Introduction
One of the most epic accomplishments of the 21st century was the invention of the computer and the subsequent creation of computer networks. The interconnection capability of computer systems is arguably the feature that makes them most versatile and invaluable to their users.
With this realization, many manufacturers in the early days of computing set out to develop devices that could be used in internetworking. At the onset, various manufacturers designed network architectures that were specific to their devices leading to a lack of interoperability between devices by different manufacturers (Wetteroth 4). This was very inefficient and as such, there arose a need to come up with a common standard which would guarantee the seamless interconnection of various heterogeneous architectures.
The International Standards Organization (ISO) was therefore formed as a body charged with developing and publishing international standards. This body came up with the Open Systems Interconnection referencing model (OSI). This paper shall set out to explain the components of the OSI reference model as well as the need for adopting the standard.
Importance of the Open Systems Interconnection Referencing Model
The OSI reference model was produced in 1974 by the ISO encourages the creation of network equipment that is non-proprietary in nature by the various vendors in the field (Wetteroth 4). This model consists of seven layers with a description of the services that each layer must provide to the layer above it. An important point to note is that the OSI model is not a specific network architecture but rather a description of what each layer must do.
As such, manufacturers are required to use this as a guideline when coming up with their own specific network architecture. Any device that conforms to the OSI standard is guaranteed to be able to communicate with another device that meets the same standards and functionality of devices is also Operating System independent. This results in great interoperability of the various network devices. In coming up with the various layers of the OSI, various principles were considered.
Most notably, it was seen as necessary for each layer to have well defined functions; these functions had to be chosen in a standardized manner and the boundary between them was such as to minimize data flow through the interfaces. As a result of this, the model allows for the investigation of various network errors which would otherwise be very hard to find without the existence of layering as outlined in OSI.
The seven layers of the OSI model
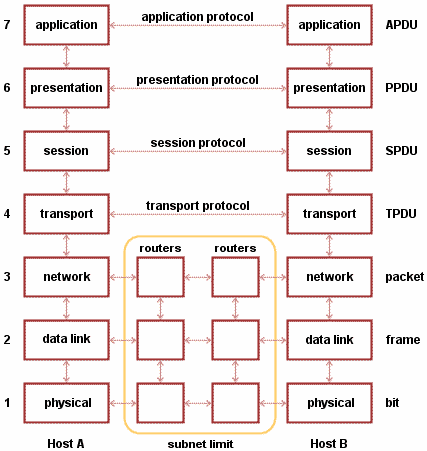
Layer 7: The Application Layer
This layer is the interface between the user and the network. The application layer “controls how the operating system and its applications interact with the network” (Hallberg 32). The functions of this layer include providing application programs with access to the network, control of data flowing through and the recovery from any error that might occur.
At the application layer, the data been sent is encapsulated with an application header and the application data which constitutes the data being sent through the network. The protocols that exist at this layer include Telnet, FTP, SMTP and HTTP. The data transmission process begins with this level receiving data from the user application.
Layer 6: The Presentation Layer
This layer provides certain functionality which result in readability of data for the application layer. This is done through a number of coding and conversion functions which result in information that can be read across systems. The layer “transforms the data from the session layer to provide a standard interface for the application layer and from the application layer to a network format” (Lowe 397).
The presentation layer in essence takes the data from the lower levels and puts them into a format that an be understood by the system. Hallberg reveals that some of the functions that take place at the layer include: compression and decompression as well as data encryption and decryption (31). In addition to this, this is the layer responsible for setting standards for different systems.
Layer 5: The Session Layer
This layer controls the various sessions between communicating devices by establishing, maintaining, and when communication is over, terminating the connection between the communicating devices. This layer performs negotiations between the communicating devices on issues such as flow control and user identification and authentication on the network (Hallberg 30).
The Session layer also delegates who is to send or receive data at a given time and goes on to stipulate as to how long this will take place. The session layer allows for graceful closure and provides synchronization services.
Layer 4: The Transport Layer
The transport layer provides data transfer between communicating users by managing flow of information from one node to the other. This transfer is transparent in nature thereby the higher level layers need not concern themselves with the specifics. This layer also manages the flow of data and divides the streams of data into packets which are reassembled at the other end. At this layer, data is segmented and a TCP header placed at the end of each segment.
This header includes control information such as start and end flags so as to enable the recipient to establish the size of the message (Lowe 397). Sequence information is also provided so that even if data is transmitted non-sequentially, it can be reassembled back to the original form in the right order. This layer ensures that the all the data packets sent are received and that they are decoded in the proper sequence. The two major protocols which function at this layer are TCP and UDP.
Layer 3: The Network Layer
This layer provides the functional means of transferring data sequences of varied lengths from source to destination (Lowe 397). The packets of data obtained from the session layer are segmented into frames and their logical addressing is done. This layer covers the issue of addressing and routing. At the network level, an IP header is added. This makes the segments packets. The header information at this layer includes the IP address of the source and the destination.
This is necessary for the logical-physical address mapping routers use this information to forward data to the required destination. This is done by translation of the IP address and MAC addresses. The network layer relies on the routing information provided to send individual packets to the correct destination and to notify the recipient of the source from which the packet originated.
Layer 2: The data-link layer
This layer turns the frames provided by the network layer into raw bits of zeros (0) and ones (1) in readiness for transmission at the physical layer and reconstitutes them to frames at the other end.
The data link layer encapsulates a header which contains LLC information identifying network layer protocols, Frame check sequence for error checking and the MAC address of the source and the destination. As such, at the data link layer a frame contains a header which has the IP address, MAC address and various control information (Lowe 398).
This information is necessary for hubs and switches to enable them tell where to forward information. The Data Link Layer ensures that there is an error-free communication between the two communicating nodes and as such, if any error is detected, the layer requests for a retransmission of data from the transmitting node. The error detection mechanism method employed by this layer is the Frame Check Sequence.
Layer 1: The physical layer
The physical layer is responsible for the “transmission of the streams of bits through a physical media” (Wetteroth 3). This may be through a sequence of electrical impulses or through light variations. Wetteroth states that the Physical Layer specifies the attributes of the physical medium that will be used for network communication (3).
As such, definition of how the physical cable is attached to the Network interface Card is provided at this layer. In addition to this, the layer is also responsible for monitoring data error rates. Hubs, repeaters, network adapters perform on this level.
Memorizing the Seven Layers
To enable me memorize the seven layers, I have come up with a simple mnemonic which is fairly easy for me to remember: “Please Do Not Take Salty Pork Always”.
The first letter to every word in my formulae represents a level in the OSI reference model starting from Layer 1 all the way to Layer 7.
Conclusion This paper set out to perform a concise yet informative research on the OSI (Open System Interconnect) standard model that was created by the International Standards Organization. The paper began by reaffirming the need for standardization in the computer network industry.
From the discussions provided, it has been seen that without standardization, the industry would have been full of devices that cannot interoperate which would greatly limit the choice for consumers since they would be forced to buy all devices from one vendor so as to avoid running the risk of devices not working together. From this paper, it is also clear that the OSI reference model plays a crucial role in ensuring interoperability among various networking devices.
Works Cited
Hallberg, Bruce. Networking, A Beginner’s Guide, Fifth Edition. McGraw Hill Professional, 2009. Print.
Lowe, Doug. Networking For Dummies. For Dummies, 2007. Print.
The Manual Page. The different layers of the OSI model. 2009. Web.
Wetteroth, Debbra. OSI Reference Model for Telecommunications. USA: McGraw-Hill Professional Publishing, 2001. Print.