Introduction
The rising tensions between the North Atlantic Treaty Organization (NATO) and the Russian Federation have heightened the risk of cyber-attacks. Multiple airports in the United States were recently alerted by sources confirming the likelihood of Russian attacks attacking American businesses. One of the transportation hubs that came under assault was LaGuardia Airport. This document offers the technical team recommendations based on the COSO Internal Control Framework and COSO Enterprise Risk Management Framework for the company. The purpose is to undertake root-cause analysis, risk assessment, measurement, and control rating assignment to calculate residual risk. Risk management, corrective action plans, and risk surveillance Key risk indicator (KRIs) give crucial knowledge for navigating cyberspace which is becoming more dangerous.
Risk Event Selection Process
For critical operations centers such as LaGuardia Airport, cyber-attacks might lead to the breakdown of operations, which can quickly precipitate a national catastrophe. The assaults may cause electricity shortages, military equipment malfunction, and leaks of national security secrets, leaving the nation exposed (Malik 7). According to the Impact x Likelihood scale in Figure 3, cyber-attacks on such transportation hubs are immediate and severe. In case of a cyber-attack, there is a high likelihood that operations will be disrupted immediately and may damage infrastructure that may take a long to restore fully.
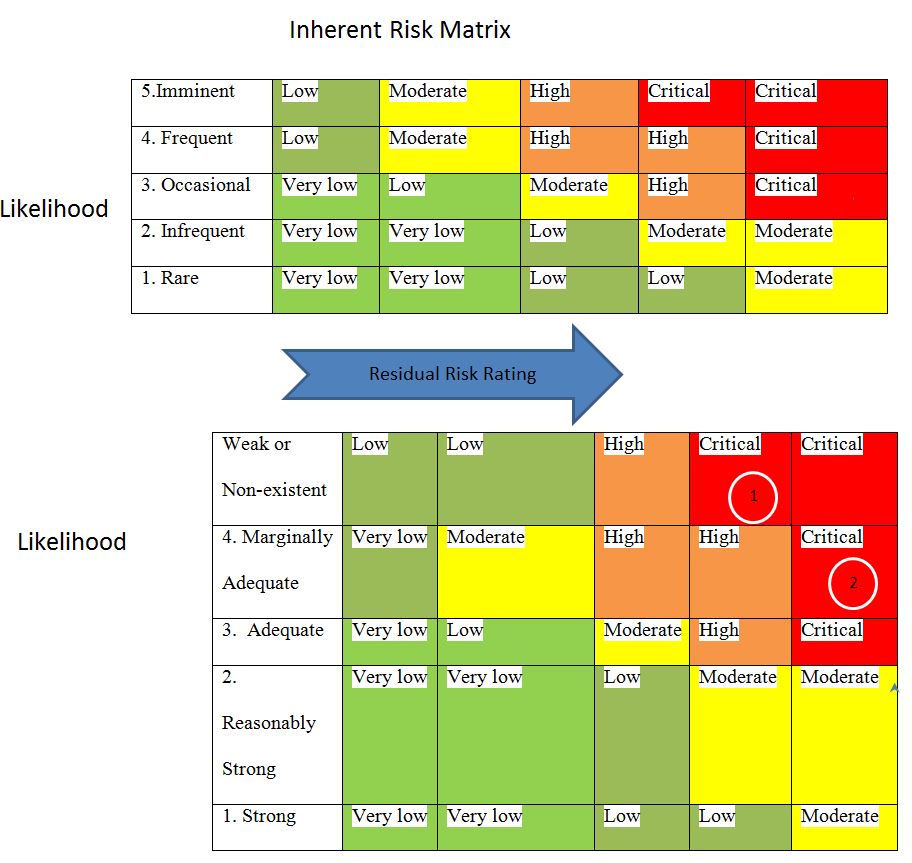
As in Figure 1, the consequences are severe in the event of a successful assault since the attackers may harm the company’s money, reputation, and legal standing. On account of safety, the corporation is expected to endure long-term negative media attention worldwide, resulting in a game-changing loss of market share. In the event of harm, the corporation faces severe punishment and penalties, lawsuits, including class actions, and imprisonment of its leadership.
