Introduction
History of Cyber Crime
The virtual environment of the global network has been inundated with cybercriminals (Yar, 2013). According to Lewis University, the phenomenon of a cybercrime dates back to 1971, when the web was first invaded by the virus notoriously known as Creeper.
It was very simple by the present-day standards, yet it managed to cause havoc across the Internet (Ruiz, Winter, & Park, 2015). Unfortunately, viruses and other tools used by cybercriminals are getting smarter and increasingly more sophisticated; causing global concerns regarding personal information and business data. A similar situation can be observed in the UAE (Enzer, 2011), which was identified by the Assocham-Mahindra SSG study as one of the countries that cybercriminals attacked India from (Sethi, 2015).
Cyber Crime in the United Arab Emirates
The recent introduction of updates to the UAE Cybercrime Law 2016 will impose a set of more augmented penalties on the offenders, including a life sentence. However; the specified regulation does not have tangible effects on cybercriminals as it does not allow for the willing acceptance of proper behavioral patterns and the recognition of cybercrime as an intrinsically negative phenomenon. Therefore; the development of programs aimed at changing the target audience’s concept of cybercrime is crucial.
Cyber Crime in Dubai
It is viewed positively that the current legislation reinforces the significance of the letter of the law. For instance, “Dubai Police have urged victims of online social networking sites to approach authorities because their hesitation encourages suspects to target more victims” (Al-Najami, 2010). However, the lack of information regarding the concept of cybercrime, the ways of inhibiting it and the tools that the UAE society can use to prevent cybercrimes are not completely obvious. Thus; the number of cybercrimes has been increasing in the UAE generally, and in Dubai particularly as shown in Figure 1 (Hasbini, 2014).
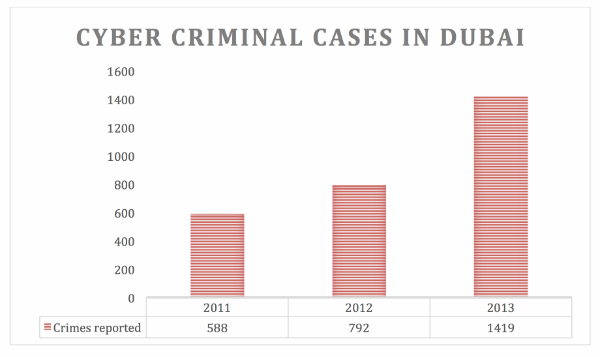
Therefore, the focus should be shifted from providing penalties to reinforcing knowledge promotion among ICT users. Also, awareness programs should be created to educate people on cybercrimes. Thus; significant progress can be expected. Accordingly, the UAE government saw the necessity and urgency to review the cybercrime law of 2012 and amend it to protect the society, economy, and environment more effectively.
Policy Understanding, Formulation and Development
The Federal Law No (2) of 2006 on the Prevention of Information Technology Crimes
This law is meant to regulate the telecommunication sector and to deter the occurrence of cybercrimes. Article two through to four deals with the violation of the information technology rules and regulations as well as the penalties that come with such acts or omissions.
An imprisonment term not exceeding one year and penalty of not more than AED 20,000 will be imposed on offenders for crimes like unlawful access to a website leading to violation of privacy, erasure, deletion, damaging, disclosure, alteration, destruction or replication of information (Cross & Shinder, 2008).
Moreover, temporary detention and fine not exceeding AED are to be imposed on the person that uses any information technology device or Internet to disrupt, delete or modify the information or data (article 5). The law further considers the relationship between medical records, diagnoses, treatment, and their distortion through the Internet and sets out the repercussions for such acts (United Nations, 2007).
Other critical issues that are provided for by this law pertains to the use of the Internet for bullying, impersonation through the internet, online banking violations, online prostitution or fornication, abuse of Islamic shrine or ritual, defamation, promotion of wrongdoing, online drug trafficking, money laundering and the use of the internet for terrorism activities. There are further provisions on how this law shall be enforced and the parties responsible for its implementation. This law is particularly important because it sets out clear boundaries to the right and wrong uses of the Internet and other ICT devices.
The Amendment: Federal Decree-Law No. (5) of 2012 on Combating Cybercrimes
This law analyzes different scenarios for cybercrimes and how they may be committed. The law states the relevant punishment for each type of cybercrime under varying conditions under various circumstances(Lunt & Livingstone, 2012). The most prevalent class of these crimes is as enlisted in article 44 of this law are crimes against State security.
These are the crimes listed in articles 4, 24, 26, 28, 29, 30, and 38 of the Decree-law. This law is very important especially in the phase of rapidly emerging crimes that are committed using the Internet and the ICT systems. Thus, the aim is to ensure that the illicit content, which is usually very characteristic of major websites, does not find its way to the public (Holt & Schell, 2011).
