Introduction
The term “airport police system” refers to the procedures and tactics used to ensure customer safety. The safety system aids aviation officials in detecting any type of infiltration into the airfield. The material in the following paper will be utilized to present an excellent work strategy for an airstrip. The initial stage is to put together a powerful, competent, and determined management group that will strive to achieve optimal airport protection with the assistance of well-trained specialists. Second, in order to achieve optimum safety and management, the terminal needs to establish an aviation project. The port assures that all dangers are handled and addressed by building a cutting-edge surveillance system.
The airports have to make every effort to ensure that all structures are developed and configured properly. They are in perfect harmony and work tirelessly to acquire the highest degree of proficiency. The airline should also address the importance of managing and overseeing security processes. The requirement to develop a safety company for items sent by commercial airplane to the airfield is a necessity, and it necessitates a company structure to plan and implement internal risk assessment processes, as well as set the aims and range of the Flight Safety Committee. Senior management decides the functional group protection committee, which is in charge of creating safety initiatives and giving direction, guidance, and collaboration. The special commission will be obliged to take measures and provide the safety advisory board with comments and suggestions. Develop documentation, undertake risk appraisals, design and establish rules all at the appropriate time.
Security Force
Selection
To safeguard the safety of customers, workers, airlines, and electronic information systems, aviation security services should be established on federal and worldwide norms and policies. When choosing the optimal architecture, airport strategists and planners are heavily urged to examine the possible influence of shifting security issues and surveillance and security evacuation mechanisms on terminal infrastructure design. To ensure that designs allow the application of regional airfield and plane operator emergency measure standards, planners and engineers should work with aviation personnel organizers, flight crew, and Federal aviation security officials.
Organization
Project members, featuring airfield managers, terminal coordinators, municipal assistance agencies, and TSAs, will provide aviation protection services. The team can be established in these circumstances in collaboration with other institutions such as airports, intelligence services, freight and postal carriers, crisis intervention groups, anti-terrorist troops, and hazardous gadget law compliance authorities. The air travel expertise entails a slew of necessities that regions must address, including effective valid passport and border control, knowledge exchanging and the recognition of elevated travelers, security testing of individuals and cargo, worldwide anti-terrorism goals, and a slew of other interconnected priorities.
Training
Danger training is required for all trained security employees to obtain crucial and essential danger skills and knowledge to apply competitive abilities that assure excellent performance. To handle airport security problems, training is centered on education and awareness. Understanding that the armed services employs training as a crucial component in handling security risks is like recognizing that all protection professionals use it. Tactical training is vital because it allows soldiers to practice more effectively and in larger numbers across a larger area without causing undue inconvenience or placing others in danger. It is especially critical for all branches of training in which diverse components of the security services come together to collaborate and synchronize their movements.
Airport Layout
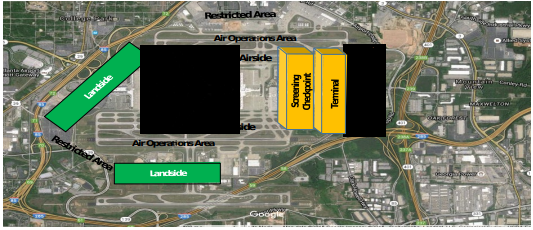
The major goal of this airline configuration is to create a system that would allow travellers to arrive at their destination in the least amount of time feasible by minimizing the overall time necessary for various customer and luggage operations before attaining the present value. Modifications in station design and airline processes are among the test options. In complement to idea research, numerical simulations are utilized to assess the solution’s practicality and quality. An airfield is divided into three sections: airside, inland, and terminus. The airside of an airfield is where airplane activities actually occur. The area of an airstrip and structures that both traveling customers as well as the quasi-public have unlimited access is referred to as the inland. The terminus is the third section and from a security point of view, airport terminal are normally separated into two different zones, known as airside and landside.
There is need to grasp what landside and terminus protection entails in order to get a decent knowledge and be able to evaluate the major factors of aviation safety for both terminal and landside security planning phase. The portion of the airfield that is available to the general public is known as the landside section. Community and worker parking spaces and structures, terminals and public highways, car rental and transportation services activities, hotel amenities, industrial and commercial projects are all examples of landside zones. The terminal is divided into two sections: landside and airside. From the standpoint of aviation safety, the two key goals in both landside and terminals safety design process are maximizing security operational effectiveness and passengers flow while reducing passenger pain and delay. The first focus will be security, given the existing terrorism concerns and worries, while also attempting to accelerate passenger movement. Because no two airports are the same in terms of size, extent, or nearby region, each must be uniquely designed.
