Computer systems have experienced significant advancements over the past two decades. This has led to an increase in their use as more organizations employ these systems to harness the informational process and communication benefits of computers. The pervasive use of computer systems has led to an increase in the number of attacks on computer networks. The sophistication of the attacks carried out against computer networks has also risen, making it necessary for countermeasures to be developed against the attacks. An integral tool in the protection of the computer network infrastructure from attacks is the Intrusion detection and prevention systems.
Intrusion detection and prevention systems (IDPS) are systems that detect intrusions on the network and then react to block or prevent these unwanted activities. IDPSs, therefore, perform the task of intrusion detection and intrusion prevention. The detection task entails analysing the computer system and network for any inappropriate, incorrect, or anomalous activity. The intrusion prevention process entails taking action that is aimed at blocking or preventing the attacks that have been identified. The IDPSs has five major elements that include the data gathering module, the pre-filtering module, the decision-making module, the communications module, and the human interface module (Furnell 167).
The data gathering module obtains data from the network or the host. The pre-filtering module assesses the gathered data to discard the data that is not relevant to security. The rest of the data is sent to the decision-making module, which uses various intrusion detection techniques to determine if an intrusion has taken place and its exact nature.
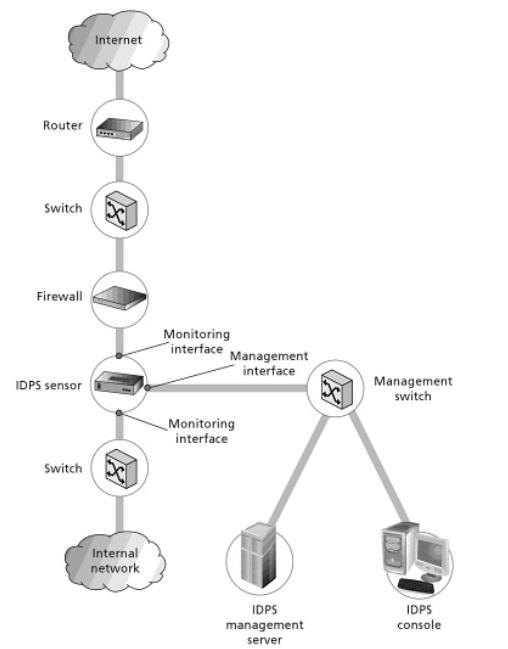
There are three main IDPS placement options that an organization can utilise. Whitman and Mattord declare that the placement of sensors or software programs has a significant effect on how the IDPS operates (188). The First is the network-based IDPS, which monitors and analyses the packets in a particular segment of the network to identify incidents. The analysis looks for indications of current or successful attacks on a segment of the organization’s network (Whitman and Mattord 189).
This type of IDPs will have a number of sensors for monitoring the network and management servers. The sensors accept all the packets coming to the network and proceed to analyse it. The network-based IDPSs are able to detect intrusions and maintain logs of all events. After detection, the IDPSs take action to stop the attack. The preventive actions might involve ending the TCP session, dropping the suspicious activity, or altering malicious content (Scarfone and Mell 46). Network-based IDPSs are often deployed just before the firewall that connects the network to the internet.
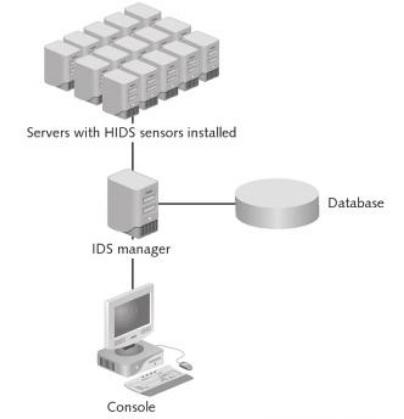
The second technology is the host-based IDPS, which examines the activities taking place in an individual host in order to detect any unusual processes. A major component of these systems is the monitoring software application that is installed on the monitored machine. The software applications are known as agents, and they are able to engage in detection and prevention processes. Due to its local positioning, the host-based IDPS might succeed in flagging attacks that the Network-based IDPS missed. The Host-based IDPSs logs information in its own database, which enables the system to have an independent audit trail in case an attacker succeeds in compromising the system logs (Furnell 167).
