Introduction
The modern society could be characterised as the digitalised one. The rapid development of technologies along with the reconsideration of traditional methods cultivates a new way of thinking that includes the extensive use of digital devices to attain improved outcomes and facilitate the shift of priorities towards diverse, innovative practices. That is why computers become an integral part of almost all current organisations functioning. Development of particular software designed to encompass all operations and align their cooperation acquires the top priority. The same processes can be observed within the aviation sphere.
At the moment, it plays a fundamental role in the further evolution of the society and cultivating globalisation across the world (Cromie et al. 2015). It also offers numerous transportation services to passengers, companies, and governmental agencies. In this regard, the implementation of innovative practices and computers are crucial for the sphere as it enhances efficiency and contributes to better results. However, further digitalisation of the aviation industry and empowerment of technologies might become a two-edged weapon which gives rise to numerous security concerns stipulated by hackers attacks. In general, the issue of cyber security becomes central for the modern world and aviation sphere. For this reason, leading agencies that regulate the functioning of aviation around the globe like the International Civil Aviation Organisation (ICAO), Airports Council International (ACI), the Civil Air Navigation Services Organisation (CANSO), and the International Coordinating Council of Aerospace Industry Associations (ICCAIA) agreed on aligning their actions on cyber threats to eliminate potential vulnerabilities and guarantee security to passengers and cargoes.
Background
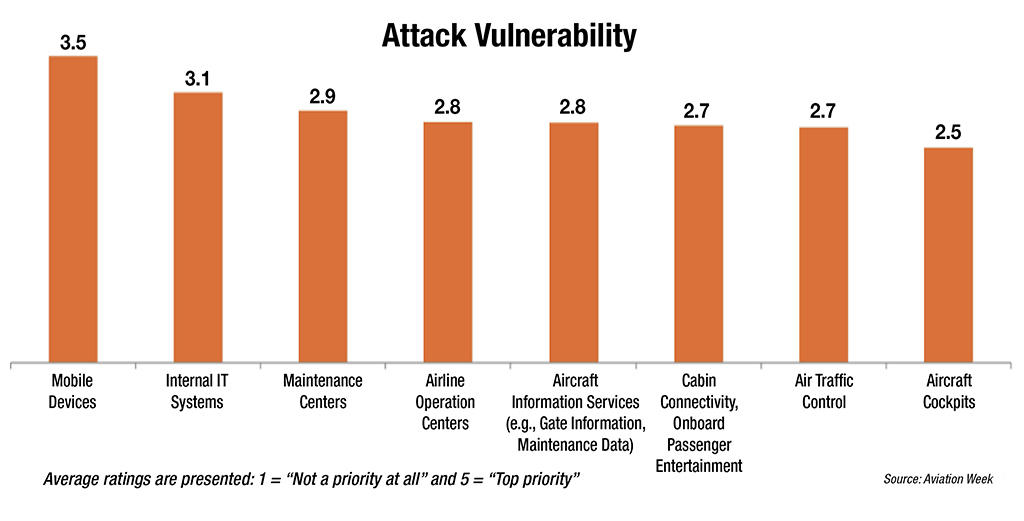
Drastic alterations in the working environment preconditioned by technologies also introduced numerous vulnerabilities and potential threats (see Figure 1).
Moreover, the tendency towards the increased sharing of crucial information to guarantee the efficient functioning of the aviation sphere opens up the potential for cyber attacks (Ferguson & Nelson 2013). The implementation of next-generation systems deteriorates the situation and creates new vulnerabilities because of the increased use of digital devices and growing demand for various pieces of data. Regarding these facts, the issue of cyber security obtains the top priority as one of the leading methods to protect the sphere of aviation and eliminate all vulnerabilities that will undoubtedly appear when implementing new technologies. Therefore, it could be defined as a set of tools, concepts, systems, guidelines, approaches, practices, and technologies that are developed and used by organisations to protect their cyber environment and its users from hacker attacks and guarantee a stable functioning of a particular software (Hall 2015). Due to the rapid evolution of digital devices, cyber security also evolves and acquires new features related to the aviation industry. At the moment, it encompasses a wide array of tasks and responsibilities to guarantee the comprehensive investigation of the environment and improved threats detection.
