Introduction
As part of our data communication and laboratory experiment, we were required to carry out an investigation on Wi-Fi and LAN technologies. The experiment comprised of several units. The units were TCP/IP LAN technology, advanced LAN technology, rack server module, wireless LAN technology, copper tool kit, protocol analyser, and network analyser. The software analysed were software network monitoring analyser and AirMagnet Wi-Fi Analyser Pro (IEEE, 2012). The units were completed in three sessions. During the sessions, we observed and took notes. The notes indicated how the units were configured in real LAN networks. Similarly, the notes documented the features of software utilized. As such, LAN Traffic V2 from ZTI Corporation was utilized in the creation of traffic for internet protocol networks. The protocols used were TCP, UDP, ICMP, or SCTP. Illustrated below is the laboratory report obtained from the investigations.
Theory and background
Wi-Fi is a type of communication technology. The wireless technology enables two communication devices to interact in a computer network. The technology utilizes 2.40 GHz UHF and 5.00 GHz SHF ISM radio bands (Misra, 2010). On the other hand, LAN refers to is a computer network, which integrates PCs in a local area like an office, college, or residential homes (Peterson & Davie, 2011). LANs are different from WANs because they cover limited geographical locations. ARCNET and Token Ring were widely utilized in the early 1990s to construct LAN networks (Sarkar & Basavaraju, 2013). Currently, Ethernet over twisted pair cabling and Wi-Fi have become very popular in the construction of LAN networks due to their designs. TCP/IP architecture comprises of four layers (Williams, 2012). The layers are application, transport, internet, and network. Smart switches can be managed through WEB. A user is required to log into a web-based interface to configure the switches.
Equipment setup & procedure
Unit 1-7 procedures setup and procedures:
- Devices and network circuit equipment were assembled at the computer lab.
- The students identified TCP/IP LAN technology, advanced LAN technology, rack server module, wireless LAN technology, copper tool kit, protocol analyser, and network analyser components.
- The students observed and noted the configuration of the units in real LAN networks.
Second session procedures:
- The LAN Traffic V2 traffic generator software was obtained from the computer lab.
- Using the sender part of the LAN Traffic V2, sixteen simultaneous UDP, TCP, and ICMP connections were generated.
- Using the traffic data generator, the students configured packets size.
- The inter packet delay for each connection was recorded.
- The students generated ICMP echoes using ICMP protocol
- With the help of an automatic data generator, the students analysed throughputs, received data, sent data, sequence-numbering errors, RTT average, and jitter figures.
Third session procedures:
- A Wi-Fi Analyser was obtained from the computer lab
- Using the Wi-Fi Analyser, students noted how to diagnose network connectivity issues.
- The students noted how to conduct decoding and finding packets on decodes screen.
- The students noted how to enable spectrum analyser and detect interfering devices.
Wi-Fi Analyser discussion
Using Wi-Fi Analyser, the students inspected and assessed Wi-Fi network issues automatically (AirMagnet, 2013). With the tool, the investigators were able to resolve end-user problems faster. Equally, they were able to inspect signal strength, security risks, and Wi-Fi network susceptibilities. The figure below shows a screenshot of a Wi-Fi Analyser.
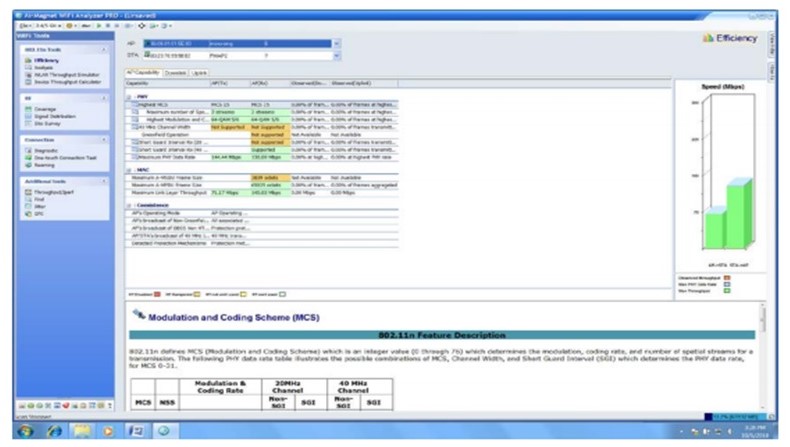
As shown in the figure, the analyser aids in the assessment of network efficiency, network issues, device throughput, WLAN or cell coverage, site RF signal distribution.