The agents are able to monitor system configuration databases and issue warnings when suspicious changes to the file attributes occur. Since the host-based IDPSs are deployed on endpoints, they are able to analyse the activity within an encrypted network by observing the unencrypted activity taking place within the individual host. Intrusion prevention can be carried out in a number of ways. The agents analyse code running on the host and can prevent malicious code from executing. The network traffic to and from the host is also analysed to prevent unauthorized data transfers. The agents are also capable of monitoring file systems to prevent inappropriate file access by users or programs.
The final placement is the application based IDPS which is a refined implementation of the host-based IDPS. These systems are deployed on individual hosts and like host-based IDPSs; they consist of agents that engage in intrusion detection and prevention. Application-based IDPSs differ from host-based IDPSs in that they examine an application for abnormal events as opposed to examining a single system for file modification (Whitman and Mattord 202). By monitoring applications, the agents are able to detect anomalous activities such as invalid file executions and unauthorized user access. Since the application-based IDPSs track the interaction between users and applications, they are able to trace specific activity back to individual users. Similar to host-based IDPSs, application-based IDPSs are also able to monitor and analyse encrypted data.
Incident Report Plan
An efficient IDPS is bound to detect an incident at some point in time. When the incident has been detected, it is imperative for the IT team to react appropriately. IR strategies are the pre-defined approaches that an organization uses to address and manage the environment after an incident has occurred. The strategies aim at handling the security breach or attack in a manner that minimizes the damages to the network infrastructure and also limits the costs of recovery.
The IR life cycle is a series of steps that should be followed to ensure that incidents are effectively dealt with. The first step in the lifecycle is preparation, and it entails the creation of an IR mechanism and the installation of minimum security requirements that the organization must achieve to prevent intrusions from occurring. Leighton declares that the organization must keep reviewing and updating the established minimum security baseline in the IT and network infrastructure to keep up with the changing threats (28). The incident response team is identified in the preparation step, and the responsibilities of the team are articulated.
The second stage of the IR life cycle is the Detection and Analysis State, which is the phase where the incident has occurred, and it has been detected. The detection can be made by an IDPS, the end-users or IT department staff members. The incident response team will analyse the incident to see if it needs further action. Using his/her expertise, the skilled responder will be able to flag an incident as a false-positive or as a real threat that requires a response. If it is determined that the event is a legitimate incident, the responder will engage in data collection in accordance with the pre-established organizational policies and procedures (Leighton 29). The data will later be analysed to reveal the exact nature of the incident.
The next step involves containing and eradicating the problem identified in the previous step. Containment is integral to ensure that the threat does not compromise the entire organizational network. In some cases, containment might involve isolating the affected system from the network. Leighton declares that the containment efforts should endeavour to secure the data (30). After containment, full eradication of the cause of the incident should be carried out.
The eradication method will depend on the nature of the threat, and it might require the deletion of malicious software and corrupted data. Once the cause of the incident has been eradicated, the IR team can engage in the recovery phase. The aim of this step is to restore the system to its pre-incident operation mode. Recovery efforts depend on the nature and scale of the attack, and they might involve restoring the system using uninfected backups, rebuilding the entire system, or changing system passwords.
The fourth step is the post-incident activity which involves careful documentation and a thorough review of the incident. The documentation includes the data analysis carried out during the detection stage of the life-cycle. The IR team reflects on the incident and the new threats that the organization is exposed to (Leighton 30). The incident dealt with provides a learning opportunity for the IR team. The lessons learnt from the incident are used to make improvements to the security of the organization.
Upgrades or adjustments to the organization’s infrastructure can be made to ensure that similar incidents do not occur in future. In conclusion, an assessment is made as to whether the preparations made helped in dealing with the incident. If the preparations were inadequate, they should be amended to ensure that they are sufficient in case of a future incident. The life-cycle, therefore, moves back to the preparation phase where changes are made in light of the new knowledge gained from the incident.
Works Cited
Furnell, Steven. Securing Information and Communications Systems: Principles, Technologies, and Applications. NY: Artech House, 2008. Print.
Leighton, Johnson. Computer Incident Response and Forensics Team Management: Conducting a Successful Incident Response. Boston: Newnes, 2013. Print.
Scarfone, Karen and Peter Mell. Guide to Intrusion Detection and Prevention Systems. Montgomery: National Institute of Standards and Technology, 2007. Print.
Whitman, Michael and Herbert Mattord. Principles of Incident Response and Disaster Recovery. NY: Cengage Learning, 2013. Print.