Risk Assessment
The majority of modern strategies created to protect a cyber environment could be considered three-pillar ones as they try to understand, define, and assess all threats and risks that might appear because of cyber attacks (see Figure 2) (IATA n.d.). These three-pillar strategies demonstrate the increased efficiency in terms of airports complex setting as they delve into the majority of fundamental factors. Risk assessment becomes one of the critical activities that create the basis for the implementation of a potent security system. Therefore, ICAO, IATA, CANSO, and ICCAIA agree that this aspect should be given significant attention to develop a particular framework (CANSO 2014).
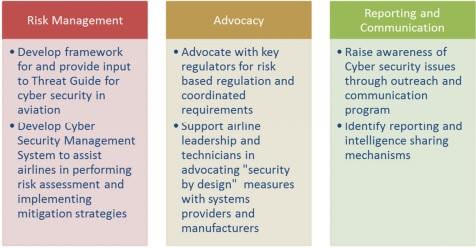
The enhanced risk assessment practice could also help to eliminate all vulnerabilities before a potential attack and minimise a chance of a thriving intrusion. Under these conditions, the following classification of threats to improve their management is suggested: intentional or unintentional; targeted or non-targeted (CANSO 2014). There is also an attempt to define a risk regarding its source: foreign nations engaged in information and economic warfare; hackers, terrorists, virus writers, former employees, etc. (ICAO 2016). However, all these risks might result in serious failures or system collapse as the airline industry relies on computer systems extensively and considers them the basis for its further evolution (Krause 2003). Under these conditions, all modern airline companies implement robust systems to assess risks and hacking threats (Price 2013). At the same time, they lack cooperation and have not accepted a holistic approach to the existing digital environment to realise the global problem of the issue (CANSO 2014). The agreement mentioned above should solve this problem by suggesting a universal method that fosters cooperation.
Threats and Vulnerabilities
As it has already been mentioned, there are diverse threats that might impact the functioning of both ground and air services and result in numerous failures. Additionally, along with the classification that rests on the type of source and character of threat CANSO suggests consideration of the motivation of international actions as one of the crucial components of risk assessment (CANSO 2014). The degree of cyber attack preparation determines the level of threat (see Figure 3) and demands specific actions to protect the system and respond appropriately.
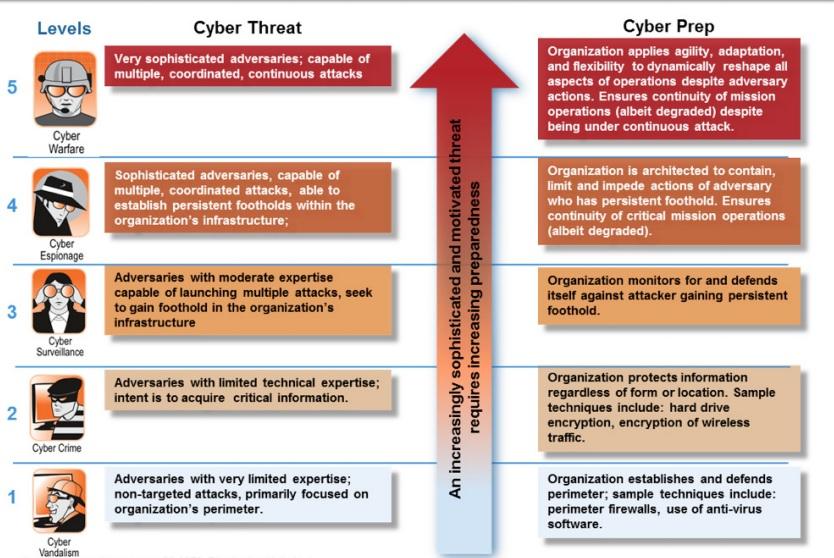
For instance, if an attack is organised by an international organisation which devotes much attention to all its aspects, it could be considered a very sophisticated attempt which is capable of multiple and continuous malicious actions (CANSO 2014). In general, the range of threats is extremely broad and continues to grow (Rankin 2010). Attackers could use diverse resources and approaches to achieve their goals and harm organisations. That is why the existing problem could not be solved by a single agency or a single solution (Raphael 2013). The above-mentioned variety of threats demands the corresponding diversity of actions performed to protect organisations and people from and potential interventions. It also means that to face all challenges that appear and create the safe environment agencies should engage in a long-term cooperation to build increasing levels of information system security.
