Abstract
This paper presents a detailed study of asymmetric and symmetric encryption and decryption algorithms by focusing on the operations, the strengths, and weaknesses of the RSA and Data Encryption Standard (DES) algorithms.
The best characteristics of DES and RSA algorithms can be combined to form a hybrid encryption algorithm to provide the desired properties of message integrity, authentication, and non-repudiation.
Cryptography
According to Curtin (2007), cryptography is the study of the mathematical methods used to develop algorithms which are used for secret writing to enforce message authentication, integrity, and confidentiality.
Cryptography enables the detection and prevention of cheating and malicious activities (Akl & Taylor, 1993).
Encryption
Encryption is a process that uses an encryption algorithm to convert a message from plaintext into ciphertext, making the message unreadable to a third party (Akl & Taylor, 1993). Figure 1 below shows a cryptographic system used to encrypt and decrypt messages.
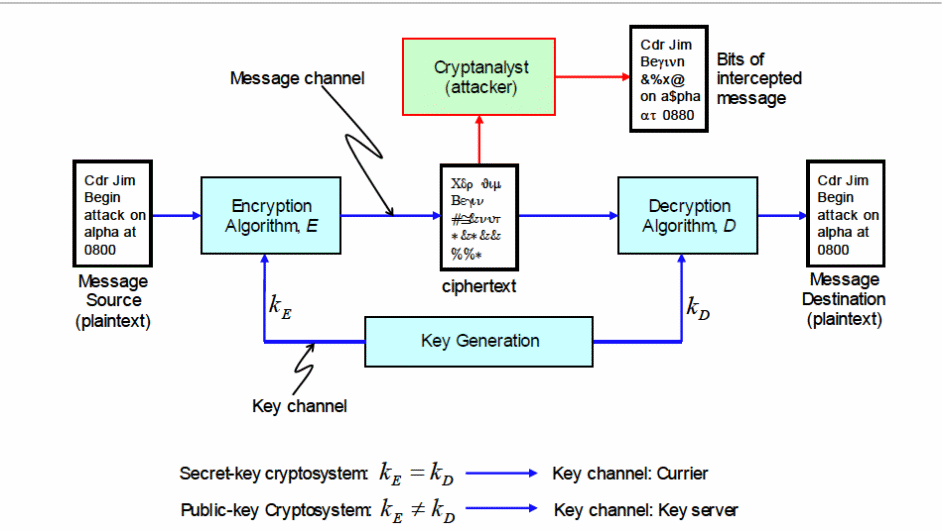
The figure above illustrates the public and private cryptosystem which is used to achieve message encryption, decryption, integrity, authentication, non-repudiation, and confidentiality (Curtin, 2007).
Symmetric
Bellovin and Merritt (1992) argues that a symmetric algorithm uses one secret key to encrypt plaintext into ciphertext and to decrypt ciphertext into plaintext.
The advantage with the symmetric algorithm is that it consumes fewer resources than its asymmetric counterpart. The main challenge with symmetric algorithms is to keep the key secret. However, if the key is known to the attacker, the communication becomes unsafe (Curtin, 2007).
Asymmetric
An asymmetric encryption algorithm uses a public key to encrypt a message and a private key to decrypt the message (Curtin, 2007). The encryption key is kept public and is known as the “public key” while the decryption key is kept secret and is known as the “private or secret key”.
It is impossible to compute the secret key using the public key, making it difficult for a cryptanalyst to attack the asymmetric cryptosystem. The main disadvantage with asymmetric algorithms is that they are slower than symmetric algorithms (Fujisaki & Okamoto, 1999).
Block and Stream Ciphers
Curtin (2007) argues that block ciphers operate by breaking a message into fixed block sized messages which are encrypted using the same key. Stream ciphers operate by encoding each symbol of the plaintext into ciphertext.
The advantage with block ciphers is that a smaller block can be created from a large message. The “problem with the stream cipher is that an error can be propagated to the recipient after the message has been encoded” (Fujisaki & Okamoto, 1999).
Data Encryption Standard (DES)
The Data Encryption Standard (DES) is an algorithm that was developed by IBM in 1970 and has been used for classified government and commercial applications since its discovery.
DES is a block cipher which uses the Feistel structure which functions by processing 64 bits of plaintext into 64 bits of ciphertext based on a 56 bit variable. The message to be enciphered is subjected to substitution and permutation steps.
Substitution is done by mapping each element of the plaintext into the corresponding element of the ciphertext. Substitution takes a 48 bit number as input to produce a 32 bit number as output (Fujisaki & Okamoto, 1999).
In the permutation step, the input block is split into two halves, denoted as L (for the left block) and R (for the right block). For each substitution and permutation steps, the right half (R) remains unchanged but the left half (L) is transformed depending on the encryption key.
At the end of each permutation step, L is swapped into R and R is swapped into L. After each permutation step, the results are again swapped back illustrated in figure 2 below.
