Introduction
Brisbane Savings and Investment Bank (BSIB) have developed to be a major player in banking industry in Australia. Although relatively new having been established ten years ago, the bank has experienced a fast growth rate. Due to good business environment, the bank was able to expand its domestic operation by increasing the number of branches.
The bank currently has branches in all major towns and cities in Australia. BSIB still maintains its Head Office in Brisbane major operations are based. Among the major operations at the Head Office include Retail Banking, Internet Banking and Business Banking. Retail Banking focuses on management of branches, customer accounts, loan and mortgage and cards.
On the other hand, internet banking sector deals with managing online customers and online banking products. Business banking focuses on managing business based accounts, loans and mortgages and overdrafts. Apart from the Head Office, BSIB has another major office in Adelaide.
The major operations based at Adelaide office include Institution Banking, Superannuation Products and Insurance Products. Operations in foreign exchange, hedge funds, share trading and bonds are managed from this office under Institution Banking. The office is responsible for management of insurance products such as life insurance, land protection, home and contents insurance.
BSIB has experience rapid growth over the last ten years. When it started ten years ago, the bank had 1000 employees. The number of employees has increased with increased operations and it currently stands at about 17000.
Computers and computer based information systems are integral part of every organization in modern days. Information system in an important resource in any organization and has significant contribution to an organization’s productivity. In order to integrate the use computers and computer based systems effectively, an organization must exercise control over these important resources (Hall & Singleton, 2005, p. 39).
Although computer systems have positive contribution on productivity and efficiency, cost of irregularity and errors that may develop in the systems may have very severe effect on an organization. Control is essential in order to enable an organization to avoid or mitigate the negative effects.
An organization can be affected severely by destruction or corruption of its database; data and information loss, loss of computer assets; effect of computer abuse; ineffectiveness of some computer systems and overall way in which computers are used within the organization.
To avoid or mitigate negative effects that can result from use of computers and computer systems, information system auditors have become necessary. Information audit have become essential in order to enable an organization find gaps between its IT policy and usage and deficiency in information system design, results and usage.
Information System Audit has become very essential with increased use of information systems. It entails gathering evidence which aids in the determination of whether a given computer system meets the required data integrity. In addition, it ensures effective utilization of resources. This increases the probability of an organization attaining its goals. Information System auditors not only ensure that there is adequate internal control on information system but they also ensure that the systems achieve their objectives.
The IS Auditor should see that not only adequate internal controls exist in the system but they also wok effectively to ensure results and achieve objectives. Audit should ensure that internal controls implemented are proportional to assessed risk in order to reduce the identified risks to a health level. They also need to assess adequacy of internal of internal control in mitigating IT related risks.
Information system has an important place in BSIB growth plan. The banks operations are fully computerized form normal baking operations to human resource management. Failure of information system can therefore have negative impact on the bank and affect its competitive advantage in a highly competitive environment. Auditing services for BISB for the last ten years have been provided by an external auditing firm. An audit team of six auditors have been responsible evaluating the organization’s IT systems.
External auditors’ audit services however have been at a high level. BSIB executive management feels the need for more detailed audit and has proposed to establish an internal audit team. The internal audit team has the mandate of conducting a detailed audit of the major processes of the bank, business operations, databases, systems, application, IT security and general business and IT management.
IT Environment
ACL Software
Audit Command Language (ACL) Software is one of the audit software packages. It is the most popular and common audit package followed by IDEA (Interactive Data & Extraction & Analysis). The software is used to help audit process in an organization. The software play significant role in supporting financial statement audits.
ACL helps auditors to be more efficient when conducting their roles. The package has become very important as electronic environment becomes more standardized. Using ACL auditors can be able to obtain important information for evaluation as well as simplify data processing. The software is an effective tool to data extraction and analysis therefore making it easier to perform information system audit.
BSIB will be using ACL software to extract and analyze information from its information system. Auditing the bank’s information system without the help of a program would be challenging. The company has complex IT environment with a lot of processes, data and information supported by the system.
