Abstract
Windows and Linux are operating systems environments with significant differences that IT staff needs to be informed of when making decisions about the most appropriate software to adopt for any specific computing environment. Security is one of the most critical differentiating components between Linux and Windows considered in the discussion as user programs and data at corporate and individual levels get majorly concerned about the safety of their files and data. The Linux kernel architecture is modularized enabling programs to run independently of the other programs resident in the kernel.
This does not allow damaged programs to access and damage other programs in a Linux environment. That enhances the security rating of Linux’s at different user levels. On the other hand, Windows kernel programs are packaged into a single kernel and rely on remote procedure (RMC) mechanisms to invoke actions in other machines. The RPC mechanism enables security holes inherent in Windows to be exploited to breach system security by responding to requests from user programs with the potential to cause damage to other files.
However, other critical issues discussed include the total cost of ownership issues and the reliability of software platforms, vendor lock, migration constraints, device drivers, and memory management to crystallize the differences between Windows and Linux in making informed user decisions.
Introduction
A debate has been raging on between proponents and opponents of Linux and Windows operating systems in the security, usage, total cost of ownership, and reliability issues. In addition to that, other comparative areas that have been of major concerns in deciding between the software products is on vendor lock issues, migration from one hardware and software platform to another, device drivers on both operating systems environments, and memory management strategies, and security as a critical area of concern particularly at user and corporate levels.
To crystallize the differences between the two software products, a detailed research and discussion was ensured in this paper considering the merits and demerits of open source and proprietary software in relation to user benefits and copy right laws and patent rights. The research goes further to discuss in detail findings about security issues based on design considerations of both Linux and Windows. The Linux kernel architecture is modularized enabling programs to run independently.
Therefore another program cannot be affected by a corrupted or damaged program resident in the kernel. That ups Linux’s security rating. On the other hand, Windows kernel programs are packaged into a single kernel and rely on remote procedure calls to enable communication to be invoked in any remote machine. The RPC mechanism enables security breaches to be easily implemented on Windows programs since the mechanism can be used to invoke programs to run and perform tasks on a remote PC without the explicit authority of the user. In addition to that, once corrupted programs are allowed to run, they easily spread damage to other kernel programs causing such undesirable harm. The report culminates with a conclusion on about the findings and choice the IT staff can take.
Literature Review
Open source and Proprietary software
Windows and Linux operating systems are designed with unique merits that distinguish them from each other. Windows is proprietary software that allows users to access the compiled program without accessing program code while Linux is open source software that allows users to access programs along with program code. Linux allows programmers and users to examine the code associated with respective programs allowing them to modify the code to meet specific user requirements.
Therefore, Linux provides users with the flexibility required to use their innovative skills besides allowing them a greater degree of flexibility to provide cost effective solutions. However, with Windows OS, inaccessibility to program code does not allow users to modify and tailor or customize programs to meet specific user need. Despite the advantage associated with Linux, windows products have for a long time dominated the market as products are already tailored to meet user needs before releases are made into the market (Bozman, Gillen, Kolodgy, Kusnetzky, Perry & Shiang, 3).
Comparatively, Linux is open source software that provides a platform for a network of different expertise in software engineering to write and improve on existing software exploiting the synergy in their skills while contributing to better, more efficient, and secure Linux software products. That implies that available Linux software products can be re-written with new enhancements and redistributed for use in the IT industry and the corporate world. In addition to that, no stringent distribution regulations are binding on newly written software.
However, redistributed software demands that program code to be made available for modification or enhancement or as may be seen fit or appropriate by the receiving party. Therefore, in terms of ownership, no discrimination accounts for the Linux’s distribution and product ownership (The Top 10 Reasons to Switch to Linux, 2).
On the other hand, windows are a proprietary software product that is bound by regulatory constraints in its distribution and usage. Therefore, patent rights and copyright laws apply for Windows. That implies the Windows software cannot be modified except under strict licensing to specific firms with stringent distribution restrictions. Typically, a user who purchases windows product is issued with a license and cannot access the underlying software code as it is contended that the underlying program code is bound by intellectual property rights. Therefore, for windows, intellectual property rights hold and are enforceable by copyright laws (The Top 10 Reasons to Switch to Linux, 4).
