Project overview
The ministry of foreign affairs of Qatar deals with all of the international affairs and foreign policy of Qatar government and other countries governments. It has around 75 diplomatic mission around the world.
The current methods of communication used to send confidential document are; diplomatic mail, e-mail and fax. Diplomatic mail service would take two to three days to deliver documents. However, faxes and private lines don’t provide any type of security as they are unencrypted.
The emergence of virtual private network have created a secure and cheaper medium for transferring sensitive information, and documents between two or more organizations through public network such as; the internet site-to-site VPN.
Throughout my studying period and work experience in networking technology, I have thought of implementing new technology in my work. My idea is to implement VPN technology to support mailing, and video systems in the ministry. This technology will solve many problems such as; providing a lower cost solution of communication and enhancing securing lines and sharing confidential documents.
The VPN connection is to be created between the embassy of the state of Qatar in London and the ministry of foreign affairs IT data centre.
Finding the user Requirements
According to (Sommerville, 2004), Requirements capture involves three different phases which are as follow:
- Eliciting requirements
- Validating requirements
- Recording requirements
All of theses separate phases were carried out in order to start the project.
Eliciting requirements
Both primary and secondary researches were performed to obtain the requirements from two different users who were interviewed and questioned. The two user categories are Ministry of foreign affairs IT staff and some users from the embassy of the state of Qatar in London.
Primary Research
Case Study
Communication as a process has become most fundamental to any business. Initially at the start of the computer age, a lot of focus and weight was placed on data processing or traditional stand-alone processing. However as it became evident that these standalone systems could be networked and be able to collaborate even in processing, the aspect of communication began to gain attention. As it were, information that resulted from these data processes required transmission or dispersion. A communication dimension therefore needed to be added to this setup to ensure that the information resulting from the data processing would be effectively transmitted to where it was most needed to enable timely decision-making. The state of information received would then determine the decision to be taken by the recipient. This called for increased technological studies to ensure this. One such step was the introduction of the virtual private network (VPN) a communication approach aimed at providing reliable corporate data transmission within the public domain. Virtual private network (VPN) ensures that there are dedicated routers and servers to a corporate providing a virtual private network within the public network such as the internet. These servers and routers are configured to a corporate standard portraying a private network within the internet. The routers exchange data and information over the internet as though it is a private network. The advantage of such an implementation continues to be proven. The Middle East Airline (MEA) is one such case where VPN has been utilized and continues to benefit MEA.
The Lebanese’s national airline Middle East Airlines entered a $3 million contract with aviation IT service provider SITA. The contract covered the deployment an IP Virtual Private Network (VPN) to link all of the MEA’s branches worldwide. The interconnection will cover Rafic Hariri International Airport in Beirut the airline’s headquarters as well as nineteen branch offices. This will be achieved using SITA’s own virtual private network, and is eventually going to improve performance and security. The airline connection speed will be upgraded from 8kbps or 16kbps to at least 64kbps performance. The improvement and effectiveness of the business applications resulting from this venture is expected to cut down the operating costs. “SITA has demonstrated that it has the advanced technologies, industry expertise, and round-the-clock support required to meet our evolving communication needs” (Suton 2008, p. 1).
The Middle East airline is currently running applications such as the Gaetan reservation/inventory/departure control application, cargo scheduling as well as Oracle financial over the VPN. The infrastructure is well able to cater for future scalability requirements. (Suton 2008, p. 1)
The IP migration has been considered a success implying the viability of VPN implementation. In summary, it is envisaged that the VPN solutions can add security, flexibility providing for the much needed network support services for MEA. This can also be looked at as one of the largest virtual private networks in operation today.
Primary research methods are used to generate data which does not already exist (Erica & Priest 2009). There primary research techniques were used which were: questionnaire, Interviews and observation.
Observation
I spent few days at the embassy of the state of Qatar in London and I used to work at the IT department of the ministry of foreign affairs and from that I observed the following problems with the current communication and file sharing systems:
- The only way of making a phone call is via the normal PBX; International call from Doha to London and vice versa which has the following disadvantages:
- The cost of the voice conversations are very high
- Only Voice conversation can be made; Video call conferencing can’t be established
- Lack of security; any one can hack into the voice conversation and listen to it
- Sending files and important document are done by using faxes which again has a higher cost and non-secure at all
- To solve the problem of the fax security diplomatic mails were used but again it is very slow as it takes 3 to 4 days to reach the destination
- Sending files by emails are used too but again it might be hacked and any one can read the important document sent by the e-mail
Interviews and questionnaires
Several interviews was carried out with the IT stuff at the Ministry head quarter and with some users at the embassy of the state of Qatar in London and from these interviews the following points were concluded:
From the questionnaires, the following can be deduced:
IT Staffs
- IT staff are controlled from the finical department with the budget so they need a cost effective solution for the voice conversation
- Security is a very important feature that the IT staff look for
- They need to get rid of the diplomatic mails
- They need a better way of a fast and secure file sharing
Embassy users
- They need to call the ministry of foreign affairs almost every day due to business need which cost them a lot using the existing technology.
