Administration
- Two configuration system to create
Introduction
This paper is to explain the transaction codes and their uses. We are going to check the transactions code, but some of which are important have been demonstrated in this paper.
In the process of work, system administrators use the set of transactions that include SU01, ST02, SM50, RZ10, DB02, and SECR.
Main body
The transaction SU01 can be used for the administrator authorization and the creation of a new system user. ST02 fulfills the functions of identifying the SAP system buffer performance statistics. SM50 transaction allows seeing and managing the work processes in the system and reducing or increasing the workload based on the data. Further on, RZ10 allows editing the instance profile by clicking the extended maintenance and change buttons in it. DB02 is another statistical transaction that allows seeing the database history, applications record, and current storage capacity. Finally, SECR transaction is concerned with security and environment audit matters. Accordingly, it is transaction SM50 that would allow modifying the threshold value for disk usage percentage for an alert monitor.
In the very initial stage of the workshop several client-server models, both software and hardware, were taught. At the same time, the class taught us the basic fundamentals of the study with general information with a needed description related to issues that are important for the overall study. R/3 system architecture was presented with much clarity and it was indicated that the basic association of 3-layers. These layers are database, application, and presentation. Alongside, there was enough information that allowed gaining the understanding of the layers with their disadvantages and basic advantages. Clarifications were also made in the context of the introduction of the subject that included the numerous aspects of 3 tier layers including background and work processor type-dialog.
In the context of the R/3 system, Transmission Control Protocol/Internet Protocol or TCP/IP was used. This is a case-sensitive network and in wider usage, the Transmission Control Protocol or TCP and the Internet Protocol or IP belongs to the category of Internet protocol suite which can be defined as a set of implementation of communications protocols that is used for protocol stack. This protocol stack is the key functioning authority on which the activation and operation of most of the commercial networks and specifically the internet depend to maneuver. This process is used so that it enables the easy delivery and collection of files to and from the manager. Alongside, Network Basic Input/Output System or the NetBIOS makes it possible within the network of large TCP/IP networks in the local form in order to communicate the initial application. All these make it possible for the proper installation of Windows O/S and it provides name resolution for NetBIOS and IP.
The IP name decree is generally connected with the NetBIOS in case there is a communication problem and the retrieval of the hostname is not possible. However, on the framework of TCP/IP configuration, it is possible to locate the IP name resolution under the parameters of the NetBIOS resolution and with the use of the Windows NT 4.0. For this purpose, the software SAPGUI is used. This is a technology that can be used in the context of SAP R/3. Internet Transaction Server (ITS) technology is served on HTML and SAP R/3 is used for connection related to the SAP system and the computer. However, in order to make the Internet Transaction Server applicable, it is important to use Windows NT server or UNIX application servers. As a result, the total system makes it possible for the application to become a better productive medium and the R/3 system would be helpful for use of the internet under the framework of a 3-tier client/server with a much-enhanced performance output. The end result would make sure that the user would be able to connect to the internet once there is the availability of the SAPGUI application and internet connectivity.
It should be noted that the WAS or Web Application Server is a part of the ITS. Transaction AL11 was used in the third workshop as a profile in default mode. Here the startup profile is served on a fundamental basis in order to find and activate the system file. Now, the SAP R/3 ERP system requires several tasks like display, delete, update and insert to operate. The list below is the enumeration of transactions. This was done with the help of results, observation, and screen dump. As a result, Transaction /nal11 includes the entire assimilation and contents of SAP directories. It should be noted that F: drive contains most of the files in the screenshot.
Task 2.2B: These is transactions listed below and set up a table (spreadsheet) to display your main.
