Introduction
The applicability of game theory in making decisions is an interesting aspect to observe. Game theory can be defined as a set of actions by particular decision makers, who are aware that their actions affect each other. Thus, for every case in which there are more than one decision maker –player, and more than a single direction for action involved, there is a game that can be formed from such case. Thus, it can be stated that game theory can be applied to more than one context. Despite being associated mostly with economics, game theory is not restricted to such discipline. Nevertheless, financial aspects are always found in most decision making processes. One case that can be investigated using game theory can be seen through the issue of piracy in video gaming world. The most recent top story in such context is that Playstation 3 – a video game console manufactured by Sony was jailbroken. A jailbreak is a hardware and/or software modification process that allows running unauthorized software on a particular device. In that regard, the present paper will attempt to describe the current story along with the preceding events as a game situation. Additionally, the solution to such situation will be provided and compared with the way it turned out in reality.
Game Description
A certain background might be required to explain the context of the current situation, regarding piracy and Sony Playstation 3 (PS3). Initially at the time of the release, PS3 had the ability to install any other operating system (OS) on the device. It is alleged that such option contributed to that PS3 could not be jailbroken for a record period of time, as opposed to other video gaming devices, as it gave hackers the opportunity to install their programs without the need to break the security of the system (Digital Foundry; Fahey). Once Sony discovered that the option of installing other OS might make their system vulnerable, it had two strategies to choose, either such option or to keep it. The payoffs of both strategies are not completely known for Sony at the time, as it did not know how it will turn out. The information at the time of making the decision was known to both parties, and thus, making the game of perfect information.
The second participant of the game can be seen through hackers’ community. They also had several decisions to make, which according to their statement in 27th Chaos Communication Conference (27c3) was largely based on the actions of Sony (Digital Foundry). Thus, their strategies can be divided between choosing to break the security of the system or not, i.e., cooperate with the manufacturer or not. The payoff for the hackers’ community can be seen in terms of satisfaction for the hackers’ community and avoiding losses for Sony. The best option, in that matter is ten, no losses incurred by Sony, and total satisfaction by the hackers’ community. The measurement can be estimated through the statement made, where the number five might mean moderate satisfaction, assuming that hackers will not be obliged to jailbreak a system that was already open, and moderate losses for Sony, as it will have the opportunity to patch the security for future games. The payoffs in this game are assumed, based on the common knowledge and rationality. Considering the Sony was the last platform that was not jailbroken by hackers, the worst pay off is that their games can be copied freely through the internet, incurring huge losses to the company. The worst payoff for the hackers’ community is the possibility for litigation, which might mean that in an ideal case they will have to stop their activities for the time of such litigation.
Representation
The game can be described as a sequential and with perfect information. The extensive representation of the game can be seen through the following graph. Considering that there are opportunities for both parties to gain in this game, such game can be described as a non-zero sum game.
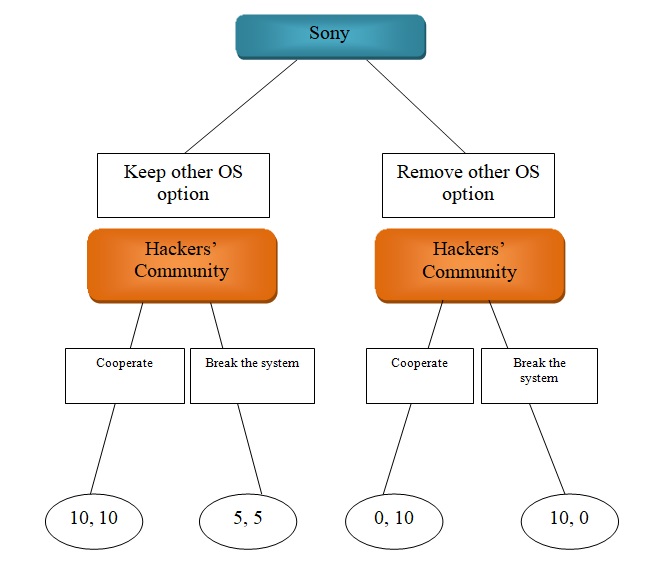
In normal form, the game can be represented as follows:
The Solution
In order to solve the game which is of sequential order and perfect information subgame perfect Nash equilibrium (SPNE) method might be used. Such method is dependent on the characteristic of the game consisting of subgames, i.e. “a subset of branches and decisions in a game tree” (Rasmusen 256). The solution of such game can be seen through backward induction, where the determination of the path begins at the last node, and then moves backward. For the game described, the payoff for hacker community is chosen at the last node, where the outcomes providing maximum payoffs are chosen. Such nodes are the far left and far left nodes, each of which constitutes a ten; the rest of the nodes are ignored. Next, the payoff for the first player – Sony, is determined between the two path chosen previously, which in this case is either to remove the other OS option or to keep it. The option providing maximum payoff to Sony is to keep the other OS option. Thus, the selected path represents the equilibrium in this case. An illustration of backward induction can be seen through the following graph.
