Abstract
Privilege escalation detects possible malicious operations by detecting the usage of unnecessary privileges. By abusing security or setting on an application or system component, privilege escalation refers to a strategy for getting access to privileges that should not be accessible to that individual. The participants in this qualitative study were college students, and it was conducted entirely online. Primary and secondary sources played an essential role in the data collection process, while thematic analysis took an essential role in the investigation. Privilege escalation allows attackers to access a system, maintain and improve their expertise, and engage in a more dangerous and severe activity. Attackers who seek to escalate their privileges can exploit single-step verification. Even if an attacker does not have the password, it is only a matter of time before they gain an authorized user’s username. If they get a working password, they can move around the system undetected.
Introduction and Background
Regarding privileges, the operations and programs must be provided by users, including whatever they require to perform respective jobs with ease. Unnecessary additional privileges can misuse the permissions, so privilege escalation detects possible malicious activities. Privilege escalation denotes a technique for gaining access to privileges that should not be accessible to that person by exploiting security or set on an application or system component. An attacker with escalated rights can steal personal information, install malware, and even cause serious harm to a Linux kernel. The attackers begin by identifying the target computer to learn about the applications that are installed on it. After outlining the target machine, the attacker devises a strategy for another step and compiles a summary of the data obtained thus far. The perpetrator then confirms that the loophole exists and leverages the session hijacking flaw on the client’s computer, allowing them to bypass the existing user account’s limits.
The assailant can access the functioning and information of another person through horizontal allowances or gain higher-level privileges, such as those of an owner or administrator, a process described as vertical escalation. The horizontal vulnerability allows an attacker to keep their general user privileges while gaining access to the functionality or content of other identities. The vertical susceptibility allows the invader to achieve administrative access, such as Windows manager or an entire client on a Linux operating system. It is much more dangerous than horizontal user credentials since attackers gain privileges from a less privileged user to a more excellent privileged user. With these valid credentials, the attacker can steal all confidential material, conduct potentially dangerous instructions, install malicious on the machine, and severely damage the operating system. Offenders can erase any traces of their activities by destroying records and other proof, allowing thieves to steal sensitive data or install malware straight on workplace computers.
This paper explored the security tactics that could contribute to a better privilege escalation assault on every Linux-based computer. Aggressors can utilize testimonial exploitation, susceptibilities, misconfigurations, social engineering, and malware to elevate system privileges. Kernel exploits and abusing SUDO Rights are two approaches for escalating privileges in Linux. Credential exposure, assuming passwords, shoulder browsing, dictionary assaults, rainbow table attempts, password guessing attacks, login spraying, password updates and resetting, and credential cramming are all strategies used by attackers to obtain entry to information.
Cloud storage tubs subjected to the web with no verification, logins used for admin accounts, and insecure missed payments due to incompetence or lack of awareness can result in session hijacking. An invader discovers a vulnerability in the system accessible to managers but not disclosed. Worms, evil bots, rootkits, ransomware, trojans, spyware, and adware are illustrations of software utilized for privilege escalation. Scareware, phishing, and pharming are examples of social engineering assaults that intruders can use to increase privileges. When attacking kernels, attackers must first discover the flaws, create or acquire hacking tools, transmit the vulnerability to the destination, and run the exploit.
Problem Statement
While Windows clients are statistically more common, Linux vulnerability assaults are serious weaknesses to evaluate a corporation’s security stance. A company’s most essential services, such as databases, web servers, and firewalls, are almost certainly running Linux. Constraints to these crucial systems can seriously impair if not wholly destroy, an entity’s ability. As the Internet of Things (IoT) and integrated technologies become more commonplace in the workforce, potential victims of evil hackers grow. Given the widespread use of Linux machines in the office, this equipment must be hardened and secured.
Objectives of The Project
The primary objectives of this study include exploring the security tactics that could contribute to a better privilege escalation assault on every Linux-based computer. This research also considers how intruders can effectively elevate their credentials on a host machine using known tactics and how users can safeguard their networks from such attacks. This research will enable the researcher to absorb the foundations of Linux remote access; it is not a cheat sheet for using Linux functions to enumerate things but offers an appropriate enumeration for user credentials.