- They are sending a lot of confidential document to the head quarter using the diplomatic mail. They need a faster way and hence still very secure.
- They need and organised filing electronic files system that is linked to the HQ.
- Sometimes, they need to make a secure phone calls for security reasons.
Validating requirements
After gathering the data from the questionnaires and observation I have deeply analysed it to ensure that it is clear and does not make any conflicts with the IT HQ.
Recording requirements
Both the users and the IT staff requirements were recorded in a nice readable way.
Primary research results
Form the primary research results I came up with a VPN, virtual private network, solution which can fulfill the user requirements.
The following points are the benefits from the new proposed VPN solution:
- Cost effective connectivity method and significant reduction of the monthly cost as the calls can be made over the internet (Voice over IP or VoIP).
- The calls can be secured as site-to-site-VPN can be used that has encryption capacities; the Site to site VPN Creates a secure tunnel between cooperate and the branch office.
- Site-to-site VPN creates an encrypted tunnel between main office and its branches.
- Shared applications and services using electronic archiving system can be accessed remotely from the embassy to the servers at the head quarter.
- File and document mailing can be done in a fast and secure ways; as all the data and e-documents are encrypted and can only be read by the end user who has the decryption key.
- The system has a minimum downtime when performing any required upgrades; “availability” (Andersson et al 2006).
- The system is flexible to include modifications or any branch addition in the future.
- The system can operate on various platforms easily as the VPN used over internet which is available almost every where.
- The system is easy to learn and use and user documentation will be provided too.
VPN Background theory
A virtual private network (VPN) is a computer network that uses a public network like the internet that can provide secure connectivity between remote offices and users with their head quarter or main office. The main benefit of VPN is to provide a non-expensive ways of communication as owing a private telecommunication lines are very expensive; VPN Enhances Productivity and Cuts Costs. The data are transferred between the head quarter and the remote sites in a secure ways as Encryption is used to encrypt the data.
The following picture is an example of an internet VPN:
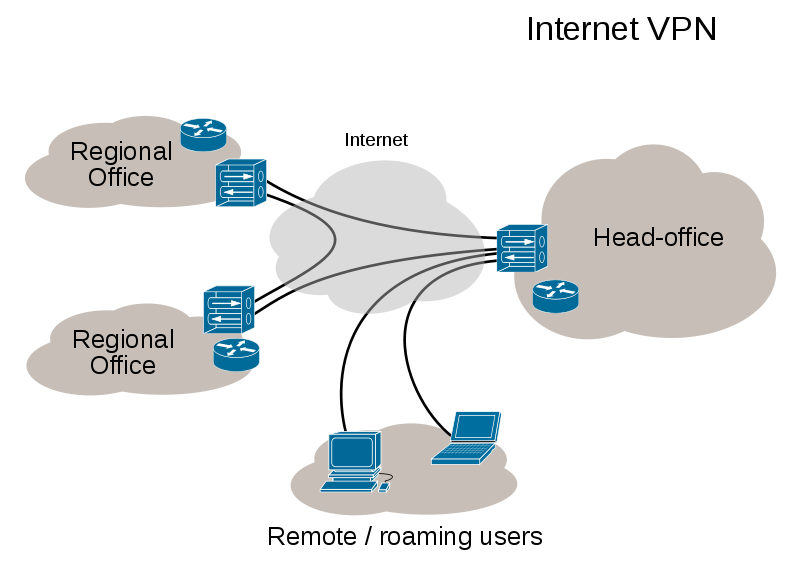
Some companies like CISCO and Juniper provides a VPN solution to the customers that has exceptional security features through encryption and authentication technologies that protect data in transit from unauthorized access and attacks. An intensive research was performed to study a these two solution to learn their practical requirements and uses (Lindsay 1997).
