Introduction
Businesses must invest in solid solutions to fulfill growing demands for secure and dependable networking infrastructure. The planned network and a solution for a cyber security infrastructure for the Exeter outpost of the Plymouth Hotel are discussed in this study. The report summarizes the client’s initial needs and includes additional suggestions for improvement. The layout of the report includes an introduction, methods, results, and discussion.
The network architecture describes the network’s design and configuration, including IP addressing and subnetting, whereas the system architecture describes the proposed system’s hardware and software components. Measures taken to protect the privacy, integrity, and accessibility of the network are outlined in detail in the section devoted to the security architecture of the system. Ultimately, we will recap the solution and its advantages to Plymouth Hotel. Guaranteeing the safety and efficacy of the client’s network infrastructure is the overarching goal of this study.
System Architecture
Overview of the Core Infrastructure
The networking and cybersecurity system architecture of Plymouth Hotel is based on many pillars: The network topology for the Plymouth Hotel’s South West locations consists of several LANs linked together and a WAN connecting all of the LANs to the main server farm (Enoch et al., 2021). Hardware components for the network Routers, switches, firewalls, and access points make up the Plymouth Hotel’s system architecture. When keeping the network safe from hackers and other malicious actors, firewalls and routers are the best bet. Users’ wireless connections are established via the access points.
Software for the network infrastructure at the Plymouth Hotel includes the hotel’s central operating system, network protocols, and security programs. Regarding networking, operating systems manage the hardware, whereas network protocols allow devices to talk to one another (Enoch et al., 2021). The antivirus program is installed to safeguard the computer system against malicious software, viruses, and intruders. A data center is the nerve center of any large-scale information system, and the data center for the Plymouth Hotel is where all the servers, storage devices, and applications are housed. All the information gathered from the hotel’s daily activities is processed and stored in the data center. Figure 1 below shows the client-server system of the proposed system of Plymouth Hotel.
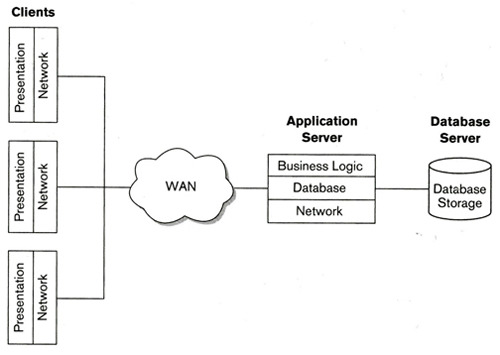
The Plymouth Hotel uses several security measures across its system architecture. They include network segmentation; access control; encryption; intrusion detection and prevention systems; and security monitoring (Bondarenko et al., 2021). These safeguards will prevent unauthorized access to sensitive information and keep systems running smoothly. The identical system architecture would be implemented for the Exeter location, with new network hardware and software to facilitate the branch’s operations. The network’s topology would be modified to accommodate the new branch, and suitable safeguards would be implemented to protect the branch’s data and network.
A High-Level View of the Solution
The Plymouth Hotel has decided to open a second location in Exeter. As a result, it is presently accepting proposals for designing the networking and cybersecurity infrastructure needed to support the new site (Enoch et al., 2021). By being an impartial consulting organization, we must propose a service to meet the hotel’s requirements (Bondarenko et al., 2021). The new activities at the branch include using a management system that allows front desk staff to see and handle guest bookings. A management system lets the manager see and manage information about the team, web browsing by staff and guests, and web applications allowing guests to schedule room service online. Figure 1 below shows the networking and cybersecurity architecture of the institution.
Our proposed solution centers on a network layout that guarantees visitors, workers, and managers separate data flow. Herein lies the framework for the proposed solution. According to Chen and Yang (2021), partitioning network traffic into their respective categories is crucial for adequate security and management (Zedgenizov et al., 2020). Without it, it will be impossible to reach such objectives. Additionally, the system will integrate a cybersecurity design to guard against common threats like malware, viruses, and unauthorized access.