Despite the distinguishing features of each of the two software products, each has its own merits and demerits when applied for use in industry. It is important to discuss in details the meriting and de-meriting factors to crystallize the differences between windows and Linux that users should identify before they go for any of these (OS The Top 10 Reasons to Switch to Linux, 3).
Linux is open source software and seems to outdo windows in various aspects. Linux has a total cost ownership (TCO) advantage over windows because it is free accessible. Implying copyright laws and patent rights are not enforceable components in the Linux environment. In addition to that, the cost of hardware and supply chain administrative expenses trend downwards for Linux software products. A number of research findings suggest that the cost of running networks operations on Linux is far much lower than running networks on proprietary software platforms (Linux vs. Windows Total Cost of Ownership Comparison.
That is reinforced by the cost on productivity of the Linux operating environment, and the stability and security features associated with the open sources software. On the other hand, Windows products are expensive and deny users free accessibility besides copy right laws and patent rights being enforceable components in the windows environment. In the industry application, different corporate organizations have identified the lead in total cost ownership (TCO) of Linux as a driving force behind its widespread acceptance. Linux allows open source system developers to modify and evolve code at a fast pace compared with windows which relies on their own in-house developers (Linux vs. Windows Total Cost of Ownership Comparison, 3).
However, other researchers contend that the TCO for Windows seems to be lower than that of Linux. In support of that argument is the fact that ongoing costs are influencing variables in determining the overall cost of the software product. These include staffing costs, labor-intensive costs, and other related costs. On the other hand, hardware and software acquisition costs have been identified to contribute an insignificant cost to the total cost of ownership. Typically, the argument is based on the fact that the routine time required for the IT staff to maintain IT related infrastructure base on the Linux and Windows systems differ by a significant margin.
Comparatively, staffing costs for Windows have been identified to be significantly lower than staffing costs for Linux (Windows® vs. Linux® in Corporate Environments Information for IT managers. These costs have been identified to be inherently influenced by the immaturity of Linux, a gap that could be breached with time as Linux becomes increasingly available in the market and as IT professionals become more experienced in the use and operation of the Linux operating system. That approach is proactively influenced by system management tool vendors who have facilitated the supply and use of Linux in the market (Windows® vs. Linux® in Corporate Environments Information for IT managers, 3).
Security
Research and other industry findings indicate that the Linux operating system provides a secure platform from attacks typically because of the design and development methodology of the software. Typically, the security features incorporated into the Linux operating system addresses the needs for programmers who have had a hand in the creation of the software besides the issues that concern system administrators.
The main driving force behind the development of Linux is robustness and security as a major concern. These security features, according to research reports, provided a further impetus to the shift from Windows to Linux operating system platform by many organizations. Typical examples include the U.S department of defense specifically because Windows operating system suffered severe system security holes subjecting data and programs to potential risks (Ramadan, 4).
All these security enforcements have been achieved by utilizing expertise to provide security solutions in computing as a collaborative effort. Essentially, the development of Linux as an open source product was based on the theory of many eyes. Based on that argument, many expertise have been collaboratively devoted in analyzing the software code subjecting the software to harsher scrutiny with the advantage that new versions or parches are developed early enough to cushion users from vulnerabilities of security attacks (Ramadan, 4).
Issues related to security on the Windows environment indicate that the Windows has minimal chances of being subjected to the rigor and scrutiny of the software code as the number of programmers developing the software is limited. In addition to that, the development team is not open to exploit other programming expertise available in the IT world today. Thus, the Windows operating system is vulnerable to security attacks as has been evident in the industry (Ramadan, 4).
Findings indicate that security attacks have resulted in exponential losses including corruption of confidential files and data at the corporate and individual levels. However, the possibility to patch up security holes in both operating systems is possible. Comparatively, therefore, security patches can be applied in real time with Linux while Windows providing patches which require further attention. The aim of developing Linux was to address security issues that had been inherently identified with windows (Ramadan, 4).
Sometimes security can be pegged on the design of the operating systems. Based on that argument, a comparative analysis of windows and Linux designs will serve to crystallize the reason for a specific OS (Ramadan, 4).
