Software-Defined Networking
Software-defined networking (SDN) is a cloud-based architecture intended to enhance a network to be more flexible and efficient to handle. When using SDN, there is centralization of management by conceptualizing the regulator plane from the data advancing function in the separate networking (Abbas et al., 2020). SDN offers a centralized and programmable network that consists of various elements. First, there is a control element responsible for the centralization and control management, automating and enforcing other task commands.
The second element is the southbound Application Programming Interface (APIs) used to relay the data and information between the independent network gadgets and controller planes. Such devices that information is relayed include switches, routers, firewalls, and access points (Pradhan & Mathew, 2020). The last element used in the centralization of the programs is northbound APIs that convey data between the applications and policy regulators, whereby an SDN appears like an independent function.
According to the Global Networking Trends 2020 report, SDN has been widely adopted across the data quarters. That means a range not less than 64% for the data centers, Wide Area Networks by a range of not less than 58%, and 40% in access networks (Abbas et al., 2020). The main purpose of SDNs is to simplify operations by decoupling the control planes, achieving a faster time to promote through the deployment of applications and services by use of APIs (Pradhan & Mathew, 2020). Therefore, there are four areas that an organization that can rely on SDN technology to make a competitive advantage. First, network programming, logical centralization and control, network abstraction, and interoperability openness.
SDN controllers are in the market because the developed companies have utilized their capability to sell the components. Examples of SDN networking components include Cisco Open SDN, Brocade SDN, and Jupiter Contrail SDN (Rosa, 2019). Additionally, there are open sources of SDN components such as Beacon, Opendaylight, and Ryu. The open-source networks are linear with the SDN designs; therefore, they provide a better interface useful to the companies.
Intent-Based Networking (IBN)
Intent-based networking (IBN) is a developing technology idea that targets to apply an intensive level of artificial intelligence and networking insight. To elaborate on the insights, they replace the monolithic processes of configuring networks and respond to network issues (Yichiet et al., 2021). That means the management of a given organization can send a request to communicate to the network the intended outcome instead of coding and executing the single tasks manually.
The benefits of using IBN are reduction in manual tasks, fast resolution through effective troubleshooting, reduced risks associated with compliance of networks, improvement of security, and optimization of analysis (Rosa, 2019). Examples of IBN networking include Cisco, Apstra, closed-loop, and Silicon Valley. For example, the given company from the analysis text has various tasks that it wants to perform to improve operations (Benzekki et al., 2016). Assuming that the company has IT experts who have specialized in microservices architecture, they can undertake various tasks to achieve that.
For example, the Caduceus has 2,000 Microsoft Windows computers in the workstation. It intends to utilize the Dell OptiPlex series, whereby several changes will be required. The IT team can access the cost by use of IBN. First, the desired intention would be ‘running of Intel Core i5 processor, install windows 10, contain 8 Giga Bites (GB) and configure 256 GB hard disk drive’. Each action will be put against the cost, and the automation would be validating the intent and translating it into action (Abbas et al., 2020). Through the quality control monitor department, the company will check the feasibility and control the actions in axes ensuring that the intent works.
How Virtualizing the Desktop and Now Back-End Infrastructure Are Complementary and Related
The notable difference between SDN and monolithic programming is that SDN is software-based while traditional networking is hardware-based. Therefore, SDN is more flexible and allows users to control and manage resources in a virtual way throughout the control command (Yichiet et al., 2021). The SDN controllers have a northbound feature that utilizes APIs to develop a direct communication using the required protocols that would oppose traditional design that uses all the available elements for the user to manually remove. In the Caduceus example, the IT personnel can direct network paths and have a proactive arrangement of network services that can produce linear communication with the financial controller (Benzekki et al., 2016). The fact that the company’s resources can be accessed remotely means that there can be the generation of abstract copies of the physical networks from a central firm’s locations.