The Risk Factors, Risk Conditions, and Risk Consequences
Root cause Analysis/Bow-Tie Analysis Diagram
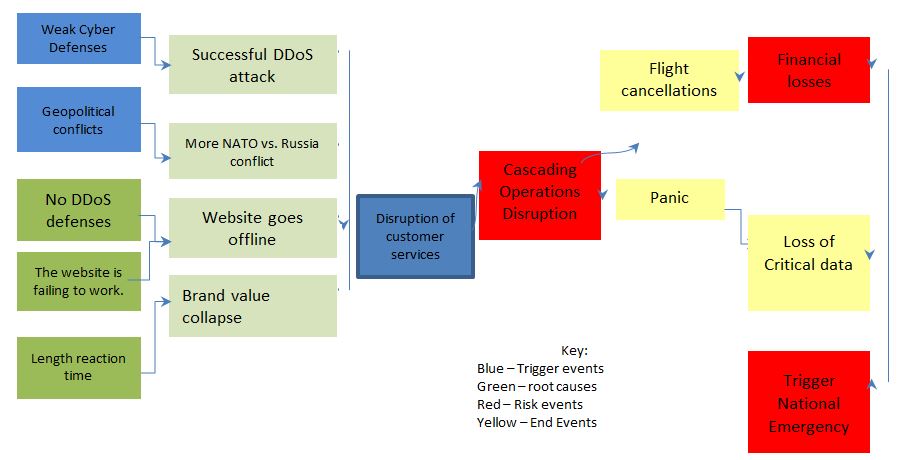
Risk Event
Due to the escalating geopolitical tensions with the Russian Federation, cyber-attacks on NATO member states have become more likely. On October 10, 2022, cyber-attacks targeted critical airports in the United States (Margolin et al. 1). According to ABC, the assaults were connected to a Russian Federation hacker (Margolin et al., 2). At around 3:00 a.m. Eastern Standard Time, LaGuardia Airport reported a Denial of Service (DoS) assault on the company’s main website. Des Moines International Airport, Los Angeles International Airport (LAX), Chicago O’Hare International Airport (ORD), and Hartsfield-Jackson Atlanta International Airport were the other impacted airports (ATL). According to the reports, a hacking gang called Killnet has specified airports in the United States among its targets (Margolin et al. 3). Since Russia invaded Ukraine, the group has targeted NATO groups as revenge for military support to Kyiv.
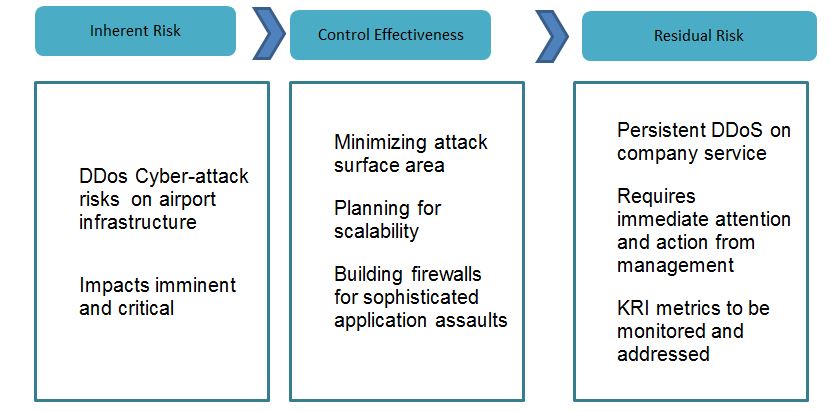
Controls
Based on the impact of a successful DDoS assault on the everyday lives of Americans and LaGuardia Airport’s performance while under attack, the control efficacy is rated as somewhat strong. The institution failed to safeguard its system by neglecting to remedy two significant flaws. First, LaGuardia Airport should have a significantly decreased attack surface area to restrict DDoS attack triggers. Second, the technical team at LaGuardia Airport should have established firewalls capable of mitigating complex application assaults by designing mitigations against invalid requests and preparing for scalability.
Based on the vulnerability caused by the successful DDoS assault by Killnet hackers, the residual risk assessment indicates that the particular organization’s management must take steps to reduce the harm caused by similar attacks. Controls should limit the effect of a Denial of Service (DoS) attack in which legitimate users cannot access resources and, as a result, cannot locate the required information or carry out the required tasks. On a larger scale, the intrusion might expose other organizations to service disruptions, causing a domino effect on operations.
Control Rating Rationale
Figure 2: LaGuardia Airport COSO’s Internal Controls Intervention
The updated COSO ERM Framework requires LaGuardia Airport to show its commitment to integrity and ethical standards. The management must tighten supervision and internal controls, especially regarding the current state and possible cyber security weaknesses. The human resource teams at LaGuardia Airport should guarantee that they have access to competent organizations that can help with fragile but crucial internal activities. The organization requires specialist teams, especially developing cyber security technologies such as artificial intelligence (AI) and supercomputers.