Windows Design
Based on the design, Windows for most part had been a single user system that has in the recent past emerged into a multi-user model. In its design, Windows came with the inbuilt ability that allows user access to the entire OS. That implies that critical files of the system are subjected to the disposal of the system user exposing the whole system to intentional or unintentional interference. In addition to that, because of the failure of the OS to separate users from critical files that the functionality of the system relies on, Windows is susceptible to the destructive effects of malware and Trojan horse programs.
However, the shift to a multi-user model has signified the trend in Windows designs in the recent developments. Typically, Windows 2003 reflects features unique to a multi-user system. However, irrespective of these improvements, Windows still experiences security holes, a critical security concern in the corporate world (Probert, 2).
The packaging of program features into a single package in the kernel makes windows a monolithic architecture. All windows services are coupled and interdependent in the kernel. That makes Windows less competitive. Thus, the issue of independence is overly abridged while the tightly coupled components such as Internet Explorer expose the whole system to security risks and in the event of one component getting affected, there is the possibility of the infection spreading to other system components and corrupting the functionality of other system files (Probert, 2).
On the other hand, the possibility of a flaw specific in graphics rendering does not allow Windows the flexibility to separate specific graphical rendering features into specific functionalities. Therefore, the issue does not limit corruption of specific graphical rendering files from spreading throught the system and causing damage to the whole windows operating system components. Thus, reinforcing the argument that flaw in graphical rendering schemes has the possibility of destroying the whole system functionality (Probert, 2).
Another charactering element of a monolithic system typical of the Windows OS is its instability. That allows instability when changing any system component since these components show high interdependence. That has the ability to cause a cascading effect on all applications that run on the system. Typical scenarios have been documented in the history of usage of the Windows OS specifically unique to Windows XP service pack 2. In this case, reported failures of other system components and applications when trying to change one component of a machine have been frequent (Probert, 2).
Another disadvantage with windows is its overdependence on remote procedure calls (RPC). RPC exposes the OS to potential security risks since other computers in a network can invoke functions in the user’s computer to perform tasks that may not have been explicitly directed by the user. It is possible for potential attackers to exploit the flaws that may be inherent in the RPC mechanism to instruct even remote computers to perform certain tasks that may be a breach of security and confidentiality.
The RPC mechanism is central to the functionality of Windows OS. Therefore users are left with no other option as they cannot disable RPC’s mechanisms in the Windows OS. It is important to note that RPC is one of the most important sources of risks that impair the functionality of the Windows OS rather than the applications that run on the OS. However, blocking the RPC port and services that attack RPC provides the best mechanism for dealing with vulnerabilities that the RPC mechanism is subjected to.
That is the case with many worms such as the slammer worm that impaired the functionality of systems running on the Windows operating system with catastrophic consequences. That was typically due to the exploitation of the security vulnerability of the RPC mechanism when used over the internet. On the other hand, Linux comes with a range of design issues that up or trend the software component positively.
Linux Design
From the design perspective, Linux has experienced limited instances of system security lapses than Windows. It has been arguably demonstrated that security breaches of the Linux OS have been exclusively due to holes in configuration settings. Typically, a large number of users in surveys conducted revealed that 90% of users have not experienced the problem inherent with viruses and other malware programs with their potential risks to user data and programs choosing between the two products (Windows and Linux for High Performance Computing, A Crimson Perspective, 4).
One of the design elements that distinguish Linux from Windows is the modular design that is typical of the Linux operating system. While, as discussed elsewhere, Windows is monolithic, Linux exploits the concept of modular design of its kernel software components. Implying that the Linux kernel consist of software components that are not tightly coupled together, hence only interdependent. Typically, therefore, any flaw in any system component does not put any other component does not other system components to risk. It is also important not note that the Linux kernel supports the aspect of modularity and where the modules are interdependent, as mentioned above. It is also useful to note that the Linux kernel is rarely vulnerable to potential damages (Tanenbaum & Albert, 4).
It is also worth noting that while Windows graphic drivers run from the kernel of the OS, Linux on the other hand does not allow graphic drivers to run from the kernel, thus sparing the Linux OS the potential vulnerability of the destructive effects of malware and other programs (Khetan, 3).