The Scrutiny screen offers a thorough analysis about a number of Wi-Fi associated concerns. The figure below represents an analysis screen.
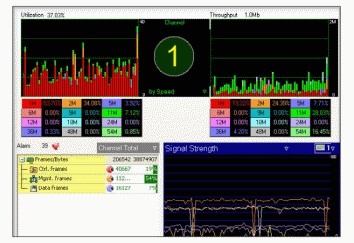
The tool enabled the investigators to analyse network data between any chosen pair of AP and STA, or AP alone, 20/40 MHz statistics, short guard interval, A-MPDU, and MCS (AirMagnet, 2013). The figure below illustrates the images obtained from the WLAN throughput simulator. The images indicate the obtained network, node, and media throughput under a number of networks. As indicated in the images, the users can configure or add additional nodes into the system.
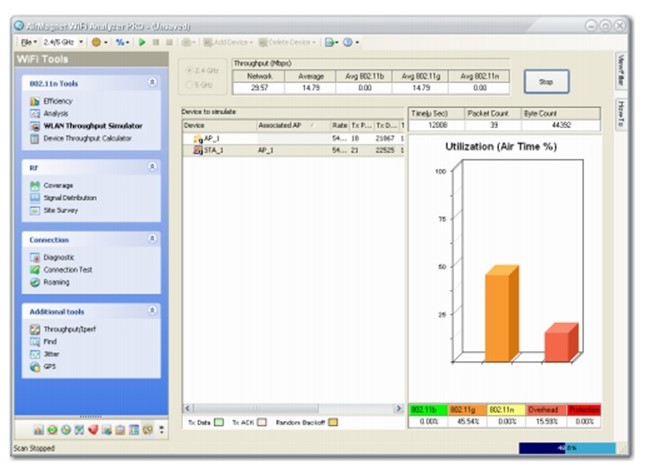
Network analyser is an essential tool for every IT technician. Through it, they can examine and troubleshoot a number of corporate wireless network operation problems such as throughput challenges, connectivity challenges, device clashes, and signal multipath issues.
LANTraffic V2 discussion
LANTraffic V2 is a traffic generator (ZTI Communications, 2013). The software can be utilised in a number of windows platforms. In the experiment, it was noted that the software could be implemented in different protocols. The protocols are UDP (User Datagram Protocol), TCP (Transmission Control Protocol), ICMP (Internet Control Message Protocol), and SCTP (Stream Control Transmission Protocol). It was also noted that the software uses the Microsoft Windows TCP/IP stack. The software does not depend on any transmission or telecom line during its operation. Therefore, any transmission line compatible with Windows OS was utilized. The transmission links utilized in the experiment included Ethernet, token-ring, hyper-Lan, WLAN, WAN, remote access, and PLC. The software comprised of a sender part and receiver parts shown below:
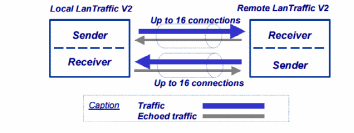
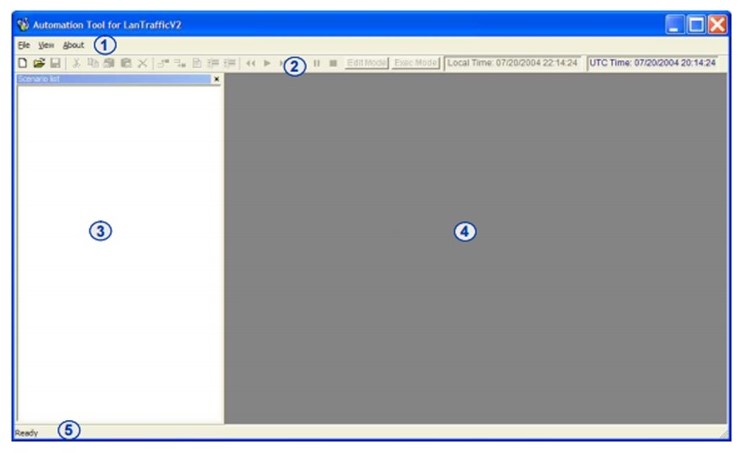
When LANTraffic V2 tool was initiated, the following image was displayed on the PC’s screen. Area 1 represented the menu bar, area 2 represented the tool bar, and area 3 displayed the list of opened scenarios. On the other hand, area 4 represented a working area while area five represented the status bar.
