Windows 10 Operating System
The firm needs to upgrade and use the Windows 10 Enterprise operating system once it decides to upgrade. The operating system offers additional security features based on Windows 10 Professional architecture. The OS is ideal for an enterprise environment because of its performance and security features. However, the installation relies on Random Access Memory (RAM) and Read Only Memory (ROM) space (Arshad et al., 2021). When analyzing the installation methods, it is important to deploy them automatically. The automatic deployment is achieved through Microsoft autopilot and in-place installation. Windows 10 has numerous security features, such as Windows Defender, firewall, and BitLocker. The backup and recovery are handled professionally by the Windows 10 interface (Arshad et al., 2021). The OS has a default backup mechanism, and when it crashes, it provides the user with a restoration functionality to its previous state.
Windows 10 backup data has a file history feature that allows the data to be added to external or local devices. Organizations can benefit from the backup and recovery unit because the computers will be able to recall their previous sessions. The analogy helps the computer to evade disasters by synchronizing the recovery unit with the preference that worked (Singh & Singh, 2018). The booting process can recall the best last session that worked and use the syntax. However, the OS can be formulated in the setup to protect backups through multiple copies or store it in multiple locations. The firm should consider upgrading to Windows 10 because it provides reliable ambient conditions. The updated platform ensures that the firewall is functional every time. Users will be able to interact with the latest technologies and advance their understanding of decision-making. Windows 10 is faster than other versions, such as Windows XP, Windows 7, and Windows 8 (Singh & Singh, 2018). The OS has multiple support systems to host much software that an organization deems beneficial.
Purpose
The document’s purpose is to show an overview of the Windows 10 implementation process. The document offers the necessary evidence about the ideal installation process while showing the virtual configurations. The first part will show the upgrade matrix and the security features of Windows 10 (McKeown et al., 2019). In the second part, the analogy revolves around standard features in a newly installed host. Lastly, the third part provides insights into the risk factors affiliated with the upgrade or installation process of Windows 10.
Windows Installation
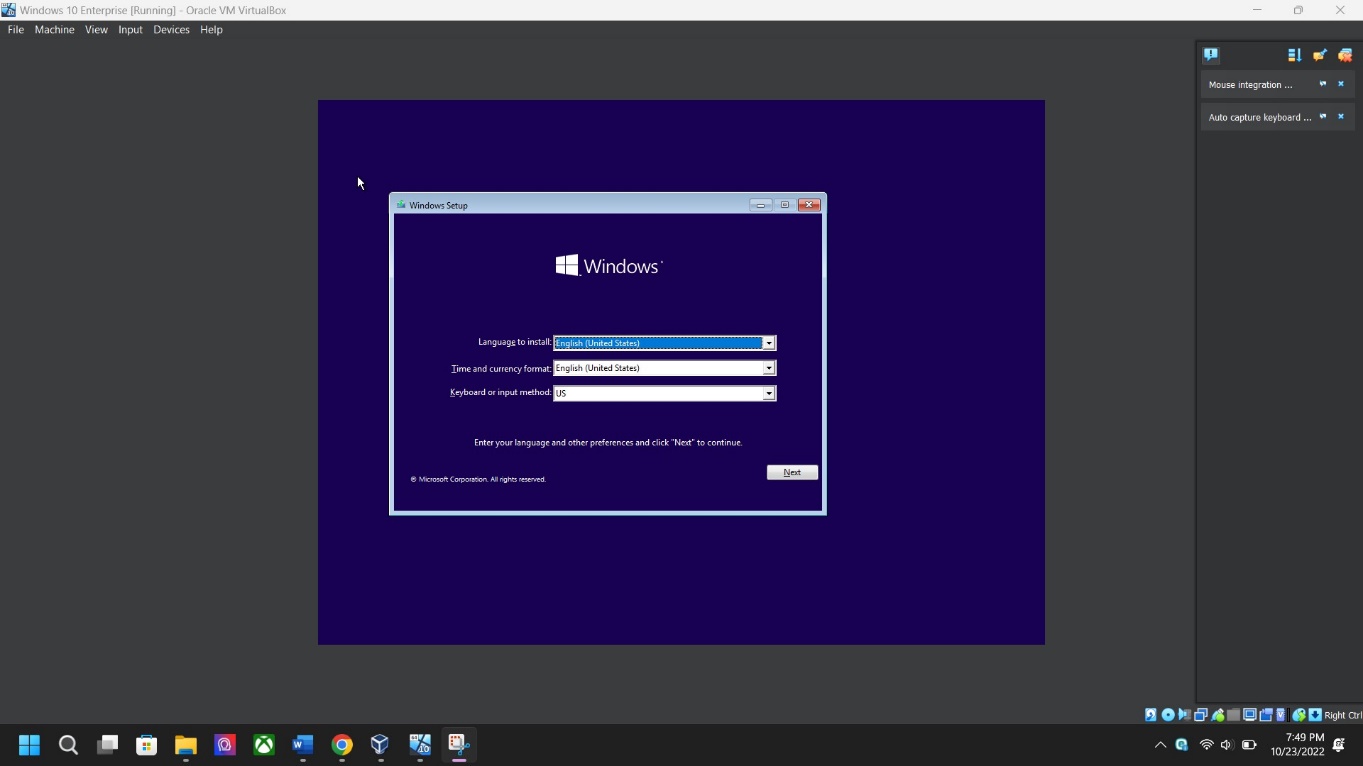
OS version screenshot – The screen will display the operating system windows, click NEXT.
*Verify that all the prompts on this installation step are accurate before clicking NEXT.
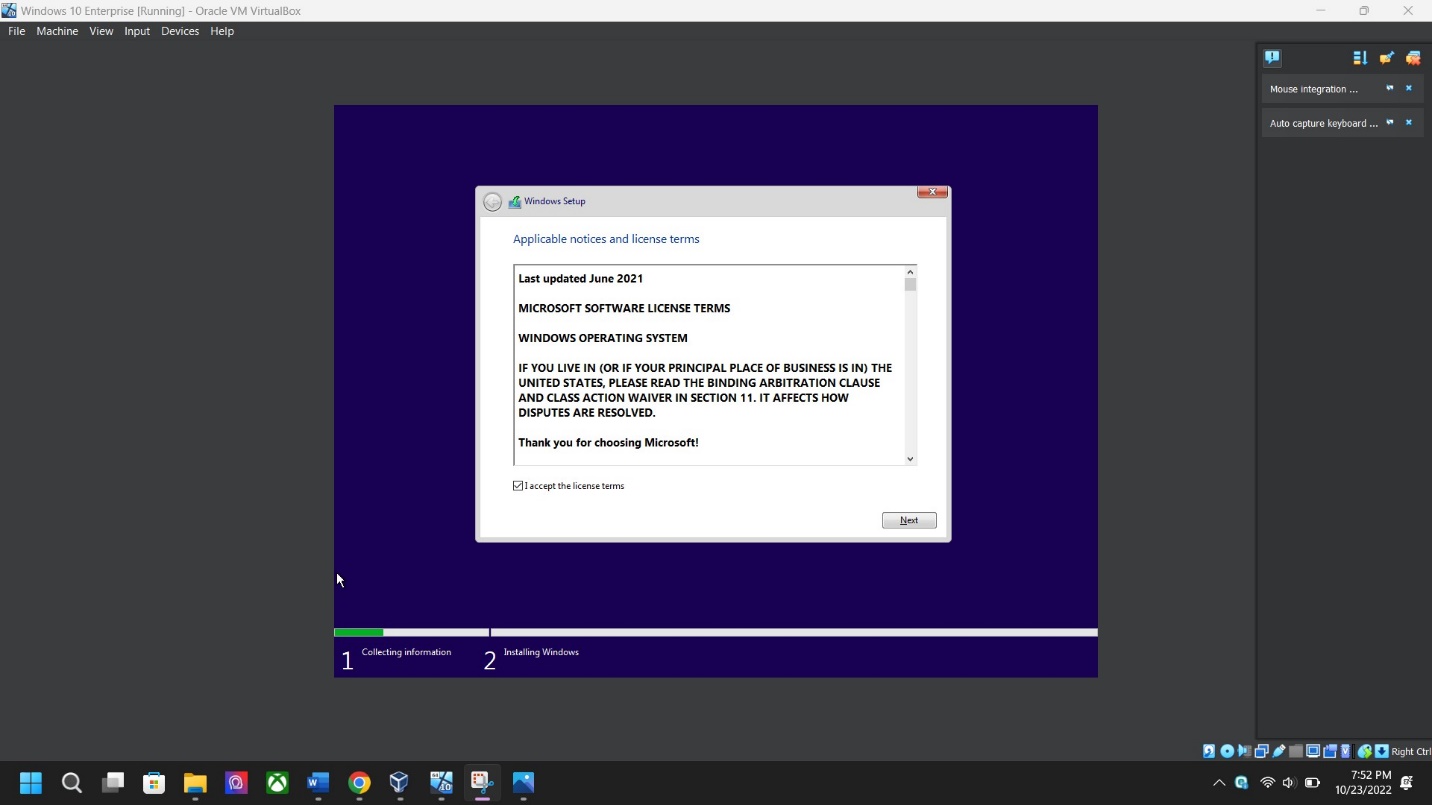
License acceptance screenshot – Click the NEXT Button to accept the license terms.