On the other hand, it is evidently noteworthy that Linux does not overly rely on the RPC mechanism. Implying network defaults are disabled on the Linux OS environment. Linux does not allow programs to access the network without due configurations. Therefore, these programs cannot take instructions from the internet or any other networked source. That implies that when the user wants to access the internet, one must turn on supporting features with explicit configurations to enable a machine to ignore requests from the network and only respond to local requests or as configured (Khetan, 5).
In addition to the merits significantly advantageous with the use of Linux, Linux can be installed and administered from a remote location making the remote server more secure compared to a local server. That implies that one can log into a computer with limited privileges and restrictions to a specific user. At this point, log in administration can be achieved through web based interfaces. That essentially implies that the any security hole can not affect the server, but affects only the user’s level account leaving the rest of the system unaffected by the malicious program. Typically, the security vulnerabilities due to the modularity of Linux compared with Widows OS that incorporates its entire functional programs into the OS kernel places Linux at an upper hand compared with the Windows OS.
Reliability
Linux’s robustness and reliability is demonstrated in the ability of the software to offer real time computing solutions, efficient hardware and software utilization, and intelligent use of hardware resources. Linux provides the multiprogramming abilities making system updates more efficient without the need to reboot a computing system. A comparative study of Linux with windows on reliability indicates that hardware that runs the Linux operating systems is less vulnerable to crashing than windows (Khetan, 6).
Vendor lock
Proprietary software suffers from the disadvantage of vendor lock. On the other hand, the Linux operating system (OS) provides platform for industry users to negotiate the cost of appropriate software for their enterprises based on a range of offers by different vendors. Noteworthy is the compatibility that characterizes Linux. Linux can be installed or deployed on different hardware platforms allowing organizations to benefits from low cost software that meet organizational computing needs. Thus, organizational bottom lines are enhanced as the need for more expensive proprietary software is not the concern. Linux offers computing solutions that are characterized by independence providing flexibility to mission critical organizational business requirements (Maiorano & Marco, 4).
Migration
Transforming an organization’s IT infrastructure does not demand complete and costly transformations or overhauls with an organization on a Linux operating system platform. That implies that the efficiency of organizational infrastructure and hardware lifespan are extended, a cost saving advantage. That advantage is reinforced by the ease of migrating Linux servers while ensuring a flawless transfer of data and files between servers in addition to optimizing processor power. Migration for Linux servers in a heterogeneous environment ensures critical applications are maintained while deployment can involve a thoroughly scheduled testing to establish a secure environment (Khetan, 7).
On the other hand, Linux applications can be tailored to address individual corporate needs. That holds true if an organization employs experienced staff enabling customized applications to effectively fit organizational requirements. Despite the advantages that characterize Linux over windows, it is worth discussing its demerits to allow IT decision makers make informed decisions that impact positively in designate areas of choice. Organizations which thrive the use of Linux as the operating system platform corporate stability over the time has lacked insufficient support (Khetan, 7).
On the other hand, Linux has been disadvantaged by a steep learning curve. That is due to a lack of universal interfaces compelling further training on new user interfaces that come with new software products. The issue of portability is further reinforced by a myriad of Linux software product distributions. It is worth noting that different distributions are characterized by different software deployment approaches.
Another supporting feature of Linux as a disadvantage different software installation demands with the possibility of the disadvantage of resulting into a dark cloud. Due to the popularity of the windows OS, many users find it difficult to shift from the windows platform to the Linux platform. That is typically due to the advantages that characterize the windows operating system as discussed later in the paper. On the other hand, windows operating system comes with merits over the Linux operating system as discussed below (Tanenbaum & Albert, 9).
Typically, windows have been identified to be user friendly by providing a graphical user interface working environment. In addition to that, windows provide a simplified installation guide for the user on its installation. On the other hand, Linux does not provide a user friendly graphical interface. In addition to that, Windows offers a variety of software choices with new applications that are tailored to meet user and corporate needs (Khetan, 8).