Workshop 3A: Analysis of System Parameters:
Task 1.3A. Examine the Default profile
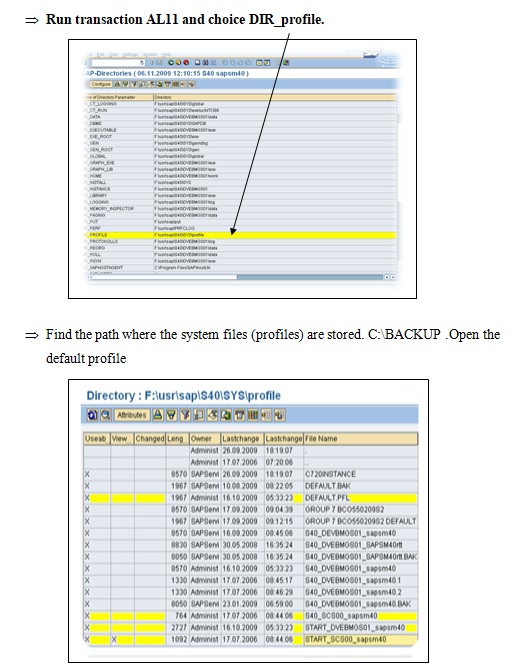
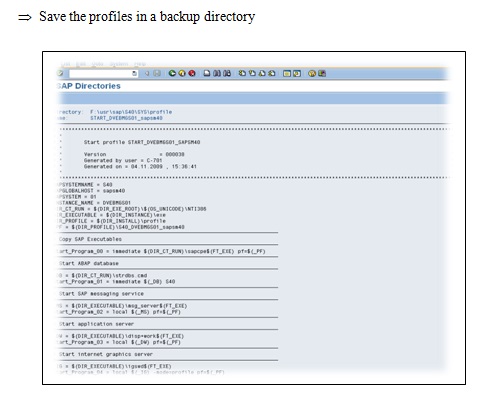
Task 2.3B Examine the Start up profile
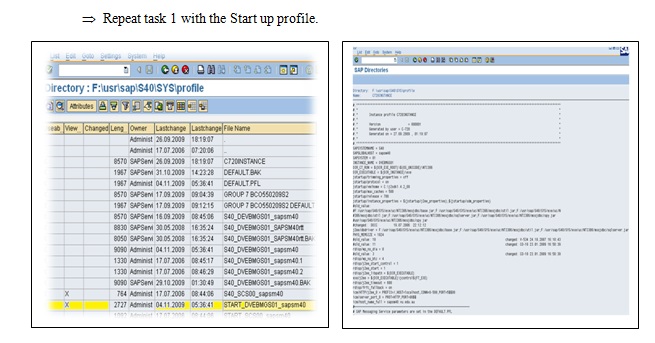
Task 3.3B: Examine the Instance profile
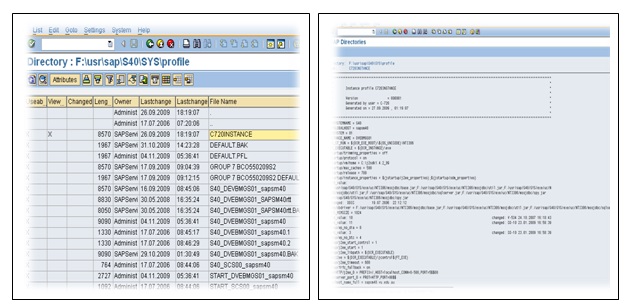
Repeat Task 1 with the instance profile