New Cybersecurity Agreement
Regarding the gradually increasing cyber threat and the need for immediate actions to cooperate efforts and eliminate vulnerabilities, in December 2014, the International Civil Aviation Organisation (ICAO), Airports Council International (ACI), the Civil Air Navigation Services Organisation (CANSO), and the International Coordinating Council of Aerospace Industry Associations (ICCAIA) agreed on aligning their respective actions on cyber-threats to create a Roadmap related to this problematic issue (Civil Aviation Cybersecurity Action Plan n.d.). The Civil Aviation Cybersecurity Action Plan became a fundamental document to foster international cooperation aimed at the creation of the safe environment along with the further improvement of protective systems, approaches, and practices. Another important goal of the document is to “prepare civil aviation against future challenges from cyber threats” (Civil Aviation Cybersecurity Action Plan n.d., p.1). It means that ICAO, ACI, CANSO, and ICCAIA will share their perspectives and visions on the question to create the most efficient common approach which will cultivate shifts towards new more efficient solutions and practices. The Roadmap created by these organisations include fundamental aspects that acquire the top priority:
- elaborate a common perspective on cyber threats
- share risk assessment
- agree a common language
- outline specific recommendations
- present to the public a new joint approach
- promote cooperation among state-level authorities and industry to establish coordinated aviation cybersecurity policies.
- promote a robust cybersecurity culture
- promote the use of current security measures
- establish mechanisms to share information
- ensure situational awareness
- refine best practices (Civil Aviation Cybersecurity Action Plan n.d., pp. 2-3).
Measures
Common Perspective on Cyber Threats
Therefore, the given list describes a scope of actions needed to promote significant alterations in the aviation security and guarantee its improved functioning. Thus, the first point that introduces the necessity of the creation of a joint perspective on cyber threats could be considered fundamental for the further cooperation between agencies that signed the Plan. All actors should have same views on the current situation and its further evolution to be ready to act together and improve aviation industrys ability to resist threats and guarantee safety to passengers. Therefore, the given measure should also be considered as a critical one because of its impact on the further evolution of the sphere. The attempt to create a common approach and unite to resist high pressure that comes from hackers or other attackers is essential for the further growth of the industry and its enhanced security (Civil Aviation Cybersecurity Action Plan n.d.). In the long-term perspective, organisations will continue to review and communicate threats to preserve the high level of awareness and be able to respond immediately.
Shared Risk Assessment
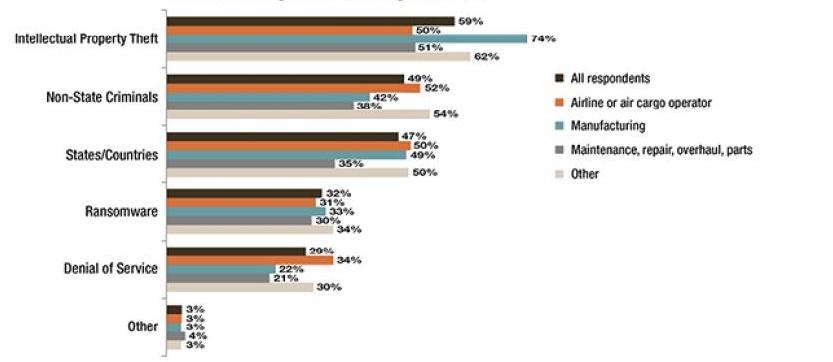
Sharing risk assessment is another practice that is outlined with the hope to eliminate vulnerabilities and address existing threats to the airline industry. The fact is that every agency has its approach to identification of leading attacks objectives (Tamasi & Demichela 2011). It considers the frequency of peculiar problems occurred in various spheres (see Figure 4).
This attempt to structure risks and provide reliable statistics has a positive impact on assessment practices. However, convergence in approaches might deteriorate final results. The above-mentioned action plan suggests elaborating a unified strategy that compares risk assessment processes from different stakeholders and creating a platform to share knowledge related to this issue (Civil Aviation Cybersecurity Action Plan n.d.). It will evidently result in the enhanced ability to respond to the major risks by using experiences acquired by other agencies (Singer & Friedman 2014). Altogether, the given measure becomes extremely important regarding the tendency towards the appearance of new threats as leading agencies will provide their knowledge to less prominent ones.