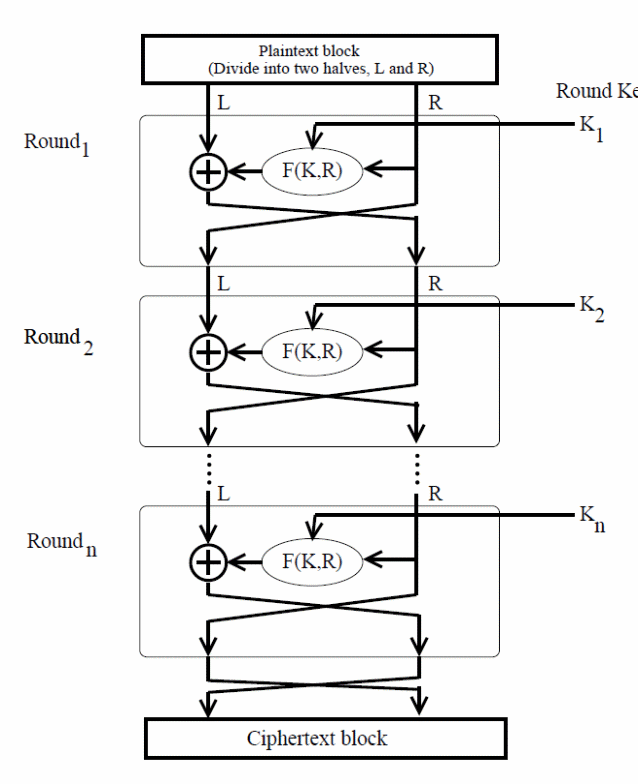
From the above diagram, F denotes the scrambling operation on the input message using the Ki round key, which is derived from the main encryption key. According to Curtin (2007), F is the Feistel function that is used to scramble the messages.
Suppose E denotes the encrypted message which consists of two output blocks at the end of the ith round. The output messages are denoted by LEi and REi respectively. The output messages after the (i-1) Th round are represented by LEi = REi−1 and REi = LEi−1 Φ F (REi−1, Ki) respectively.
In this case, Φ is the exclusive bitwise OR operator. The message is decrypted based on the Feistel structure. Each round of the decryption message provides an output corresponding to each round of the encryption message (Curtin, 2007).
This property does not change even if the Feistel function is changed. The encryption and decryption rounds are illustrated in figure 3 below.
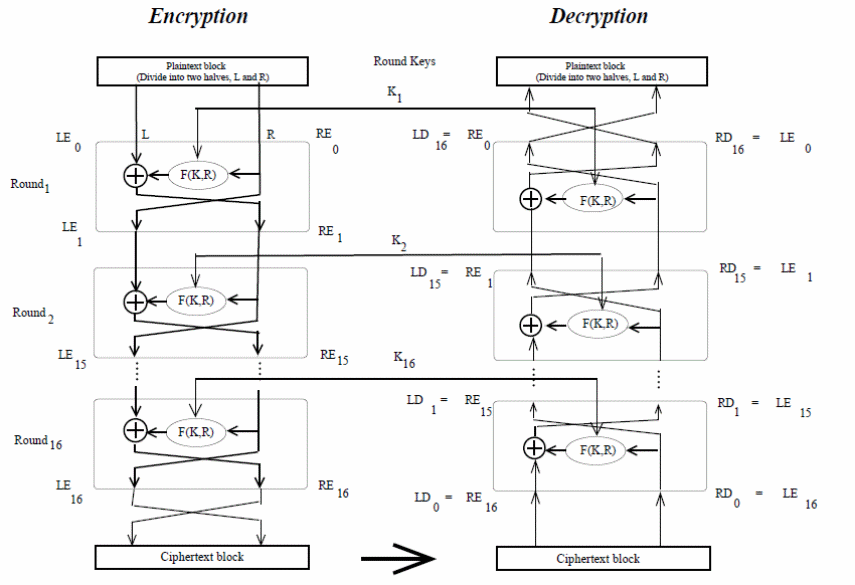
The disadvantage with DES is that it uses a weak key and a weak substitution s-box. However, the strength with DES is that it has the desired property of completeness and avalanche effect (Layton, 2006).
Application areas
DES can be applied in a number of applications to provide the desired message security. DES operates in different modes which include the Electronic Code Book (ECB) which operates on a 64 bit key to transform plaintext into ciphertext.
The ECB provides secure transmission of single values. The other mode of operation is the Cipher Block Chaining (CBS) which is used for message authentication and block oriented communication. The ECB mode of operation depends on the XOR operation (Layton, 2006).
DES can operate on the Cipher Feedback (CFB) mode which requires the processing of j bits at a time. The method is used to authenticate stream based message communication.
Other modes of operation include the Output Feedback (OFB) which is a stream oriented communication paradigm and the Counter (CTR) mode which is used for high speed message communication.
Message Authentication (MA)
DES provides message authentication and integrity based on a mechanism that does not allow unauthorized modification of messages. Message Authentication (MA) is achieved by using a message authentication code (MAC) (Menezes, Oorschot & Vanstone, 1996).
To achieve message integrity, the sender of a message uses DES to encipher the last part of the message with the message authentication code (MAC) based on the Cypher Block Code (CBC).
