Network Topology Design
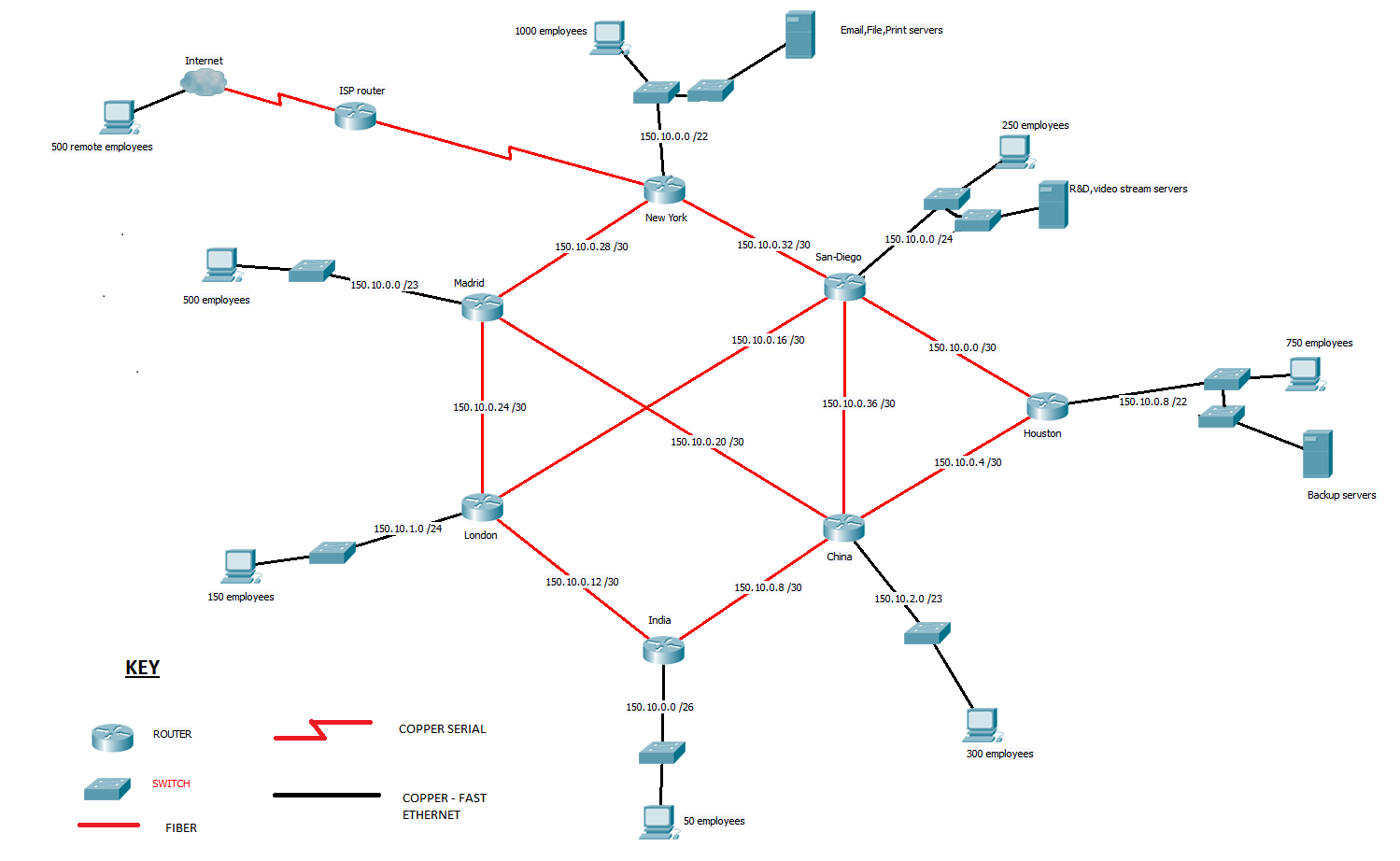
Explanation of the Design Topology
The network design used the allocated company address space of 150.10.0.0 /20 and employed variable length subnetting to distribute the subnets according to the demands by the number of users per given subnet.