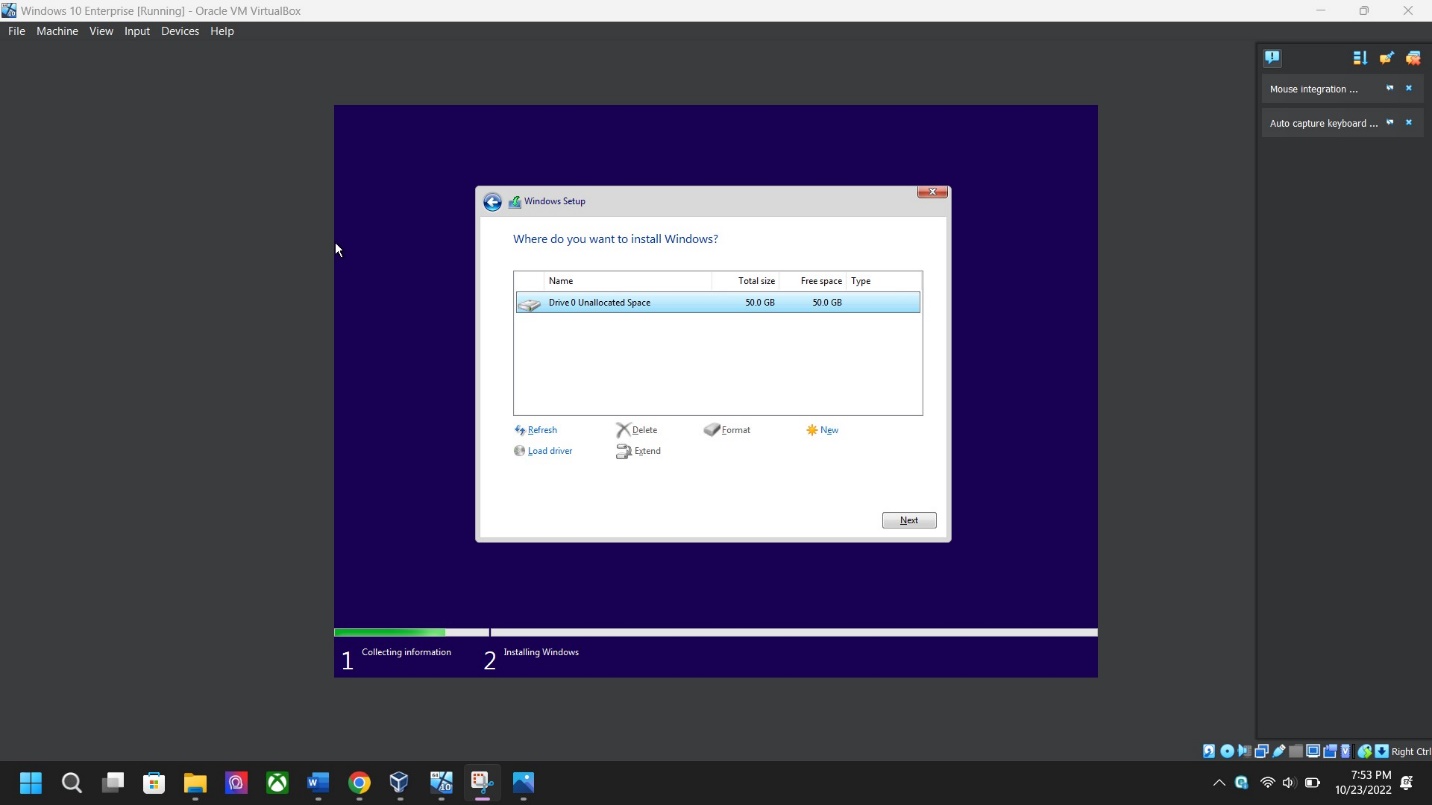
Disk configuration screenshot -The primary hard drive will be configured automatically during installation; if another disk is preferred, you can select it. After choosing an option, click NEXT.
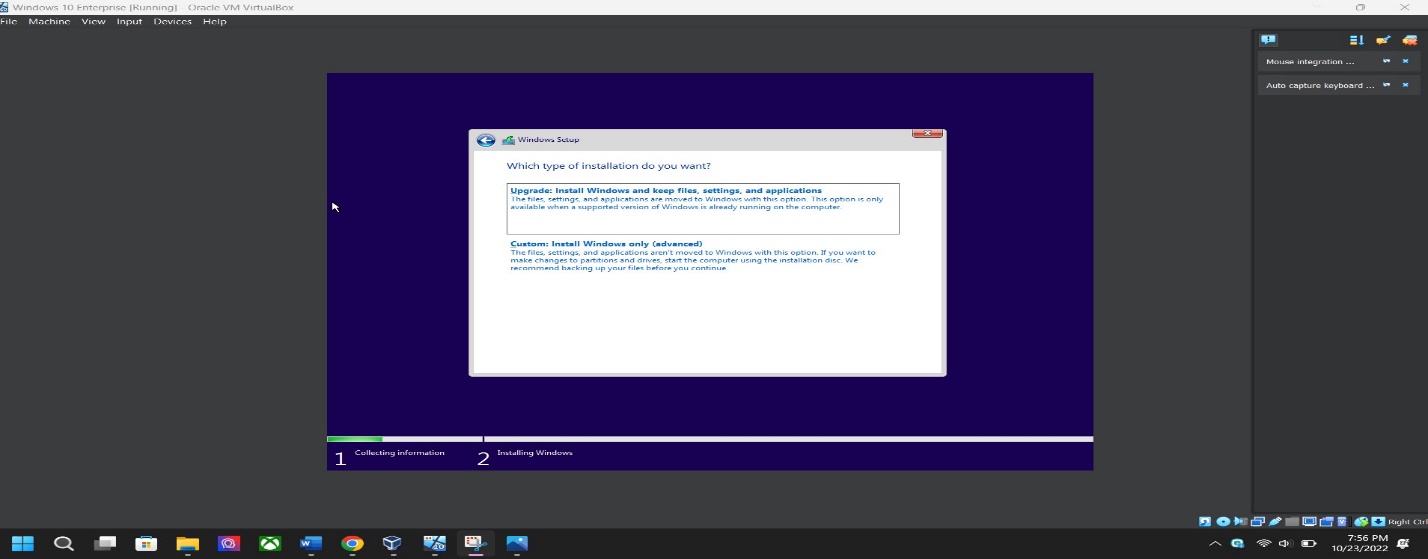
Custom installation vs. upgrade installation – Select “Custom: Install Window Only (Advanced)”. This option lets you create a Windows installation disc or drive that will work on any compatible PC.
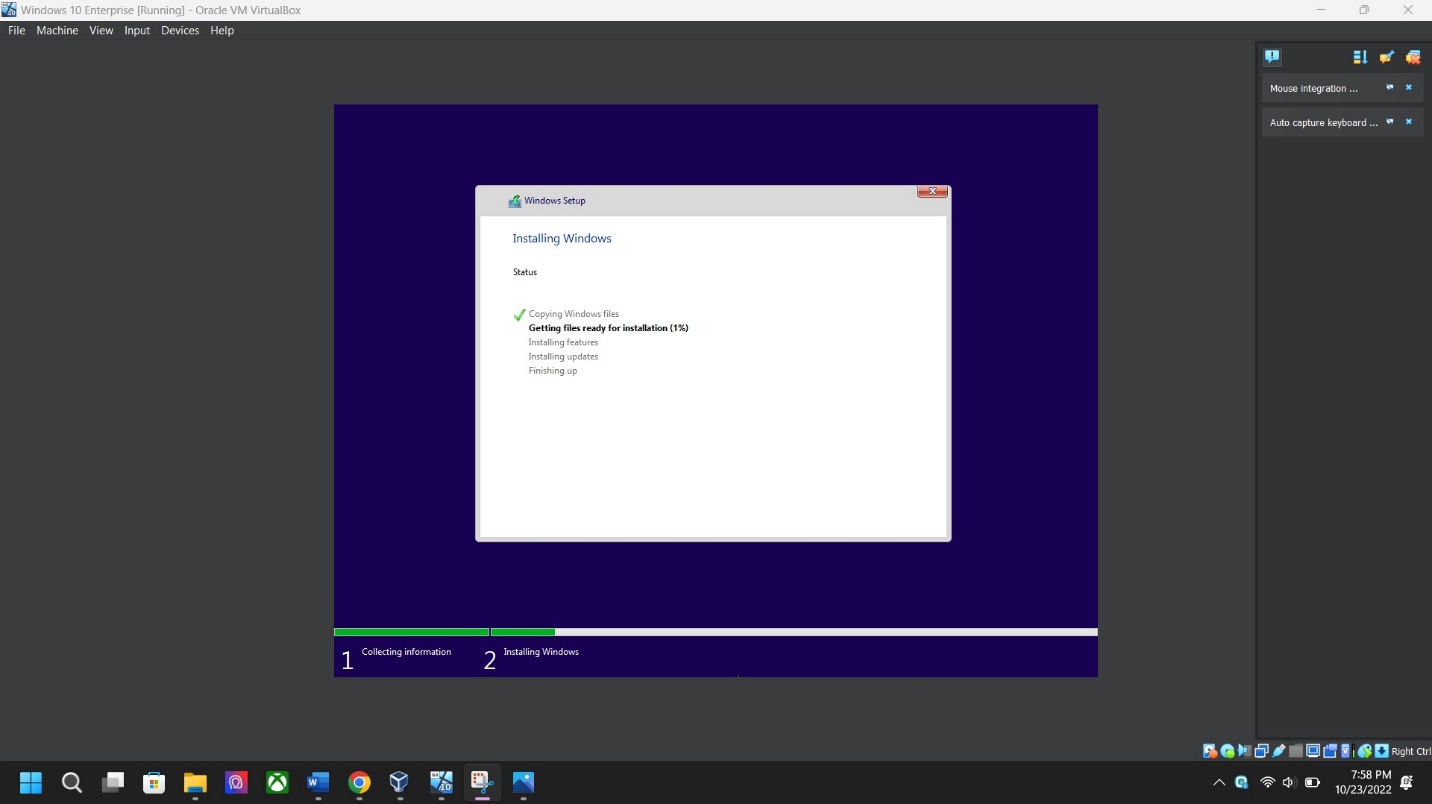
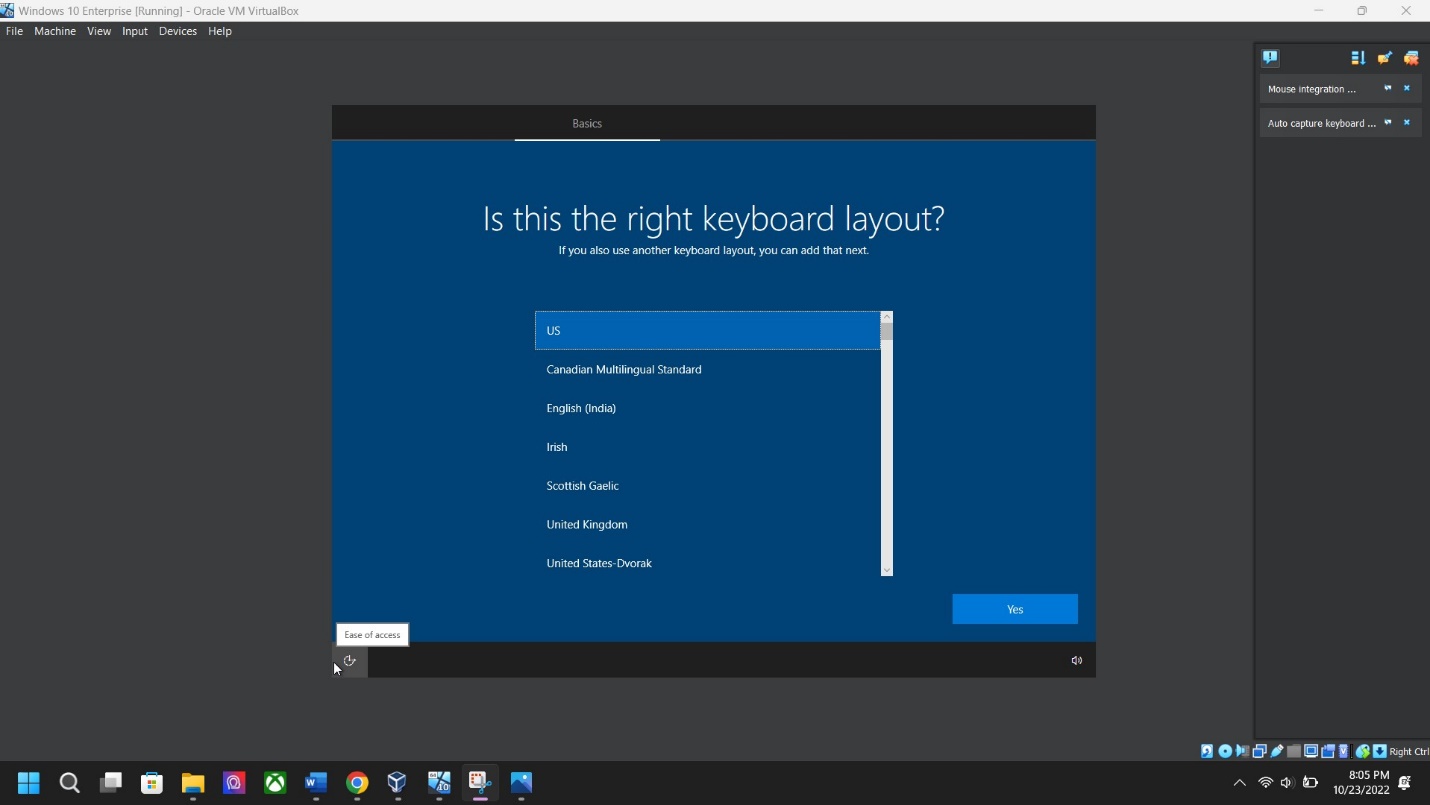
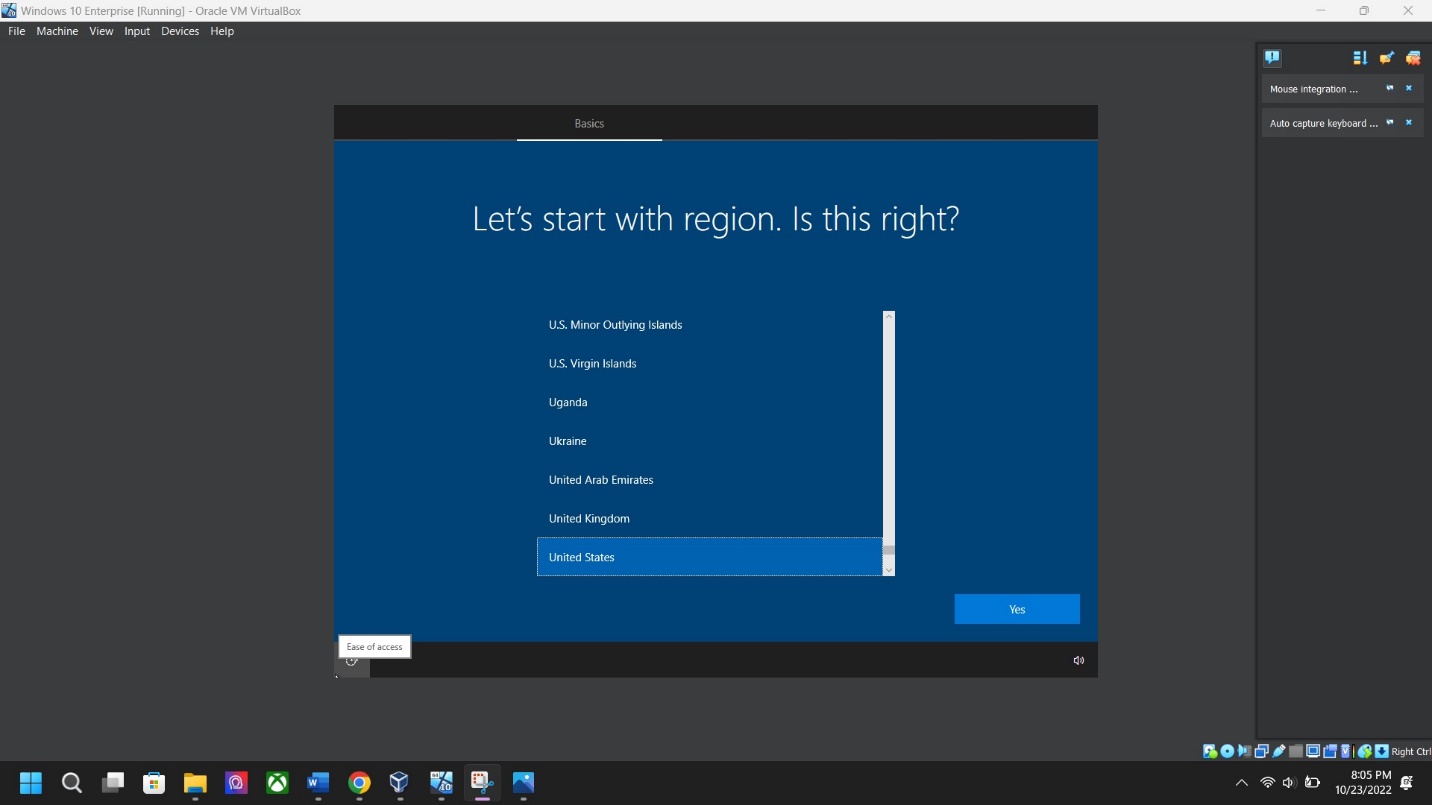
Region/Keyboard – Select your preference for region and keyboard then click Yes.