Task 4.3B: Run transaction RZ10
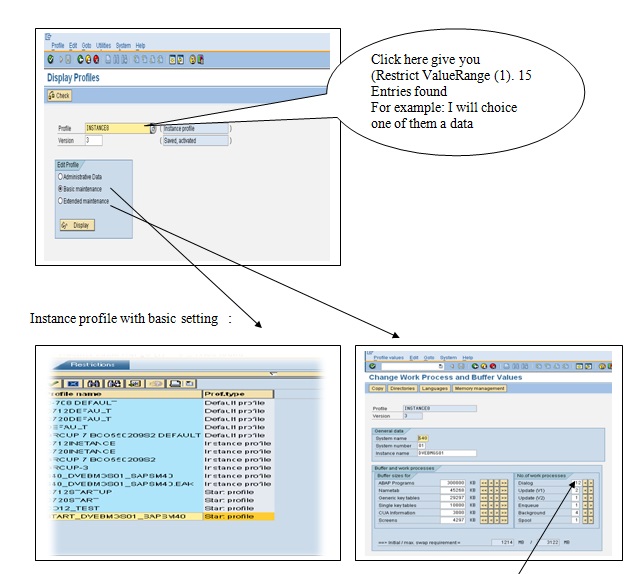
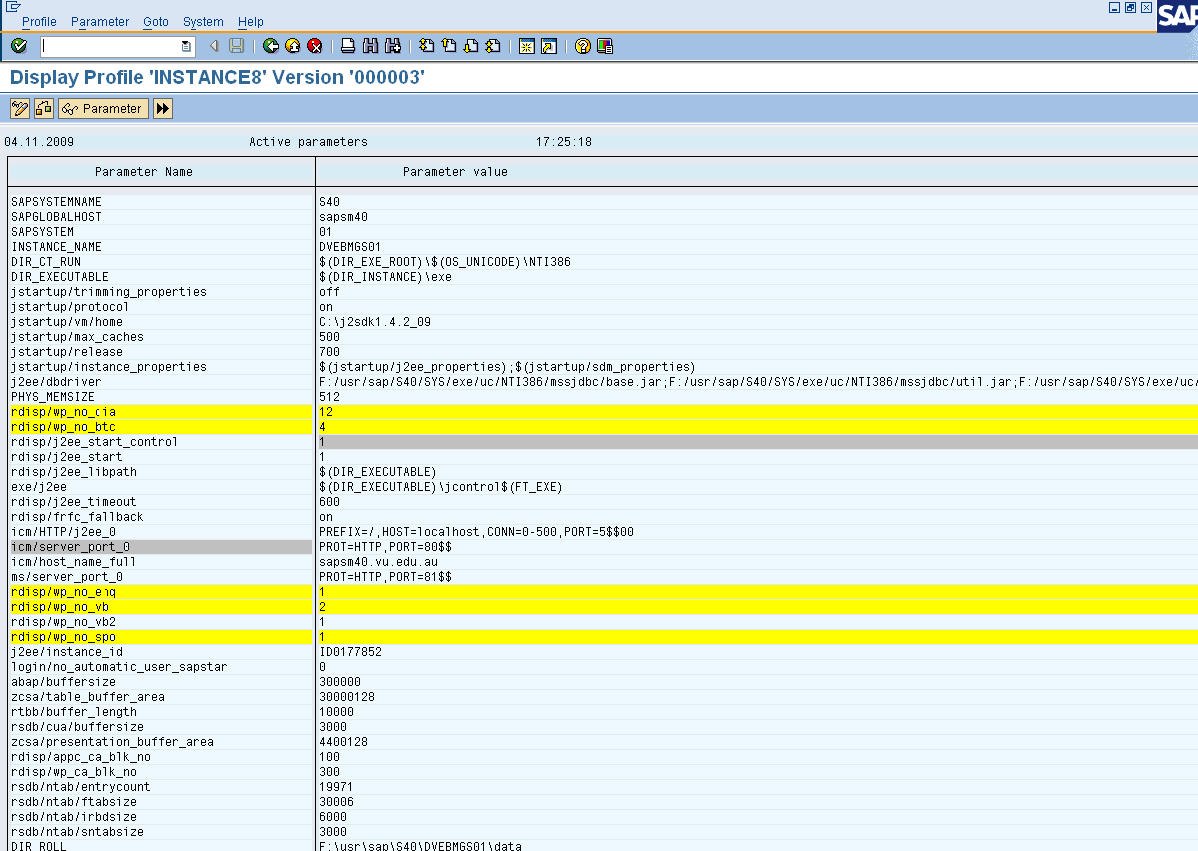
List the rest of the work processes and do not make any changes to any of the parameters. The changes to the profile parameters should be made after a system resource change, and these will only take effect after a restart of the affected instance, or the entire system.