By using the program, the auditors will be able to extract the information they require, analyze the information and be able to make appropriate recommendation. By using the ACL software, the auditors will be able to take less time to conduct their audit, cause less disruption to normal working of the bank and be able to obtain more reliable result.
ACL uses queries to obtain information from extract information from information system. BSIB has a wide IT environment. The organization used information technology to carry out most of its function. ACL queries could be prepared and used to extract data and information from the system.
Queries could be prepared to obtain information on how the organization’s resources are used. Information system is very important resource to BSIB. Auditors need to obtain information on how the resources are used in order to verify whether they are used for the good of the organization. Apart from obtaining information on how the organization’s resources are used, queries could be prepared in order to obtain information on effectiveness of the system in meeting the organization’s objectives.
The organization’s IT environment comprise of various system to make up the overall system. For instance, queries could be prepared in order to obtain information on effectiveness of ERP in managing the bank’s human resources. Variables to effectiveness of an ERP should be identified in order to assist the auditors to prepare appropriate queries.
Appropriate queries are required in order to obtain the appropriate information from the bank’s information system. Before preparing queries, the auditors must identify the king of information that they require from the system. After identifying the data that they require to extract from the system, the auditors should outline the design of their queries. The queries should outline the variables that would be used and the way the data would be obtained.
After preparing the design, the auditors would then prepare the queries using ACL command. This would call for detailed knowledge on how to use ACL. An individual with technical knowledge on ACL software would be required for this process. ACL will help the auditors to identify various issues of interest.
Through ACL software, the auditors will be able to point out activities and control weaknesses that can compromise the organization from meeting its objectives. Auditors will be able to identify data integrity, security, physical environment security, system efficiency and management continuity (Piattini, 2000, p. 107).
The software will enable the auditors to identify weaknesses in input control, access control and data integrity. The software will enable the auditors to get information on how the server is used and management. They will be able obtain information on disaster recovery situation of the organization.
The information system has various components that have to work together for the overall goals and objectives of the organization. The ACL software will enable the auditors to obtain information on how well the various components work together. It will enable them to identify weaknesses in the whole system and pinpoint the areas that would require to be reviewed.
Concern for Audit and Control
Information systems are a major resource at Brisbane Savings and Investment Bank. Most of the activities in the bank are carried using computer system. The bank’s success therefore depends highly on effectiveness of information system. Various risks associated with information such as data loss, abuse, and data integrity can compromise the bank’s performance. The bank has grown at a high rate in the last ten years.
Starting in Brisbane ten years ago, the bank has been able to establish branches in almost all major cities and towns in Australia. Because of size of the bank’s operations, it is not possible for the management to exercise control over each and every activity. The bank’s employees have been able to increase from a thousand ten years ago about seventeen thousand currently.
Managing the large size of staff could be challenging without the help of information system. To ensure that the information system is used effectively to help the organization meet its objective, auditing is essential. Information system auditing would help the organization to identify weaknesses in the system and therefore help the organization take the appropriate corrective measures. Auditing would also ensure the computers and computer systems in the banks are used in the intended way and for the benefit of the organization.
Role of Internal Audit Group
BSIB has been relying on external auditors to audit its resources including information system. The executive management however feels that the external auditors are not adequate. The external auditors are not able to conduct detail audit since their audit is mainly at high level. Internal audit group is essential for the organization in order to conduct a thorough audit of the organization’s resources.
Since internal auditors are centered at the organization, they will be able to conduct more detailed audit and therefore help the organization gain better control of its resources, be able to identify weaknesses in the system and take appropriate and timely corrective measures.
The main functions of the Internal Audit Group will include verifying whether computer and computer systems are used appropriately, verify where security issues are in order, ensure security of physical environment of the information system, verify whether there is appropriate input and access control and audit effectiveness of information system in meeting the organization’s objective (Dube & Gulati, 2005, p. 72).
Information system has great impact on the other auditing conducted in the organization. The information system is used for most of the banks activities. All other auditing therefore is influenced by the information system auditing. The information system holds most of the organization’s data and information.
The organization’s databases have data and information on how other resources in the organization are used. They contain financial information, information on human resource and other important information. Information system audit therefore have great impact on the other audit.