Authentication is done by the recipient of the ciphertext which has the MAC appended to the last part of the message by running ciphertext on DES and comparing the results with the original plaintext (Liao & Chao, 2008).
RSA
The RSA algorithm was developed in 1977 by Rivest, Shamir & Adleman of the Massachusetts Institute of Technology (MIT) and is widely used as a public key scheme to encrypt and authenticate messages. The algorithm uses both public and private keys (Dent, 2004).
The public key is available to the public, but the private key is kept secret. The “public key is used for signature verification and message encryption while the private key is used to create signatures and to decrypt messages” (Gordon & Jeffrey, 2004). The message on transmission cannot be forged.
RSA solves the problem of key distribution and digital signature verification. The strength of the RSA algorithm is in the use of two relatively prime numbers (Menezes, Oorschot & Vanstone, 1996). Based on Euler’s theorem, RSA functions as follows:
aø (n )mod N = 1 (Akl & Taylor, 1993).
In this case, gcd (a, N) =1.
N is the product of p and q, i.e. N=p.q. (Akl & Taylor, 1993).
Based on the initial equation, ø (N) = (p-1) (q-1), if the values of p and q are carefully chosen, the values of e and d are the inverse of mod ø (N). If the results for mod ø (N) are correct, the condition for k in the equation expresses as e.d=1+k.ø (N) is true. The following are true:
Cd= (Me) d.
M1. (Mø (N)) q
The sender uses a different and secure communication system to avoid the problem of white noise to achieve the desired privacy of the messages in ttransit based on the RSA algorithm, which makes the RSA cryptosystem system slow and expensive.
Message authentication
The sender of the message can prove that he or she is the source of the message, m, by using a private decoding component of the message to compute C= md mod N, which is transmitted to the recipient in the form of (C, m).
The recipient computes Ce mod N to confirm that the output message is similar to m (Stamp, 2005). The original code is (N, e) which is the message sent from the source. Consider a typical example in which m = 3, using the private key, we can compute the initial decryption as follows:
md (mod N) = 310 mod 559 = 542
Encryption is done on the message by the recipient as follows:
cd (mod N) = 5425 (mod 559) = 3
Comparing RSA and DES
A comparative analysis of both RSA and DES shows that DES is better in decrypting messages than RSA. RSA is however, better than DES in providing a solution for key agreement and key exchanges. DES has a lower avalanche effect and lower power consumption.
RSA has a higher avalanche effect, higher power consumption, and lower throughput. DES has a higher confidentiality and scalability than RSA (Scheirer, 1995).
Hybrid Encryption Methods
The hybrid method enforces data integrity and authentication using DES for data transmission purposes by relying on the DES property of higher encryption efficiency.
RSA is used to encrypt the DES key, and the system uses RSA to send the encryption and decryption keys which operate at the same speed as triple DES (Nadeem & Younus, 2005).
Flaws
The weakness with the hybrid method is that it is practically difficult to implement and is slow.
Conclusion
This study has established the characteristics of symmetric and asymmetric algorithms.
To overcome the weaknesses of the RSA and DES algorithms, the research shows that the best of both algorithms can be combined to create a hybrid algorithm which provides higher message confidentiality, authentication, and integrity.
References
Akl, S. G., & Taylor, P. D. (1993). Cryptographic solution to a problem of access control in a hierarchy. ACM Transactions on Computer Systems (TOCS), 1 (3), 239-248.
Bellovin, S. M., & Merritt, M. (1992). Encrypted key exchange: Password-based protocols secure against dictionary attacks. In Research in Security and Privacy, Proceedings. 1 (1), 72-84).
Curtin, M. (2007). Force: Cracking the Data Encryption. New York: Standard, Springer
Dent, A. W. (2004). Hybrid Cryptography. IACR Cryptology ePrint Archive, 210. CRC Press. Web.
Fujisaki, E., & Okamoto, T. (1999). Secure integration of asymmetric and symmetric encryption schemes. Advances in Cryptology—CRYPTO’99. Springer Berlin Heidelberg. Web.
Gordon, A. D., & Jeffrey, A. (2004). Types and effects for asymmetric cryptographic protocols. Journal of Computer Security, 12(3), 435-483.
Layton, T. P (2006). Information Security: Design, Implementation, Measurement, and Compliance. New York: Taylor & Francis.
Liao, H., & Chao. Y. (2008). A new data encryption algorithm based on the location of mobile users, JA: Information Technology Journal, 7 (1), 63-69.
Menezes, A., Oorschot , P., & Vanstone, S. (1996). Handbook of applied Cryptography. New York: CRC Press.
Nadeem, A., & Younus, J. M. (2005). A performance comparison of data encryption algorithms, CA: 1st International Conference on Information and Communication Technology, 2005 (1), 84-89.
Scheirer, B. (1995). Applied Cryptography “Protocols, Algorithms and source code in c. New York: John Wiley & Sons.
Stamp, M. (2005). Information Security: Principles and Practice. New York: John Wiley & Sons.