Literature Review
Users borrowed the idea of file management and permissions from UNIX. One method the system defends itself from unauthorized interference is through access policies. Every document and directory on a UNIX web application has various functionalities, determining who is permitted to access the file. Any other person attempting to read the file will be unable to do the practice. When one tries to view the folder as a non-superuser, they receive the permission refused error. There are various categories of Privilege Escalation in Linux, including kernel exploits, misusing services running as a source, abusing SUID executables, manipulating SUDO privileges/user, exploiting poorly configured cron jobs, and users with ‘.’ in their path, file permissions, and password mining.
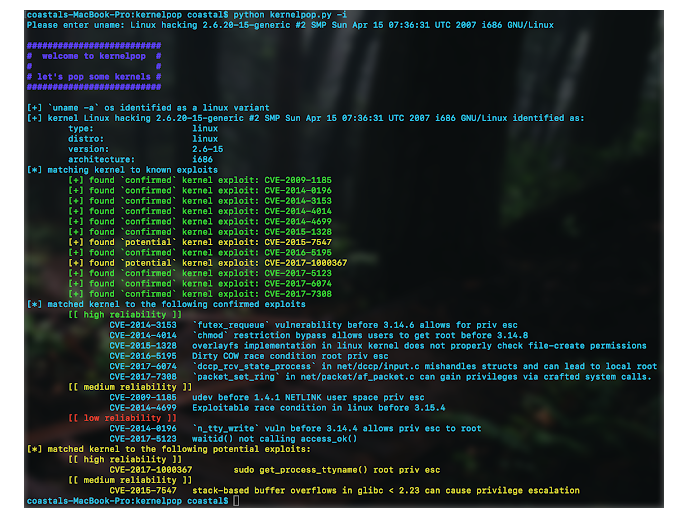
Intruders use kernel exploits, a software element that lies at its foundation and has complete control over every event in the machine, to escalate privileges. Consequently, exploiting kernel weaknesses almost invariably results in a complete cyber breach. They target a specific edition of the kernel or system software and are typically run remotely on the targeted system to elevate permissions to root. Kernel exploits describe programs that use kernel flaws to run obfuscated code with enhanced privileges. In the manner of a master command prompt, effective kernel exploits often grant hackers superusers access to computers. Escalating to the administrator on a Linux machine can often be as simple as copying a kernel vulnerability to the destination file system, developing it, and running it. The first step in finding OS & Kernel information is to enumerate the present operating system and kernel information to detect possible kernel exploits. To manually examine kernel information, intruders run “uname –a; lsb release -a; cat /proc/version /etc/issue /etc/*-release; hostnamectl | grep Kernel”.
The well-known EternalBlue and SambaCry exploits take advantage of the Linux privilege escalation service, usually executed as root. Exploiting services running as a source enables an enemy to obtain code implementation and Local Password Cracking only with one vulnerability. Along with its dangerous combination, users widely used it to propagate ransomware worldwide. Users should constantly ensure that web servers, database servers, mail servers, and other services are not installed as root. Network administrators frequently operate these facilities as root, oblivious to the security risks. There may be remote services but are never reachable to the public.
Exploiting SUID privileges allows an attacker to execute arbitrary files with the proprietor’s rights, which can be granted on a Linux executable for many purposes. The ping tool, for example, requires root rights to start a stable connection, but non-root users can also use it to check the connection with other sites. To access raw network connections, the Linux ping tool, for example, typically requires root capabilities. When the ping software is marked as SUID and the owner is set to root, ping runs with root access whenever a truncated privilege program runs. The issue is that when managers install third-party software or perform logical modifications, they may unintentionally introduce unsafe SUID setups. Many sysadmins don’t know where to put the SUID value and where to avoid it. Because an intruder can rewrite any system files if the SUID bit is set, it must not be set by users on any document editor.
