Introduction
Literature review pertains to cross-examining what other scholars have done in the field of study. This is based on the idea that knowledge is cumulative. Revisiting other people’s ideas and thoughts help in formulating both theoretical and conceptual frameworks. In this study, the researcher will employ some theories of motivation, which are part of theoretical literature.
Conceptual literature will be revisited by scrutinizing what other researchers have concluded in their studies regarding to motivation of employees. Literature review is important because it offers a foundation to any study.
Generally, literature review is related to determining how much is known. It is important because it keeps away unnecessary duplication of data and gives more knowledge to the researcher (Lauby 2005, p. 7). The researcher can only avoid mistakes committed by other researchers if he/she reviews literature. Therefore, review of literature helps a researcher to formulate a study that stands the taste of time.
Child Pornography
Research shows that child pornographic material found on the internet is usually a result of abduction. This behavior has always threatened to interfere with the very survival of society since it has various effects to children. Children found engaging in pornography are normally victimized.
In one of the studies conducted in the US, 100 victims were interviewed and the results had some similarities. First, victims complained about physical pain because they were forced to engage in activities that they are not used to doing. Children feel threatened because those taking them through such pains might even be their relatives (Dombrowski, Gischlar, & Durst, 2007).
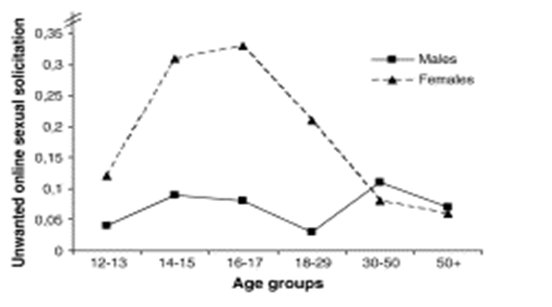
Unwanted sexual solicitation
As shown in the graph below, adolescents are in danger of sexual solicitation. Since there is no enough data to support this claim, this study would try to prove that unwanted internet sexual solicitation affects family relations in one way or the other.
Through the internet, the family is exposed to risky sexual behaviors. A study conducted in Dutch among the adolescents indicated that adolescents were likely to engage in sexual solicitation as opposed to adults. In the study, females were frequently solicited as opposed to men. In the study, the benefits of sexual solicitation were few as compared to the risks (Bourke, & Hernandez, 2009).
Conclusion
From the above information, it is eminent that research gaps exist hence it is pertinent to conduct a study to establish the extent at which the internet affects family relations.
Methodology
The proposal would utilize quantitative research methods in conducting the study and collecting data. Quantitative research would be used since it aims at summarizing data mathematically.
In this regard, the research will take the form of a survey, whereby the researcher will identify some individuals and post questionnaires to them. The sampled population will be selected randomly in order to eliminate biases (Hakim, 2000). The researcher will further make follow-ups, by conducting respondents on phone.
Design
There will be two key methods used to gather information in the proposal. The first one will be through a questionaire, which will be administered online to the selected victims and offenders. The questionaire will seek to capture various attutudes of victims and offenders as regards to child pornography and unwanted sexual solicitation.
The second source of information that will be used in the proposal would be literature on various aspects internet harassment. The focus of the literature review will be to find information on effects of the internet on family members and also to determine the current state of research as regards to the effects of the internet. The questionnaire will have four Parts.
The first part will seek to capture the biodata information of respondents. The second part will deal with the demography and gender of the respondents. This would ascertain the prevalence of views in varoius categories in order to ensure that if any differences come about, then they would be captured in their demographic space.
The third part will deal with societal status and experience of both victims and offenders as regards to child pornography and unwanted sexual solicitation (Creswell, 2003).
The motivation for this section came from the understanding that different sections of population respond differently to change, based on age and societal status. The fourth part will delve into the specific issues relating to the effects of the internet to victims and offenders, starting from the understanding of the concept to the possible effects it would have on respondents.
Theoretical and Conceptual Framework
The study will utilize deductive scaffold because some theories will be used to give a certain picture of the study. Deductive reasoning starts by analyzing some concepts before moving to the field to confirm the claims.
The researcher will analyze some theories related to child pornography and unwanted sexual solicitation before moving to the field to collect data. The technique is constructive because it equips the researcher with relevant information. In other words, deductive reasoning moves from generalizations to the specific idea. Two theories will first be analyzed before moving to the field.
Sampling Methods
The most applicable sampling method for the proposal will be random sampling. Considering that the targeted population consists of children and adults in the families, there was no much risk of having biased data.
If the survey needed to cover the entire family members, systematic sampling, coupled with stratified sampling would be ideal to ensure cross-sectional representation. However, the survey targeted children and their parents. Hence, random sampling would prove to be sufficient to collect required data (Crotty, 2003).
References
Bourke, M., & Hernandez, A. (2009). The Butner Study, Redux: A Report of the Incidence of Hands on Child Victimization by Child Pornography Offenders. Journal of Family Violence, 24(3), 183–93.
Creswell, J. (2003). Research design: Quantitative, qualitative, and mixed methods approaches (2nd ed.). Thousand Oaks, CA: Sage.
Crotty, M. (2003). The Foundations of Social Research: meaning and perspective in the research process. London: Sage.
Dombrowski, S., Gischlar, K., & Durst, T. (2007). Safeguarding Young People from Cyber Pornography and Cyber Sexual Predation: A Major Dilemma of the Internet. Child Abuse Review, 16(3), 153–70.
Hakim, C (2000). Research Design: Sucessful Designs for Social and Economic Research. New York: Routledge.