The personal computers on the various remote sites represent the various numbers of company employees at these sites who are interconnected using a switched network environment.
This is shown by the switch between the various site routers and personal computers on the designed network topology diagram. Each personal computer is given a default gateway internet protocol of the interface of the site router facing the local site subnet, which is also assigned an internet protocol address that is part of the address space allocated to that subnet.
The remaining network addresses within the distributed subnets are then allocated to the users in those subnets.However, the remaining address space for additional subnets and users reserved for future use.
The addressing scheme that was used in designing the network topology
Link Speeds used in the design of the network
- Fiber links (red links) – 10GBps(gigabytes per second) links
- Copper lines (black links)
- Router to switch on the seven sites – 1 Gbps(gigabytes per second).
- Host PCs and endpoint devices – 100 Mbps(Megabytes per second).
- All servers – 1 Gbps(Gigabytes per second).
Protocols used to fulfill the network design
The WAN (wide area network) network between the seven company locations used the OSPF routing protocol whereby the site routers were all in area 1.
The WAN routers exchanged link state advertisments and maintained a state table of all the remote networks thus making them capable to sufficiently route packets to remote destinations on the company Wide Area Network.
On the individual site servers, the following protocols were used to access the data
New York
- Email – email was accessed by simple mail transfer protocol on port 25.
- File transfer – file transfer was accessed by file transfer protocol and ports 20 and 21 were used.
- Intranet web – intranet web was accessed using hyper text transfer protocol (https) and port 443 was used.
Houston TX
All backups to this server were carried out using file transfer protocol and ports 20 and 21 were used.
San Diego
For the video servers on this site, the protocol used to acces them is the Real time streaming protocol on port 554.
Wide Area Network
The wide area network employed a partial mesh layout to increase on redundancy but also enable savings on the cost of installation as well. It was made up of seven routers intercoonected using fiber 10 Gbps links.The seven site routers are interconnected using leased lines.
Remote Acess Networks
Remote access to the marketing employees was achieved by the use of a remote access VPN (virtual private network) that terminated at the New York router from the internet.
The Remote access employees used a thin client on their personal computer model wherby they were to access the company website from any remote PC connected to the internet, download a java applet that would then act as a tunnel for the VPN and after they input their login credentails get access to the companies resources.
Authentication
Before being admitted to the network or allowed to access network resources, users are authenticated against an authentication server that resides within the New York subnet.
Before the users from the VPN are authenticated, the router at the New York site prompts for the login credentials after they have downloaded the java applet and secured a secure tunnel for usage. Once the user inputs the login credentials, the router passes them by the use of RADIUS ( remote authentication dial in user service) to the authentication server which then sends an access granted or denied back to the router to thus either grant or deny access to company network rsources or not.
Security
Security for the network was employed using the following mechanisms;
Access Control lists
Access control lists were implemented on the router facing the internet at the New York head quarters that denied any access to system resources for connections initiated from outside not unless via the VPN which had user authentication controls enabled. This prevented unwanted access to company resources by unauthenticated users thus providing a layer of security.
Access control lists are also used for router interfaces conecting to the servers at different sites. This allows only users with authorisation to access information being restricted.
Authorisation and auditing
Session authorisation and auditing is enabled for all authenicated seeesions.
Authorisation limits a user’s access to the company resources by their privilege levels that is, remote sales representative might not have access to the companies payroll database although they have access to the company network system and resources.
Auditing enables the generation of logs a for all user sessions. This allows for proper monitoring of users activities and management.
Login delays, login timeouts
The networks authentication system employed login delay systems for successive logins and login timeouts if unsuccessful logins were entered sequentially. This prevented DoS attacks on the network.
Virtual Private Network
The use of a VPN for remote access secures the data in transit as it is encrypted and provides a secure channel of remote access of data without being prone to malicious attacks such as hacking.
Fault Tolerance
The network design has a good fault tolerance as its WAN employs a partial mesh and all WAN routers exchange routing advertisments. Incase of a link or router failure, the rest of the network can continue with operation as data packets can very easily be re-routed across the failed link.