The proposed Technology would help accomplish these objectives by being highly available, scalable, and simple to manage. To this end, we propose using virtualization tools like VMware or Hyper-V to spin up computers in the cloud that are both easy to manage and scalable to meet the hotel’s evolving needs (Zhou et al., 2019). One of the most crucial needs for the suggested solution is to provide a secure, reliable, and expandable infrastructure that aids in running the hotel’s business (Zedgenizov et al., 2020). The hotel’s infrastructure must support the front desk and employee management systems, enable staff and guests to access the internet, and provide online applications that guests can utilize to request room service.
Aims to Achieve the Proposed Solution
To meet these criteria, the proposed solution will include several necessary parts. The hotel’s core infrastructure, consisting of servers, switches, routers, firewalls, and access points of various types will be designed and built with the hotel’s unique needs in mind (Zedgenizov et al., 2020). The servers are responsible for hosting the hotel’s administrative systems, such as the front desk and employee management systems, and the online apps guests use to make room service reservations (Zhou et al., 2019). To ensure these systems’ dependability and responsiveness, their corresponding servers will need sufficient processing power to handle the loads imposed by these applications (Dexter & Epstein, 2021).
The network’s switches and routers will facilitate communication between nodes. Controllers will guarantee connectivity between servers, access points, and other network devices, while routers will establish connections to the Internet and any other external networks. Figure 3 below is designed to show the system interface of the proposed system architecture.
A firewall will be installed to control network access and block malicious users. This action will be taken to ensure the security of the network. The hotel’s Firewall will be set up to automatically reject any traffic that does not adhere to the security requirements (Heryanto & Salma Azizah, 2019). It will be regularly updated to ensure it can identify and block any new dangers as soon as they appear. To guarantee that guests always have a reliable internet connection, we will set up different access points from those we use for our staff members (Prastowo & Indriastuti, 2023). This ensures that guests’ data is isolated from the hotel’s private network and that they cannot access it.
Moreover, it is possible to create a scalable solution by planning for the hotel’s expected growth. This will call for scalable infrastructure elements (such as network switches, routers, and access points) that can be added as the hotel’s needs develop (Kim et al., 2021). To provide the required level of security and control over network traffic, divide it across guest, staff, and administration networks (Bondarenko et al., 2021). An abundance of service availability ensures that essential business operations are always available to employees and customers. Able to expand to meet the needs of an increasing number of guests at the hotel.
Simplified administration reduces the time and money needed to keep the infrastructure running well. To enable traffic between visitor networks, employee networks, and administration networks, the proposed system will make use of virtual local area networks (VLANs) and access control lists (ACLs) to manage access and traffic flow (Gentile et al., 2021). In addition to a separate wired network used just for administrative tasks, the web will be designed to provide dedicated Wi-Fi access points for guests and employees (Bondarenko et al., 2021). With this method, we can ensure that guests cannot access the hotel’s private network while at the same time ensuring that staff members have secure access to the internet and the hotel’s private network.
Consistently high service availability, the system will include redundant components such as switches, firewalls, and servers. Moreover, the secondary power supply can be installed to keep life-support systems running even if the primary power grid goes down (Bondarenko et al., 2021). The proposed system will use scalable, modular components to accommodate future growth as the hotel’s needs evolve (Moreno-Vozmediano et al., 2019). The scalability of the solution will be guaranteed in this way. The hotel can expand its user base, service offerings, and geographical footprint with this strategy without significantly increasing its budget. Not only that, but it will aid the hotel financially as well.
The proposed method relies on centralized management tools such as network management software and security information and event management (SIEM) systems. They were used to simplify management, reducing the complexity and cost of administering the infrastructure (Moreno-Vozmediano et al., 2019). Due to these innovations, the hotel’s IT department will be able to manage the entire infrastructure of the network and the security system from one convenient location.
The report proposes the following design principles to guarantee a practical and visually acceptable outcome. The proposed answer for the Plymouth Hotel’s relocation to Exeter features an extensive, business-specific network and cyber security infrastructure (Gandotra et al., 2020). The mainstays of the infrastructure are the computers and wireless networks used by staff members, guests, the hotel’s website, and the various payment mechanisms. The company plans to increase the number of visitors it can host in the next two years, so it needs a network architecture to grow with the business (Gandotra et al., 2020). The solution aims to provide a trustworthy link for hotel staff, guests, and hotel systems while keeping performance and availability high.
