Proposed topology and justifications
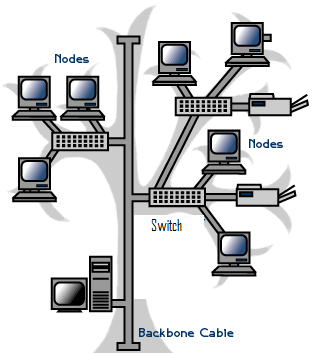
The tree topology being proposed is essentially blend of various designs in Star topology connected together using the bus topology. Switches and similar networking devices used in LANs are then directly connected to the Tree bus where each of them acts as the root of the tree (Deal 2008). One key merit this topology is because of its dynamic manner in which it has room of extending the school’s network for future more than what other networking topologies offer on the same as shown in the figure below (Tamara 2005).
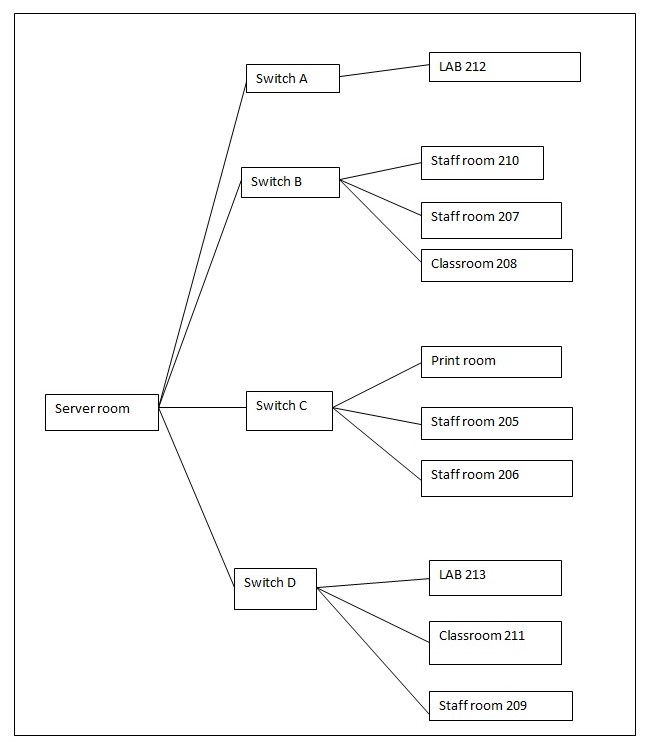
LAB 212 will require its own switch due to the separation by the staircase that may cause cabling difficulties. The section containing staff room 210, staff room 207 and classroom 208 will also need their independent router. The print room, staff room 206 and 205 will have its own switch, while the section having LAB 213, classroom 211 and staff room 209 will have its own switch. The server room will host the main router from the backbone of the whole school network. Wireless routers will also be installed in the LAB 212 and LAB 213 (Tamara 2005). Switch to switch connections will be via the router installed in the server room. An overview of the segmentation of the network is shown in the figure below. The file and web servers will be connected to the main network of the institution through the backbone cable via the router in the server room.