Common Language
Next, the cooperation between the ICAO, ATI, CANSO, and ICCAIA introduces the need for similar terminology for actors to understand each other. In accordance with the relevant statistics, misunderstandings between various airline companies due to the differences in terminologies or methods remains one of the significant causes of failures or security threats (Tamasi & Demichela 2011). In this regard, promotion of existing and unified standards and frameworks might decrease the number of threats that appear because of misunderstandings and different perspectives on the same issue. Therefore, ICAO suggests a particular guidance material for the creation of a specific glossary that should be used when creating a framework to struggle against numerous threats (Civil Aviation Cybersecurity Action Plan n.d.). This guide encompasses a wide array of experiences, competencies, pieces of data, and approaches acquired by the organisation due to the enhanced risk assessment and management. The use of this unified guidance material is an efficient measure to increase awareness related to the most topical threats and introduce methods to eliminate them within a particular airport and across the world.
Specific Recommendations
The following offering is closely connected to the previous one. The plan presupposes the development of “joint prepositions and recommendations”( Civil Aviation Cybersecurity Action Plan n.d., p. 2). It means that the central agencies accept the responsibility of identifying the key areas where regulation is emerging and offer a particular set of measures that could help to create an efficient framework deprived of potential vulnerabilities. The proposals also include the aim of providing input to the development of standards and practices that will be included in the guidance material which has already been mentioned. It could be considered a potent method that introduces radical alterations in the way airline companies function (Abeyratne 2016). The use of shared experiences and knowledge promotes the creation of a new environment free of vulnerabilities noted by agencies in their previous risk assessment procedures or faced by some companies in their practice. Knowledge is one of the most powerful tools of the 21st, century and the given measure suggests its accumulating to improve the situation in the sphere.
New Joint Approach
One should also realise the fact that the outlined scale of changes could not remain unnoticed by the public. For this reason, it is essential to present people with the consistent and efficient approach to managing leading threats that appear due to the evolution of technologies and science. The given task becomes crucial regarding a significant role media plays in the majority of modern processes. Every event or accident might deteriorate the image of the aviation sphere and cultivate wrong concepts among the population. For this reason, the plan introduces these measures to attain increased peoples understanding of the main actions performed by agencies to protect them from all hazards and threats. Under these conditions, relations with publicity become an essential aspect of the suggested set of operations as it ensures the high level of awareness among passengers and their ability to evaluate the situation critically and act most appropriately.
Cooperation Among State-Level Authorities and the Industry
Therefore, aviation is closely connected with governmental authorities as it is an important strategic tool that could help to perform numerous complex transportation tasks. At the same time, the evolution of the industry is impossible without the support provided by the state-level authorities. In this regard, promotion of cooperation among state-level authorities and industry to establish coordinated aviation cybersecurity policies is the central task outlined in the plan. Considering the scope of current threats and actors who might be responsible for the organisation of attacks, only the state-level authorities could help to struggle with threats and eliminate vulnerabilities. Therefore, states which cooperate with ICAO, ATI, CANSO, and ICCAIA should also sign the suggested act to ensure that all its statements will be observed. This measure becomes extremely important to promote the cooperation across the globe and foster relations between governmental authorities to attain improved results and guarantee safety both to passengers and cargoes.
Robust Cybersecurity Culture
This intention correlates with another task outlined in the plan which is to promote a robust cybersecurity culture (Civil Aviation Cybersecurity Action Plan n.d.). Numerous investigations of the sphere emphasise the fact that the tendency towards the appearance of new cyber vulnerabilities and threats along with the growing role of aviation in the modern world demands a completely new culture to manage risks and realise the probability of their further appearance (Abeyratne 2016). That is why ICAO, ATI, CANSO, and ICCAIA demonstrate their intention to provide guidance on implementation of new strategies and methods to protect the IT sector and software used by airports to regulate their functioning. Implementation of these measures ubiquitously means the cultivation of a new culture which is needed to mitigate a negative impact of malicious hackers attacks and ensure the efficient functioning of all processes needed for any airport to work without failures that might become crucial regarding the nature of the sphere.
Use of Current Security Measures
All these actions are introduced with the primary purpose to promote the use of current security measures to guarantee the increased level of cyber protection and ensure that passengers will not suffer from numerous threats to their security. The agreement between four leading agencies that regulate the functioning of the aviation sphere will stipulate a radical shift of priorities towards the use of innovative practices outlined in their recommendations. Regarding the rich experience they possess in this field, this step will evidently result in the promotion of innovative cybersecurity measures globally and elimination of vulnerabilities that remain unnoticed by other companies or agencies because of their poorer knowledge or experience.
