Introduction
E-bazaar is an open market for electronic goods. Its current business prospects are bringing in large profit margins, and the management is considering implementing an online system to connect its head office and the remotely located warehouse. This is expected to be accomplished within a tight but feasible budget.
The setup will include several workstations and servers, as well as high-quality printers (Darukhanawalla and Bellagamba, 2009). Additionally, there will be a need for multiple email addresses, basic security and authentication implementations, and internet access. E-bazaar is considering using the internet to connect to their remotely located warehouses. To achieve this and ensure that their online system is secure, the management has contracted VPN experts who have concluded that the e-bazaar needs a virtual private network implemented. In modern economies, businesses that previously used to handle local information now have to think of global markets. Multinational companies now have their branches and outlets spread all over the world (Ciampa, 2006).
Simultaneously, concerns of their network data security and hacker threats have become more prevalent. The nature of virtual private networks (VPN) and their secure establishments within public networks will be examined. Additionally, an understanding of VPNs will be established while keeping track of security mechanisms, paybacks and cost-saving rewards. For a long time communication has been through leased landlines within a wide area network (WAN). The WAN was reliable, secure and enabled businesses to have communication beyond their geographical areas. Unfortunately, the cost of using leased lines remains prohibitive especially when the distance between remote sites is large. With increase in the popularity of the internet, many businesses turned to the internet in order to cut on running costs and expand their network which has eventually paved way for the evolution of virtual private networks (VPNs).
Technology has undoubtedly transformed the way businesses and organizations share information and dissemination of feedback to customers and suppliers. Previously many companies had been reserved in trying to publish information on the internet (Brown, 1999). However, with the invention of VPNs, many businesses can now transact over the internet in critical information with little or no known business risk. A virtual private network represents a remote point to point connection linking two sites. This connection facilitates the transfer of data over a concealed link. Consequently, the secure link provides a private network communication, in the face of a public. A VPN has two core components. The first element is a VPN gateway with manifold network interfaces. The purpose of this component is to selectively encrypt and decrypts data as it flows through. The establishment of a VPN to connect two remote sites requires the use of two gateways. A VPN client on the other hand is the second component installed on a PC which moderately encrypts and decrypts data from a network protected by a VPN gateway. “Since VPNs can be created from anywhere in the internet, strong security features are needed to avert malicious access to private networks and secure private data as it is transmitted over the public network” (Step-by-step guide for setting up VPN-based remote access in a test lab, 2011, p.1).
One of the pertinent issues that arise from the use of VPNs especially for businesses like e-bazaar involves the security of corporate data and information. VPN implementation ensures that authentication processes such as Internet Protocol Security (IPSec) are implemented. Internet Protocol Security (IPSec) provides a framework for data security and user authentication within a public network (Kessler, 1998; Qu, 2002). It is a vigorous standard that has stood the test of time and emerged as a strong standard within the internet industry. Data authentication systems can be used to establish if the data has been modified on transit.
Authentication of all the remote users is of paramount importance to ensure that unauthorized persons are denied access to the private network. Alternatively digital certificates are credible for checking user identity and can be installed in the remote computer. There are basically three known approaches to virtual private network implementation. The choice depends on the need, funds available and suitability to the business or organization.
These general configurations include:
Intranet based VPN
This represents an IP-based password protected network suited especially for companies that disseminate information across a network while maintaining authorization.
Extranet-based VPN
Extranets allow controlled access to networks from external networks for example customers, and business associates closely related to the company. The business may want to connect to certain close contacts by way of a closely monitored extranet VPN.
Remote-access VPN
This type of VPN makes it possible for organization’s distant employees to access company resources inexpensively through the Internet Service Provider’s (ISP’s) infrastructure (Carugi and De Clercq, 2004). It is important to note that the same network can be used to establish the three different types of VPN namely: remote-access users, intranets, as well as extranets.
Besides encryption and decryption, a VPN must ensure that data is not modified in transit by authenticating senders which can be accomplished through a username and password (Yuan and Strayer, 2001). The process of proofing that data has not been tempered is called integrity checking and is done by executing a mathematical algorithm; to data prior to sending and figuring out the same hash at the recipients end.