CISCO for example provides two VPN technologies (VPN 2010) that are Site-to-Site and remote access
Site-to-site
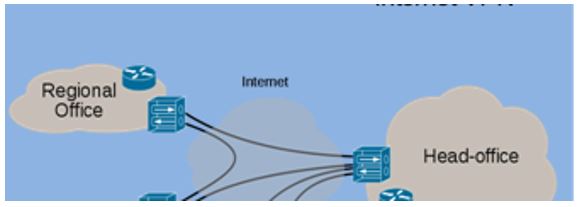
It extends network resources to branch offices by using the internet to create a WAN, wide area network, and infrastructure. All traffic between sites is encrypted using IPsec protocol Cisco VPNs also offer:
- Reliable transport of complex, traffic, such as voice (which is what we need in our project)
- Simplified provisioning
- Integrated advanced network intelligence
Remote Access VPNs
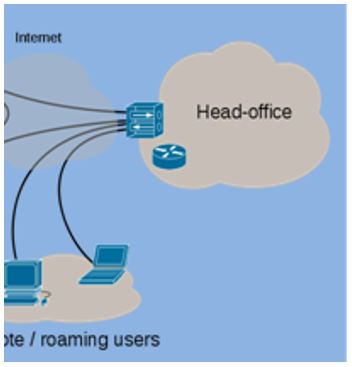
Remote access VPNs extend almost any data, voice, or video application to the remote desktop, emulating the main office desktop so that anyone, at any time and at any where can access the main desktop.
Secondary research
IP telephony
Organizations are realizing the cost cutting benefits by employing VoIP for voice transmission from the advent of the internet and data networks (Vbulletin 2010). Rather than have a dedicated network to cater for the transmission of voice, the internet infrastructure comprising of data networks continues to prove vital in the accomplishment of IP telephony. IP telephony supports consistent voice communication. The Cisco Unified Communication has realized the major benefits of the IP telephony in today’s corporate world and has invested in providing Cisco IP telephony solutions.
- Providing a highly reliable communication channel that is also scalable. This takes advantage of the available LAN and WAN.
- IP telephony results in improved employee productivity by use of supporting solutions such as the Cisco Unified Communication.
The suitability of the Cisco Unified Communication solution offers a number of services such as voice delivery, video, mobility and the support of IP phones. This range of products makes IP telephony an aspect that can literally transform the communication requirements of any organization. Most firms are exploring the wide range of options available to IP telephony and are making huge cost benefit advancements towards this goal (Stellman & Greene 2005).
The role played by IP telephony can therefore not be underestimated and as more and more firms are hooking on to the internet, the data network infrastructure is coming out as an important factor in the promotion of IP telephony (IP telephony – Cisco systems, 2010)
System Requirements
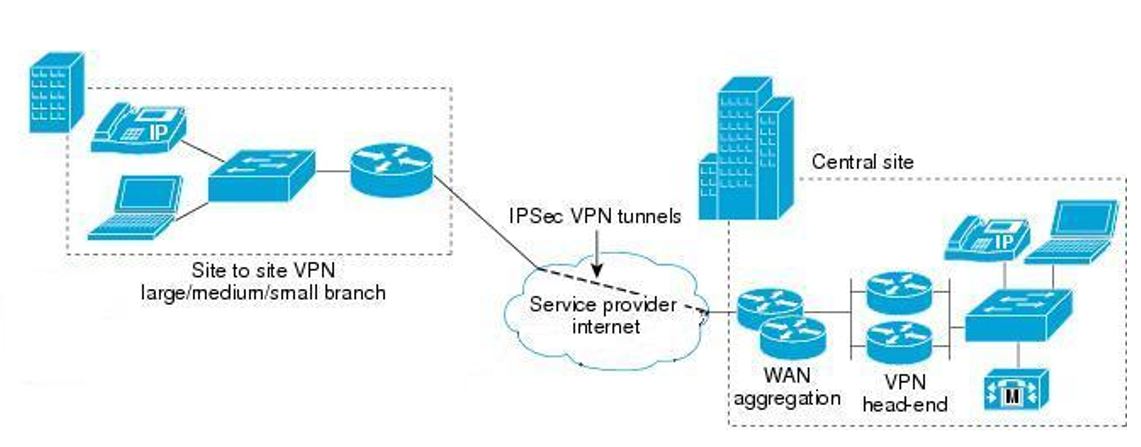
For real life scenario, the following equipments are required for implementation:
- WAN Cisco routers with static public IPs
- Cisco PIX firewall on each site
- Cisco Call Manager in the HQ
- Cisco Switches
- Cisco IP phones
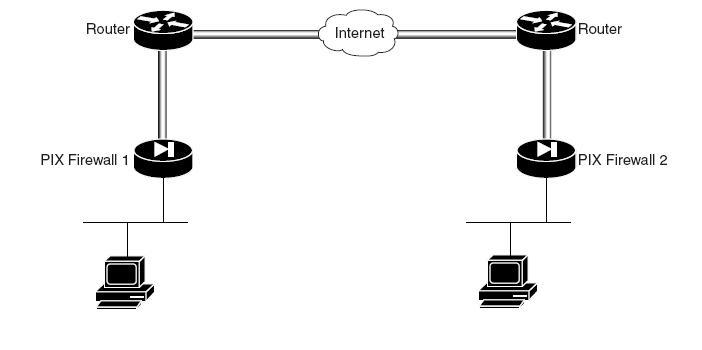
Each Cisco routers provide internet connectivity for its network. Both network must have public IP assigned by the Internet providers. PIX firewalls are used to negotiate and establish the VPN tunnel between two ends. The Cisco CallManager is used to handle all of the VOIP calls and it acts as PBX. Extra feature which can be used at the branch end by adding a Cisco CallManager Express on the top of the router (i.e. Cisco Integrated Services Router). In case of the VPN tunnel failure, the Cisco CallManager Express can still handle calls inside the branch network thus the employees can call each others (Davies 2007).