Components of Internal Audit Group
Internal audit is important for BSIB to exercise successful internal control. For internal control to be successful, the Internal Audit Group must be well composed. It should contain individuals with appropriate qualifications but above all, they should be able to work together as a team. The internal audit group would be comprised of team of well trained qualified staff drawn from various departments in the bank.
The team will be led by an Audit Team leader. To ensure cooperation within the team, the Audit Team Leader will play a significant role in identifying members to the internal audit team (Dube & Gulati, 2005, p. 67). Retail Banking, Internet Banking, Business Banking, Institutional Banking, Insurance Products, and Superannuation Products should be represented in the internal audit group. Audit team may be subdivided into business audit and IT audit, each headed by an audit leader.
Five audit team leaders will be involved, each heading an audit team. 35 internal audit group members will be required. The members will distributed among the audit team depending on workforce. The personnel working as auditor should have obtained sufficient training in the prerequisite on internal auditing techniques. To qualify, internal audit group members should have completed an internal audit course offered at a recognized third party.
Members may also receive training by a personnel having successfully completed internal audit course and also having adequate experience in practice (Cascarino, 2007, p. 132). The audit group must demonstrate high level of integrity and professionalism in their practice. Audit Plan is essential for successful internal audit. Using the Audit plan, the auditors will be able to identify priories and establish strategies for meeting auditing goals.
Importance of identifying Risks and Controls
Successful Internal Audit begins with a successful identification of risks and the controls involved. Identification of risks and control play a significant role in preparation of Audit Plan and therefore has important role in determining the direction of an audit (Cascarino, 2007, p. 117). Risks and controls enable auditors to set priorities for their audit process.
Various risks and access issues have to be considered in BSIB audit. Physical risk such as system failure and theft are involved. For example, the bank’s server room is poorly ventilated therefore exposing the server to physical failure. The server room is also accessible to employees and visitors therefore exposing the system to several risks such as theft, physical and internal tampering.
Controls are necessary in order to ensure that information system works effectively. The auditors should identify the available controls. The controls would give the auditors a guideline on how to carry out their duties and help them identify weaknesses in the system more easily.
Detection of Risks at BSIB
There are various ways which are used in detection and control of risk at BSIB. Inherent risks refer to vulnerability of an audit area to errors that could be significant individually or in combination with others. They occur where necessary internal control is lacking. Control risks refer to errors that could be significant either individually or in combination with others considering that the errors could not controlled by internal control.
Various inherent risks are involved within the banks IT system. Group data warehouse is used by all applications using a common interface. This can lead to errors in case of failure. The bank’s server room is accessible to all employees and visitors without control. The server room is also poorly ventilated therefore exposing the system to possible failures. Some of controls risks involved include use of outsourcers to offer IT services.
The IT infrastructure is managed by an outsourcer whose location is currently not well known. Mortgage/loans products, insurance and superannuation products are also management by outsourcers. Although these are possible sources of error, the internal control may not be able exercise absolute control.
Information System Risks at BSIB
BSIB information system environment is prone to various risks. Some of these risks are outlined below.
- Physical risks
- Controls risks,
- Security risk
- Data integrity
- Performance risks
IT infrastructure of the bank is managed by an outsourcer whose location is not well known. This poses the banks to possible risks in case the bank losses track of the IT service provider. Access to sensitive IT resource is not well controlled. For example, access to the banks servers is open to all employees and visitors therefore exposing the bank to risk. The server rooms are poorly ventilated therefore exposing the servers to possible failure.