With Extended Maintain ace
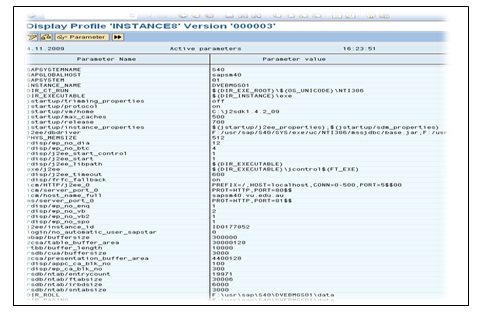
Repeat with advanced editing. (Extended Maintenance)
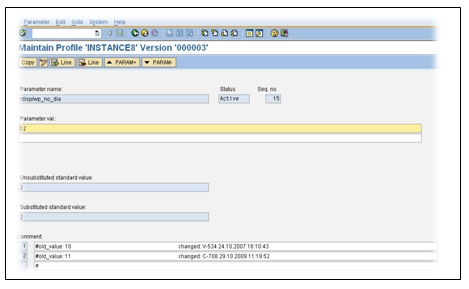
What information can you describe in this screen?
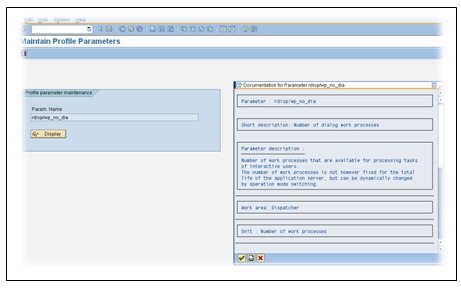
The number of dialog work processes is 12. The rest of them are updates (v1), update (v2), Enquire, background, and spool work process. Do not make any changes to any of the parameters. Changes to the profile parameters should be made after a system resource change, and these will only take effect after a restart of the affected instance, or the entire system.
Task 5: Login parameters. Can you find the relevant parameters that relate to the following?
The minimum password length
validity period of passwords
validity period of new user’s passwords
maximum number of failed logon attempts
Task 6: Run the report RSPFPAR to display the system parameters for the instance to which the user is currently logged on. [Hint: use transaction sa38 with no variants]
You can also use programs at the operating system level using the user adm: sappfpar all.
To check the parameters you can use sappfpar check.
Task 7: Determine the value of the following system parameters

Why there is a risk once the OS level profile is changed?
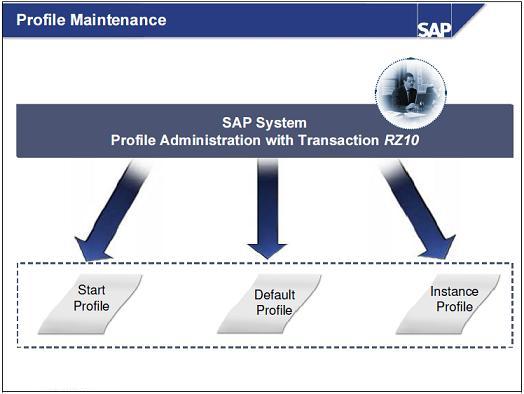
Implementation of Transaction RZ10 or the application of operating system editor is the two basic methods that can enable the change in the OS level profile. Nevertheless, text editor use for the change is risky as it becomes absolutely essential for the user to validate and justify the changes. These changes should be made correctly and without any error. Once there is an error, the values of the set parameters would change and the entire system may collapse and would not start. However, the second method of using Transaction RZ10 is a far better option. Transaction RZ10 is used by SAP and it provides maintenance and administration of the profile thus the values of the set parameters would never change and the entire system may never collapse. Subsequent details are some of the rewards by means of Profile management:
- Fundamental management and preservation of the cases
- Alterations in profile is confirmed for reliability
- Management of numerous adaptations of a single profile
- The contrast of the dynamically used report and the reported stock up in the catalog
- Instantaneous commencement of particular considerations.
It should be noted that in the case of systems that are non-productive in nature, one can actually make alterations to the system profiles. However, when it comes to SAP systems in production, the need for such changes are hardly needed. Nevertheless, sustainable CCMS profile maintenance should be put into use.