All security requirements must be examined at the same moment as the desires on the airfield, its geography, and the capacity of the airbase, as well as the estimated annual passenger traffic. We must also examine the number of staff and the appropriate quantity of security officers necessary, which will vary according to the size of the airfield. Whereas the landside region is more difficult to guard due to its open nature, it does not require the same amount of security as the terminal and the airside sections. With cameras, roaming patrols, and number of officers, they is more readily managed.
To ensure strong security standards, the positions and amenities of landside structures and access routes will also have to be protected. The security standards for the airside region are more complicated since they encompass guarded zones where real airport operations are performed and only authorized staff may access them. The places where cargo is loaded, and also the flying line whereby aircraft taxi, board, and alight, are examples of these processes. Fencing, video recorders, motion detectors, roving guards, protected entry points, and security credentials are required to keep these places secure and segregated from the public at large.
The safety system in the terminals is a considerably more difficult condition to design. There are two components to the terminals that is the general sector where the wider populace is welcome to come and leave as they like. Only travelers and their baggage that have gone through police checkpoints, as well as approved airport workers, have entree to the antiseptic area. Passengers must go through a fairly regimented security process in order to obtain entry to this antiseptic section of the airport. The actual safety assessment of both people and their bags will be handled by skilled and well – trained scanners and safety officers. Elevated electronic devices, highly trained monitors, and other means will aid these staff in doing their tasks. Then we need to provide them with the resources they will need to do their tasks correctly. We must provide them with security checkpoint equipment, such as x-ray devices, to check through traveller luggage and check for suspected items which can be used to do damage. Deploy full-body detectors to check passengers seeking to board commercial aircraft for any weapons or questionable objects they may be transporting.
Due to the general spread of bombs used in terrorist acts, we also need to build chemical testing devices and have dynamite and narcotics detecting dogs on hand due to their high smelling skills. It is critical to have cameras that are continually watched all through the terminals. Designers must not lose focus of the reality that we must address the demands of the travelers who need to use these amenities, despite how much emphasis we place on security elements of airport services. Designers must remember that they must move through the procedure as quickly and comfortably as feasible. The surveillance procedure is necessary, but it must be carried out with competence and decency. That is why, regardless of how significant the tools and technologies are, and the human aspect is what makes all the difference. Security personnel and security agents must be skilled not just in spotting bad men, but also in treating passengers with respect and dignity.
Passenger Travel Process
The buying of a flight for plane flight starts with the acquisition of a flight and concludes with the traveler departing for their destinations.
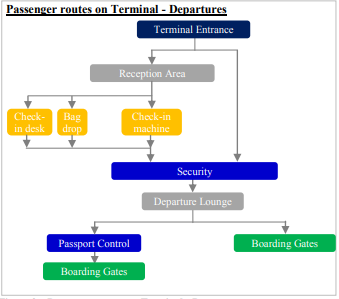
The customer pathways through the airport differ based on the traveler’s check-in type and whether or not they have checked luggage. Check-in booths, self-service devices, and the Web or online application are the three options for registering. All travellers wishing to take a flight must undergo a customer and hand examination. All international travelers are required to pass a boundary examination. Most terminals have a disembarkation hall, as well as shopping and recreational facilities immediately following security screenings. Before flying, one must show their identification documents and boarding permit.
Airport Arrivals
Passengers can choose one of two paths once a plane lands: change flights or exit the air base.
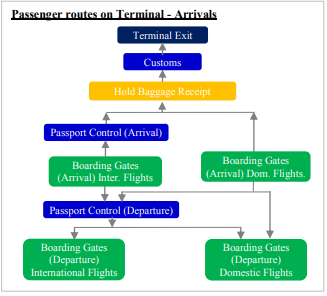
Baggage Routes in Terminal
There are numerous pathways in the station based on cargo categorization. Guests are responsible for their own luggage from the time they arrive at the terminal until they board the plane. Customer safety checks are used to manage hand luggage. Cargo storage options: At the reservation booth, inspect the traveler’s luggage. Luggage will be transported to the hold baggage claim area for safety checks once it has been verified. After going through the retain baggage area, the luggage enters the “Categorization” carrier, which transports the luggage to the sledding slope. When the luggage gets at the paratrooper, it will be placed into the tank and flown by plane.
Security Control and Facilitation
ICAO appears to have set two minimum requirements: “streamlining the procedure of entering and leaving the airports” and “profoundly improved air traffic control.” Because of the growing list of risks that have developed in current years, civil aviation security is continually changing. The essential security actions implemented by airlines after 11 September 2001 are the prohibition of beverages in proportions more than 100 ml of identified traveler networks (not simply metal scanning) and the installation of aircraft fortification in the entrances.