Network Architecture
Wired and wireless networks form part of the network’s backbone, allowing staff, guests, and hotel systems to communicate. According to Sujatmiko et al. (2020), Subnetting is used in the proposed network design to provide for logical traffic isolation and efficient IP address utilization (Gentile et al., 2021). The network’s architecture is hierarchical, with the access layer at the top, followed by the distribution layer, and finally, the core layer. Distribution layers are in charge of traffic aggregation from access switches and VLAN routing, whereas access layers connect end devices to the network (Fata & Kusuma, 2018). The core layer ensures that all network communication is fast and reliable. It accomplishes this by facilitating rapid communication between various distribution switches, as shown in figure 4 below.
Subnetting scheme divides the network into four distinct groups: management, sales, visitors, and staff. The sales team uses the subnet 33.3.3.16/27, which provides 32 IP addresses, whereas the administration team relies on subnet 33.3.3.0/28, which provides just 16 (Gentile et al., 2021). The guest network utilizes the 64 IP addresses on the 33.3.3.48/26 subnet. The Exeter location can use any 256 IP addresses available on the network with the network address of 33.3.3.0/24. The Wi-Fi network for staff members uses the 32 IP addresses available on the subnet 33.3.3.128/27 (Moreno-Vozmediano et al., 2019). The hotel uses sixteen IP addresses in the subnet 33.3.3.192/28 for its website and payment processing services.
Virtual local area networks (VLANs) are used in the network design to provide a logical partition of data traffic between distinct groups of users and types of equipment. Many kinds of virtual local area networks (VLANs) have been proposed, including those for administration, sales, guests, employees, management, and servers (Gentile et al., 2021). Several types of users can be separated using virtual local area networks (VLANs), such as administrative, sales, guest, and employee VLANs (Gentile et al., 2021). Instead, the administration of VLAN is what gets used to handling all the networked gadgets. The hotel operates a server virtual local area network (VLAN) to allow guests and staff to connect the hotel’s many server-based systems, including the hotel management system, employee information system, and room service application.
The switches in the network are designed to function at both Layer 2 and Layer 3 of the OSI model, allowing for inter-VLAN communication and routing. While access switches provide connectivity to end devices on a Layer 2 basis, distribution switches perform routing and VLAN aggregation at a higher Layer 3 (Peng et al., 2019). Due to the invention of high-speed core switches, distribution switches can quickly and efficiently communicate with one another. The network architecture uses redundant links and devices whenever possible to ensure high availability and fault tolerance (Fang et al., 2019). The proposed architecture requires the Spanning Tree Protocol (STP) and Rapid Spanning Tree Protocol (RSTP) to ensure that redundant links are used efficiently and loops are avoided.
Security Architecture
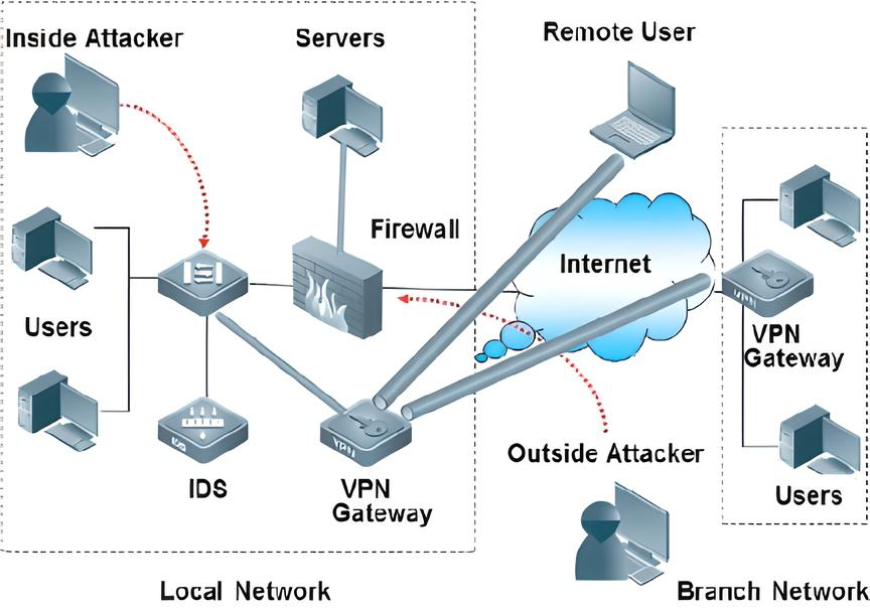
Cybersecurity infrastructure comprises various security controls and technology. These safeguards and technology are in place to counteract the many forms that cyber-attacks might take (Khlaponin et al., 2022). The proposed cyber security architecture includes firewalls, IDPS, VPNs, and security policies and procedures. The proposed firewall architecture employs a perimeter firewall to shield the hotel’s internal network from the internet and the outside world. The Firewall has been configured to allow only authorized communications and block potential threats (Joshi, 2016). The Firewall uses stateful inspection and deep packet inspection to inspect application layer traffic and defend against threats like buffer overflow and SQL injection.
