Introduction
The paper illustrates findings on the Internet of Things for homes and presents its benefits and challenges. Part 1 describes the future home, identifying the types of Internet-connected devices, the benefits such connections may offer, and the issues and challenges such links present. The implications include discussions on IoT devices, functionality, and services.
Part 2 provides a recommended policy concerning data collection, sharing, data usage, and protection of data collected. The privacy policy is an important document, the purpose of which is to inform the potential client of the services that the necessary measures are being taken concerning personal data. Hence, privacy policy details the service provider’s views and procedures on the information collected from customers. Additionally, the author identifies specific concerns regarding the IoT and its future.
The Future Home
Description of IoT at home
The IoT can be characterized as the unification of the virtual and real worlds with the help of many devices and sensors connected to the same network and providing interaction between machines and people. Wu et al. (2020) suggest that the Internet of Things (IoT) era started because of the rapid increase of computing technologies and intelligent devices’ usage. Yang et al. (2018) state that the IoT concept refers to the interconnection of many electronic devices into one network. The IoT systems usually consist of a network of smart devices and the cloud platform they are connected to.
Consequently, IoT facilitates our present-time life, including smart transportation, healthcare, and even home systems. According to Wu et al. (2020, p. 35), IoT connects many smart devices into one system, which allows humans to access enormous user data to enable exceptional smart products and services, “yield insights and train task-specified machine learning models.”
Yang et al. (2018) agree that IoT devices store, analyze, process, and interpret tremendous amounts of data. Modern technologies have significantly increased the possible frontiers of IoT applications. One area that contributes to a significant simplification of management and control over life support systems is smart home technology. Ali et al. (2017) admit that the smart home is the fastest expanding area of the IoT because it offers innovative and intelligent services. Therefore, the development of the Internet of Things influenced the progress of the concept of a smart home.
The IoT connects smart devices in the home into a computer network. Shouran et al. (2019) state that devices can productively interact with each other through Internet Protocol (IP) addresses. With the help of the network, devices exchange information and work in real-time at the user’s direction, but without his intervention. For instance, Yang et al. (2018) argue that the combination of IoT and home appliances and equipment helps make the home remotely controllable and smarter. Even though a smart home concept has been known since 1980, namely traditional home automation, nowadays it is developing and growing (Yang et al., 2018).
Notably, many start-ups and global corporations like Google, Apple, and Samsung Electronics are offering innovative products and services to target the growing market of smart homes (Yang et al., 2018). Geneiatakis et al. (2017) affirm that IoT supports many services and applications, such as smart homes. Thus, smart IoT objects communicate and interact with mobile devices and various servers to collect, manage and exchange data.
The fundamental idea behind the smart home is the introduction of home automation to simplify household chores. Yang et al. (2018) provide a clear definition that a smart home is a residence equipped with a communication network, high-tech household devices, and sensors that can be remotely accessed and monitored. Shouran et al. (2019) emphasize that the usage and demand of IoT smart home services are continuously growing. Notably, the smart home analyzes the data of smart devices. It demonstrates the information received to the user in a convenient format and processes and interprets the commands given by the user and sends them to the devices.
Shouran et al. (2019, p. 4) inform that a smart home includes four core elements: “the service platform, smart devices, home gateway, and a home network.” Accordingly, devices exchange data through a home network, while a home gateway monitors the data flow between devices connected to the external network (Shouran et al., 2019). Consequently, the service platform utilizes the services and distributes them to the home network.