Travelers and high-risk visitors, according to IATA, should analyze risk assessments more thoroughly. Individuals are being studied more closely in order to identify bombs. They decided to obtain facial readers at terminals after the terrorist assaults on New Year’s Eve in 2009 to identify the threat evaluation of munitions, and the client procedure has been adjusted to be more dependable (Li, 2018). The following are the primary steps used to reach this goal: The service aims to cut airline operational costs (staff, office, and paperwork) while also allowing customers to access low-bandwidth aircraft terminals. Due to robotics personal service, the port is also trying verhard to create this procedure less reliant on employees and simpler for each customer to complete.
System for Screening Passengers
Everybody who wants to board a plane is obliged to pass through the security check. The passengers must first put their belongings in hand luggage’s such as such as purses and handbags. Aerosols, liquids and gels should be packed in a bag. Equipment such as phones, laptops and metallic objects such as coins and keys should be placed in a basket. Wearing large clothes such as the jackets, jewelry, hats is forbidden in the airport therefore they should be removed and placed in the terminals. Any form of luggage is then placed in conveyer belt for electronic scanning. The passengers should inform the in attendant officers if they have any form of medical objects such as implants or any other medical related equipment’s.
Through the Metal Detector
Passing the Geiger counter (portable) security checks can be chosen at random if they occur in all regions of the planet. It is possible that the safety analysis procedure may need to be rechecked until the issue is rectified. Other detecting approaches may be used. You can choose hazardous tests at chance after one have completed the feature choosing procedure. One can choose the explosion recognition test at random once the first selection step is completed.
Explosive Trace Detector
Travelers would be forced to undertake standard liquid, spray, and lubricant inspections on their hand bags prior to takeoff. It may potentially be deliberately chosen for Terrorist Detection (ETD) screening at this stage. The ETD assessment will be comparable to the one conducted at airport checkpoints in Queensland. After one has made a choice, the program will prompt one to remove any electronic objects in their wallet or purse. Sanitary products would be used to clean them, their handbags, and personal devices, which will then be examined for contamination. This procedure should take no more than 30 seconds.
Spot Screening Program
SPOT refers for Screening of Passengers by observation methods, and it is a program administered by the National Transportation safety board Administration in the United States. Its job is to spot possible terrorists among airport passengers using a list of 94 objective standards, many of which are symptoms of stress, anxiety, or deceit. To spot possible offenders among airport visitors, the bright spot employs a set of 94 factual measures. The requirements are separated into various segments, with numbers for every requirement in the “reported benchmark position.” Delayed flights, tensions, concerns, nervousness, hand perspiration, and piercing the chilly design, for instance, are only a few of the suspicions listed in the SPOT comparison report. The technology also has AI systems that have the capability of any suspicious movements.
Behavior Detection officers
Agents trained in behavioral detection, identified as behavior assessors, will be on the watch for questionable behavior and activities mostly around dedicated airline registration and gate locations. Consumers presenting appearances and conduct signals or behavior signs, as well as randomly chosen customers, will indeed be orally engaged by conduct Evaluators. Clients will be selected and questioned in an unpredictable manner by behavior evaluators. For the primary reporting SPOT, Psychosocial Investigators (BDOS) do extra inspections in accordance with the necessary criteria. The approach was successful in detecting people who were carrying illicit substances, guns, and other contraband. The behavior detection officers also act as protectors to protect passengers from being conned within the airport. They also act as guide to first time passengers in the port. As compared to electronic crime detection, human observers are more accurate and can reason out in situations that require cognitive ability.
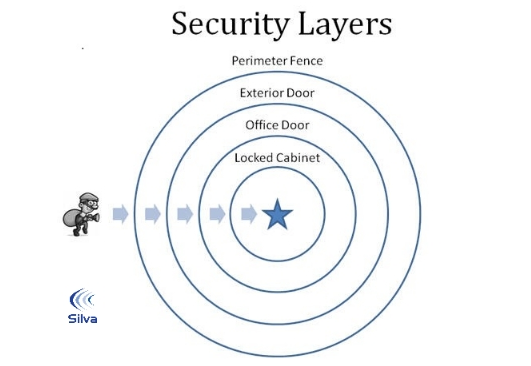
Concentric Ring Theory
To prevent attackers from entering the zone, the circular principle of physical safety necessitates the usage of numerous levels of protection measures. Several innovations may be employed to fulfill the corporation’s goal if the concentric zone hypothesis is used. The majority of them are centered on preventing complete confidence in one stratum while also spreading it to other layers. As a result, the assailant will have to pass it through numerous levels until it hits its destination (for example). The greater the security, the more strata the organization employs. Reaching the target as rapidly as feasible is one of the intruder hypotheses. The exact idea is used in concentric rings, but the duration and time intervals are increased. Those who possess exposure to tiers with varying rates at which invaders get to the objective will have varied authorization. In armed services notions, for example, admission to army barracks and other facilities is restricted. The issue is slowing down the rate at which illegal persons get access to locations they shouldn’t be.