The profile maintenance tool has the following advantages:
- Convenience of use
- Extensive profile checks
- Testing of (several) individual profiles for consistency
- No inconvenient profile editing at the operating system level
- Changes to profiles are logged
- Profile data is held in the SAP database (security, consistency)
Run transactions SM51and SM50. Record your results
Transaction code sm51
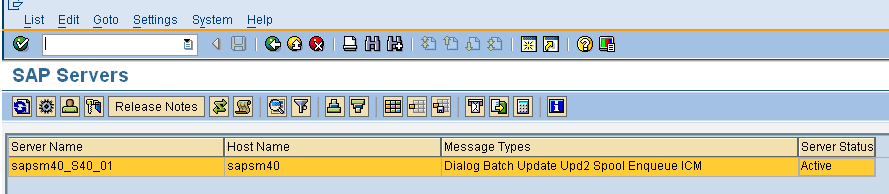
Transaction code sm50
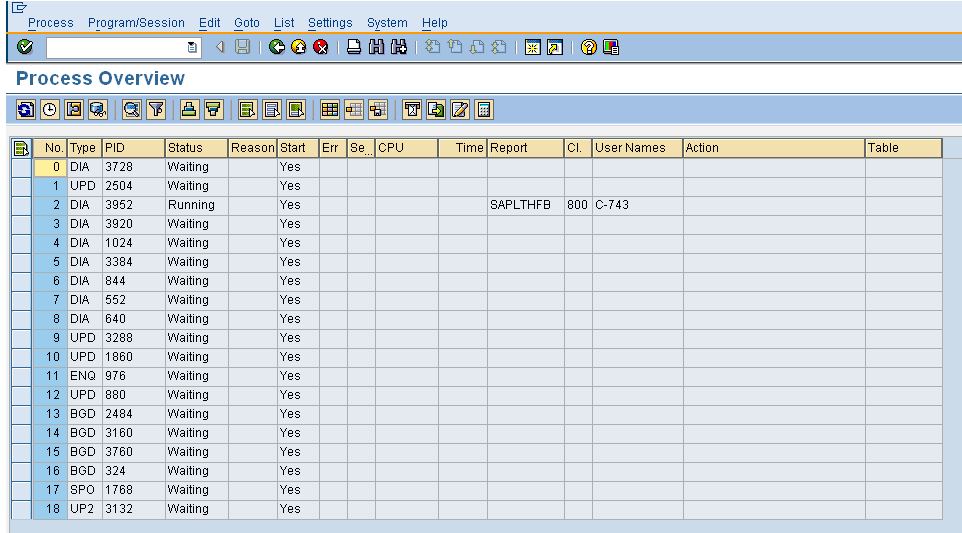
In the code sm50, it gives u the list of the current work process. In my case we have a dialog work process running in client 800 and the user is c-743 and the rest are in waiting mode.
Administrator could you check the number of work processes from the operating system level out of:
- In Windows, I can see the work process status from SAP MMC in WP Table.
- In UNIX, You use DPMON utility.
After Go to profile directory and use the following command. Try to fire this command using theADMuser.
dpmonpf = After this command you will be in DPMON screen than press m for menu and than press p for process table and you are done.
Workshop 4B: User Administration
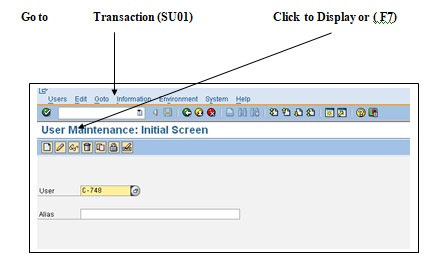
Create users using transaction SU01.