For the demonstration scenario, I will use GNS3 network simulator to simulate the VPN tunnel between the two ends.
For VOIP demonstration, I will use the following equipments:
- ADSL Cisco router (857)
- Broadband Cisco router (861) , with static public IP
- Linksys ATA (SPA 3102 and SPA 2102)
The two Cisco routers will negotiate and establish the VPN tunnel. The Linksys SPA 3102 will act as PBX and also can be connected to the PSTN telephone network using the FXO port. The Linksys SPA 2102 acts as an ATA (Analog Telephone Adapter).
Resources required for implementation
- A PC work station.
- Broadband Internet connection, with static Public IP.
- GNS3 Network Simulator.
Risk assessment
Risk management is important in order to ensure the successful completion of this phase of the project and also the complete project.
(Nielsen 1993)
Lack of management goodwill
This medium probability risk may be because of inadequate user involvement during system requirement elicitation. When the analysis process is not well performed and does not involve the management or address their concerns, then this is likely to occur. A contingency measure to counter this risk would be conducting an all inclusive systems requirements analysis. Highlighting the long-term benefits of the VPN implementation especially to the management. Establishing tangible economic benefits of the implementation is one of the ways of bringing the management onboard.
Natural disaster
This is a low to medium probability risk that may be because of the natural happenings such as floods, earthquakes, hurricanes and tornadoes among others. A contingency measure would be to establish and define adequate back up procedures most preferably offsite. However not much can be done about this natural occurrences. Only mitigation measures such as infrastructure insurance can be put in place to address this risk (Launer 2005).
Inadequate testing
This is a medium to high probability risk that may be as a result of project slip or an ill-prepared user or even inadequate user requirements capture process. Contingency measures in place may include a properly constructed project schedule that addresses the project tasks including testing in terms of duration and deliverables at the end of such as a phase.
User mistrust
This is a low probability risk as a result of poor analysis. Limited user involvement during the analysis resulting in inadequate system requirements elicitation is the main reason for such mistrust. Contingency measure would be a thorough analysis involving the user at that point and eventually during the project progression.
Limited expertise of the project team
Inadequate funding
This is a low probability risk mainly resulting from lack of management goodwill. While addressing the project benefits the management should be heavily involved and in agreement. The contingency measure here would be conducting an all-inclusive analysis.
References
Andersson, E., Greenspun, P. & Grumet, A., 2006. Software engineering for Internet applications. Cambridge : MIT.
Davies, B., 2007. Doing Successful Research project, using qualitative or quantitative methods. USA: Palgrave Macmillan.
Erica, H. & Priest, J., 2009. Business and management research: paradigms & practices. Basingstoke: Palgrave Macmillan.
IP telephony – Cisco systems (2010). Web.
Launer, L., 2005. Middle east airlines makes connection, Seattle, WA: The Boeing Company.
Lindsay, J., 1997. Software Engineering. Seattle, WA: The Boeing Company.
Nielsen, J., 1993. Usability Engineering. Cambridge Massachusetts: AP Professional.
Sommerville, I., 2004. Software Engineering. Harlow: Pearson Education.
Stallman, A. & Greene, J., 2005. Applied Software Project Management. Cambridge, MA: O’Reilly Media.
Suton, M., 2008. Middle east airlines makes connection with SITA- Technology: Arabianbusiness.com. Web.
Vbulletin, 2010. vbulletin. Web.
VPN, Virtual Private Networks, 2010. Web.