The Federal Motor carrier safety Agency was founded in the aftermath of the “October 11” atrocities to ensure the integrity of the United States transportation industry (“Security, Transport Administration”). The TSA has implemented a tiered surveillance system with 20 distinct layers of safety to defend the air transportation system from possible terrorist assaults. A BDO is a defense system structure used by the TSA to defend terminals and airplanes from numerous terrorist activities and dangers linked to the SPOT.
System Integration for Maximum Security
In the field of airport screening testing, technological efficiency and socially acceptable remuneration are all mechanical advancements. Any alterations to recognized gateways for detecting metals would have more damaging consequences, as well as privacy breaches and reduced passenger safety. Most airports are intended to accommodate standard size airplanes if the spacecraft’s weight necessitates a bigger arm impact that may be disastrous not only for the hands but also for the effects of terminal degradation and other problems. More than one billion kilograms might have an impact on most airports’ present models. As per Caiba India Consultants’ homepage, the “‘ intelligent tag” may “transform the current logo, leading travelers through numerous parallel bilingual terminals without mingling, and can even give a touch screen, allowing guests to be controlled manually.”
The requirement for airlines necessitates technology development that not only expedites the assessment of photographic luggage but also reduces costs. The airline will create scanning and detecting solutions for munitions, firearms, toxic elements, biological devices, espionage, radioactive objects, and physical and biochemical warfare, among other things. Security systems can fulfill the demands of many businesses because to their flexible setup, effective design, and user-friendly interface. In a culture where customers are endangered by other technological activity, the customer experience is becoming increasingly safe.
CCTV system
Monitoring the air surrounding individuals or handling them to eliminate hazardous components from them rather than their belongings are examples of possible samples. A number of procedures can be used to identify the component of relevance. Visitors using sample procedures are unlikely to be concerned about the specifics of biochemical detection methods. The main security mechanism is the ability to contribute in its execution. The administrator is in charge of the protection system’s judgement call aspects. The capacity to engage in voice is a crucial aspect of accuracy. Determine whether or whether there are any possible threats to the airplane.
It is critical to incorporate technologies in order to collaborate in a prompt and effective manner. To begin, it is a video-based connection network that connects all safety actors interested in aviation security. In three regions of the runway layout, sound and motion sensor technology will necessitate the same sort of method, which will be controlled from a centralized point. So that any catastrophe scenario may be instantly identified and the appropriate response group can be contacted. The security people who watch and defend the culture are the most valuable commodity. We must improve our capability to send them to where they will be required the most. The most significant disadvantage is the continual change in flight.
When reviewers are really busy, they shade and take a seat, although in other locations, this activity has greatly risen. It is vital to sustain a constant flow of production due to the lack of steady and secure flows. When two or three foreign planes arrive, the terminal may see the requirement to move qualified personnel swiftly and efficiently by looking at the immigration gates. It may be used by employees, and there are methods for determining where and when they are needed. Simply set the mechanism up for in-person or online delivery. The solution will be to employ current technologies to assist the first sensor in conducting offsite diagnostic tests. They’ll be able to perform genuine traveler investigations and luggage examinations. How to assess customers based on known trends of behavior.
Access to Airport Operation
The committee proposed that the Government should speed its social factors programs to assist airplanes and corporations in incorporating physiological surveillance training into the development of quality assurance equipment, as well as inspecting travelers and advising personnel on safety checks. Establish an appropriate functional efficiency test to establish the best combination of capabilities in newly created systems, as well as studies in the fields of ergonomics, choice, orientation, and motivation for dynamite operators. Human controllers must be successfully integrated with the entire defense system in consumer transportation based on current or projected modern tools. This will allow travelers to transit through an airport at a quicker rate, resulting in not just favorable interactions with personnel but also action. Three major parameters have not been estimated after examining the elements of the technology after thinking and thoroughly comprehending its execution.