Mechanisms to Share Information
However, ICAO, ATI, CANSO, and ICCAIAs officials correctly realise the fact that the further development of top security measures is impossible without efficient mechanisms of data sharing and threats identification. This framework is fundamental for the stable functioning of the sphere as different agencies across the globe face diverse vulnerabilities and acquire experiences how to overcome these hardships. Regarding existing globalisation trends, migration and spread of attacks could be predicted. Under these conditions, the given measure is essential for the creation of a unified approach to struggle against malicious interventions performed by organisations or individuals with the main aim to harm the aviation sphere and create a flap both among passengers and organisations.
Situational Awareness
Situational awareness is also considered another crucial element of Civil Aviation Cybersecurity Action Plan and should be cultivated to achieve the main goals. Thus, it helps to remain informed about the most topical issues and coordinate responses to any potential threat that might appear in nearest future (Civil Aviation Cybersecurity Action Plan n.d.). In general, it is a potent tool that establishes an efficient framework needed to introduce fast and efficient responses to any emergent situation. This method will cultivate even more systematic coordination of actions performed by agencies in terms of their attempts to eliminate existing threats and create an outstanding protection system that will help to preserve a safe environment.
Refining of the Best Practices
Finally, the last goal outlined in the plan is the refining of the best practices that are used at the moment to preserve their efficiency and create the basis for their further evolution (Civil Aviation Cybersecurity Action Plan n.d.). It also includes cooperation between all stakeholders to ensure that only innovative practices are implemented across the industry. The given task demands a significant commitment from all parties. Moreover, the constant upgrading of technologies used in the sphere is also an essential step that stipulates significant technological advance and guarantees that organisations will be able to meet all challenges that might appear.
Conclusion
Altogether, the suggested Civil Aviation Cybersecurity Action Plan should be considered a potent attempt to improve the situation in the aviation sphere and protect airline companies from malicious attacks performed by organisations or individuals. It presupposes specific measures to create the efficient framework that will help to share data about potential threats and cultivate a new security culture needed to protect passengers and cargoes. Analysing these approaches, their focus on the further evolution of the sphere should be admitted. ICAO, ATI, CANSO, and ICCAIA correctly realise current trends related to cybersecurity and warfare and try to create the basis for the enhanced global cooperation along with the implementation of new technologies.
Reference List
Abeyratne, R 2016, Rulemaking in air transport, Springer, Montreal.
CANSO 2014, CANSO Cyber security and risk assessment guide, Web.
Civil Aviation Cybersecurity Action Plan n.d., Web.
Cromie, S, Ross, D, Corrigan, S, Liston, P, Darragh, L, & Demosthenous, E 2015, ‘Integrating human factors training into safety management and risk management: a case study from aviation maintenance’, Proceedings of the Institution of Mechanical Engineers, Part O: Journal of Risk and Reliability, vol. 229, no. 3, pp. 266-274
Ferguson, M & Nelson, S 2013, Aviation safety: a balanced industry approach, Delmar Cengage Learning, Clifton Part, NY.
Hall, R 2015, The transparent traveller: the performance and culture of airport security, Duke University Press Books, Durham, NC.
IATA n.d., Fact sheet. Cyber security, Web.
ICAO 2016, Safety report, Web.
Krause, S 2003, Aircraft safety: accident investigations, analyses, & applications, McGraw-Hill Education, New York, NY.
Price, J 2013, Practical aviation security, second edition: predicting and preventing future threats (Butterworth-Heinemann homeland security), Butterworth-Heinemann, New York, NY.
Rankin, W 2010, ‘General aviation security: a safety management system model for collegiate learning’, Journal of Aviation/Aerospace Education & Research, vol. 19, no. 2, pp. 35-44, Web.
Raphael, R 2013, Airport security: a national security challenge, German Marshall Fund, Washington, DC.
Shay, L 2016, Ranking commercial aviation’s cybersecurity priorities, Web.
Singer, P & Friedman, A 2014, Cybersecurity and cyberwar: what everyone needs to know, Oxford University Press, Oxford.
Tamasi, G & Demichela, M 2011, ‘Risk assessment techniques for civil aviation security’, Reliability Engineering & System Safety, vol. 96, pp. 593-599.