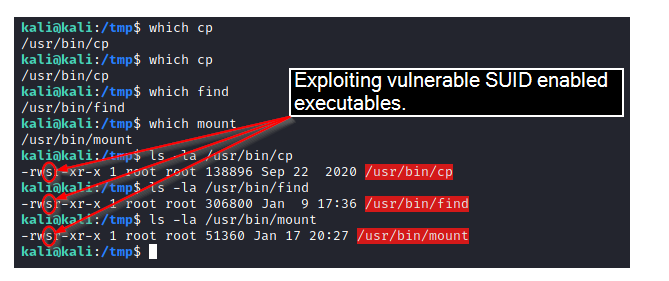
Specific instructions list all of the SUID commands currently on the structure. The guidelines will look for documentation in the / encyclopedia the operator root possesses with the SUID authorization print them, bits, and redirect all faults to /dev/null. The authorization indicates only the files that the person has access to view. The commands will look for files in the / folder controlled by the username core to show only the files that the person has access to view. The folder has the SUID authorization bits, writes them, and then diverts all exceptions to “/dev/null. find / -user root -perm -4000 -print 2>/dev/null find / -perm -u=s -type f 2>/dev/null find / -user root -perm -4000 -exec ls -ldb {} ; “
If the assailant cannot gain root access through other means, he may attempt to corrupt the individuals by manipulating SUDO access. Invaders can essentially execute any query with root capabilities once they obtain a connection to any SUDO users. Administrators may only enable users to perform a few operations through SUDO, but not all tasks. Still, they risk unintentionally introducing vulnerabilities that could lead to backdoors. Assigning SUDO access to the search command, for example, allows other users to find specific files/logs in the computer. An assailant can execute code with root permission even if the admin is uninformed that the ‘find’ command comprises arguments for command accomplishment.
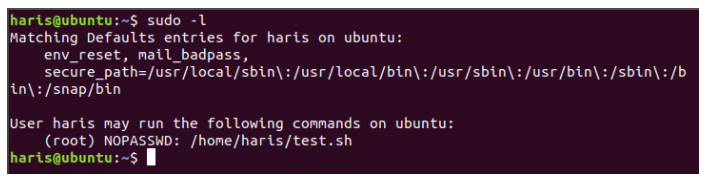
If not correctly configured, attackers can use Cron tasks to gain root access. Cron jobs are typically run with system privileges. Individuals can launch obfuscated code with admin privilege if people can effectively tamper with any scripts or binary specified in the cron tasks. ‘.’ in a given PATH shows that the person can run compiled code from the root folder. The user inserts ‘.’ to their PATH to avoid getting to type those two different words every time, which is an excellent way for an intruder to increase their privileges. For instance, if Susan is a system administrator who adds ‘.’ to her path to avoid having to type the two characters twice. When ‘.’ is added to the PATH initially, Linux looks for the program first in the current directory, then elsewhere.
Methodology Adopted
This qualitative research was conducted in a cyber, whereby the targeted participants were college learners. Both primary and secondary sources played significant roles in data collection. Primary sources denote the researcher’s first-hand information directly from the field, while the scholar obtains secondary data from printed materials such as books, journals, and websites. The researcher conducted various surveys during the data collection, recorded in a tape for future use. Thematic analysis played a significant function in the analysis. A method of probing qualitative information is content analysis. Thematic analysis played an essential role in the investigation. Content analysis is one method of analyzing qualitative data. It is usually used to refer to a collection of texts, such as an interrogation or translation.
Privilege escalation allows attackers to access a system, maintain and improve their expertise, and engage in more dangerous and severe activities. For example, privilege escalation can turn a superficial viral infection into a significant data breach. Attackers who seek to escalate their privileges can exploit single-step verification. Even if an attacker does not have the password, it is only a matter of time before they gain an authorized user’s username. If they get a working password, they can move around the system undetected. Among the ethical issues, the researcher faced included unwillingness from the participants to answer some of the questions they were asked by the researcher as most of them thought their data could be interfered with or used for other purposes other than research aims.
Results and Project Findings
Privilege escalation enables attackers to acquire system access, maintain and enhance their expertise, and engage in more harmful severe behavior. Privilege escalation, for instance, can turn a minor virus infection into a significant data breach. Privilege escalation notices possible malicious operations by detecting the usage of unnecessary extra privileges. By abusing security or setting on an application or system component, privilege escalation refers to a strategy for getting access to privileges that should not be accessible to that individual. Assailants can use privilege provocations to open up additional attack avenues on a victim machine. Increased exposure to other devices connected, deploying more malicious files on a victim machine, altering privacy controls or rights, and gaining mobile access or information on a scheme beyond the permissions of the initial compromised account are just a few examples.
In exceptional cases, obtaining root privileges to a target computer or a core system is critical in conducting investigations when security personnel suspects root access. Malware on critical areas, odd logins, and unexpected computer networks are all signs of user credentials. According to the firm’s compliance requirements, any vulnerability occurrence must be treated as a severe security alert and may need to be disclosed to authorities. There are various categories of Privilege Escalation in Linux. The methods include kernel exploits, misusing services running as a source, abusing SUID executables, manipulating SUDO privileges/user, exploiting poorly configured cron jobs, and users with ‘.’ in their path, file permissions, and password mining. Security flaws such as software defects, configuration issues, and erroneous network access are commonly used in session hijacking attacks.