Timely business processing is the most obvious advantage that results from VPN implementation (Burnes and Stoller, 1998). This is besides the cost saving on shared resources as well as operations and a centralized management even in dispersed settings. At the pace E-bazaar is doing business, it is envisaged that they are likely to expand their reach to open more branches to cater for increased demand for their products. Therefore, in providing this design plan additional consideration towards business expansion should also be considered (Fortenberry, 2001).
Securing VPNs
It is assumed that the e-bazaar network layout is a hub and spoke topology. Generally this topology adapts well to the dynamic multipoint VPN and can support IPSec between the spokes. The VPN topology implemented by e-bazaar is capable of supporting a number of VPN security solutions including IPSec direct encapsulation, virtual tunnel interface, DMVPN and generic route encapsulation (GRE) over IPSec (Quiggle, 2001; Lammle and Timm, 2003).
The point to point tunneling protocol (PPTP) defines one of the methods suitable to implement the e-bazaar VPN. The approach can use the point to point protocol (PPP) to implement security over the VPN that links e-bazaar’s outlets (clients) and the warehouse which is remotely located.
General explanation of VPN infrastructure implementation
In order to setup a simulated site to site VPN implementation a number of requirements are necessary. As indicated in the diagram that follows here below five computers will be needed. Each of which has average capabilities and able to support interconnections. “Additionally, there will be need for other connectivity devices such as hubs or switches in order to ensure that the network is partitioned as shown in the figure (Figure. 1)” (Brown 1999, p. 31). The VPN implementation will be carried out using Windows 2003 server standard edition installed on the virtual console from where a number of screen shots of the setup process will be generated. The five computers will be setup to simulate different functions necessary to portray a site to site VPN environment. Four of the five computers will be running Windows 2003 Server standard edition apart from the computer dedicated as the client which will be running Windows XP professional edition.
The Windows 2003 Server software is a suitable choice to use for this exercise because it is packaged with many other support tools such as ‘autoenrollment’ that can be utilized to implement this simulation.
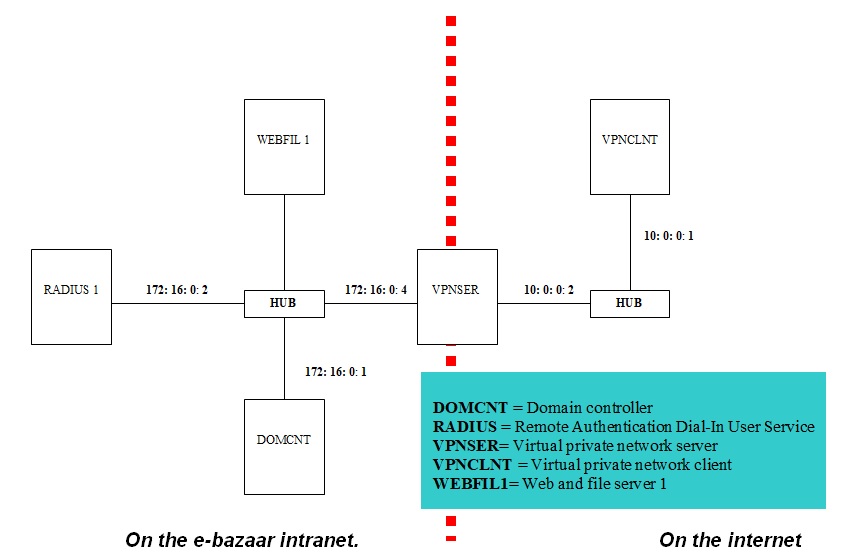
From the diagram above, a portion of the network represents e-bazaar’s intranet while the other portion represents the internet network segment. The computers on e-bazaar’s network are interconnected using a layer 2 switch. VPN layer 2 implementations are also feasible with Cisco appliances (Luo, 2005; Xu, 2009). Private IP addresses are assigned to all the computers used within this setup. The IP address 172:16:0:0/24 is assigned to e-bazaar’s intranet while 10:0:0:0/24 represents the internet portion of the network. Firewalls are setup on RADIUS1 and web and file server (WEBFIL). The firewall is configured on the client computer (VPNCLNT).