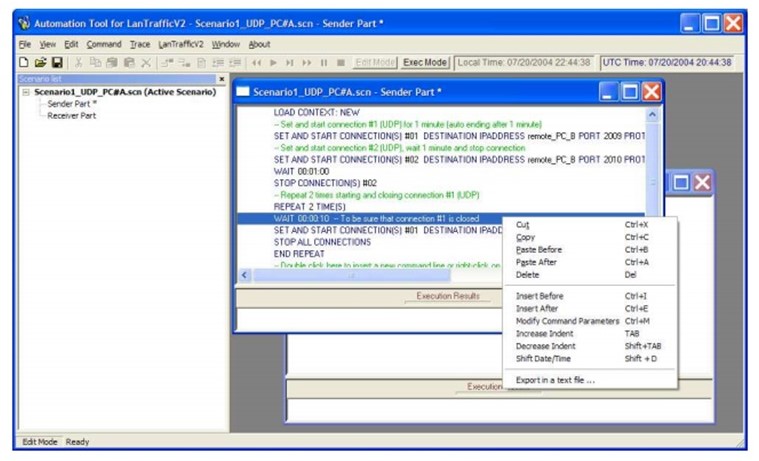
To create a new file, investigators had to click on the file folder, select the window, double click on the command line, and select the prefered command to be inserted in a chosen scenario. Thereafter, the investigators had to right click on the choosen command line before saving the new scenario. The above findings are illustrated in the figure below:
Conclusion
In conclusion, it should be noted that the above experiment comprised of three sessions. In the first session, students were required to observe how the units 1 to unit 7 were configured in LAN networks. In the other session, students analysed features of LAN Traffic V2. In the third session, AirMagnet Wi-Fi Analyser was assessed. Through the above, the investigators were able to analyse Power over Ethernet, network diagnostics, TCP/IP utilities, wireless network diagnostics, and analysis of protocols and traffic on LANs.
Based on the above findings, it is apparent that an understanding of computer networks is very essential for every IT technician. Through the knowledge, they can examine and troubleshoot a number of corporate wireless network operation problems such as throughput challenges, connectivity challenges, device clashes, and signal multipath issues.
References
AirMagnet, A. (2013). AirMagnet WiFi Analyzer Pro. Web.
IEEE, I. (2012). IEEE 802 Standards. Web.
Misra, S. (2010). Selected topics in communication networks and distributed systems. Singapore: World Scientific.
Peterson, L., & Davie, B. (2011). Computer networks: A systems approach (2nd ed.). San Francisco, Calif.: Morgan Kaufmann.
Sarkar, S., & Basavaraju, T. (2013). Ad hoc mobile wireless networks principles, protocols, and applications (2nd ed.). Boca Raton: CRC Press.
Williams, R. (2012). Computer systems architecture: A networking approach. Harlow, England: Addison-Wesley.
ZTI Communications (2013).Traffic Generator for IP Networks. Web.