Introduction
With the current rate at which internet is developing, it becomes more and more feasible to utilize the infrastructure dedicated for public networks. Such utilization eliminates the need to build an infrastructure that will connect different private networks. In that regard, the principle can be seen as the main foundation lying in the work of Virtual Private Networks. Virtual Private Network (VPN) can be defined as “a set of interconnected networks in different locations “(Finlayson et al., 2003).
For the business environment such technology can be specifically important, especially in a contemporary context. There are several usages of VPN. One of which can be seen through the fact that outsourcing and distant working are two of the aspects in the current environment which demand that users working distantly should be connected into a single private network. In that regard, the option of using the networks provided by the service providers, such as those using ATM and Frame Relay protocols, can be seen costly with their bandwidth insufficient (Finlayson et al., 2003).
The security of such leased line s is another issue that put such choice in a disadvantage. In that regard, implementing VPN technology in a constructing an enterprise network can be seen as a suitable solution which will reduce the costs of usage for the company and the user, provide sufficient bandwidth, secure the connection, and at the same can be used in multiple business purposes (Barracuda Networks, 2009).
In that regard, considering the fact that that the majority if not all modern business corporations have private network, which are connected to the internet, the present paper will document the process of designing and implementing VPN in a general business environment of small to medium companies, in which the main emphasis is put on the providing remote to users to the company’s private network.
Requirements and Technologies
In order to identify the main requirements for the project, two research were conducted to collect data on such aspect – a primary research and secondary research. The aim of the primary research was in identifying the technologies, while the aim of the secondary research was in investigating each of the identified technology.
Primary Research
For the primary research, a series of semi-structured interviews were conducted with Information Technology (IT) specialists administering private networks in different t companies. The aim of the research was in identifying the common technologies and requirement needed to implement VPN in a company.
Five respondents were selected through convenience sampling (Creswell, 2009), with individual interviews scheduled in a period of a week. The outline of the interview can be seen in Figure 1. The interviews were recorded and transcribed for analysis and identification of common elements.

The common components needed to provide a remote access for the users in a company were identified in the primary research as follows:
- VPN client
- VPN server
- Firewall
- IPSEK Encryption
The aforementioned components were identified as common and necessary in an every case of VPN remote access to the company’s intranet. To the question on additional optional requirements that might implemented in the network, three respondents indicated additional authentication system for the computers used by the users, e.g. finger print authentication, while two respondents indicated autonomy of the servers as an important aspect that should be considered in order to keep servers running.
All respondents recommended paying attention to software and hardware compatibility when designing VPN. The overall design of VPN for a small business can be seen on the figure below.
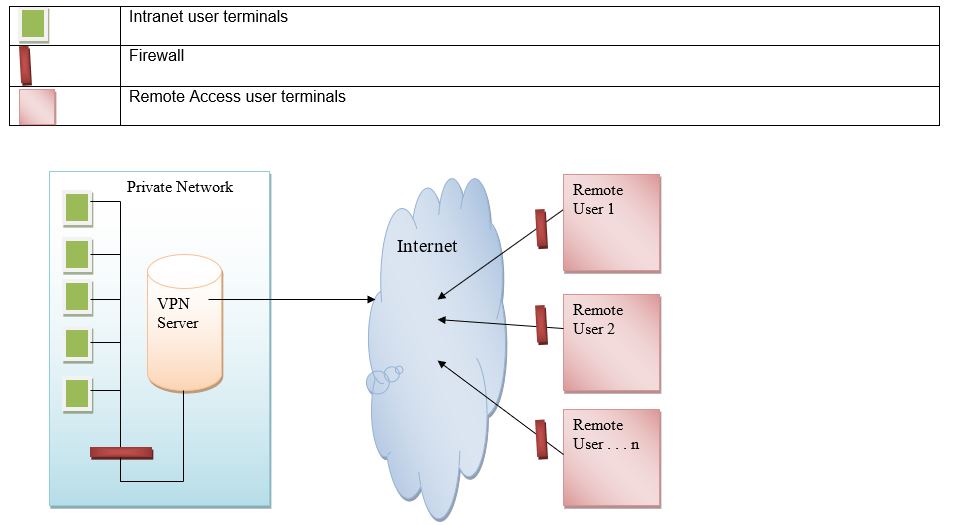
Secondary Research
The secondary research involves analyzing the literature on the technologies identified in the primary research, providing an overview and general recommendations that should be used in forming the requirements of the system.