Create the users user1 (co- xx A )and ADMIN5502-xx by copying sap* in client xxx (800)
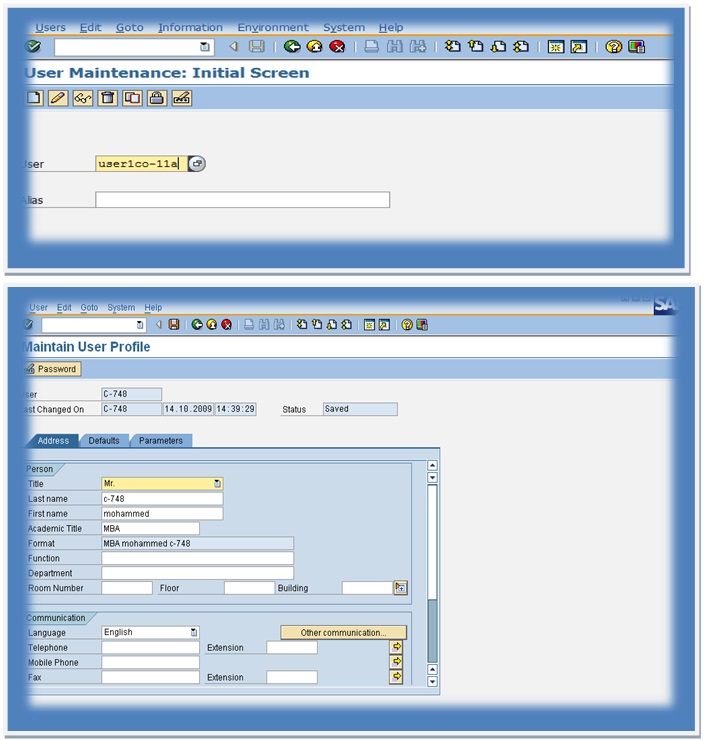
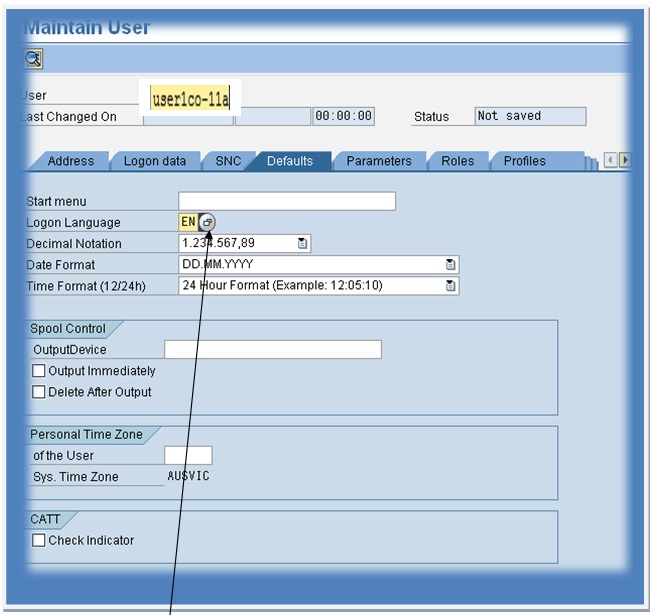
Here we are creating, copying the features of the existing roles, and assigning them to the user-created.
Now, we are using the transaction (pfcg) to generate this functionality. In the pfcg session, copy the role (sap_bc_enduser) to the new role bc5502-22 which is a non-critical authorization for all users.