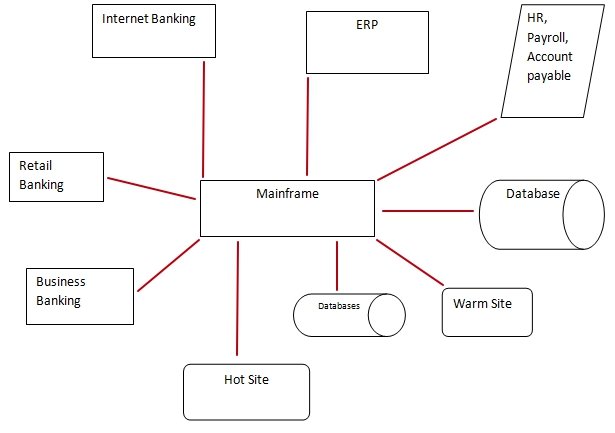
All the data in the bank is interfaced to the mainframe at real time. This can lead to bottle-neck especially during peak hours raising some data integrity issues. Various applications used to manage various processes such as Syst-Tell, Bus-Bank, Cust ID and Trade-FX are add-up application. The application can lead to scalability and efficiency issues as the bank’s operations increase. Data integrity is a major issue at BSIB. Integrity of data inputted into the bank’s ERP is not certified by the necessary authorities.
Common Information System Risks
Information system auditing is essential in order help an organization indentify risks and take timely corrective measures (Piattini, 2000, p. 92). Organization security is the most important information system risks considered in information system auditing. An IS auditor should ensure that an organization has well defined policy to ensure security its information system.
Information system resources are vital to an organization. An auditor should verify that the IT assets declared in an organization’s policy are actually existent on the ground. Employees and other individuals using information system can contribute to IT System risks. IT system users should be aware and adhere to laid down security policy. Other risks include physical or environmental security, operational management, business continuity and compliance.
Various measures should be taken to mitigate the information system risks. An organization must develop and maintain an IT policy to provide guidance on the way IT resources are used (Hall & Singleton, 2005, p. 68). There should be proper access and input control to manage the way data is inputted into the system and the manner access is allowed. Authentication policies such as accounts and password controls are necessary.
Audit Methodology
Appropriate audit methodology is necessary for a successful information system audit. Key areas in an information system audit consist of audit planning, risk assessment, performance of an audit work and reporting (Cascarino, 2007, p. 87). Adequate planning is necessary before conduct. During planning, the purpose of the audit will be stated clearly. Various requirements for the audit would be identified and appropriate preparation made.
The responsibility, authority and accountability of the auditors are defined during this stage. Planning involves also identification of essential resources including members of the audit members (Weber and Jamieson, 2008, p. 95). Risk assessment is the second stage in information system audit. In this stage, possible risks in the information system are evaluated in order to provide the auditors with direction to follow in their audit.
After risk assessment, the actual audit work is conducted. Audit work depends highly on audit planning and risk assessment. Using risk assessment results, the auditors develop audit plan or program that would be used for auditing. Reporting is an important step in auditing methodology.
After conducting the audit test, IS auditor is expected to prepare and present appropriate report that communicate the outcome of the information system audit. The audit report includes findings from the audit, conclusions and recommendations. The reports may also include reservations that auditors have on their audit, qualification and limitations of the IS audit.
Communication in Information Auditing
Communication is a very important element in auditing. Good communication is required in obtaining information as well as communicating the results to the appropriate authority. Information System auditors work as a team. The outcome of audit process is not an individual effort but collective effort from all the audit team members (Weber & Jamieson, 2008, p. 65).
Proper communication framework is therefore required in order to enable the members to share information and thoughts as they carry out their duties.
Apart from communicating among themselves, Information System auditors need to collaborate with other employees in an organization in order for them to obtain the necessary information that they require. Information system auditors need to communicate the results of their audit to the necessary authority. Reporting and other ways of communication should therefore be streamlined.
Information Systems Audits BSIB IT Environment
Information system audits are required in BSIB IT environment. Areas of high risks should be given more emphasis during the audit process. An audit is required to assess the services provided by the IT outsourcers. Management of the organization’s IT infrastructure, mortgages/loans, and insurance and superannuation products is provided by outsourcers.
The resources and services are vital to the bank’s performance and should therefore be audited. Oracle ERP has raised various performance issues. To verify the system’s performance and contribution to overall BSIB performance, a detailed audit is required. The organization’s mainframe is vital to performance of BSIB’s information system.
Performance and management of the mainframe require auditing. The bank’s information system is comprised of various applications. The applications are possible source of shortfall in the organization and therefore require auditing. The bank’s server room and Hot Site are other areas that requires audit.