IPsec
IPSec encryption is related to the general framework of the security of remote access which is Authentication, Authorization and Accounting (AAA) (Hernick, 2007). IPsec is related to the authentication aspect of such framework in which other security protocols include PAP, CHAP, EAP, and IPsec.
IPSec can be defined as the protocol that provides security services as the IP layer by “enabling a system to select required security protocols, determine the algorithm(s) to use for the service(s), and put in place any cryptographic keys required to provide the requested services” (Hernick, 2007). An alternative to using IPsec can be seen thorough Secure Socket Layer (SSL). The choice of IPsec can be seen justified by the fact that SSL is limited to web-based applications, and in that regard, in case the cooperation between remote users and the company’s intranet involves such aspects as printing, file sharing, etc, SSL might not suit the purpose.
Additionally, IPsec provides additional level of security (Bradley). Thus, IPsec can be seen as the recomme3nd protocol to be used, although regardless of the choice, it is stated that neither of the protocols protects from vulnerabilities such as the following:
- Virus outbreaks
- Slow network conditions generated from unwanted traffic.
- Impersonation of authorized users.
Firewall
Firewalls refer to any software or hardware barrier that protects network entry points, protecting “organization’s network from malware and other threat agents seeking to enter through connections to the internet or other external networks” (Olzak, 2006). Firewalls can be implemented on the hardware and the software level in the proposed network.
Considering the costs, it is suggested that individual remote users install firewalls on each terminal independently through software, while private network can be protected using hardware firewalls. Accordingly, the firewall might be separated from VPN, or used as an integrated VPN gateway that combines more than one function at once, e.g. firewall, VPN, and a router.
The important aspect is to configure the firewall to let VPN IPsec traffic go through (Lewis, 2006). The choice of using either of the options, i.e., an integrated or a separate solution might depend on the size of the company, the number of terminal, and the estimated bandwidth of the traffic.
Requirements
The main requirements that can be derived from the research can be seen in indicating the minimum hardware and software recommendations for both remote users and the intranet in the company. For the private intranet, the following recommendations were identified:
- The network server
Software requirements – Microsoft Server 2003 can be recommended as the software that will run the server, covering such infrastructure requirement as “a domain controller, DNS server, Certificate authority and DHCP-(Dynamic Host Configuration Protocol) server” (VPN Tools).
Hardware requirement – the hardware requirements for the server can be seen through the official requirements recommended to be used with Microsoft Server 2003, which include:
- Minimum 550 MHz processor
- Minimum 256 megabytes of Ram (Microsoft, 2005)
It should be noted that the aforementioned requirements are the minimum recommended, and thus, increasing the number of terminals in the network, the requirements should be increased as well.
- The VPN server
The VPN software can be implemented through a specified hardware solution such as a Cisco dedicated VPN 3000 concentrator. Such hardware can be used with specific software Cisco 1751(Cisco Systems, 2004). Using unified software hardware platform can increase compatibility and facilitate the installation and the configuration phase.
Remote users –remote users might not be obliged to specific hardware requirements, where “VPN user may require a solution that does not involve a costly replacement of their existing hardware” (Finlayson et al., 2003). In terms of software, no VPN client is required for operating systems above Windows 98.
Thus, Windows XP might be recommended as the minimum for clients, with any hardware requirements corresponding to the selected operating system. It should be noted that bandwidth minimum requirement will depend on the tasks remote users are required to perform.
Risk Assessment
The risks in IT projects are common and in that regard appropriate risks assessment should be conducted in order to identify the risks, their degree, and the plan that can be used to mitigate such risks. Although there are external environmental factor that might influence risks (Murch, 2001), the following table will attempt to indicate the internal risks that might occur at various stages of the project.