The proposed IDPS architecture makes use of both host-based and network-based intrusion detection and prevention techniques. Mazhar et al. (2022) argue that the network-based IDPS monitors suspicious network behavior, such as abnormal traffic patterns, and reports any findings to the proper security personnel (Peng et al., 2019). Servers and desktop computers are only two examples of equipment that the host-based intrusion detection and prevention system (IDPS) checks for signs of malicious activity or penetration.
The hotel staff and authorized outsiders can utilize the virtual private network (VPN) built into the design of the proposed VPN to securely access the hotel’s internal network from a remote location. A VPN can prevent snooping and modification of transmitted data by employing standard encryption protocols like SSL and IPsec (Martynenkov, 2021). Several measures are being considered to ensure the hotel’s systems and data remain accessible, private, and unaltered in case of a breach in the security policies and processes under consideration (Peng et al., 2019). Some things addressed in the policies and procedures are data encryption, backup and recovery, user authentication, access control, and incident response. Figure 5 below represents the system architectural diagram for Plymouth Hotel in Exeter.
The proposed system design for the Plymouth Hotel’s Exeter outpost provides a complete network and cyber security infrastructure in line with the needs and aspirations of the business, as shown in figure 3 above. The architecture includes numerous security mechanisms and technologies to defend against cyber-attacks and threats, as well as a network design that is scalable and adaptive to accommodate future growth (Peng et al., 2019). The suggested architecture ensures excellent performance and availability, giving guests, staff, and hotel systems reliable and secure online connectivity. The architecture also includes redundant network and device components to increase availability and fault tolerance. The suggested system architecture provides a solid basis for the Plymouth Hotel’s operations in Exeter.
Conclusion
In conclusion, the new Plymouth Hotel in Exeter, the proposed networking and cybersecurity infrastructure solution, comprises a network configuration separating data flow for guests, employees, and management. This is a piece of the puzzle for the new building in Exeter. The solution also includes security measures to prevent hacking, malicious software, and other cyber threats. The proposed approach is widely accessible, extensible, and easy to manage. It uses virtualization software to quickly create cloud-based computers that are both scalable and easy to manage. To run smoothly, the hotel relies on specialized hardware, including servers, switches, routers, firewalls, and access points.
The system uses VLANs and ACLs to control access and traffic flow, and it includes redundant parts to guarantee continuous service. The system also uses centralized management tools to simplify administration, cutting overhead costs and improving efficiency. When the hotel’s demands change, the proposed solution may grow with them thanks to its scalability and modular design. Considering the hotel’s anticipated expansion, it allowed to implement the changes.
Plymouth Hotel’s network and security infrastructure are built on a complex foundation of hardware, software, a data center, and other protective measures. Several local area networks (LANs) are linked, and a vast area network (WAN) links all offices to the main server room. The hardware comprises routers, switches, firewalls, and access points, while the software comprises operating systems, network protocols, and security software. The hotel’s data network infrastructure is housed and processed at one central location. Network partitioning, authentication, encryption, intrusion detection and prevention tools, and constant surveillance are all part of the cybersecurity arsenal. The identical system architecture would be adopted for the Exeter branch, with the necessary modifications to enable the branch’s activities and keep the network and data safe.
References
Bondarenko, S., Tkachuk, H., Klochan, I., Mokhnenko, A., Liganenko, I., & Martynenko, V. (2021). Modeling of economic security of the enterprise at change of investment maintenance. Studies of Applied Economics, 39(7). Web.