However, Windows suffers from the disadvantage of an insecure system hence subjecting corporate data and programs to vulnerability from attacks. In addition to that, a comparative study of Windows and Linux indicates that Windows suffers from instability that is susceptible to virus and worm attacks. In addition to that, OS incompatibility with other software applications causes monetary losses especially when migrating windows servers of an organization’s IT infrastructure.
In addition o that, Windows does not provide the flexibility to configure the software to meet individual and specific corporate needs. However, the need for further detailed comparisons of windows vs Linux is necessary to crystallize the differences for IT specialists to make informed choices in meeting individual and corporate IT needs (Khetan, 8).
Device drivers
From the perspective of device drivers, the Windows OS provides sufficient derivers during installation making the OS functional. It is also possible that generic drivers can be used in a Windows environment to provide the functionality required after the OS’s installation. In addition to that, Windows provides a variety of drivers for update purposes that follow after the base software has been installed. On the other hand Linux provides device drivers as modules. That implies that the drivers do not need user intervention when being installed. In addition to that, the software modules are packaged and installed at the request of the user. It is also important to note that when migrating in the Linux environment, the OS has the ability to detect new drivers, a unique charactering element with Linux and de-meriting the Windows OS (Maiorano & Marco, 4).
Memory Management
Memory management is one of the critical functions of operating systems. That calls for a comparative study of the memory management schemes of Windows and Linux to crystallize key differences for software vendors and IT staff into selecting the most appropriate OS software specific to specific operating environments. An operating system should provide fair and efficient allocation and use of available memory to up or improve the performance of a computer’s hardware system.. Typically, the concept of memory management allocates various responsibilities to the OS. These responsibilities include relocation where programs running in the CPU are swapped into main memory based on storage space demands and out of main memory as the memory manager may determine to be fit.
On the other hand, the operating system is responsible for memory protection where executing processes are protected from writing into the memory locations of other processes. Other responsibilities of the OS is to ensure sharing a single program segment, physical organization of memory where program and data can be stored either in volatile or long term memory. These memory management responsibilities are unique to each OS. To that end, both operating systems have memory management schemes that typically define of each OS environments as discussed below (Tanenbaum & Albert, 45).
Windows Memory Management
The memory management unit (MMU) is responsible for managing memory in a Windows operating systems environment. In a typical Windows 2000, the OS partitions memory into fixed page sizes as illustrated in fig. 1 below.
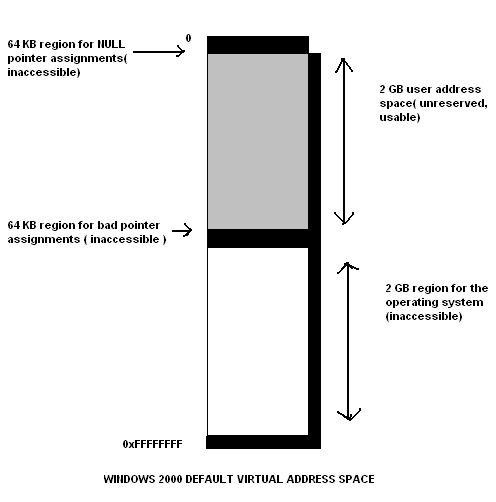
The paging scheme can make pages to be available when either process have been swapped out or simply not in use, contiguous memory space may be reserved by virtual memory when reserved storage space is used up, or these pages may be put aside in to minimize disk space usage, and enables threads to identify and estimate their memory requirements. Paging in the Windows OS environment, specifically with Windows 2000 allows programs to be assigned fixed memory partitions following certain assignment conventions. However, processes are moved in and out of storage space to avail memory for use.
Typically, when memory is not enough, the virtual memory manager takes over the memory management responsibility by recovering through memory displacement schemes. That strategy reduces the resident set that determines the variable allocation of memory allocations (Linux vs. Windows The Bottom line, 3)
It is important to note that user processes in Windows 2000 uniquely identifies memory sizes of 32 bit address spaces and assigns to each process a memory size equivalent to 4 GB. The operating system assigns itself memory by default at this point. Typically, an equal memory space is assigned to the OS and user process. However, it is possible for user processes to occupy more memory space allowing the OS to occupy less memory space of the total 4 GB of memory. The latter memory allocation scheme is in the ratio of 3:1 respectively. However, a comparative discussion of Linux memory management schemes as discussed below id necessary to crystallize the difference schemes employed by Linux and Windows (Tanenbaum & Albert, 36).