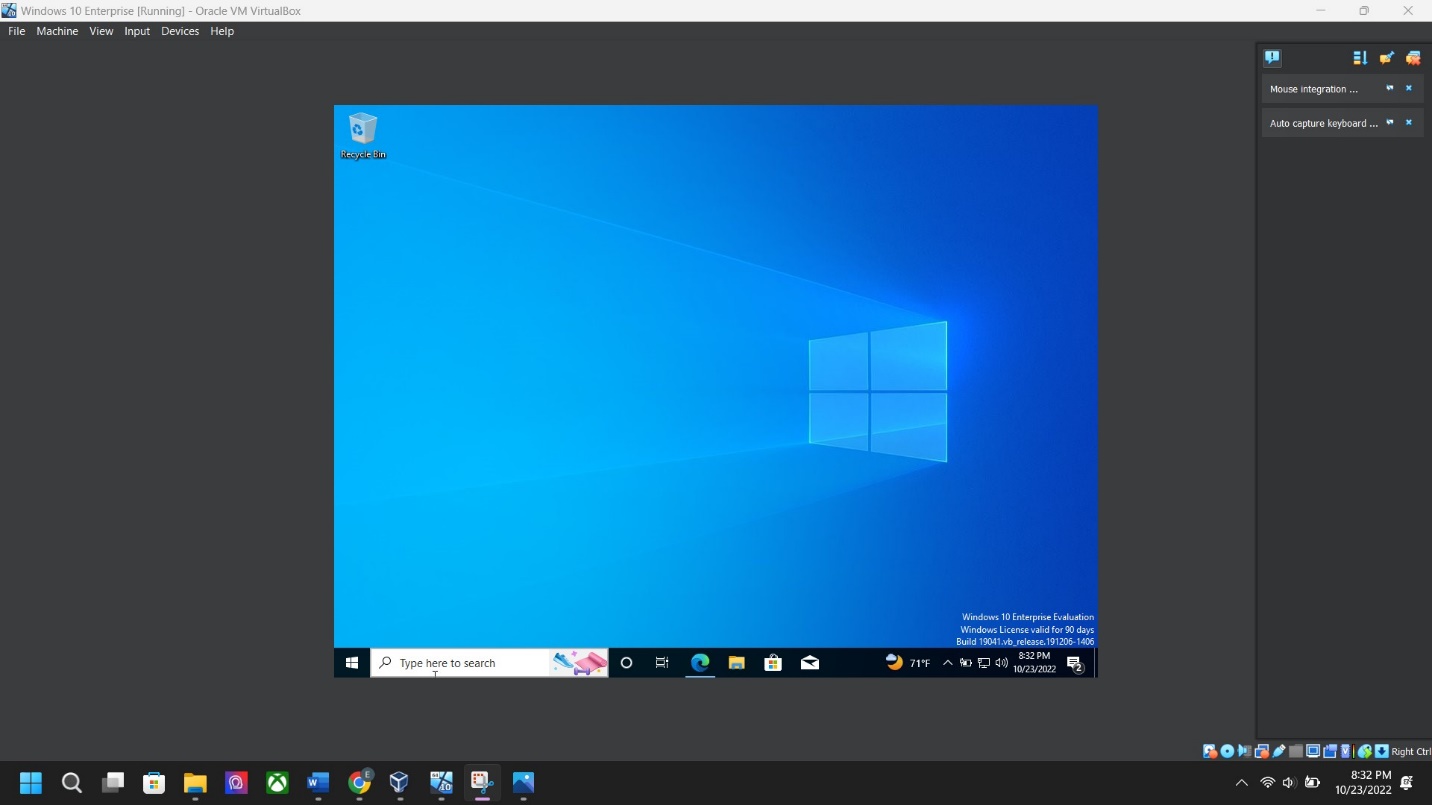
Host machine up and running screenshot:Date: 10/23/22 Time: 8:32
Windows Configuration
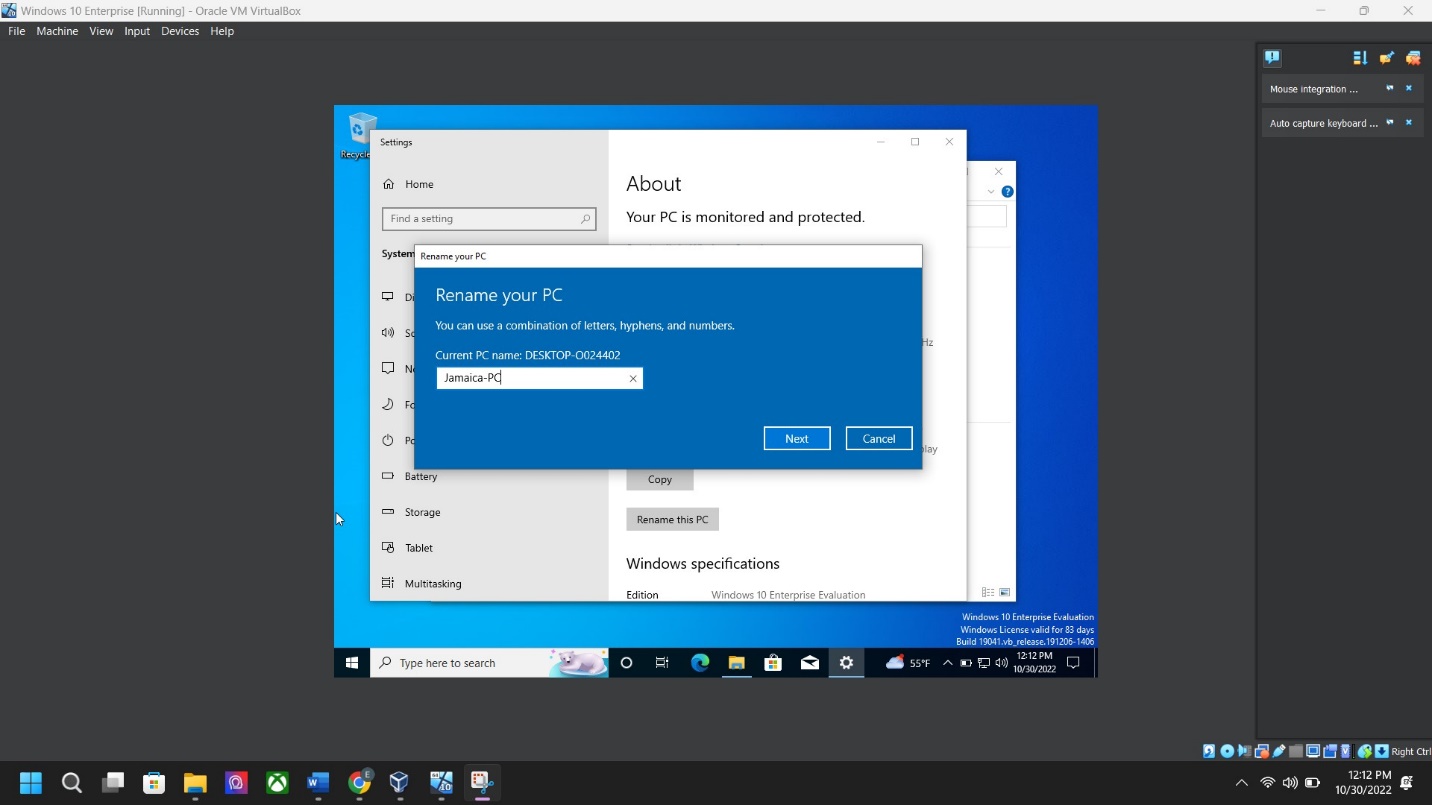
Step 1: Computer name screenshot – Go to > File Explorer > Right Click “This PC” > Properties > About > Click “Rename this PC” > Next
Step 2: Desktop theme screenshot – Click “Setting” > “Personalization” > “Themes” > Then select any theme you would like.
Before Theme:
After Theme:
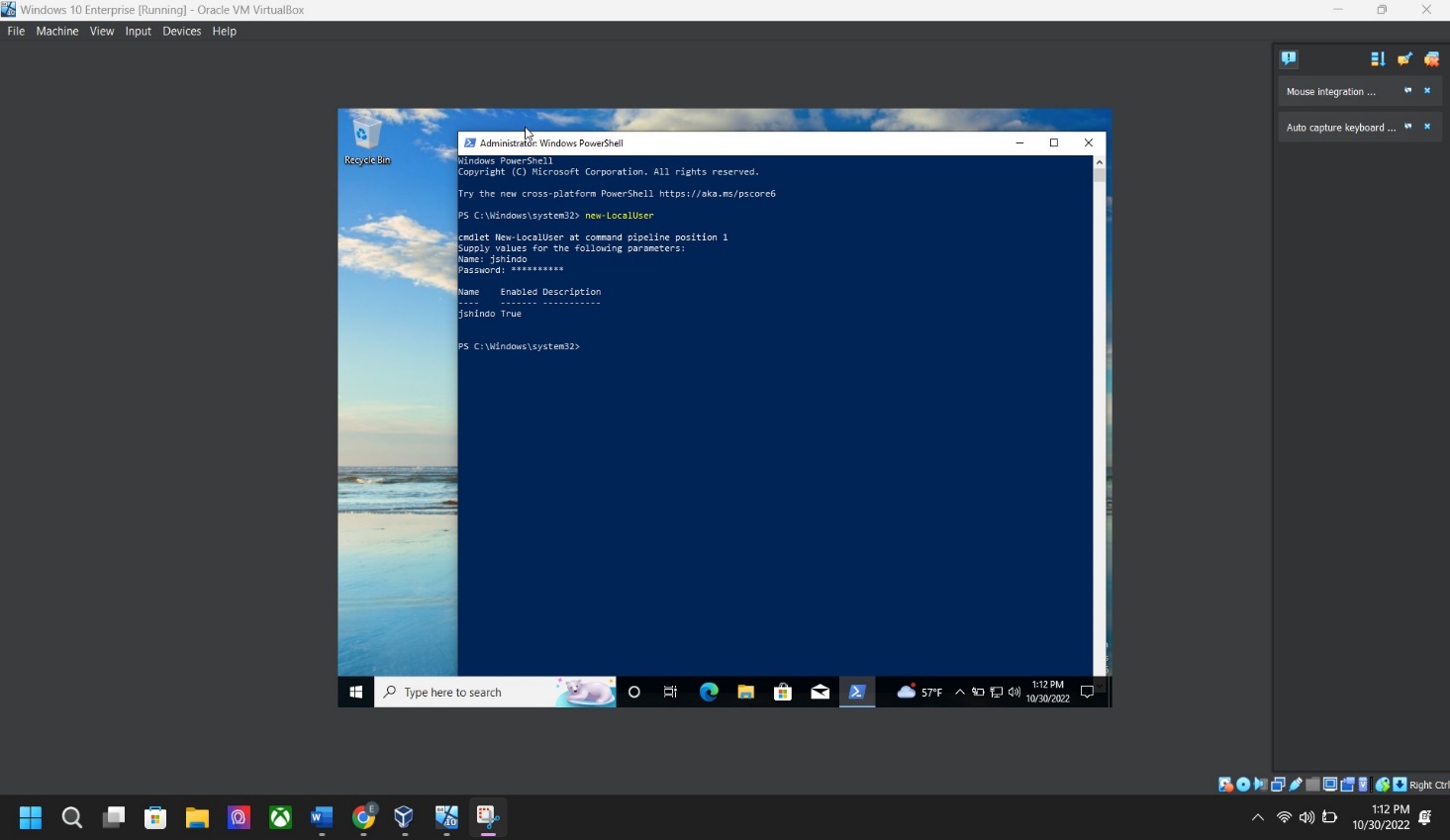
Step 3: Local user account screenshot – Go to “Window Power shell” > “run as ADMINISTRATOR” > type “new-LocalUser” > type the user account name (First Initial, Last Name) > click ENTER.
