UNIT 6 Computer Security
- Threats facing Microsoft products;
- ISA server security settings.

Overview
Characteristics of winNuke attacks:
- Exploitation of windows network products.
Microsoft products threat and vulnerabilities:
- LAND, Ping-of-death, TCP Half scans, UDP Bomb, Port scanning and DNS attack prevention.
ISA Server DNS Filter Settings:
- Hostname overflow, length overflow and DNS Zone transfer.

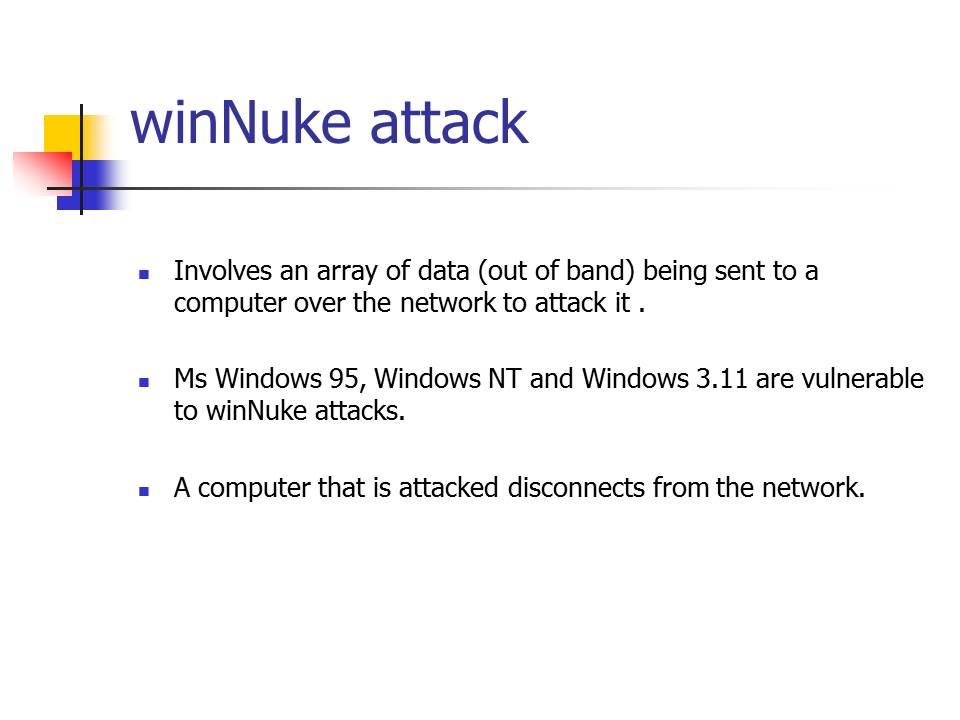
WinNuke attack
- Involves an array of data (out of band) being sent to a computer over the network to attack it .
- Ms Windows 95, Windows NT and Windows 3.11 are vulnerable to winNuke attacks.
- A computer that is attacked disconnects from the network.
- The computer then crashes and display a blue screen.
- When this happens, all unsaved data gets lost.
- The computer then remains on panic mode with the blue screen displayed.
- This can be avoided by installation of a patch created by Microsoft (Ankit & Zacharia, 2007).

Microsoft threats and vulnerabilities
LAND attack:
- In this attack, a string of TCP SYN packets are sent over a network using the same address on the source as the destination;
- It makes the vulnerable machine to reply to itself, leading to network congestion due to IPv4 crash.
Ping-of-death:
- In this attack, the attacking machine sends an IP packet (using ping utility) that is larger than the maximum size specified.
- The system of attacked machine either crashes, becomes unresponsive or reboots itself.
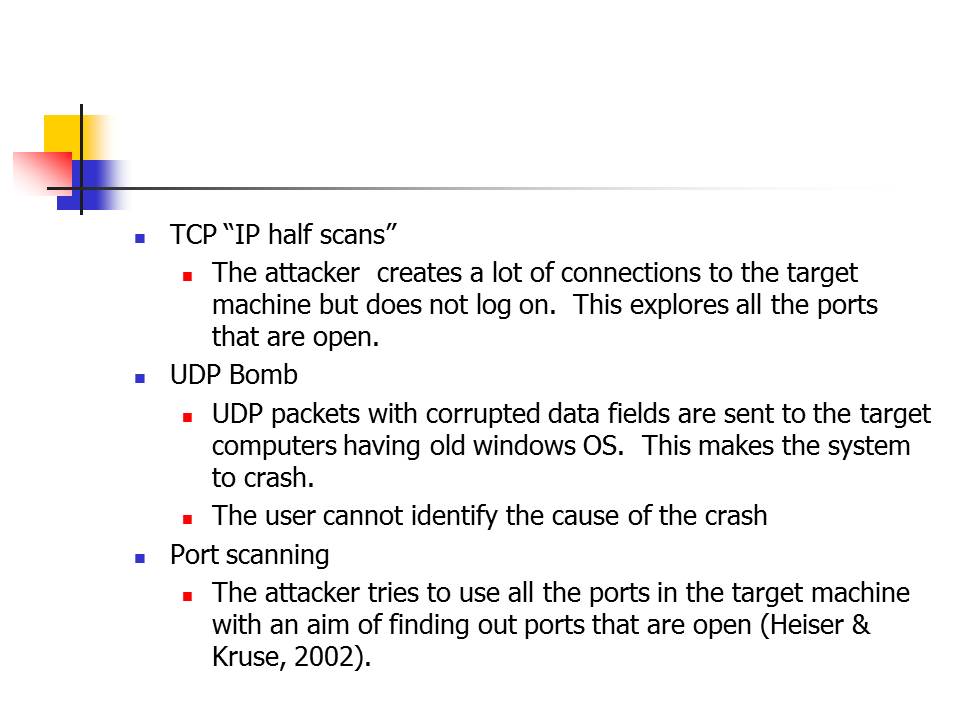
TCP “IP half scans”:
- The attacker creates a lot of connections to the target machine but does not log on. This explores all the ports that are open.
UDP Bomb:
- UDP packets with corrupted data fields are sent to the target computers having old windows OS. This makes the system to crash.
- The user cannot identify the cause of the crash.
Port scanning:
- The attacker tries to use all the ports in the target machine with an aim of finding out ports that are open (Heiser & Kruse, 2002).