Linux Memory Management
In the Linux operating systems environment, three typical structures define the virtual memory addressing schemes. These include page directories which are loaded into main memory when a program is running in the CPU where processes always take residence in single page directories. On the other hand, a page middle directory forms another component of the virtual memory addressing scheme. The concept is defined by an allocation strategy that covers several pages.
This memory allocations strategy also includes a page table. A page table points always to a specific virtual page specific to each process. In comparison with Windows, Linux can accommodate a platform independent hardware processor with a memory size of 16 bits (Callitrope & Withington, 3).
The page allocation strategy for Linux puts to use of a buddy mechanism when processes read from or write to memory. The buddy algorithm takes care of the allocation and de-allocation of main memory during process swapping. On the other hand, the page replacement algorithm for Linux is based on the clock algorithm. Each page in this algorithm is characterized by use and modify bits in main memory. However, a byte age variable replaces the use bit in the latter algorithm.
On the other hand, kernel memory is specific to virtual memory management strategies. Thus, a linked list typically used by each memory sizes or chunks. Thus, both memory management strategies are typically different and unique with each operating system as discussed above. It is important to discuss briefly process management in both windows and Linux OS environments as further differentiating strategies (Callitrope & Withington, 3).
Process Management
Process management is one of the responsibilities of the OS. In the Linux operating systems environment, a running program is described as user running. When the running process enters the kernel by issuing a system call, it acquires a kernel running state. When the kernel, using an appropriate scheduling algorithm, takes control of the CPU to execute, it is said that it is ready to run. However, the process can acquire another state referred to as Asleep in memory if acquires a state where it is waiting for an event to enable the process execute. On the other hand, the process can acquire a ready to run state when it is waiting for the swapping software to load it into memory to run.
The next state is typically referred to as sleeping, swapped. This state describes a process waiting to be moved into secondary storage after the occurrence of an event. These events and process states are illustrated in fig. 2 below (Tanenbaum & Albert, 10).
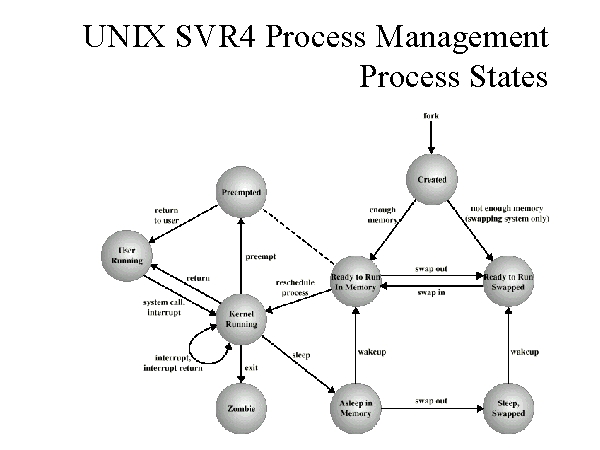
Other process states unique to the Linux OS environment include preemptive a situation where a process exits the kernel and goes to user mode.
However, processes that have been created but have not been into the running mode are referred to as created. Nonetheless, a process can be erased and unavailable but leave a parent process behind, such a process is referred to a zombie (Tanenbaum & Albert, 9).
Discussion and Point of View
Raging discussion and arguments about the differences between Linux and Windows have been going on for some time. Several industry perceptions about Linux and Windows operating systems exist today. However, a comparative research on the both software environments with typical considerations of critically characterizing elements have been visited to bring out the differences especially for IT professionals to be better informed in selecting the most appropriate OS that can meet specific needs in specific user environments.
A number of discriminating but comparative issues such as open source and proprietary software, the total cost of ownership, security issues, the design of both software products, and reliability have been discussed in detail. Other issues detailed in the discussion include vendor lock and migration between hardware platforms. Device drivers, and memory management in both environments have been considered with a culmination of a discussion of process management in the Linux OS environment have served to clearly bring out the rationale of selecting one OS over the other.