Step 4: Local group account screenshot – Go to “Window Power shell” > “run as ADMINISTRATOR” > type “new-LocalGroup” > then user group name “First Initial and Last Name”> Name: “Tetraaccounting” > click Enter.
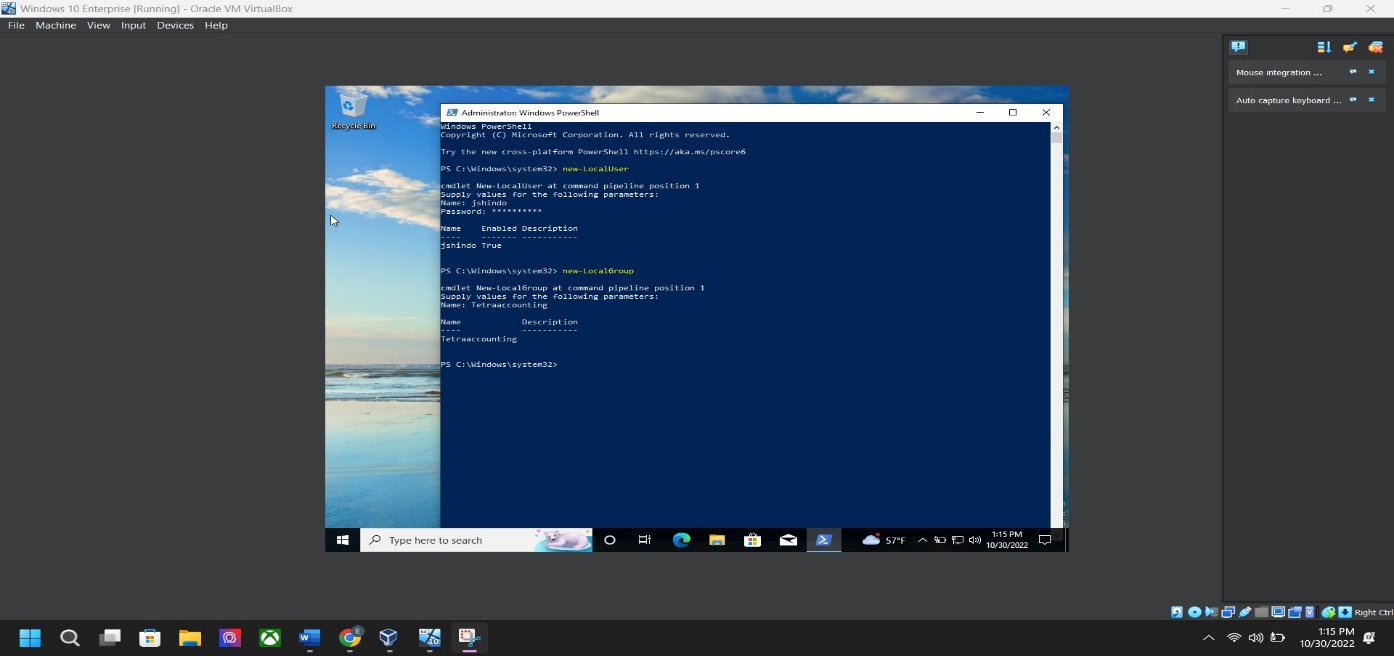
Step 5: Add user to local group screenshot – Go to “Window PowerShell” and “run as Administrator” > type “Add-LocalGroupMember -group local group name -member user account name” click ENTER
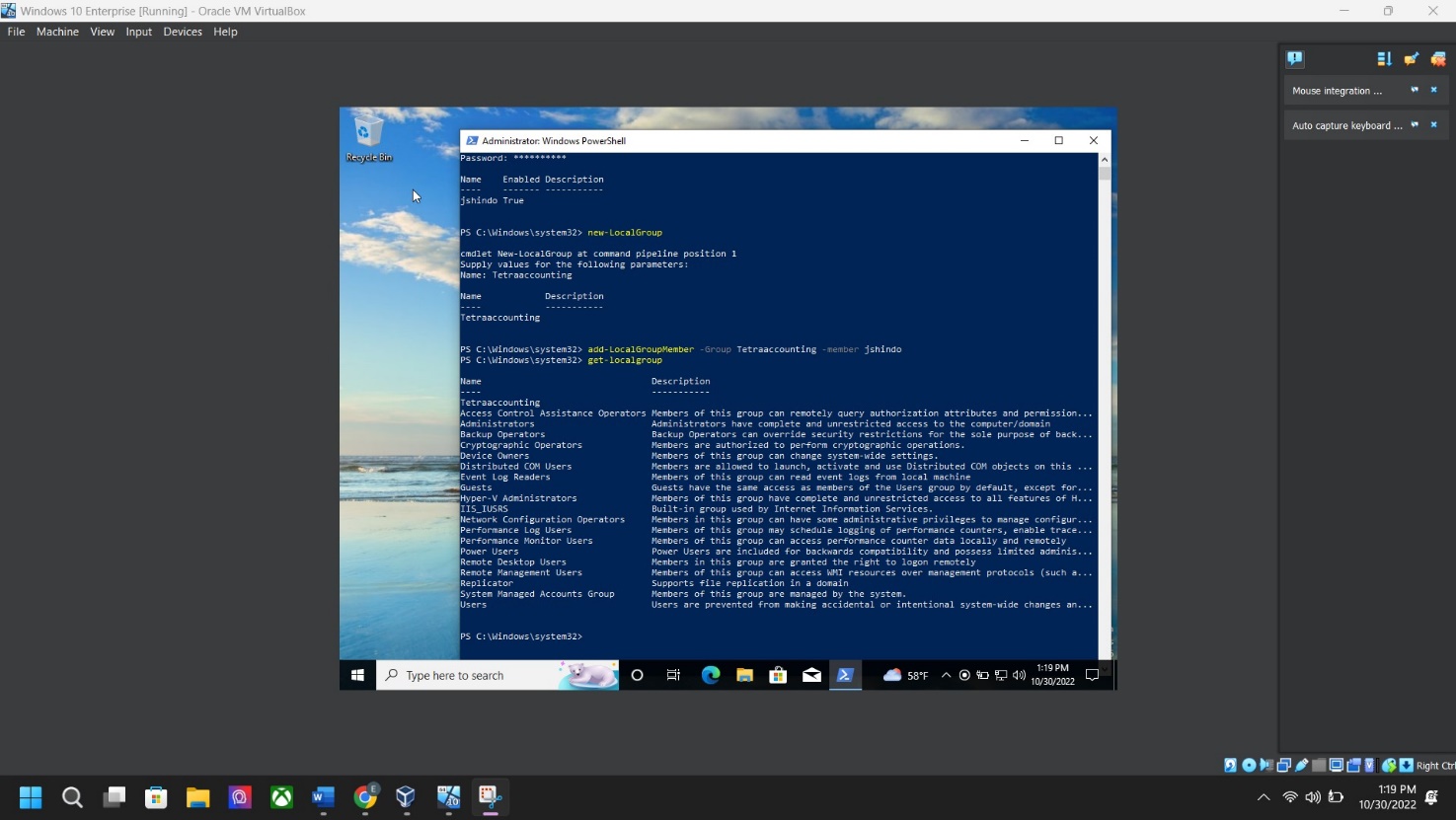
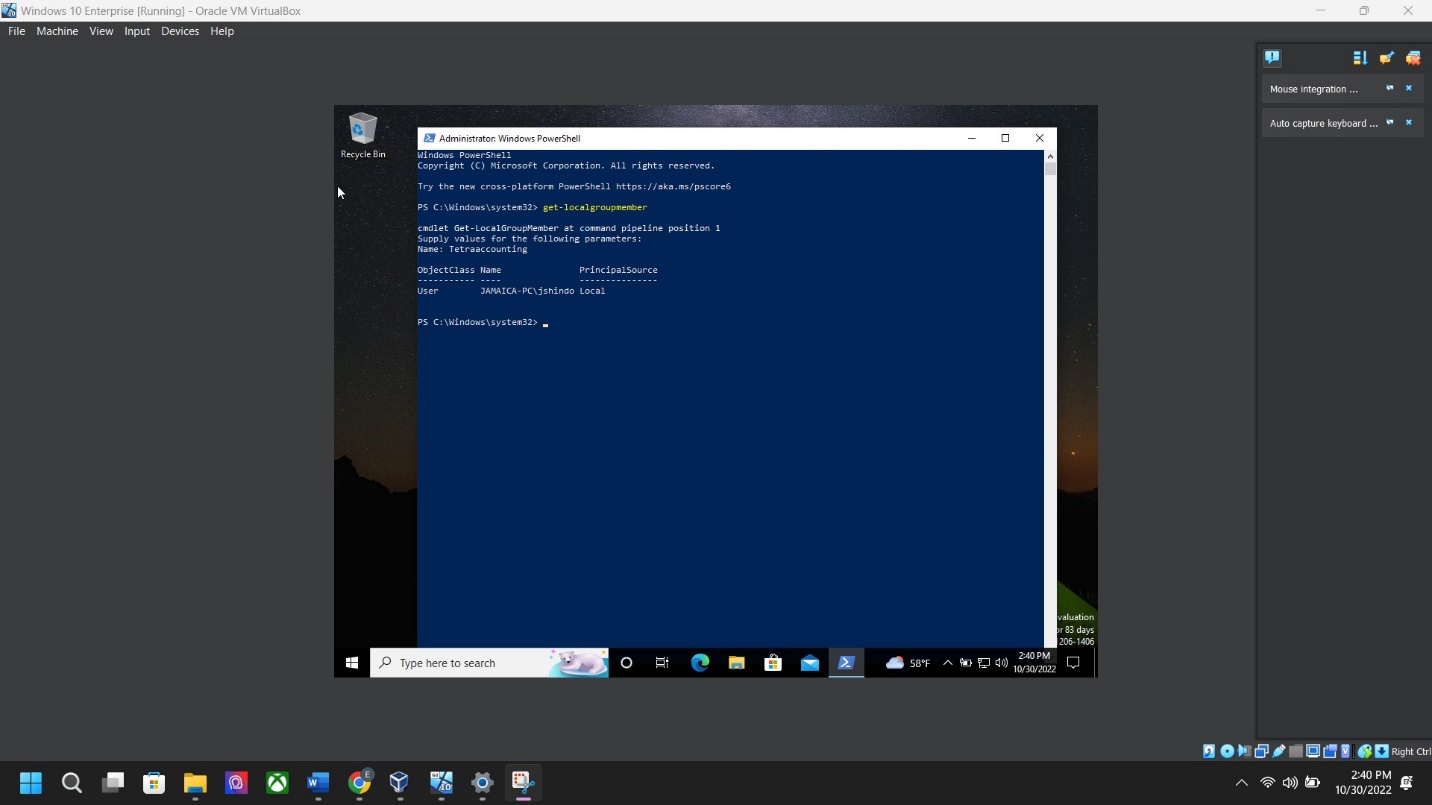
VERIFY:
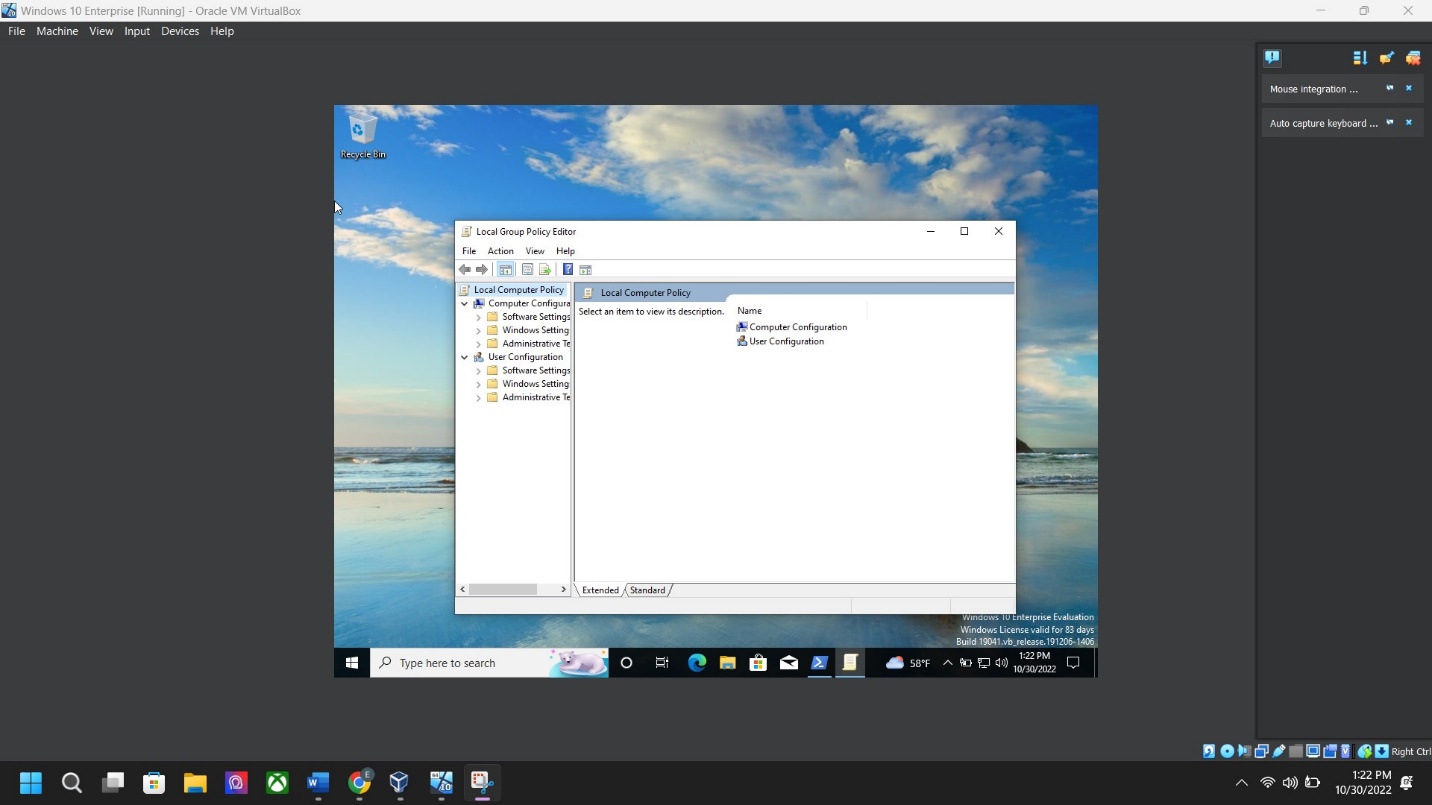
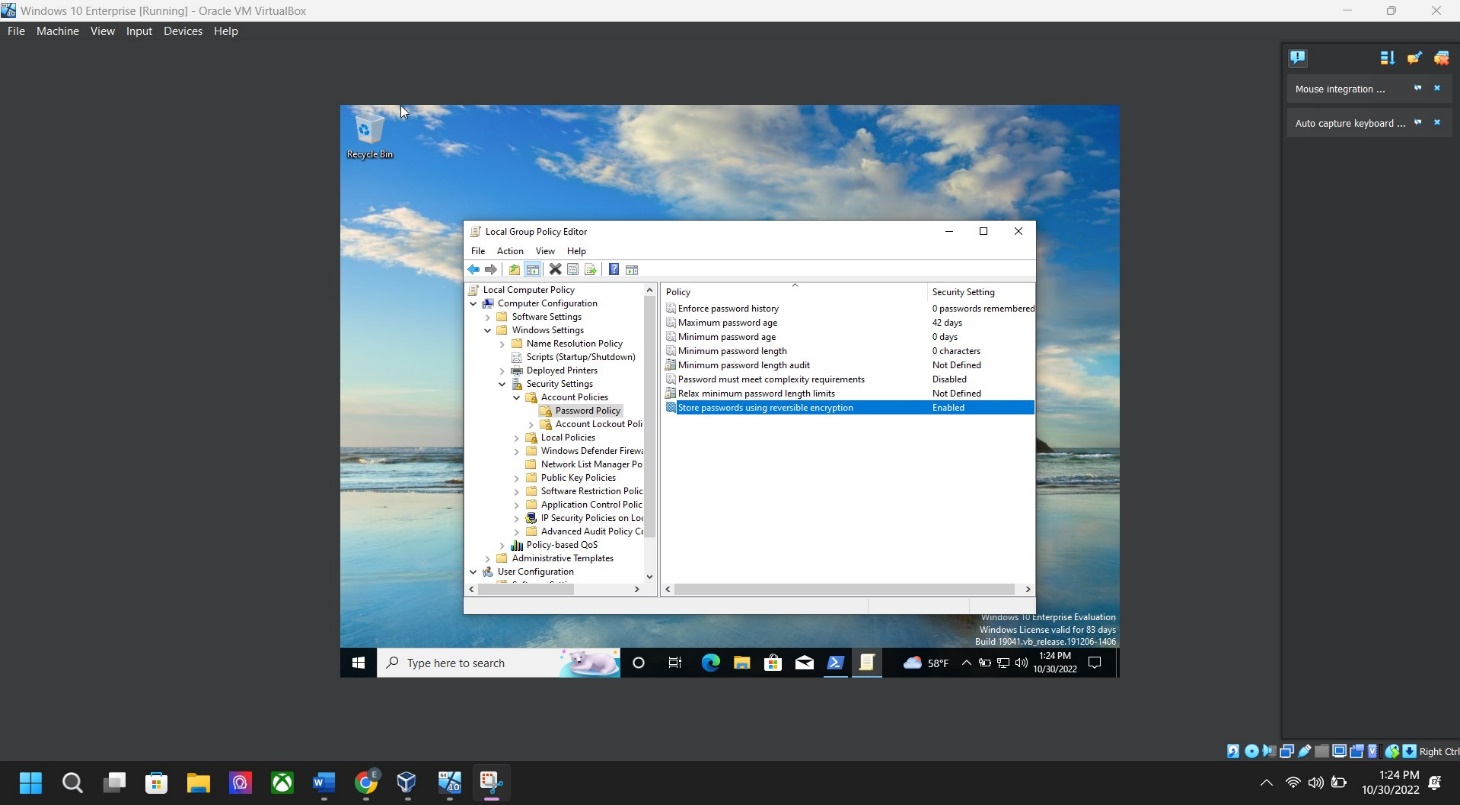
Step 6: Local group policy screenshot – type “gpedit. msc” in the search bar > Computer Configuration > Window Settings > Security Settings > Security Settings > Once in Security Setting: > Account Policies > Password Policy
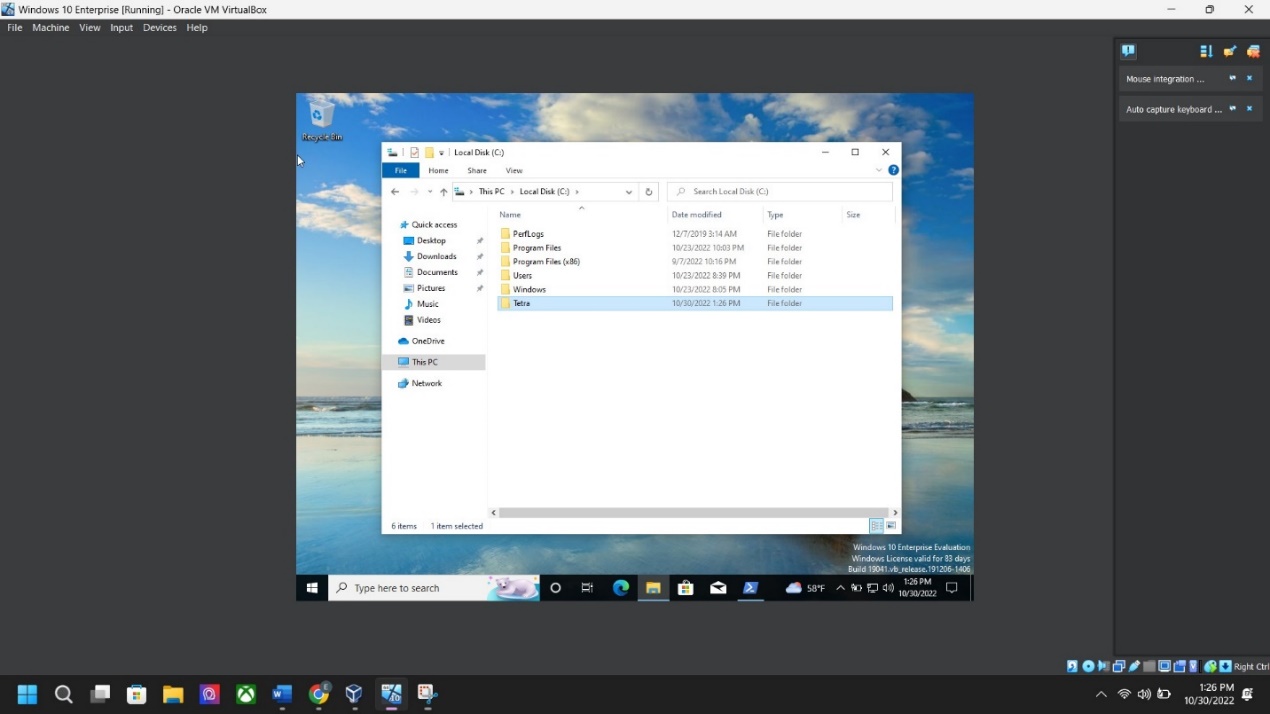
Step 7: Folder creation screenshot – Go to “This Pc” > Go to “C” Drive” > right-click any open space > click new > click new folder > name the folder “Tetra”.
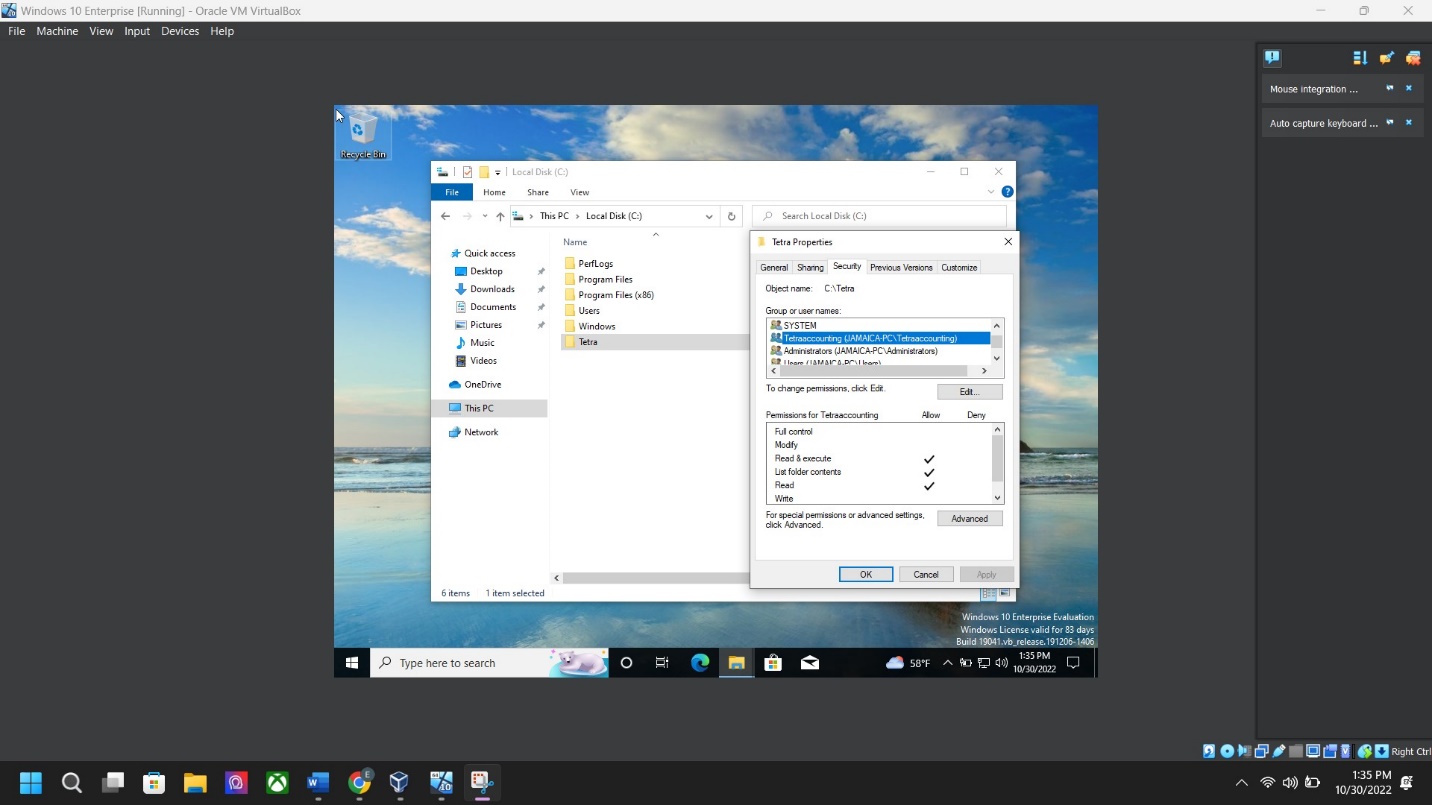
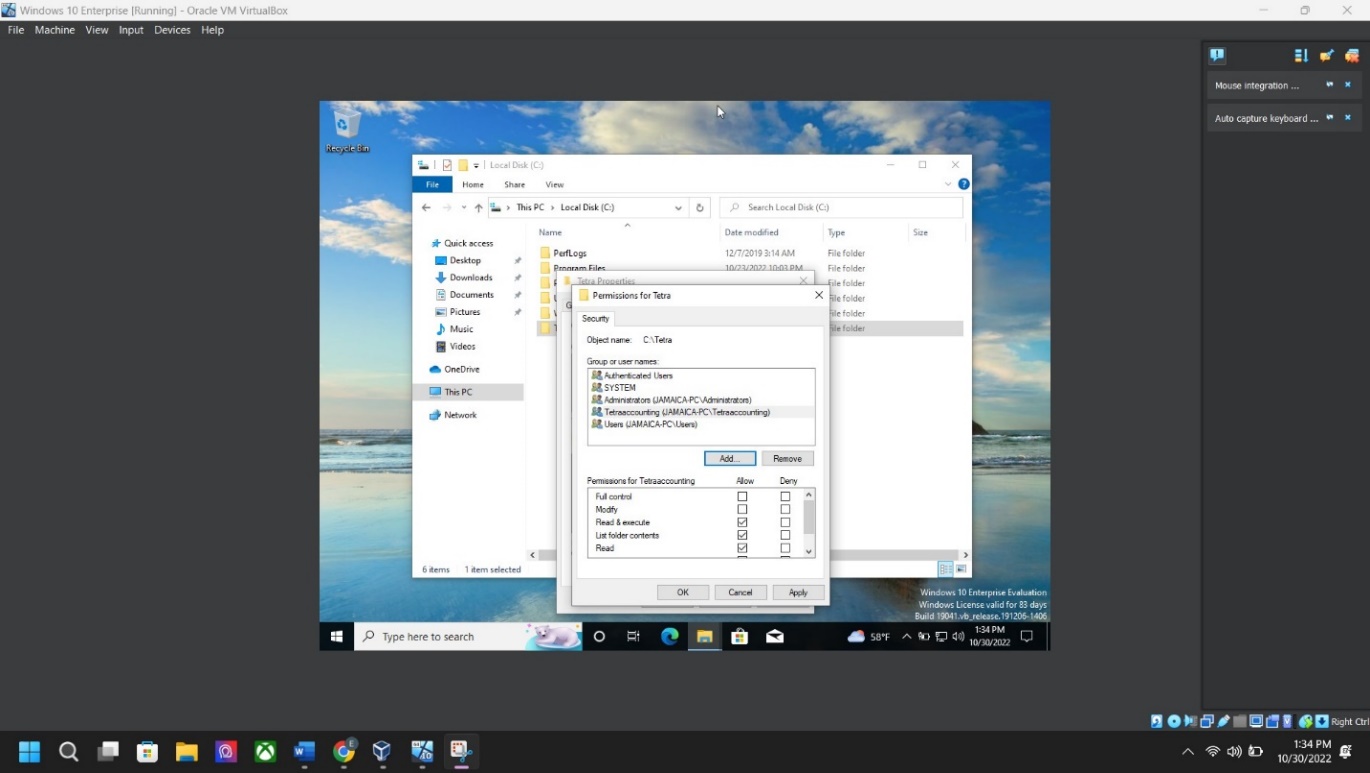