Air Carrier Safety Management
In the aerospace sector, there are several strategies to transfer commodities and customers from one location to the other. These are mostly path optimization ideas in the airline sector. These two extremely different perspectives on the customer service center: privatization of civil aviation, government interference of all air services, and a moment in time air system. The aircraft sector began to change once dynamic routing was deregulated. Today, practically all significant airlines employ a core radioactive system to attract customers and planes in every location where they function, both regionally and internationally, to use the axe pinion gears model.
The key result, according to the carrier, is that these facilities enable them to deliver greater and more regular trips for clients. The center and spread concept had become the standard for most international flights when the aircraft business was deregulated in 1978. Prior to liberalization, the national government recommended that the “connector” model utilized between two tiny airlines and multiple aircraft be half-empty, resulting in airline losses.
To link each country with its schedule and supply services, the Terminal must form agreements with other carriers. When dealing with large amounts of linked airlines, this may lead to tensions and competition for competitiveness. This is a breakthrough for regular business travels that can build distance while being comparable to numerous reductions with affiliate links or other possibilities, and intend to journey with the industry’s personnel, the issue is at their core.
The CNN story examined the coalition’s present capabilities and how partnerships with other carriers can help travelers give support during flights. “The partnership has built personalized terminals that serve most of the group’s activities at large ports such as Heathrow and Narita,” Snyder added. This could not be exactly you got in the main trip plans, independent of your contact with the other airplanes in the competition. These institutes, as well as the capacity to locate them, specify the proper path to take to reach the hub and destination of travel. One element that helps to Dubai’s growth as an air transportation hub is that protracted planes, such as that of the B777 and A340, may be linked to two anchoring locations from Sharjah to a destination.
Flights that operate on a moment in time basis, such as Terminals employ regional runways at its desired location under the mentoring paradigm. They discussed their objectives in the same way that travelers and the organization did. They often use, but they may also employ point-to-point systems. Planes play a critical role in global transportation, utilizing mentoring, center, and radio links. These flying concepts have grown so divisive that various airplane manufacturers have opposing viewpoints on their viability in the marketplace. The hub concept and radio, according to Airbus, control the aircraft sector.
Boeing built a Super A380 plane to back up his idea, claiming that the participant approach will triumph. Build a 787 biofuel that is both stylish and effective, and that is well suited to this industry. Both versions will, in reality, be employed in the business. They commute in a peer-to-peer method that takes them from their house to their location. Both techniques have benefits and drawbacks because the cubed and transmitter model represents the aircraft prior to flight, it should be employed.
The Federal Motor carrier safety Authority is requiring express and logistics businesses to assess 100 percent of their transportation cost under a Legislative statute. As a consequence of these efforts, the airline has been able to considerably alter the way, techniques, and efficiency with which items is handled, as well as the manners in which by-products significantly decrease the transportation of products. It is vital to improve the productivity of airfreight clearance procedures in order to expedite the processing while guaranteeing the greatest degree of safety feasible. Each item must be examined prior to entering the security and unloading area on the airplane, in contrast to technology that required maximum protection of the cargo being handled, stored, and carried.
Conclusion
Service quality may be improved by using fast-channel services. This kind is mostly found in international travel. This notion serves to increase the competitive advantage of air travel in locations where HST seems to be well supplied (which is not the case in Lisbon) when planning terminal and airport programs, keep the solution in mind. Passengers should take their bags to the aircraft’s entrance and the baggage to personnel in the basement as a solution to the crisis. This “quick route” service will take the place of other passengers (regular passengers) for security screening. Fast travellers pass immediately through to the “Fast Track3 Connector” stream after passing through safety. The simulation software was used to apply the alternative situational analysis at the Lisbon terminal building, which found that the effective service delivery is helpful to frequent travelers.
References
Bhandari, B., & Park, G. (2020). Development of a real-time security management system for restricted access areas using computer vision and deep learning. Journal Of Transportation Safety &Amp; Security, 14(4), 655-670. Web.
Dobruszkes, F. (2021). A global business? Mapping the densest passenger airline routes.Journal Of Transport Geography, 92(35), 102-941. Web.
Issa, K., Pierce, T., Gwam, C., Festa, A., Scillia, A., & Mont, M. (2017). Detection of total hip arthroplasties at airport security checkpoints – how do updated security measures affect patients?. HIP International, 28(2), 122-124. Web.
Kleiman, A., Cohen, I., & Berdugo, B. (2021). Constant-beamwidth beamforming with concentric ring arrays.Sensors, 21(21), 52-53. Web.
Li, X. (2018). Airport simulation technology in airport planning, design and operating management.Applied And Computational Mathematics, 7(3), 130-132. Web.