Introduction
- Ethics are concerned with placing value.
- They help determine whether an act is good or bad.
- These rules and are written into laws.
- The computing profession is no exception.
- It has guidelines on the conduct of its professionals (Pojman, 2012).

Ethics and computer crime
- Computer use was initially not regulated.
- This caused problems and guidelines had to be formulated (Barbara, 2011).
- With the freedom of the internet, new issues have emerged.
- Computer ethics seeks to address the menace.

Computer crimes
- Computer crimes are quite common today.
- This refers to any crime involving a network and a computer.
- The computer may be used in the crime or may be the target (Herman, 2004).
- Criminal exploitation of the internet is referred to as Net crime.

Cyber crime
- Cyber crime is a crime committed with the intent to harm an individuals reputation.
- It could be physical or mental harm, and directly or indirectly (MacKinnon, 2011).
- The crime is propagated by modern telecommunication such as the internet.

Malware
- Malware refers to computer virus or a Trojan.
- Viruses get into the computer without the user’s conscience (Michael, 2011).
- They are developed as normal programs.
- Viruses harm data stored in the computer by corrupting it.

Identity theft
- Identity theft involves a criminal getting and targets personal information and using it as their own.
- It can involve the hacker getting personal bank details (Michael, 2011).
- The hackers then uses the information for their own benefit.

Cyber stalking
- It means to use the internet to stalk someone.
- Many individuals leave personal information on the internet (Michael, 2011).
- This increases the vulnerability to cyber stalking.
- Cyber stalking is essentially a form of harassment.

Child pornography
- It is unbelievable, but the internet is used to exploit children (MacKinnon, 2011).
- Individuals make a lot of money from this crime.
- This presents an issue of critical concern.
- This is due to the nature of the crime and its implications in society.

Spam
- Spam refers to the numerous annoying emails.
- The annoying messages are illegal in many countries.
- A malware protected computer is used to prevent the spread of a spam.
- There are certain guides that were formulated to minimize computer crimes (White & White, 2006).

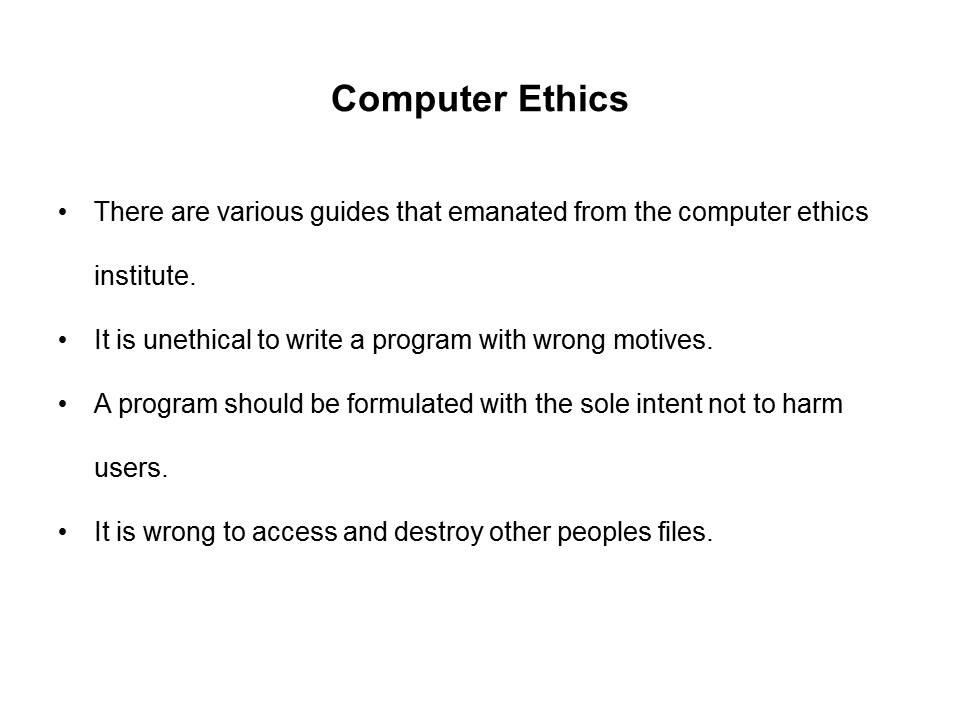
Computer Ethics
- There are various guides that emanated from the computer ethics institute.
- It is unethical to write a program with wrong motives.
- A program should be formulated with the sole intent not to harm users.
- It is wrong to access and destroy other peoples files.
- Generating and spreading computer viruses is unethical.
- Reading other peoples information is unethical.
- This is because it contravenes to their privacy.
- Using the computer to steal is illegal.
- This is computer fraud and there are laws against it.
- Using the computer to spread lies is unethical.
- Software books are guarded by intellectual property rights.
- It is thus unethical to use a product not that is not legally acquired.
- Hacking into unauthorized system is unethical.
- It is not legal to bypass authorization measures.
- Intellectual property piracy is prohibited.
- Coping another person’s work without authorization is unethical
- It is prohibitive to write a program that is harmful to society (Stephen, Maeve & Donald, 2003).
- Computer will be used to depict respect and consideration.
- The computer may be used in the crime or may be the target (Herman, 2004).



Conclusion
- Vulnerability to computer crime is evident.
- This is either through the internet or the computer network.
- It is important to be ethical to avoid crimes.
- Computer protection measures should also be applied to reduce computer crime.

References
Barbara, M. (2011) Ethics: Theory and Contemporary Issues, 7th ed. Belmont, CA: Wadsworth Publishing Co.
Herman, T.(2004). Ethics & Technology: Ethical Issues in an Age of Information and Communication Technology. Hoboken, John Wiley and Sons, Inc.
MacKinnon, B. (2011). Ethics: Theory and contemporary issues. Boston, MA: Wadsworth/Cengage Learning.
Michael, J. (2011). Ethics for the Information Age, 4th ed. Boston, MA: Addison-Wesley.
Pojman, L. P. (2012). Ethics: Discovering right and wrong. Boston, MA: Wadsworth.
Stephen, H. Maeve, C., & Donald, J. (2003). Management Information Systems: For the Information Age, 4th ed. New York, McGraw-Hill.
White, J.E., & White, J.E. (2006). Contemporary moral problems. Belmont, CA: Wadsworth Pub.