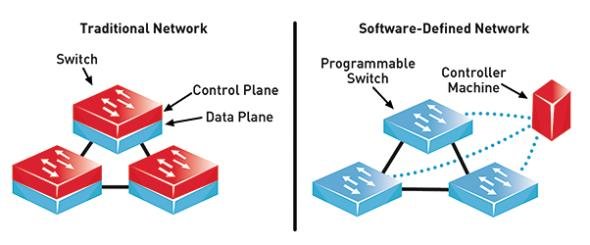
The architecture between the traditional and IBN is based on the network complexity due to automation. The two networks are built in a different era. The traditional network’s focus is for the need to revolutionize the networks and process in-line with overall business aims. The pros of IBN are the increased agility by reducing the network infrastructure for the organization. IBN works across all handsets from different levels. Unlike traditional networking, which has delays in operations, IBN improves the control and performance due to the software capability to implement tasks across all networks. The major benefit of IBN is that it can allow IT personnel to alter any constraint realized through the graphical interface instead of the device by a device that traditional ways relied on.
The cons of SDN and IBN are the controller’s vulnerability because the person needs to manage the network instead of routers and other switches. Therefore, the controller’s security must be enhanced by checking who has access to the controller for security purposes. Additionally, IBNs and SDNs have distributed denial-of-service threats due to the large numbers of undeclared intent into the network line. Since there is the elimination of physical routers and switches, there may be a missing firewall to prevent the network’s vulnerability (Benzekki et al., 2016). Although the traditional networks may not have a full centralization system when being configured, to some extent, they are safer as compared to SDNs and IBNs.
Relationship Between SDN and IBN
IBN can be framed as a modern successor to SDN since it applies most principles and architectures. That means elements such as a division between the applications and the network is used by the two networking methodologies. SDN uses a software configuration, while IBN utilizes the same concept with the physician workforce to execute various components. The two networking architectures can transform the way networks and implemented and managed (Benzekki et al., 2016). For organizations to have an advanced program, they need to combine both SDN and IBN.
IBN takes SDN to a further step by allowing network administrators to have a network configuration to address and support businesses than grow the workforce’s capability. If the organization’s personnel want to accomplish a certain intent, they can adhere to the previous SDN policies for the success of the matter (Karakus & Durresi, 2018). For example, the company wants to set Virtual Private Network (VPN)software to achieve easy tracking. Therefore, the IBN-based command will have to perform self-checks to allow the operator to run the SDN to the approved interface for tracking the data and information. Even though the cost would be approximately $2000000, the returns will be a strong cyber-secured operation that can guarantee streamlined workflow that can bring more income.
Conclusion
Organizations need to adopt the new cloud-based services in operations that require technology. From the example, Caduceus has highlighted moving from monolithic applications by adopting microservices architecture that works more independently than the traditional models. IBN is an advanced program based on SDN principles that seeks to have more functional resources but under strict supervision and monitoring. The two networks are interrelated because they apply the same deployment capability when designing an intent.
The two networking components have enhanced modern computing because they have centralized data and information points compared to the old configuration forms. One of the key factors that the paper has shown is the ability to have access to a given network without distorting the end-to-end functions within the same organization. From the analysis, it is easy to predict that in the future, IBN and SDN will have wider coverage in cloud computing, where organizations will have improved service implementation and other programs. Any modern organization should learn the benefits of SDN and IBN networks and utilize them to enhance its portfolio.
References
Abbas, K., Afaq, M., Ahmed Khan, T., Rafiq, A., & Song, W. (2020). Slicing the core network and radio access network domains through intent-based networking for 5G networks. Electronics, 9(10), 17-20. Web.
Benzekki, K., El Fergougui, A., & Elbelrhiti Elalaoui, A. (2016). Software-defined networking (SDN): A survey. Security and Communication Networks, 9(18), 58-78. Web.
Karakus, M., & Durresi, A. (2018). The economic viability of software-defined networking (SDN). Computer Networks, 135(3), 81-95. Web.
Pradhan, A., & Mathew, R. (2020). Solutions to vulnerabilities and threats in software-defined networking. Procedia Computer Science, 171(2), 81-89. Web.
Rosa, M. (2019). Improving security through software-defined networking (SDN): An SDN-based model. International Journal of Recent Technology and Engineering, 8(4), 295-300. Web.
Yichiet, A., Min, J., Lee, G., & Sheng, L. (2021). Intent-based network policy to solution architecting recommendations. International Journal of Business Data Communications and Networking, 17(1), 55-74. Web.