Step 8: Folder permissions screenshot – Right-click folder “Tetra” > Properties > Security Tab > Click “Edit” > Under Group or User Names: > Click on “ADD “type “Tetraaccounting” > click “Check Names” > Click OK > Under Permission Tab: > Click ALLOW > Click OK twice.
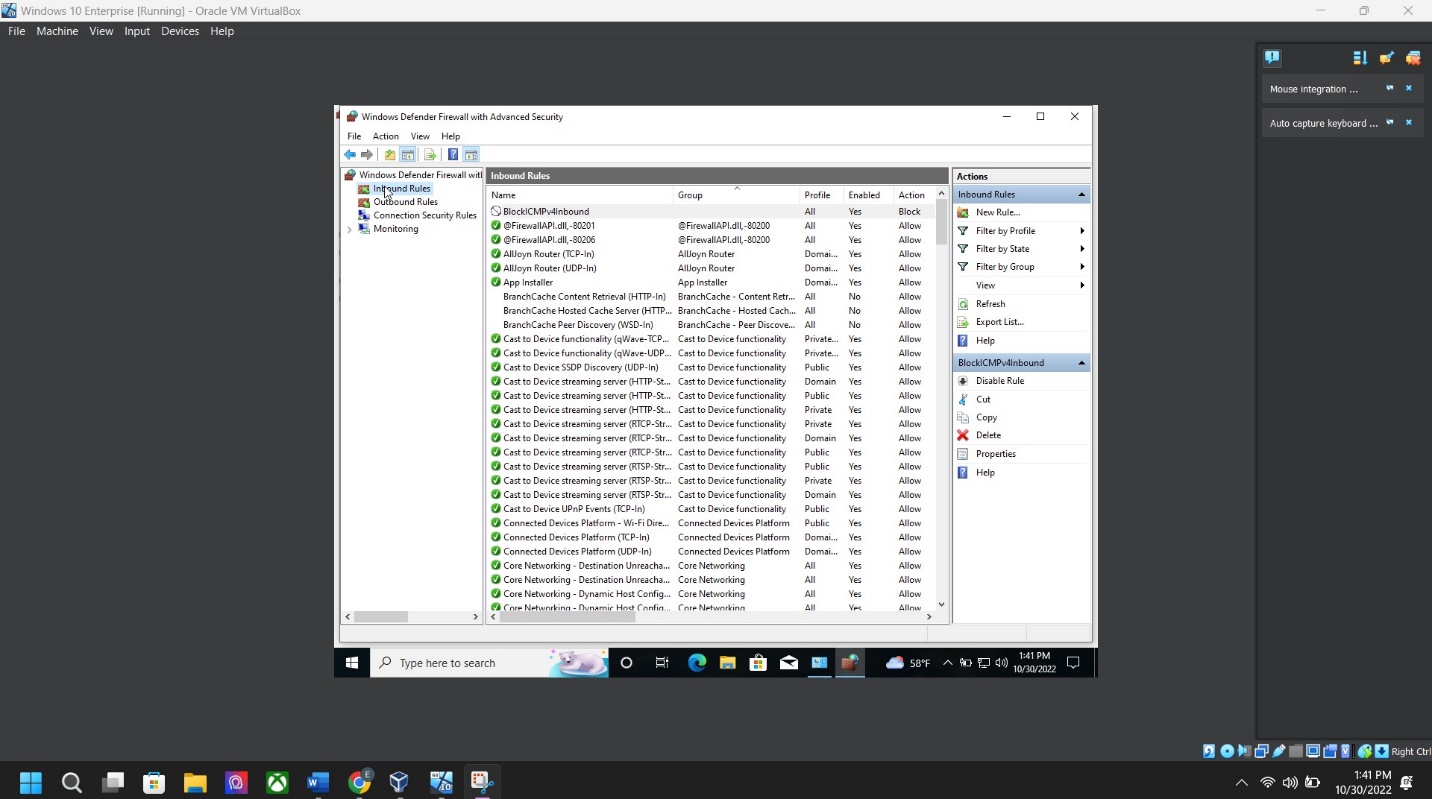
Step 9: Firewall configuration screenshot – Go to “Control Panel” > Windows Defender Firewall > Advanced Setting > Right Click: Inbound Rules > “New Rule”:
Rule type: Choose CUSTOM > NEXT
Program: Ensure “All Programs” is selected > NEXT
Protocols and Ports: Protocol Type: Choose ICMPv4 > NEXT
Scope: Click NEXT
Action: Choose Block the Connection > NEXT
Profile: Click NEXT
Name: I type “BlockICMPv4Inbound”
>Click Next and Finish
Windows 10 Upgrade Project Risk Factors
When an individual installs Windows 10 operating system, they must address the software and hardware requirements. The hardware versions must be aligned to fit the solution of the selected system. The hardware solutions must be vectored towards meeting the organizational needs. Therefore, it is worth ensuring that primary factors