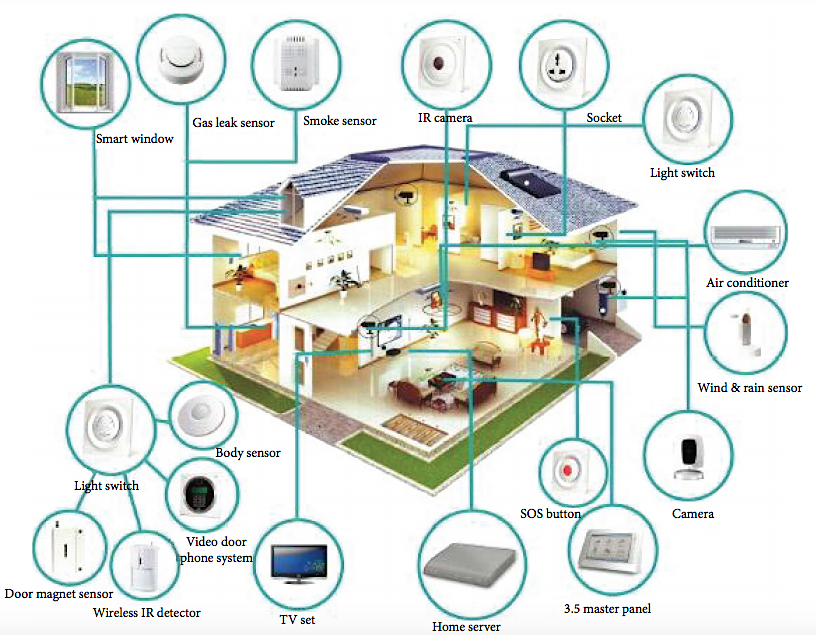
Figure 1 illustrates how a smart home service keeps track of the internal home environment and user activities. Thus, a smart home is a set of gadgets that automate and launch specific actions in the house. For instance, a smart home includes managing and controlling lighting, water supply, heating, video surveillance, and even security systems. Smart home services can be tailored to users’ needs and requests (Yang et al., 2018). Consequently, a smart home performs various functions from setting and adjusting lighting, turning on or off the air conditioning, or opening and closing windows to multifunctional security and alarm systems.
Benefits and challenges of IoT at home
The primary purpose of the Internet of Things is to connect devices anytime, anywhere via the network. Aldosari and Sidorova (2018) mention that smart home technologies range from smart refrigerators to smart toothbrushes. IoT technologies are used in home automation and security, wearable devices, and personal health (Aldosari and Sidorova, 2018). According to Wang et al. (2018, p. 3), the perceived benefits of smart home devices include “performance expectancy, effort expectancy, compatibility, and image.”
Therefore, the users expect smart home devices to improve their household activities and facilitate usage difficulties and issues. In addition, the smart house ensures being consistent with the users’ lives. Another advantage is the image, which refers to the user’s status. It is prestigious to own a smart house and use smart devices in daily life.
Despite the various benefits of IoT at home, there are several significant risks. Wang et al. (2018, p. 3) state that the considerable risks of smart homes are “privacy, security, performance, time, and financial risks. Besides, smart home services are provided over a wireless network, which is why there is a threat of intruders who can gain access to the system (Shouran et al., 2019). While IoT-powered smart homes address a variety of social concerns and provide users with unique, cutting-edge services, their limited processing capabilities make them vulnerable to security and privacy threats (Geneiatakis et al., 2017).
Armerding (2017) argues that the Internet of Things can pose a danger because developers and buyers of smart devices care much more about their features and price than about security and privacy. Each new device that users install in their smart home can be a target source of potential hacking and information theft. Significantly, many connected devices to the Internet may be insecure.
Furthermore, performance and time risks are not as dangerous as privacy and security risks because they refer to the customer’s requirements and can be solved accordingly. Potential customers may worry that intelligent home management is complicated as it takes much time and may not satisfy their needs. Another risk mentioned by Wang et al. (2018) is financial risk, which means that smart homes’ purchase and maintenance are perceived as excessive and expensive. Regardless of risks, potential customers assume that they will obtain more benefits than challenges from having smart homes because smart devices will remarkably facilitate their daily lives (Wang et al., 2018). Thus, the popularity of IoT-supported smart devices is growing.
It is essential to add that IoT technologies put their users at risk and public and private infrastructure, including the Internet’s infrastructure (Armending, 2017). Shouran et al. (2019) highlight that the advantage of smart homes, namely access via the Internet everywhere in real-time, may present huge risks, such as malicious attacks and theft of personal information. Thus, IoT usage possesses some privacy leakage risks because the user-sensitive data is uploaded to a remote cloud (Wu et al., 2020). For instance, it is necessary to establish a minimum-security requirement – a strong password before using the device, as well as provide the ability to automate the update process if the slightest threat is detected (Armending, 2017).