The Study for Amendment in 2016
Amendments are seen as the best way of ensuring that laws meet the general needs of the people and the constitution. For instance, amendments in 2016 will seek to iron out some of the lapses that have been making the application of the law to be ineffective. For instance, IP address forgery is a very minor crime and guilty parties can be sentenced to a jail term that ranges from 24 hours to a maximum of years. The amendment will target individuals making fraudulent use of computer network protocol addresses with criminal intent.
Approaches
This law is to help to push the change agenda of the government in redefining the true use of the internet and ICT system and devices (Geers, 2011). The successful implementation of the law can lead to a drastic reduction in the number of related crimes and social vices. Unfortunately, the lack of relevant knowledge by some of the concerned stage agents, which makes them irrelevant to the mission, is the major challenge that is likely to hamper the enforcement of the law. To solve this, the government needs to provide the strongest and most up-to-date training to its officers to tackle cybercrime issues.
Policy Development
According to the eightfold path analysis, the problem is the need to find a solution in curbing cybercrimes and preventing ICT crimes (Cooper, Seiford, & Tone, 2006). The evidence attesting to this scenario is derived from the government criminal statistics records showing the number of cybercrimes and the ICT devices’ crimes.
The two alternatives that have been combined in this law are the imposition of varying fines and imprisonment terms depending on the crime graveness. This law, if taken seriously, could be the most suitable criteria that can be applied to bring about the much-needed regulation of the rampant crimes in the telecommunication sector (Baggili, 2011).
The only shortfall in this law is that it requires constant monitoring of the entire web to detect signs of suspicious activities. This is to say that some crimes might be committed and go unnoticed if there is no surveillance at a particular moment. However, if the government brings all the stakeholders on board, then this should be an easy mission for its objectivity to be achieved.
Impacts of the Policy
Impacts on Society
The cybercrime law and its amendments are aimed at protecting people from becoming victims of their greediness, or that of others. It is planned to reduce the number of online gamblers, as well as of individuals who participate in money laundering. Also, young generations will be made aware of fake trading and false promotions of online cheats. The terrorist groups are expected to lose their cyber-power and cybercrime communication. For example, Twitter canceled 125,000 Isis terrorist accounts under the government’s pressure (Yadron, 2016). Most importantly, personal information and business data will be secured confidentially.
On the whole, the law in the UAE is aimed at promoting the traditional values of the people and enhancing their well-being (“UAE Cybercrime Law,” 2015). At the same time, some laws, such as the laws that penalize actions against the public morals taken online, are considered ambiguous by some scholars due to the vagueness of the definitions provided in them (Aldurra, 2013, pp. 52-53).
However, it is noted that the legal system offers “some guidance on the kinds of behavior that are regarded by society as acceptable” (Aldurra, 2013, p. i), so such laws also help define what people of the UAE should be like. Therefore, making cybercrime a legal offense and enforcing such laws promote disapproving attitudes towards those who commit such crime in society, even though making the people aware of such policies is also essential.
Impacts on the Economy
The implementation of the policy towards cybercrime is aimed at defending both the governmental structures of the UAE and its businesses. The laws which define the concrete types of cybercrime in detail allow for more effective implementation of penalties against cyber offenders.
Therefore, the policy will provide a more thorough protection for the government and enterprises, safeguarding them from hacked accounts and stolen data and money. This will allow for a safer business environment, which will have a positive impact on the UAE’s economy. On the whole, it is stressed that the implementation of the cyber policy in the UAE has the development of “a competitive economy led by creative and knowledgeable Emiratis” as one of its goals (Al-Khouri, 2012, p. 136).
Impacts on the Environment
Technologies, the cyber technologies, in particular, hurt the environment. For instance, for computers and the Internet to work, large amounts of resources such as electricity (which comes down to energy produced in power plants that pollute the environment) are consumed. Committing cybercrime that leads to significant data losses means that the resources used in production and storing this data are wasted and that new resources need to be consumed to restore or replace the data.
Therefore, implementing the policy which protects against cybercrime should have a positive effect on the environment by preventing the waste of natural resources that were used to produce the information defended by this policy. Also, the abuse of the obtained information or access might allow criminals to harm the environment e.g. political reasons, which also needs to be safeguarded against.
Challenges and Issues (Interview)
Implementation
Two main challenges are facing the amended UAE’s cybercrime law. Firstly, with the increasing rates of cybercrimes due to the rapid and complex ICT advancements; tracking all cybercrime criminals is being harder for law enforcers. The majority of organizations are struggling to keep up with the technology and thus have vulnerable areas in their system. Cyberattacks are hard to trace.
Usually, a cyberattack might be noticed when files are destroyed and irreversible damages occurred. Reporting the issue late helps the attacker conceal their steps and make it more misleading to catch them (Emirates 24/7, 2015). The accidental destruction of the evidence by policemen if not handled properly causes security specialists to waste more time trying to catch a few criminals while more attacks are happening instantaneously (ISSA, 2014).