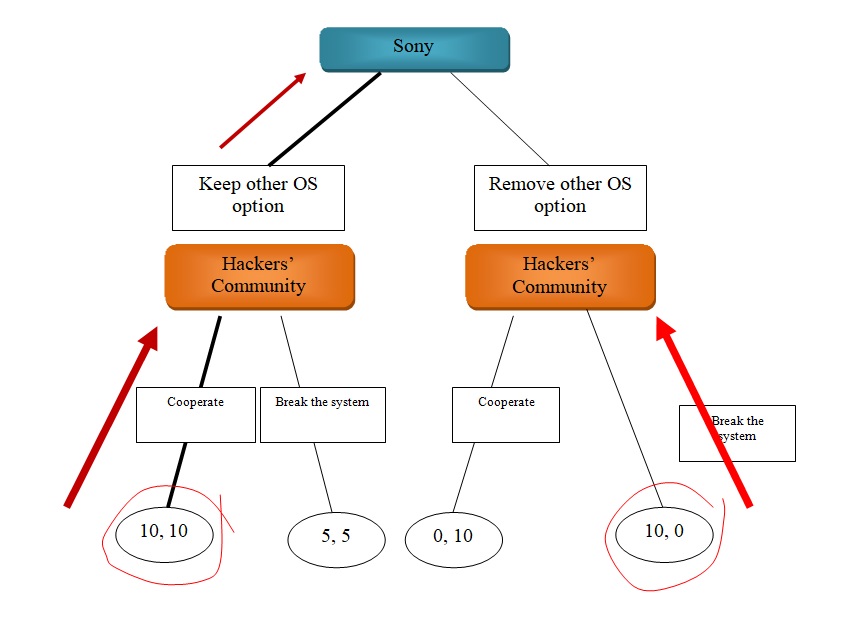
Conclusion
In reality, Sony chose the other option, to remove the other OS feature, which turned to provide the least payoff. Such fact can be explained through making the wrong assumptions regarding the knowledge each player has about the other. In that regard, Sony sought to maximize its profit, but it turned out that the assumptions of rationality was wrong. Nevertheless, it should be stated that there were a certain indication for the company that removing the other OS option would no maximize its profits, when many customers complaint for the removal of an advertised option, and accordingly, as series of law suits were filed against the company (Conley). Thus, at this stage Sony should have been aware that choosing such strategy would not be clear in terms of payoff. Accordingly, once such option was removed, hackers made their determination to restore it (Kuchera). It can be concluded, that in the presented game, one of the players failed to determine the outcome of the strategies employed, which led to an outcome with the least payoff.
Works Cited
Conley, Ray. “Sony Seeks to Dismiss “Other Os” Lawsuit”. 2010. PlaystationLifestyle.net. Web.
Digital Foundry. “Hackers Leave Ps3 Security in Tatters”. 2011. Eurogamer. Web.
Fahey, Rob. “Deep Insecurity”. 2011. Eurogamer. Web.
Kuchera, Ben. “Hacker Vows to Fight Sony Ps3 Update, Restore Linux Support”. 2010. Ars Technica. Web.
Rasmusen, Eric. Games and Information : An Introduction to Game Theory. 4th ed. Malden, MA ; Oxford: Blackwell Pub., 2007. Print.