Residual Risk Rating with Rationale
With such new technology, the threat posed by pro-Russian cyber groups is getting more sophisticated. Killnet has indicated on its Telegram channel that they want to target maritime ports and logistical infrastructure, healthcare companies, and internet trading networks. Killnet has been responsible for many high-profile strikes since the Russian invasion of Ukraine in February (Margolin et al. 3). As in Figure 4, the Residual Risk Score is vital and may need immediate action from the organization’s management and the local government.
Corrective Action Plans
Minimize Attack Surface Area
One of the initial approaches for mitigating DDoS assaults is reducing the attackable surface area, restricting the attackers’ choices quickly. The software models should not expose resources or applications to isolated ports, protocols, or apps (Karnani and Harish 9). The intervention reduces the number of potential places of attack. The firm should use Load Balancers and limit direct Internet traffic to specific infrastructure components to mitigate DDoS.
Plan for Scale
Similarly, within three months, the technical staff at LaGuardia Airport should establish procedures to accommodate a rapid increase in traffic. Bandwidth and server capacity to absorb and mitigate large-scale volumetric DDoS assaults are the two most essential factors in practice (Hekmati et al. 113). When designing the applications, the IT teams must guarantee that the hosting provider offers sufficient redundant processing capacity. Equally, teams should implement firewalls for sophisticated application assaults, such as the Web Application Firewall (WAF), which protects against SQL injection and cross-site request forgery.
Risk Owner for Corrective Action Plan
The Risk Owner for a Corrective Action Plan (CAP) should address the organization’s vulnerability to attack levels, the scalability elasticity, and the firewalls that defend the organization from DDoS assaults interrupting service delivery. The IT and Cyber Security department at LaGuardia Airport should take action, monitor, and report weekly to top management on the progress. Teams should establish perimeters around every system and user, including network firewalls and VPN technologies, and maintain stringent access control based on identifying access types.
Monitoring Key Performance Indicators
Technical staff at LaGuardia Airport should monitor early warning signals that assess metrics and give quantitative data required for reporting. Technicians must understand the importance of avoiding data breaches and identifying cyber-attacks to preserve sensitive data. The team should examine KRIs such as fire breaches that can be evaluated from the smoke detector behavior. Management at LaGuardia Airport should be concerned with Mean Time to Resolve (MTTR) and Mean Time to Contain (MTTC) results. The MTTC should compare the quality of an organization’s incident response plan execution to the time required to shut detected attack vectors on all endpoints.
Assigned Sub-committee
The IT and Cyber Security department’s Research and Development subcommittee and the Cyber security Advisory Committee shall manage the control and monitoring teams (CSA). The researcher should explore the cyber security implications of developing technologies such as artificial intelligence (AI) and supercomputers. The teams should acknowledge that introducing artificial intelligence and supercomputers across all market sectors has significantly changed cyber security (Yao et al. 102550). In the development of automated security systems, AI has become indispensable. However, it is also used to construct intelligent malware and assaults that circumvent the most current data security standards. AI-enabled threat detection systems can forecast new assaults and immediately alert administrators of any data breach.
Conclusion
Cyber security risks to vital infrastructure are becoming a significant issue in the United States. Recent DDoS attacks on American Airlines illustrate the necessity for organizations and the federal government to speed up cyber security intervention and innovation. LaGuardia Airport’s administration could consider assisting the IT and Cyber Security department with system modifications. Minimizing attack surface area, planning for scalability, and building firewalls for sophisticated application assaults should constitute the most urgent measures. The Research and Development subcommittee should address the cyber security threats connected with AI and supercomputers.
Works Cited
Hekmati, Arvin, Eugenio Grippo, and Bhaskar Krishnamachari. “Neural Networks for DDoS Attack Detection using an Enhanced Urban IoT Dataset.” 1, 2022 International Conference on Computer Communications and Networks (ICCCN), 2022. 5-213. Web.
Karnani, Suruchi, and Harish Kumar Shakya. “Mitigation Strategies for Distributed Denial of Service (DDoS) in SDN: A Survey and Taxonomy.” Information Security Journal: A Global Perspective, 2022, 1-25. Web.
Malik, Annas W., et al. “Cyber Threats: Taxonomy, Impact, Policies, and Way Forward.” KSII Transactions on Internet & Information Systems, 2022. 15-313
Margolin, Josh et al. “Cyberattacks Reported At US Airports.” ABC News, 2022, 1-33. Web.
Yao, Tiechui, et al. “VenusAI: An Artificial Intelligence Platform For Scientific Discovery On Supercomputers.” Journal of Systems Architecture 128, 2022, p102550. Web.