Secondly, international crime is another weak spot in the UAE cybercrime law. Having the internet bypassing virtually all countries’ political borders gives cybercrime criminals and computer scammers the ultimate freedom to attack people outside their countries’ domains. On the other hand, countries find it hard to punish people outside their borders, especially for those from lawless countries.
Dr. Omar Al Ghoul, a chief judge at the Federal courts in Kalba, mentioned this loophole in an article, written by The National, in which he called for stronger cybercrimes law in the UAE. He stated that “Cybercrimes are transnational, and sometimes offenders are outside the state. So maybe countries could extradite them to the UAE. There should be several international agreements to regulate such issues” (Malek, 2014).
Beckstormsaid “How you relate to the world as a country or a company explains how you will be affected by the cyber world around you”. Cybercrime criminals moved further and faster and continued their cybercrimes attacks everywhere. Having the world’s countries take a step to stop block this serious security loophole is what a future cyber-law would look forward to (WAM, 2016).
Case Study
In Egypt, ‘Operation Phish Phry’ resulted in stealing over $1.5 million from different citizens’ banks’ accounts. The cybercrimes criminals have successfully faked a bank website and directed account users to it via a hyperlink through a convincing email message. The victims trusted the well-faked website, through which the hackers stole the users’ information.
Those cybercrime criminals withdrew small amounts from different users; to avoid awakening the bank; to disturb their attention, and to make it more challenging. An American hacker was sentenced to 13-year jail and almost half of the other 47 Egyptians were declared to be innocent and the rest ran away (El-Guindy & Hegazy, 2012).
Computer users can be hacked easily, which mandates that stricter laws are required to protect users from cybercrimes and punish those criminals appropriately. In 2012, a virus attacked, damaged and deleted information from more than 30,000 computers at the Saudi ARAMCO (Elnaim, 2013). This is a weakness in the security systems that any entity or individual is exposed to the risk of cybercrimes attacks.
Best Practices
During the research team interviews, an anonymous government information security and risk management professional who is an expert with Cybercrimes stated that organizations generally and the government entities particularly respond actively and proactively to secure themselves from cyberattacks. They do not wait until cybercrimes laws are issued; otherwise; they might be attacked by cybercriminals.
He stated that stealing passwords is a cyberattack and not a cybercrime; for which frequent awareness sessions were provided; so that public employees know and implement the best practices to secure their cyberspace. Cyberattacks and cybercrimes evolve quicker than cyber laws. However, many government organizations in the UAE support compliance efficiently with cybercrimes laws by organizing campaigns such as Dubai Government Information Security Resolution (DGISR).
He added that using memory sticks or flash memory (USBs) is not a cybercrime rather than a source for successful cyberattacks; however; organizational cybersecurity policies, in compliance with and support to cyber-laws, are issued proactively for higher organizational and national cybersecurity levels. he added that worldwide (alike the US, Europe, Russia, and Ukraine) 25.4-percent chance that government organizations will be cyber-attacked and energy sector has 16.3-percent cyberattacks; so; the government-energy organization has the 41.7-percent probability to be hacked in any environment; for which the success rate will depend on the type of the cyberattacks.
He advised that Cyberattacks are moving aggressively to the MENA region and organizations should respond proactively to them as Symantec reported. He stated that 2012 and 2014 reported the most cybercrimes. He explained that organizations do not talk about their exposure to cyberattacks; so; no one will know about them; until the media reports them as happened with Bank of Sharjah that has been recently cyberattacked.
Conclusions
Summary
To sum up, it should be noted that, even though cybercrime has a history of more than four decades, it has become an increased threat over the last years. Cybercriminals may pose a significant threat to the personal safety of individuals, normal functioning of companies and governmental structures, and even to the national safety.
To safeguard against such offenses, a cybercrime policy is being implemented in the UAE. This policy is aimed at augmenting punishments for cybercrime. The policy should benefit the society, the economy of the state, and the natural environment. At the same time, it has been noted that some definitions provided in the new legislation are vague (Aldurra, 2013) and that people are often unaware of the laws regarding cybersecurity, so these issues also need to be addressed.
Policy Recommendations
- Raise awareness of the current legislation regarding cyber technologies in society.
- Because the technologies used in cybercrime evolve rapidly, organize ongoing research of the issue to provide better protection.
- Constantly monitor and improve the legislation regarding cybercrime for the laws not to lag significantly from cyber offenders.
References
Al-Khouri, A. M. (2012). eGovernment strategies: The case of the United Arab Emirates (UAE). European Journal of ePractice, 17, 126-150. Web.
Aldurra, F. A. (2013). Cybercrime and penal code: A comparative study between United Arab Emirates and Japan. Web.
UAE cybercrime law: Dh500k fine, jail. (2015). Web.
Yadron, D. (2016). Twitter deletes 125,000 Isis accounts and expands anti-terror teams. Web.