To provide security, Nagarkar and Prasad (2019) recommend frequent checking and changing the password after a specified period has elapsed in order to avoid intruders gaining access to the system through private accounts. Another recommendation is to protect the Wi-Fi network and establish a secure connection so that other unregistered users cannot connect to the system. To summarize, the solution to the IoT problems is to ensure high security for the devices.
Recommended Policy Concerning Data Collection, Sharing, and Usage
Policy on Data Collection, Sharing, and Limitations
The policy on data collection, sharing, and limitation is created for the FTC to ensure that vendors and service providers properly manage the data collection and sharing by the smart home devices. Chang et al. (2018) highlight the growing concern that customers demonstrate toward private information; thus, the service provider must have a privacy policy to protect both customers’ and providers’ rights.
The core goal is to minimize the privacy concerns of IoT devices’ customers in their homes. Therefore, the privacy policy dictates how vendors and service providers of smart devices shall care for the privacy of their customers and users. Before a customer installs and starts using smart home services, the service provider must ensure that the user has carefully read the terms for the services.
Data Collection and Security
Despite the provided comfort and safety, a smart home involves certain risks, and each potential user should consciously choose in favor of a smart home. First of all, vendors and service providers must ensure high security of devices through the development and offering of a high-quality system protected from intruders. Therefore, it is crucial to inform potential customers and users about possible risks and challenges.
Secondly, the IoT-supported innovative home system collects confidential information and personal data such as names, phone numbers, addresses, and credit cards. Briefly, privacy refers to users protecting confidential information, such as identity, movements, locations, or any other private information (Nagarkar and Prasad, 2019). It is critical for service vendors to ensure that devices are highly secure through authentication to avoid the threat of information theft.
To ensure privacy, Nagarkar and Prasad (2019) recommend frequent checking and changing the password after a specified period has elapsed in order to avoid intruders gaining access to the system through private accounts. Another recommendation is to protect the Wi-Fi network and establish a secure connection so that other unregistered users cannot connect to the system.
The service provider is responsible for the personal data processing that relates to the actions with customers’ personal data: the accumulation, use, collection, systematization, storage, clarification (update, change), depersonalization, blocking, and destruction of personal data. It is essential to add that personal data is processed in an automated way, using transmission over the Internet, mixed processing methods, and encrypted protocols.
Security Goals
In addition, the service provider must focus on the smart home’s security goals. Ali et al. (2017) state that the security goals of a smart home are authentication, authorization, confidentiality, integration, and availability. First, authentication refers to the verification of the user and communicating parties. In addition, authorization is required to guarantee that the user access rights are identified for the access control goals.
Significantly, confidentiality is one of the core security goals because it ensures that only authorized users can access private data. As follows, integration focuses on proper data maintenance in order to control any modifications or losses. Finally, availability is necessary to provide all services and resources to the authorized user. According to Nagarkar and Prasad (2019), service providers must offer awareness programs and training to confirm the users’ system security understanding. Therefore, Nagarkar and Prasad (2019) suggest that the service providers should verify that:
- Users have secure Wi-Fi.
- Access is allowed only to authorized users.
- Each device for which users create an account has a unique and complex password.
- The network is safe for home automation applications.
- The devices are protected from loss or theft and “using a secure virtual private network (VPN)” (p. 77).
- Frequent data backups competitions “to protect sensitive data and configuration settings” (p. 77).
- The robust encryption mechanisms’ implementation to enable secured data exchange and transmission.
- The customers use the service provider’s “recommended quality hardware and software to collect and observe network traffic” (p. 77).
- Customers track the system’s performance and always inform the service provider about alerts and erroneous system behavior.
Therefore, a smart device is provided and maintained by a service provider who is the above service’s copyright holder. The user of the services can only be an individual who has a contract with the service provider for the provision of services. Suppose the user installs and uses smart home services. In that case, the service provider has the right to request information from the customer that is necessary and sufficient for the prompt and correct operation of the system.
Information Sharing and Disclosure
The service provider must confirm that the client’s personal information is kept confidential. Thus, the service provider is not entitled to share customers’ personal and confidential data with third parties. The transfer of data is allowed only in cases where the client has expressed his consent to this action. The transfer of information is necessary to use a specific service and is provided for by law within the framework of the measures established by law.
