Acknowledgment
The concept of risk assessment seeks to identify possible hazards and define the level of threat and vulnerability of a specific location or enterprise. For public locations, risk assessment is a critical management aspect that ensures the safety of visitors, patrons, staff, and physical assets within the premises. This report will define fundamental risk assessment principles, provide reasons for carrying out assessments, and provide a practical analysis of the Villaggio Mall following basic guidelines.
Report Questions
- What are the basic principles of risk assessment?
- What are the reasons for risk assessment?
- What are the steps of risk assessment performance?
- How could the risk be mitigated?
Risk Assessment Principles
Risk assessment and management are used by organizations to control losses. It consists of identifying hazards or potential causes of dangerous situations in the environment, assessing the risks, and attempting to mitigate them to minimize consequences. Hazards are defined as any situation with potentially damaging outcomes, especially ones that might harm a human being. Examples include fires, smoke, chemicals, and electricity. A risk is a negative consequence associated with the situation (Safe Work Australia 2011).
Reasons to Carry out Risk Assessment and Safety Management
There are several benefits of carrying out risk assessments that justify the time and costs invested. They assist in recognizing hazards in the workplace and controlling for adverse outcomes, which significantly reduces their risk of occurring and protects against damages. A risk assessment and subsequent training can help in the prevention of injuries and protect the safety of employees and patrons alike. It is the ethical duty of employers and organizations to create measures that protect people from preventable accidents. With proper assessment, risk management standards can be raised to meet regulations and legal requirements for safe practices. Management control is more effective at controlling health and safety measures, avoiding easily preventable errors of negligence. The implementation of proactive risk management systems is necessary to reduce the likelihood of a safety-related incident (Weekes 2017).
Targeted Place of Risk Assessment
Villaggio Mall, one of the largest shopping centers in Doha, Qatar, is located in the west end of the city. It has the highest mall foot traffic in the region with 50,000 daily visitors and up to 1.5 million monthly (Villaggio Mall n.d.). Shopping malls are inherently vulnerable to numerous hazards and threats due to the large congregation of businesses and people in a relatively limited indoor area. Security and safety have become a significant priority in the retail industry in light of shopping malls becoming highly hazardous public locations.
Organization Name: Villaggio Mall
Address: Al Waab St, Doha, Qatar
Activity: Retail shopping center
Capacity: 50,000 daily visitors
Total Floor Area: 125, 000 square meters
Years operational: 12 years. 6 years after the renovation
Steps of Risk Assessment Performance
The principles of risk assessment include recognition that the problem exists and definition of the nature of the issue. This is followed by identifying alternative solutions and assessing the chosen action. Implementing the chosen action and evaluating its effectiveness is also necessary. Risk management encompasses aspects of problem solving and decision-making that are used in a business context. It is an ongoing process, but six total steps exist that allow an organization to meet its health and safety obligations (University of Southern Queensland n.d.).
Identifying Risks and Analyzing Consequences
The Villaggio Mall faces both internal and external threats. Internal threats consist of violations of security standards, safety hazards, and potential structural issues. External threats are much rarer but could include acts of terrorism or natural disasters (Prosek Security n.d.). Shopping malls are vulnerable to security threats due to many entrances with a limited number of checkpoints such as metal detectors, cameras, or bag checkers. The most common safety hazards include injury due to falls on a wet floor (cleaning or spill), malfunctioning equipment such as escalators, sprinkler systems, and fire alarms, and crowd control measures that result in injury in cases of panic (Department of Labour Republic of South Africa n.d.).
Structural issues that overlap with safety hazards can vary in nature. One of the most common safety concerns and one that caused the fire at Villaggio is electrical wiring. Outdated or damaged wiring in combination with the use of highly flammable materials in the construction of the building can cause fires or accidents. Piping issues can cause flooding, and outdated infrastructure that might lead to collapsed ceiling tiles are also structural hazards in a shopping mall complex.
Assessing Risks
Each hazard should be evaluated to determine the level of risk. Assessment can be based on a variety of factors ranging from experience to industry practices and information available from regulators and experts. Risks should be ranked, which helps to determine prioritizing which ones to control. The risk matrix such as the one below is used to categorize hazards based on either severity or probability of occurrence.
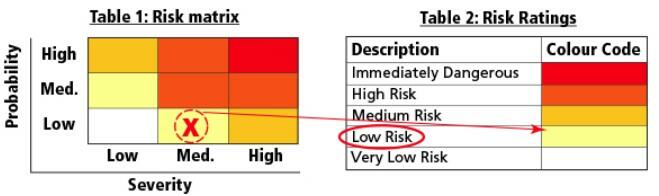
Implementing Control
Control measures for internal and external threats are similar regarding the security and structural integrity of the building, with protection from elements such as fire or flooding. Security threats can be mitigated by introducing checkpoints at every entrance, each equipped with a metal detector and baggage scanning equipment. Routine patrols should be implemented both inside and outside the building, as well as provided with adequate training to respond to changing security conditions and crowd control. Fall hazards are unpredictable but can be improved through changes to the cleaning procedures of the mall staff. Malfunctioning equipment, particularly critical safety-focused systems (such as fire alarms) should be checked monthly by regulation and provider recommendations. Structural parameters and infrastructure such as wiring can be controlled by conducting routine pre-checks on cables and switches. Electrical installations should be tested and maintained by competent utility companies, and staff should be provided with training on electrical safety. Employees must be provided with adequate equipment and resources to administer safety precautions throughout the building. Measures such as rotational schedules and checks with managerial oversight are conducive to creating a hazardless environment.
Evaluation of Controls
The assessment should be completed with a feedback and evaluation stage. Relevant process mapping, documentation, audit reports, and program evaluations should be included. Furthermore, regulatory standards and organizational experience support are vital for the evaluation stage. The assessment is completed by creating a list of relevant hazards, identifying who may be harmed, what measures are being taken, and any necessary further actions. The accuracy of documentation is paramount to maintain responsibility as well as for legal and regulatory purposes if any issues arise
Recommendations for Safety Officers
Villaggio Mall is vulnerable to public security and fire hazard risks. It is recommended that all fire protection systems be checked monthly, while structural and electrical aspects must be monitored continuously. Another recommendation is that identified hazards should be implemented into staff training on emergency preparedness. Communication is key with relevant stakeholders including owners, management, employees, and customers. Therefore, if a hazard is preventable or avoidable, proper measures of communication will be introduced so that the public is aware.
Risk Assessment Form
Reference List
Department of Labour Republic of South Africa n.d., Occupational health and safety in shopping centers, Web.
Prosek Security n.d., Risk assessment in shopping centres: what it is and why it is needed, Web.
Safe Work Australia 2011,How to manage work health and safety risks: code of practice, Web.
University of Southern Queensland n.d. Risk management in work health and safety, Web.
Villaggio Mall n.d. About Villaggio, Web.