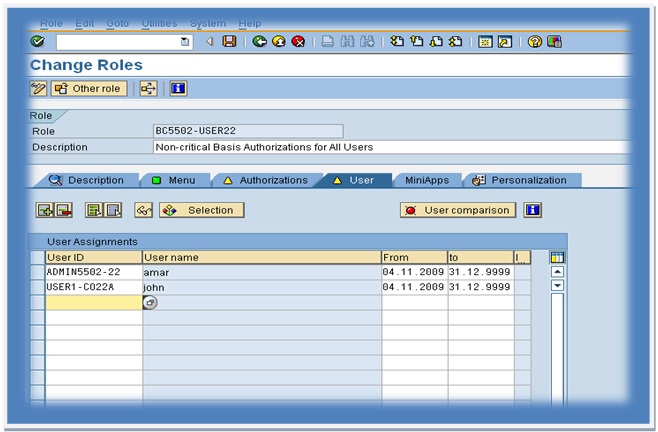
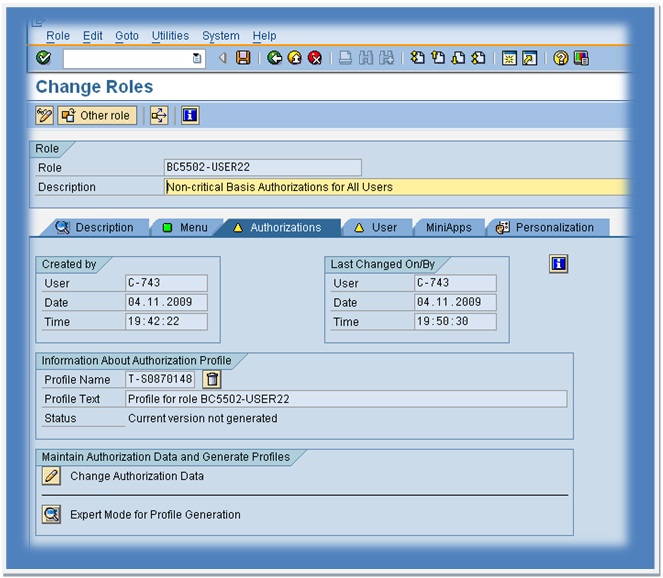
Generating authorization profiles. When going into the change mode. Choose the authorization tab and you can generate the authorization profile there. Also, we can change authorization data in the last but one option there. We can also check the expert mode for profile generation. Activate the open method and check the maintained status also.
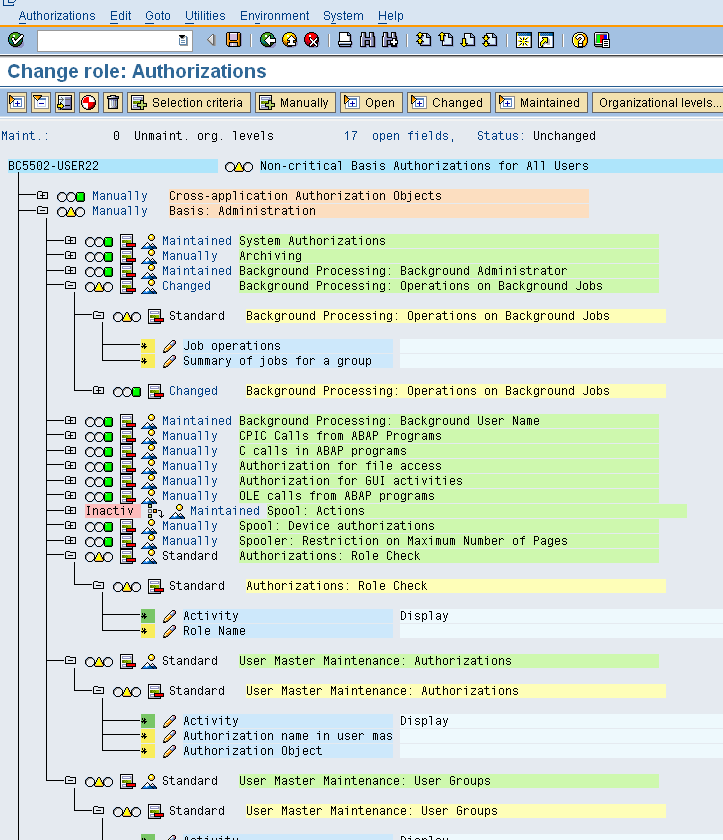
The below diagram is for open authorization and in the same way, we can also generate the maintained authorisation pattern in the same way.