Every user that communicates with a program has some level of authority. System databases, tender documents, and other infrastructure are typically restricted to users. Because they never endeavor to get access beyond their permissions, users may have inappropriate access to classified resources and may not be conscious of it. In other circumstances, attackers can take advantage of system flaws to access higher privilege levels. A hostile attacker can access restricted access by gaining control of a low-level user profile and either misusing or expanding privileges. Attackers can stay in a system for a long time, gathering information and looking for a chance to expand their access. They will eventually figure out a means to elevate access to high level than the identity that was compromised in the first place. Depending on their objectives, attackers can move horizontally to obtain control of more systems or vertically to get the admin and root access until they have complete control of the entire environment.
Recommendations
Kernel exploits should be avoided by monitoring security reports and installing Linux updates and patches as soon as possible. Administrators should restrict or disable file transfer applications like FTP, SCP, or curl, or limit access to various individuals or IP addresses, which can prevent an exploit from being transferred to a targeted system. Operators should remove or limit access to languages like GCC to prevent vulnerabilities from being executed. They ought to restrict the number of writable and executable directories. Vi, less, more, Nmap, ruby, Perl, gdb, and python are examples of programming languages that compilers, interpreters, and editors should never be given in SUDO permissions.
Any program that allows users to execute a shell should not be given SUDO rights since the least-privilege approach restricts SUDO access. Software that allows anyone to jump to the shell should not have the SUID bit set. An invader can recite or overwrite any records on the scheme when the SUID bit is established on any folder. Unless necessary, users should never launch any service as root, notably web, database, and file servers, but should maintain a patched and updated kernel. Any cron job-defined scripts or binaries should not be readable; only root should be allowed to write to the cron file and cron.d directory.
Conclusion
Single-step verification leaves an opening for attackers who want to escalate their privileges. It’s only a matter of how long an attacker obtains an authorized user’s username – even if they don’t have the password. They can travel laterally via the system undetected if they get a functioning password. Even though the assailant is discovered and the company changes the loggings or reimages the vulnerable system, the intruder may be able to maintain a firm hold, for example, through a hacked cell telephone or rootkit software on a device. As a result, it’s critical to eliminate the threat and keep an eye out for anomalies. Attackers can gain elevated privileges by exploiting design flaws, execution, or setup of numerous systems, encompassing communication systems, data transports, software platforms, computers, web apps, cloud services, and internet infrastructure. After obtaining entry to a user account, attackers can install malware at the user level and then discover how to elevate their capabilities. Attackers with elevated rights can employ malware to get continuous access to the complete environment by deploying it at the admin or root level.
References
Ahmed, A. (2021). Privilege Escalation Techniques (p. Chapter 1). Packt.
Ghavamnia, S., Palit, T., Benameur, A., & Polychronakis, M. (2020). Confine: Automated system call policy generation for container attack surface reduction. In 23rd International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2020) (pp. 443-458). Web.
Jacobsen, R. H., & Marandi, A. Security threats analysis of the unmanned aerial vehicle system. In MILCOM 2021-2021 IEEE Military Communications Conference (MILCOM) (pp. 316-322). IEEE. Web.
Kernelpop – Kernel Privilege Escalation Enumeration and Exploitation Framework. KitPloit – PenTest & hacking tools. (2022). Web.
Li, M., Zhang, Y., Lin, Z., & Solihin, Y. (2019). Exploiting unprotected operations in secure encrypted virtualization. In 28th USENIX Security Symposium (USENIX Security 19) (pp. 1257-1272). Web.
Linux Privilege Escalation by exploiting vulnerable SUID Executables. Medium. (2022). Web.
Linux Privilege Escalation exploiting Sudo Rights — Part I. Medium. (2022). Web.
Nowell, L. S., Norris, J. M., White, D. E., & Moules, N. J. (2017). Thematic analysis: Striving to meet the trustworthiness criteria. International journal of qualitative methods, 16(1), 1609406917733847. Web.
O’Leary, M. (2019). Privilege escalation in Linux. In Cyber Operations (pp. 419-453). Apress, Berkeley, CA. Web.