Moreover, the service provider must inform that the security and protection of the customer’s information also depend on the customer himself. Since the devices are connected to cloud-based interfaces, customers need to be educated about the importance of having a strong password. Access to the service must be secured with a password, so it is highly recommended to make sure that all devices have password protection, fingerprint recognition technology, or other security technologies. On the part of service providers, all confidential information must be encrypted using sophisticated encryption mechanisms to avoid hacker attacks.
Limitations
The service provider must ensure the confidentiality of the information provided by the user and protect it following contracts, as well as the requirements of international standards and legislation. Moreover, the service provider is not responsible for the customer’s actions to bypass any privacy settings and violate security measures that must be followed. Acceptance of the Privacy Policy means that the service provider agrees to the terms of processing the client’s personal data outlined in this Privacy Policy.
Conclusion
The Internet of Things has introduced significant changes in the way people live. The high-tech smart home is one of the examples where the IoT is used to automate household chores, keep residents safe, and save energy. Smart devices supported by IoT can collect data, track activity, and customize experiences to the needs and demands of users. Despite the advantages and conveniences, the IoT’s growth and development are associated with a security problem. Since all smart devices are linked to the Internet, the possibilities of cyberattacks and hacks are increasing. Despite that, the IoT continues to evolve despite all the doubts about the safety of the application in general.
At this point, IoT already refers to the many physical devices around the world that are connected to the Internet in order to collect, analyze, and process vast amounts of data. It is possible that in the future, Internet things will be present in all spheres and industries, where connected devices will be able to interact with each other, exchanging information without requiring human intervention.
The main reason for the IoT’s popularity is the pace of development of intelligent systems. It is important to note that IoT technology is at the beginning of the development journey because scientists are creating new ways of applying intelligent devices every day. In the future, more and more innovative use cases for smart devices are expected to appear every day. Consequently, regular users, businesses, and cities will take advantage of the IoT to save time and money. As the quantity of connected devices continues to grow, routine life will be filled with smart technology.
Additionally, the rapid technology development will possibly contribute to creating smart cities, industries, personal robot assistants. Undoubtedly, the presence of an extensive network that controls our reality and the global openness of data have positive and negative consequences. Therefore, an essential condition is to take the necessary measures regarding security and privacy in order to avoid risks. To summarize, it is required to ensure a bright future for the IoT, legislation, and service providers of the IoT market to pay attention to the development of data security systems.
References
Aldossari, M. Q., & Sidorova, A. (2018). Consumer acceptance of Internet of Things (IoT): Smart home context.Journal of Computer Information Systems, 507-517.
Ali, W., Dustgeer, G., Awais, M., & Shah, M. A. (2017). IoT based smart home: Security challenges, security requirements and solutions. 2017 23rd International Conference on Automation and Computing (ICAC). DOI: 10.23919/IConAC.2017.8082057
Armending, T. (2017). Can government really fix the IoT mess?CSO.
Chang, Y., Wong, S. F., Libaque-Saenz, C. F., & Lee, H. (2018). The role of privacy policy on consumers’ perceived privacy. Government Information Quarterly, 35(3), 445–459.
Geneiatakis, D., Kounelis, I., Neisse, R., Nai-Fovino, I., Steri, G., & Baldini, G. (2017). Security and privacy issues for an IoT based smart home. 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO). DOI: 10.23919/MIPRO.2017.7973622
Nagarkar, S., & Prasad, V. (2019). Evaluating privacy and security threats in IoT-based smart home environment. International Journal of Applied Engineering Research, 14(7). 75-78.
Shouran, Z., Ashari, A., & Priyambodo, T. (2019). Internet of things (IoT) of smart home: privacy and security. International Journal of Computer Applications, 182(39), 3-8.
Wang, X., McGill, T. J., & Klobas, J. E. (2018). I want it anyway: Consumer perceptions of smart home devices. Journal of Computer Information Systems, 1–11.
Wu, Q., He, K., & Chen, X. (2020). Personalized federated learning for intelligent IoT applications: A cloud-edge based framework. IEEE Open Journal of the Computer Society, 1, 35-44. DOI: 10.1109/OJCS.2020.2993259
Yang, H., Lee, W., & Lee, H. (2018). IoT smart home adoption: The importance of proper level automation.Journal of Sensors, 2018, 1–11.