Workshop 5B: System Monitoring (ADVANCED)
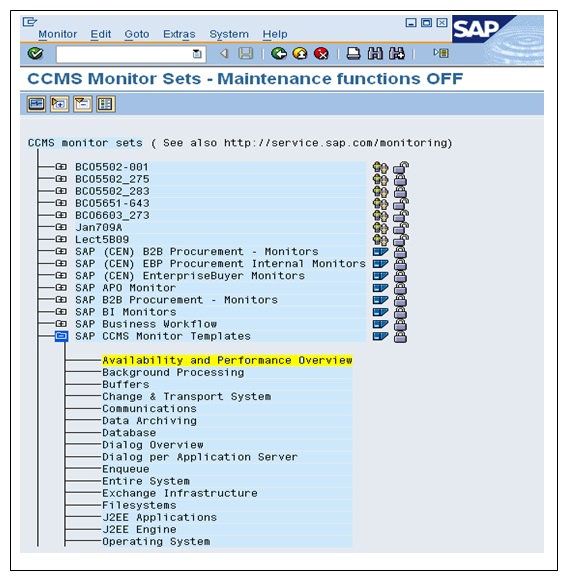
Workshop 6. Client Administration
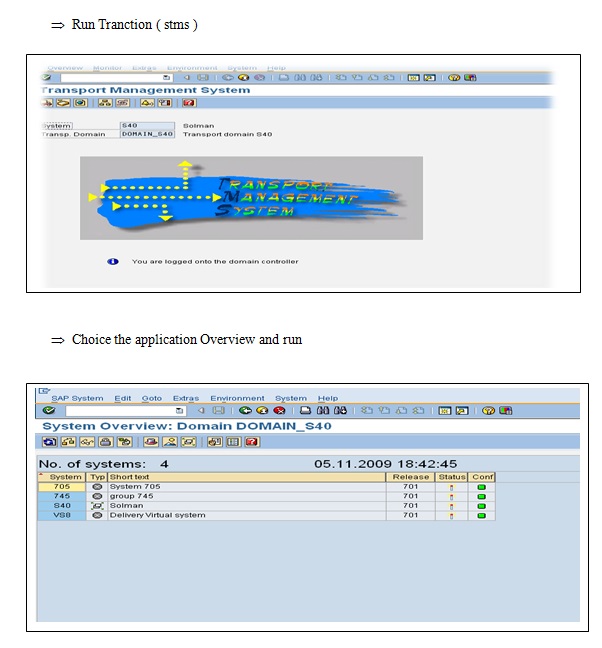
Create an additional system as a virtual system from the graphical editor tool in TMS. What is the purpose of this editor?
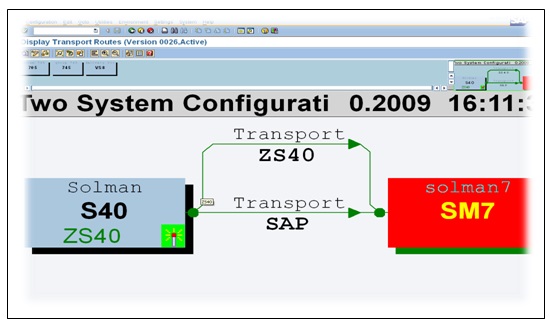
Two configuration system to create
Conclusion
In conclusion, it should be noted that the fundamental issue of the paper was to explain the transaction codes and their uses. For this purpose, a transactions code check was put to use along with a set of transactions that included SU01, ST02, SM50, RZ10, DB02, and SECR. Each part was as important as the other and together the entire paper was formed. Much of Workshop 6, Workshop 5B, and Workshop 3A were used. Their parameters used included Client Administration, Analysis of System Parameters, and Examination of the Default profile. Knowledge on elements, Transmission Control Protocol/Internet Protocol or TCP/IP, R/3 system architecture, Network Basic Input/Output System or the NetBIOS, and Web Application Server was also used. Lastly, the aspect of Profile management was put into use that indicated the advantage, disadvantages, and remedies of Profile management were discussed. It was understood that the SAP system holds a huge parameter in the operation and sustainability of the work in progress of the computer along with sustainable CCMS profile maintenance. In the context of client-server maintenance the project was extremely beneficial and helpful for future applications.