Attack detection and prevention
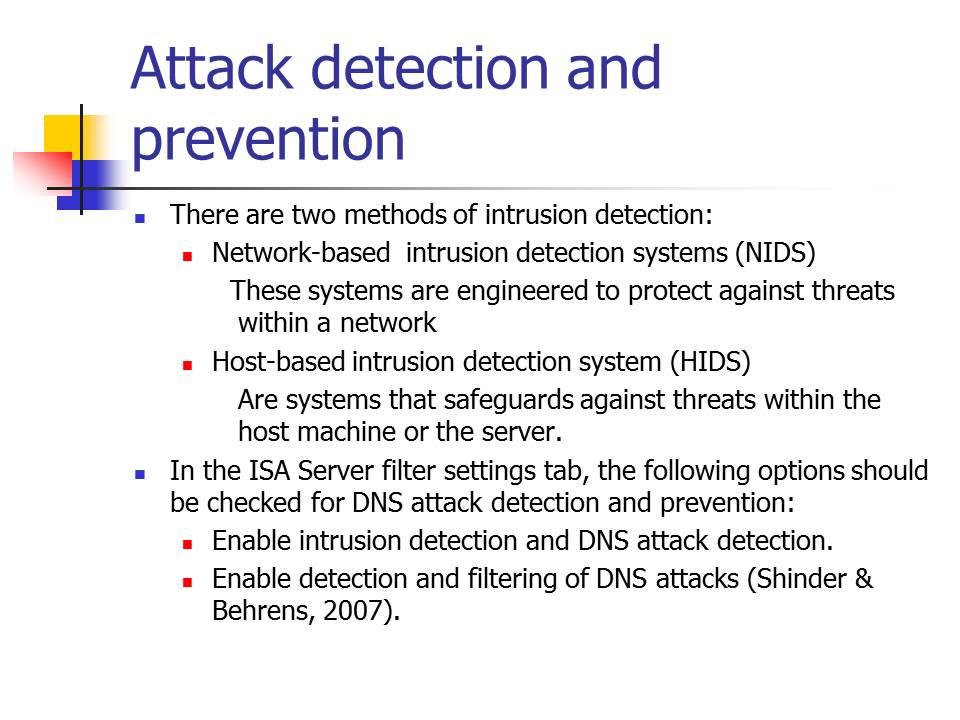
There are two methods of intrusion detection:
- Network-based intrusion detection systems (NIDS). These systems are engineered to protect against threats within a network.
- Host-based intrusion detection system (HIDS). Are systems that safeguards against threats within the host machine or the server.
In the ISA Server filter settings tab, the following options should be checked for DNS attack detection and prevention:
- Enable intrusion detection and DNS attack detection.
- Enable detection and filtering of DNS attacks (Shinder & Behrens, 2007).
Once the above are checked, there will be round the clock protection against the following attacks:
- DNS Hostname Overflow: This takes place when a DNS response meant for a host name is larger than the specified length.
- DNS Length Overflow: Occurs when the length of DNS response is designed to reflect a value larger than the required 4 bytes.
- DNS Zone Transfer: Takes place when databases containing DNS data are replicated.

Conclusions
There are various DOS attacks that the windows operating systems are vulnerable to. These include winNuke, LAND, Ping-of-Death, TCP IP Half Scans, UDP Bomb and Port Scanning.
The attacked machine show various characteristics which include hanging, rebooting, network congestion and system crash.
The DNS server filter settings can be configured to detect and prevent attacks from DNS Hostname Overflow, DNS Length Overflow and Zone Transfer.

References
Ankit, F., & Zacharia, M. (2007). Network Intrusion Alert An Ethical Hacking Guide to Intrusion Detection. New York: Cengage.
Heiser, J. G., & Kruse, W. G. (2002). Computer Forensics Incident Response Essentials. Boston: Addison-Wesley.
Shinder, T. W., & Behrens, T. (2007). The Best Damn Firewall Book Period. New York: Syngress.