are met by making decisions tailored to fit the organization’s options. Microsoft offers numerous options to foster the needs of various users (McKeown et al., 2019). First, the organization must consider recruiting the best architect for use in the installation process. It is essential to have the best team because it will offer the organization a chance to explore its decisions. Most decisions will be made during the organization, and the results will conform to the experiences.
Among the significant issues that must be addressed is the architectural design or modes the organization will use to do installations. Windows 10, a new OS, requires users to determine the manufacturing year of their host machines. Some software will not function efficiently unless updated to meet Windows 10 OS functionality (McKeown et al., 2019). The old machines are prone to be incompatible with the new operating system. Nonetheless, ensuring that the hardware requirements, such as RAM and ROM, should be more significant so that the functionality of the OS is not impaired (McKeown et al., 2019). Windows 10 will be efficient when the hard drive space is more significant. Efficiency will be fostered when users can use the OS without hanging or buffering. It is essential to consider factors that shape decisions made by system usability because it enhances the achievement of intended goals. It is risky to install Windows 10 without considering the interface and architecture. Windows 10 interface is different from the Windows 8 interface. Understanding the changes is ideal for ensuring a smooth transition and interactions.
Sources / References
Arshad, M. R., Hussain, M., Tahir, H., Qadir, S., Ahmed Memon, F. I., & Javed, Y. (2021). Forensic analysis of Tor Browser on Windows 10 and Android 10 Operating Systems. IEEE Access, 9, 141273–141294. Web.
McKeown, S., Russell, G., & Leimich, P. (2019). Fast forensic triage using centralized thumbnail caches on Windows operating systems. The Journal of Digital Forensics, Security and Law. Web.
Singh, B., & Singh, U. (2018). Program execution analysis in Windows: A study of data sources, their format and comparison of Forensic capability. Computers & Security, 74, 94–114. Web.
