Introduction
This document presents a proposal for an access control system (ACS) for a college dormitory. The ACS will have a face recognition system with a camera connected to the door. Faces of all authorized people will be first scanned and records entered into a database. When a person approaches the door and stands for a specified duration in seconds, a proximity sensor near the door is activated and triggers the camera. The person is required to stand at a designated area and look at the camera. The camera scans the face and if the scan is registered in the database, then the door lock opens and the person can enter the dorm. In case the scan does not match the records, then the entry is denied and an alarm is beeped.
Scope Statement
The scope statement for the project is given as follows – to develop a face recognition system that scans faces to create a repository of scanned faces and matches the face of people who present themselves in front of the face-scanning camera. If the scanned face of the person matches records in the database, then the door lock opens and the person can enter the dormitory. The locking system will be of systems such as turnstile locks that allow only one person to enter after access is granted.
This will prevent multiple people to tailgate and enter behind the person whose face is recognized and access granted. The purpose of this system is to prevent unauthorized people from entering the dorm and carrying out undesirable activities such as theft, assault. The purpose is to prevent a fully integrated system that will not need an operator to control and monitor.
Five Major Tasks
ACS has several components and activities. This section discusses five important tasks that the ACS must perform.
Face Scanning
The most critical part of the system is accurate scanning of facial features and reducing the face rejection rate (FRR) and false acceptance rate (FAR). A high-resolution camera of 1200×1400 is desirable. It should have a high color pixel density to correctly scan the face and send the coded signals to the database. FOR gives a measure of the number of times an authentic user who should be allowed entry, is denied access.
The acceptable rate is 1 in 100,000. The camera can face problems when a person who registered while using eyeglasses, attempt to gain access with glasses. In such cases, it is advisable to have a policy where users will have to remove their glasses while registering. Similar problems can arise for males with and without bears, and for females who may use a high level of makeup. FAR is more serious since it allows entry to unauthorized people who do not have access. A threshold limit is needed to set these errors in perspective. After the face is scanned, the camera must send the images to the server, where a match is done, and access is granted or denied. These systems have to operate at high speeds of a few seconds (Smith, Wiliem & Lovell, 2015).
Recording and Storing Entries
The server with database forms the repository where records are stored. When students are scanned for the first time, along with the face scan, other details such as ID number, name, courses, contact numbers, professor name and number, family contact details, and other details need to be stored. If the system is connected to the college database, then these contact details can be fetched and the face scan entered against the student ID number.
The main advantage of having a networked system is that the student details and scans can be entered once and used in multiple locations and access points, where face scanning, fingerprint, and retina scans are used. Records can be indexed on student ID and algorithms used to quickly match the students face who has come for access, and entry is given or denied. A large college with thousands of students would face speed related issues and the verifying sequence would take a longer time. In such cases, it is possible to have a local server with records of students who are given access. Such an arrangement would complete the scanning and verification process very fast (Ballala, Sandjeev, Swetha & Satyanarayana, 2016).
Integration With Door Locking System
The door locking system is an electro-mechanical system and physical doors must be unlocked and locked through electronic signals. When the face scan result is positive, then an electric signal is sent to the door locking system that can have electromagnetic locks. The doors will unlock when the signal is received, spring-loaded levers will open the door and the student can pull it open and enter the dorm.
A proximity switch will detect when a person passes through or is standing in the doorway. Only after the person passes through, the signal will be activated the door closed. Opening and closing of the door should be done at slow speeds so that people are not injured. If the student is holding the door or placed the fingers in the doorway, the door should not close and crush the fingers (Smith et al., 2015).
Connectivity Mechanisms for Signal Relay
Signal relay from the face reader can be done by using coaxial cables of sufficient capacity to transmit high-density data to the server and relay the information to the locking mechanism. It is also possible to use Wi-Fi and the internet for relaying the signals. If the internet is used, then extra costs for cabling, connectivity is avoided. However, if a college-wide LAN is required to connect the dorm systems to other systems, then the cabling is the best solution. The cabling allows more data to be carried, it is difficult to hack and compromise data. However, it is expensive. The connectivity to the door interlock mechanism needs to be robust since electromechanical devices are operated (Ballala et al., 2016).
Face Reader
Scanning is done with a wall-mounted scanning device that has an LED interface and camera. The LED touch screen allows users to carry out different functions. Standard sizes of these devices are 3.5 inches LED touch screen and the overall size is about 104.70(L) x 180.00(H) x3 6.00(W) mm. If the number of people in the dorm is more than 203, cameras can be placed, all connected to the same system. The device must have a Flash memory of at least 256 MB with 64 SDRAM. Devices are available, that offer multiple authentication systems such as face scan and fingerprint scan. The camera needs to record high-resolution core with infrared capabilities. The whole system will have a limit on the maximum number of records that it can store and logs of 100,000 capacities are available (Adman Technologies, 2017).
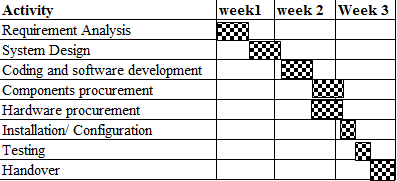
Gantt Chart
The following figure presents the Gantt chart for the project.
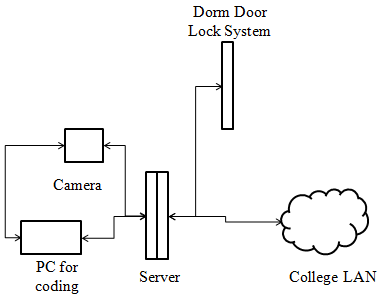
System Diagram
The system diagram with major components and their connectivity is illustrated in the following figure.
References
Adman Technologies. (2017). Face Recognition Access Control System. Adman Technologies. Web.
Ballala, S., Sandjeev, Ch., Swetha, A. K. & Satyanarayana, I. (2016). Web-Based Online Embedded Door Access Control and Home Security System Based on Face Recognition. International Journal of Advanced Technology and Innovative Research Volume, 08(11), 2081-2083.
Smith, D. F., Wiliem, A. & Lovell, B. C. (2015). Face Recognition on Consumer Devices: Reflections on Replay Attacks. IEEE Transactions on Information Forensics and Security, 10(4), 736-745.