However, it will not be necessary to setup a firewall on the domain controller (DOMCNT) as well as on the virtual private network server (VPNSER).
“WEBFIL 1 obtains its IP address using dynamic host configuration protocol (DHCP) process that is automatic (dynamic) addressing” (Brown 1999, p. 31). WEBFIL 1 will also be manually setup and given a static IP address to enable it to operate on the intranet as well as the internet. The other computers in this setup will have static IP addresses.
DOMCNT
This computer has a Windows 2003 Server installation supporting the following:
- A customized Active directory domain for the business in this case e-bazaar.com domain.
- A domain name service server for the e-bazaar.com domain
- Dynamic host configuration protocol server to support the intranet portion of the setup.
- A certification authority for example the e-bazaar.com domain.
Experiments and Results
Configuring the domain controller (DOMCNT)
The prerequisites for this setup will include the following (as shown in the appendix).
Conclusion
This paper has in part tried to demonstrate the practical steps undertaken in order to implement a virtual private network for E-bazaar which is able to connect a client to E-bazaar’s warehouse which is remotely located. The point to point tunneling protocol (PPTP) based remote access connection has been covered in detail in this writing and demonstration. It is important to realize that other implementation options using different approaches such as layer 2 tunneling protocol / Internet protocol security (L2TP/IPSec) and EAP-TLS approaches are also feasible for this setup. These other approaches can also be implemented and supported by a similar structure. With the successful testing of this implementation, it is highly likely that E-bazaar management will approve the use of a VPN in their business to gain maximum profits and acquire the much needed competitive advantage.
It is in this light also that the virtual private network implemented will improve the business processes at E-bazaar and eventually cut on operational costs. In closing this discussion it is vital to mention in passing some of the disadvantages that may accrue from the implementation of virtual private networks. The most common one is the incompatibilities among VPN vendor products (Fowler, 1999; Venkateswaran, 2001). It can also be mentioned that the implementation of VPN requires substantial resources especially during planning and setup. Additionally there is a continued and potentially destructive online threat that is normally encountered by businesses using VPN. However as much as this is the case the advantages that VPN implementation has for an organization or business far outweigh these disadvantages. Virtual private network implementation for E-bazaar remains an important undertaking that will lead to improved sales and profits for the business. A well thought out plan with appropriate funding is likely to result in a most profitable solution for E-bazaar.
Reference List
Brown, S. 1999. Implementing virtual private networks. New York: McGraw Hill.
Burnes, G. and Stoller, G., 1998. Virtual private networking. Storage Management Solution, 3(1), pp.44-46.
Carugi, M. and De Clercq, J., 2004. Virtual private network services: Scenarios, requirements and architectural constructs from a standardization perspective. Communications Magazine, 42(6), pp.116-122.
Ciampa, M., 2006. CWNA guide to wireless LANs /Uniform title: Guide to wireless communications. 2nd ed. Boston: Thomson Course Technology.
Darukhanawalla, N. and Bellagamba, P., 2009. Interconnecting data centres using VPLs. Indianapolis: Cisco Press.
Fortenberry, T., 2001. Windows 2000 virtual private networking. Indianapolis: Sams Publishers.
Fowler, D., 1999. Virtual private networks: Making the right connection. Waltham: Morgan Kaufmann.
Kessler, G., 1998. An Overview of Cryptography 2006, Web.
Lammle, T. and Timm, C., 2003. CCSP: Securing Cisco IOS networks study guide. Alameda: Sybex.
Luo, W., 2005. Layer 2 VPN architectures. Indianapolis: Cisco Press.
Qu, W., 2002. IPSec-based secure wireless virtual private network. MILCOM 2002 Proceedings (7th – 10th October), pp.1107-1112.
Quiggle, A., 2001. Implementing Cisco VPNs. New York: McGraw Hill.
Venkateswaran, R., 2001. Virtual private networks. Potentials IEEE, 20(1), pp.11-15.
Xu, Z., 2009. Designing and implementing IP/MPLS – based Ethernet layer 2 VPN services: An advanced guide for VPLS and VLL. New York: Wiley.
Yuan, R. and Strayer, T., 2001. Virtual private networks: Technologies and solutions. Muchen: Addison Wesley.