Financial Environment
BSIB financial environment has some shortfalls that impede the bank’s performance. The shortfalls should be addressed in order to improve the bank’s performance. Finance senior managers and Team Leaders should be provided with intensive in-house training in order to enable they understand financial assertions.
This would enable them to exercise more control on their areas of responsibility. More resources including additional employees should be deployed to the Payroll Team in order to enable it review remuneration amounts for each business unit group on daily basis. Human resources core function application should be expanded in order to enable it handle the increasing number of employees.
Training program and employees motivation strategies are required in order to improve performance of Accounts Payable Teams. To ensure improved performance, Account Payable Team Leader should be provided with appropriate resource in order to enable daily review of processing report and Exception report. Appropriate data integrity strategies are required in order to improve data accuracy and integrity in HR department.
Oracle ERP
Enterprise Resource Planning uses computer technology to undertake various functions of an organization. ERP integrates various functions therefore making management easier. The Oracle ERP can lead to various benefits to BSIB. The system can enable the bank integrate various functions conducted in human resource management. Instead of having independent systems to perform various issues in human resource management, the Oracle ERP will be able to handle them satisfactorily.
The system will therefore lead to cost reduction. The system requires fewer personnel and is therefore efficient. When well implemented, Oracle ERP will improve on accuracy. Some of disadvantages of the Oracle ERP are inflexibility, cost and complexity. Oracle ERP is relatively complex and therefore not easy to use. Training and retraining would be required for best performance to be realized.
Physical, Logical and Environmental Control
Information system control should be all inclusive. Physical, logical and environmental controls should work together. Physical control required in BSIB IT environment includes computer maintenance, training, backup and physical access control. Logically, flow of data and information in the system should be well outlined.
The logical structure of the information system should ensure data integrity and accuracy. Direct interface of the bank’s data with the mainframe may compromise data integrity and disaster recovery. The structure should be altered to allow indirect access to the mainframe. Various environmental controls are essential in BSIB IT environment. Access to sensitive IT resources should be controlled. For example, criteria should be laid on individuals that can have access to the bank’s server room.
Disaster Recovery and Business Continuity
Disaster recovery and business continuity plans are necessary for success of information system. BSIB IT environment is lacking in disaster recovery and business recovery. Failure of some core IT resource could lead to great impact on the bank’s performance. The banks server rooms in Sydney and Adelaide need to be distributed in order to mitigate physical risks such as fire and other failures.
Sharing Hot Site and Warm site with other organization may affect business continuity. Since, the bank is expanding at a high rate, it should consider establishing its sites. Data interface the bank’s mainframe directly. This may lead to great data integrity problem in case an interface fails.
The system should be improved to allow caching and buffering. Some disaster recovery and business continuity strategies will be necessary for BSIB. A disaster recovery and business continuity team will be necessary; alternative operational locations should be identified in case of disaster; backup sites should be implemented for the bank’s data while there should be proper safeguard of IT resource such as the servers and data store.
Auditor’s Opinion
Information system is a major resource to BSIB. The bank highly depends on its information system for most of its operations. To ensure consistent growth and high performance, BSIB information system should be well managed. There are material risks identified by BISB IT environment.
Access to some sensitive IT resources is not well regulated. In addition, various applications in the bank’s IT environment are poorly integrated. There is physical failure threat due to poor management of some resources.
Data integrity is compromised by poor training of some of the bank’s employees while disaster recovery and business continuity plan has a discrepancy. Oracle ERP and other core systems are not working well together. Brisbane Savings and Investment Bank’s information system should review its information system in order to enable the firm gain a high competitive advantage in banking industry.
Reference List
Cascarino, R. 2007. Auditor’s guide to information systems auditing. New York: John Wiley and Sons.
Dube, D. & Gulati, V. 2005. Information system audit and assurance. Delhi: Tata McGraw-Hill.
Hall, J. & Singleton, T. 2005. Information technology auditing and assurance. Sydney: Thomson.
Piattini, M. 2000. Auditing information systems. New York: Idea Group Inc.
Weber, R. & Jamieson, R. 2008. Information Systems Control and Audit. New York: Pearson Education, Limited.