Table 1. Risk assessment.
Gantt Chart
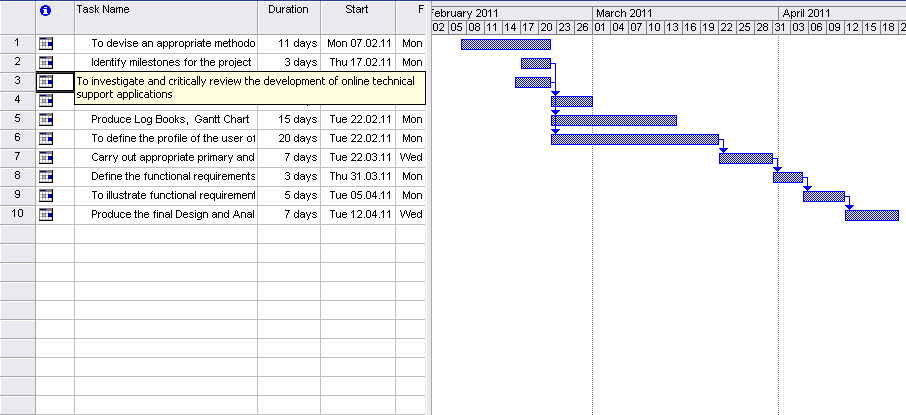
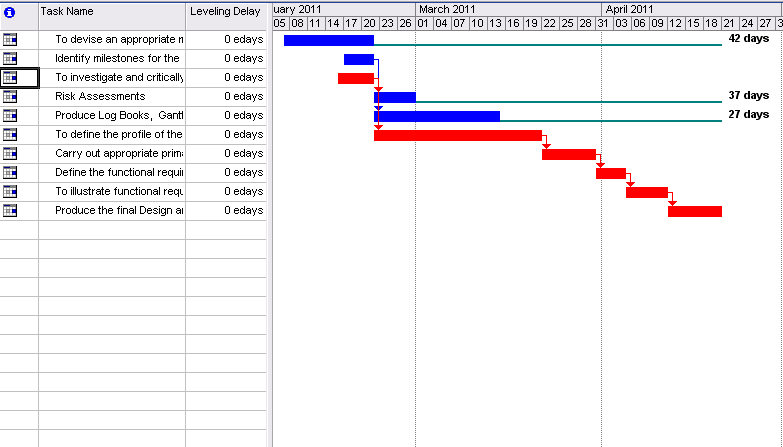
Table 2. PERT table.
References
BARRACUDA NETWORKS. 2009. VPN Technologies Barracuda SSL VPN. Barracuda Networks. Web.
BRADLEY, T. VPN’s: IPSec vs. SSL. About.com Guide. Web.
CISCO SYSTEMS. 2004. CONFIGURING CISCO VPN CLIENT AND EASY VPN SERVER WITH XAUTH AND SPLIT TUNNELING. Cisco Systems. Web.
CRESWELL, J. W. 2009. Research design : qualitative, quantitative, and mixed method approaches, Lincoln, Sage Publications.
FINLAYSON, M., HARRISON, J. & SUGARMAN, R. 2003. VPN Technologies – A Comparison. MetaSwitch Networks. Web.
HERNICK, B. 2007. VPN SECURITY AND INDIVIDUAL USER IDENTIFICATION METHODS. Master of Science in Management Information Systems Research Project, University of Maryland.
LEWIS, M. 2006. Comparing, designing, and deploying VPNs, Indianapolis, Ind., Cisco Press.
MICROSOFT. 2005. Windows Server 2003, Enterprise Edition: System requirements. Web.
MURCH, R. 2001. Project management : best practices for IT professionals, Upper Saddle River, NJ, Prentice Hall.
OLZAK, T. 2006. Just Enough Security, CyberRead Publishing.
VPN TOOLS. Setting up a VPN: Do it yourself . VPNTools.com. Web.