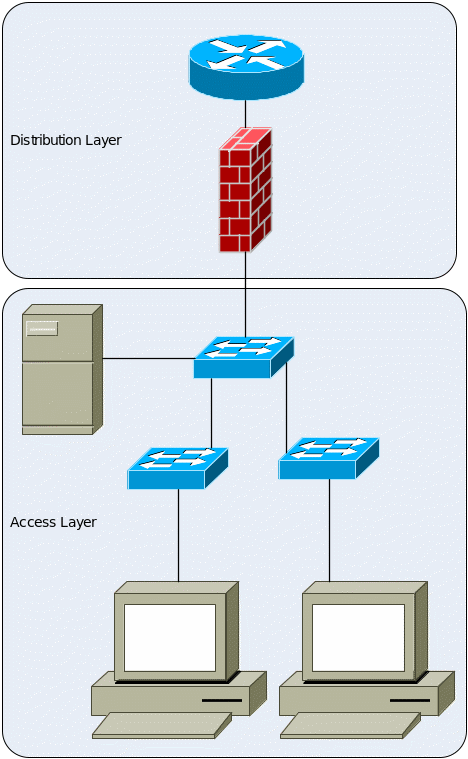
The school network will be designed to have a hierarchal format containing two layers; these are distribution layer and the access layer. As a core requirement, the network still has more room for the extension and inclusion of the core; the third layer when need arises in the future. The routers at the edge will be part of the distribution layer as well as servers for security servers but any other server will be grouped under the access layer of the network (Deal 2008). Therefore, this implies that in case a single location has to be upgraded, for example, when one or two additional department needs to be added, then this will be very easily to achieve without interfering any network operation of the remaining four locations or departments within them. This means that there will be two routers and firewalls will be found at each of the five locations. The firewalls implementation will make sure that packets are directed to the required department. This will be easily attained because School of Applied Computing of Swansea Metropolitan University networks modular model of design, in the sense that each department is independent and its own entity (Deal 2008). A typical location of the office layout networking is shown below:
The network design of any organization cannot be effectively accomplished without proper security design. It is therefore imperative that the school network design will have to adhere to the security measures set forth by the school. The first design will be a firewall implementation at each of the five locations. The entire traffic passing through the school’s network will be encrypted and will have to be linked by a VPN connection. The components on the wide area network must be configured and enabled to use login through a syslog server. Audit and certifications will have to be written by the school and there will be need of its revision on regular basis to make sure that at all times, only genuine employees with authority are the only ones being allowed have access to their respective applications at any particular time. For the purposes of accessing the two RSA authentication keys, will be required. At all times log in must be provided before any access to the network management is allowed. Equally, it is important that any production server will be part of the general school’s management network. Only a few employees will have the authority to access the network and that the network will be used to manage all servers on it. The importance of this is that it will enable accessibility to the computer and equally be in a position to provide coarse-grain protection for any server access. This implies that the five locations of School of Applied Computing of Swansea Metropolitan University network will be connected by two different networks. In order to increase the integrity and confidentiality of the provisioning system, the network must have a tiered architecture, data tier, application tier and the presentation tier. Each of these tiers will be an entity on its own and therefore control measures must be applied to make sure that only genuine authorized and authenticated transactions are move from one tier to another. Security will be enhanced by the fact that any server that connects to the outside world must be located at the network’s presentation or demilitarized zone (DMZ). In the entire network the application layer is given the duty to hosts any business logic applications that will require getting data access. At the same time, the data tier will be allowed to use the source data in the network, which are primarily from the file and the web servers. Routers, firewall and parameter will be employed in the security configuration of School of Applied Computing of Swansea Metropolitan University network. All the routers in the entire network will provide the required level of security of the network by sieving traffic to different parts of the school-protected network. The routers will use access lists configurations to carry out this duty. The DMZ will use private addresses configured on the firewall requirements. The DMZ will also house the DNS, emails, HTTP and any other types of Internet company server (Meyer 2003). Access-list is a list of instructions that group packets and are used in the configuration of the network to control, provide and deny access of the network traffic to some parts of the network or the entire network. In this network being proposed, some computers will be denied from accessing to the Internet and some resources if such a reason arises. Extended access list will be employed by the School of Applied Computing of Swansea Metropolitan University. Extended access list evaluates both the IP addresses of the source and the destination packets, the port number of the Transport layer as well as the header protocol found in the Network layer. By virtue that that the school will have different departments at a single location, access lists must be used to configure the network flow. For this reason, extended access list will be employed to avoid the interaction of host computers within a given department at a specific location. For example, the staff rooms and the computer labs will have different access lists due to the nature of the applications. At the same time using extended access lists, hosts will be prevented from accessing the Management department within a department or location. Contrary to this, the Management department’s computers will have access to the entire all the computers within the organization and the entire resources. A good implementation of the network will require that the file server and the web server located in the server room (Meyer 2003).
Cost of implementing the network
The following table shows the costs requirements for the implementation of the network
References
Deal, R 2008, Cisco Certified Network Associate study guide (exam 640-802), New York: McGraw-Hill Professional.
Meyer, M 2003, Mike Meyers’ A+ Guide to PC Hardware, New York: McGraw-Hill Professional.
Tamara, D 2005, Network+ Guide to Networks, Boston: Cengage Learning.