Chen, W., & Yang, F. (2021). Person re-identification based on partition adaptive network structure and channel partition weight adaptive. IEEE Access, 9, 101402–101413. Web.
Dexter, F., & Epstein, R. H. (2021). Simply adjusting for schedulers’ bias in estimated case durations can accomplish the same objectives of improving predictions as use of Machine learning. JAMA Surgery. Web.
Enoch, S. Y., Lee, J. S., & Kim, D. S. (2021). Novel security models, metrics, and security assessment for maritime vessel networks. Computer Networks, 189, 107934. Web.
Fang, C., Wang, M., Han, P., Cao, Y. Q., Wu, D., & Li, A. D. (2019). High-Performance MIM capacitors Using Zr-Sn-Ti-O dielectrics derived from atomic layer deposition. IEEE electron device letters, 40(5), 682-685. Web.
Gandotra, N., & Sharma, L. S. (2020). Exploring the use of Iptables as an application layer firewall. Journal of The Institution of Engineers (India): Series B, 101, 707-715. Web.
Gentile, A. F., Fazio, P., & Miceli, G. (2021). A Survey on the implementation and management of secure virtual private networks (VPNs) and virtual LANs (VLANs) in static and mobile scenarios. Telecom, 2(4), 430–445. Web.
Heryanto, D., & Salma Azizah. (2019). Application of access control list for network security at cisco router as a firewall. OISAA Journal of Indonesia Emas, 2(2), 71–76. Web.
Khlaponin, Y., Kozubtsova, L., Kozubtsov, I., & Shtonda, R. (2022). Functions of the information security and cybersecurity system of critical information infrastructure. Cybersecurity: Education, Science, Technique, 3(15), 124–134. Web.
Kim, J., McGuire, S., Savoy, S., & Wilson, R. (2021). Expected economic growth and investment in corporate tax planning. Review of Accounting Studies. Web.
Leung, R., & Loo, P. T. (2022). Co-creating interactive dining experiences via interconnected and interoperable smart technology. Asian Journal of Technology Innovation, 30(1), 45-67. Web.
Martinekuan (2023) Security Architecture Design – Azure Architecture Center | Microsoft Learn. Web.
Martynenkov, I. V. (2021). The main stages of development of the cryptographic protocols ssl/tls and ipsec. Prikladnaya Diskretnaya Matematika, 51, 31–67. Web.
Mazhar, N., Saleh, R., Zaba, R., Zeeshan, M., Muzaffar Hameed, M., & Khan, N. (2022). R-IDPS: real-time sdn-based idps system for IOT security. Computers, Materials & Continua, 73(2), 3099–3118. Web.
Moreno-Vozmediano, R., Montero, R. S., Huedo, E., & Llorente, I. M. (2019). Efficient resource provisioning for elastic cloud services based on machine learning techniques. Journal of Cloud Computing, 8(1), 1-18. Web.
Muhammad Asif Qureshi et al. “Influence of front-desk staff service quality on students’ affective commitment, trust, and word-of-mouth in higher education.” Asian Academy of Management Journal, 2022. Web.
Peng, T., Liu, Q., Wang, G., Xiang, Y., & Chen, S. (2019). Multidimensional privacy preservation in location-based services. Future Generation Computer Systems, 93, 312-326. Web.
Prastowo, I., & Indriastuti, W. A. (2023). Systems as an effort to guarantee the safety and security of guests study of hotel building fire protection. Astonjadro, 12(1), 117. Web.
Sujatmiko, B., Rozaq, F., & Wibawa, S. (2020). Project-based learning as a subnetting material completion in network design studies. Journal of Physics: Conference Series, 1569. Web.
Zedgenizov, A., Seliangin, K., & Efremenko, I. (2020). Methodology for assessing required area for allocating centers of mass attraction in layout of urbanized territories and their impact on quality of traffic management in adjacent street and road network. Transportation Research Procedia, 50, 743-748. Web.
Zhou, Z., Chen, X., Wu, W., Wu, D., & Zhang, J. (2019). Predictive online server provisioning for cost-efficient iot data streaming across collaborative edges. In Proceedings of the Twentieth ACM International Symposium on Mobile Ad Hoc Networking and Computing (pp. 321-330). Web.