Linux is open source software that is not stringently bound by copyright laws and patent rights. The costs associated with these laws and other related requirements do not apply for the Linux OS, further making the product easily available and at a minimum cost of ownership. However, opponents argue that since Linux is not well distributed in the market as is the case with Windows, the total cost of ownership (TCO) for Linux is far much greater than that for windows.
That is partially because there is less IT staff trained in the maintenance and use of Linux and related products compared with windows. However, it is agreed in the It industry that once Linux becomes more easily available, the TCO may drastically decline in favor of Linux, placing Windows at a disadvantage regarding the issue of TCO. Further, the argument is reinforced by the fact that the routine time required for the IT staff to maintain IT related infrastructure base on the Linux and Windows systems differ by a significant margin.
Comparatively, staffing costs for Windows have been identified to be significantly lower than staffing costs for Linux. These costs have been identified to be inherently influenced by the immaturity of Linux, a gap that could be breached with time as Linux becomes increasingly available in the market and IT professionals become more experienced in the use and operation of Linux operating systems environment.
From the above discussions, it is evidently clear that Windows OS is a monolithic architecture where programs and other OS features are integrated into a single kernel, the core of the OS. Windows comes with integrated services more tightly integrated to the operating system kernel making the OS vulnerable to damage in the event of an exposure to an intruder such as malware. On the other hand, Linux architecture is modular and the main driving force behind the development of Linux software is robustness and security. These security features, according to research reports provided a further impetus to shift the to the Linux operating system platform by many organizations such as the U.S department of defense.
That was specifically because the Windows operating system suffers from system security holes. Windows system communication is overdependence on remote procedure calls (RPC). RPC exposes the OS to potential security risks since other computers in the network that is connected to the user’s computer can invoke functions in the user’s computer to perform tasks that may not have been explicitly directed by the user. However, Linux can remain functional by disabling network features and enable them to access specified files and sites without caring about foreign requests to perform unusual specific tasks.
Conclusion
A comparative study of Windows vs Linux is vital for IT professionals in making informed decisions on the right options that meet user needs at individual and corporate levels. Many issues considered in the study include security as a major component. Linux’s kernel architecture is modular, allowing programs to run independently of each other, thus minimizing the potential risk of infected and damaged programs spreading their corruption to all other programs in the kernel. On the other hand, Windows programs are packaged together its features into a single kernel and heavily reliant on the RPC mechanism for communication.
That makes Windows vulnerable to the potential destructive effects of infected programs and files. As an additional advantage, Linux is subject to rigorous security tests as thousands of programmers have access to the source code and can modify the code wherever a security hole is identified in the product, a fact not welcome in Windows. However, despite the fact that the TCO for Windows is lower than that of Linux, yet the situation is trending in favor of Linux. That has reinforced the need for corporate users to revise their IT infrastructure procurement policies as cost savings, migration, interoperability, security, and hardware lifespan have favored the use of Linux at different levels of OS platforms. It is only a matter of time before Linux acquires a large chunk of market share.
Works Cited
Bozman, Jean, Al Gillen, Charles Kolodgy, Dan Kusnetzky, Randy Perry & David Shiang. Windows 2000 Versus Linux in Enterprise Computing. n.d. Web.
Callitrope, P. T. Withington, Memory Management. 2011. Web.
Choosing between Windows and Linux for High Performance Computing, A Crimson Perspective, 2010. a crimson consulting group business white paper. Web.
Khetan, Gaurang. Comparison of Memory Management Systems of BSD, 2002. Windows, and Linux. Web.
Linux vs. Windows The Bottom line, 2001. Web.
Linux vs. Windows Total Cost of Ownership Comparison, 2002. Web.
Maiorano, Antonio, Paul Di Marco, Memory Management. Web.
Probert, Dave. Windows Kernel Architecture Internals. 2010. Web.
Ramadan, Mohammad, A. Linux vs. Windows Software Engineering Perspective. n.d. Web.
Tanenbaum, Andrew, s. & Albert s. Woodhull. Operating systems design and Implementation. 2006, Prentice Hall. Web.
The Top 10 Reasons to Switch to Linux, Alacos. n.d. Web.
Windows® vs. Linux® in Corporate Environments Information for IT managers, 2004. Web.