Abstract
The purpose of this project is to provide fast effective means of secure telecommunications to protect government interests from parties that intend harm to national security. The scope of this project is limited to personnel and equipment involved in Government Special Programs and Security as required by our agency and not to include gear provided by outside agencies.
Introduction
Information without exaggeration can be considered as one of the determinant resources of development. In the modern world, information actively influences all spheres of vital functions of not only separate states, but also the global community. However, in certain cases the information can be used not only for a good cause, but also to the detriment of the interests of the individual, the society and the government. Therefore the role of information safety within the system of national security not only essentially increases, but also leads to priorities. Accordingly, the protection of communication channels occupies a special place in the main structure of a complex system of information protection.
Communication channels are among the most vulnerable components of Informational systems, where in their structure it is possible to specify a large number of potentially dangerous threats, through which malefactors can access the informational system. Modern technologies and methods of protection of telephone conversations from interception counteract practically all the means of its realization. Nevertheless, in the matter of government interests, the security priority in communications can be influential in making decisions of changing the platforms of communication and upgrading the existing communication principles. In that regard, new technical decisions would allow solving the issues of communicative security in a more complex approach without sacrificing such aspects as flexibility, price, speed and development and implementation of new functions.
This report aims to propose replacement of the existent governmental standards in securing communications, STU-III and STE with a sufficiently new and effective approach to communication, i.e. Voice over Internet Protocol. The report provides the general overview of the existing technologies and their drawbacks giving recommendations on how to overcome the obstacles in developing effective and secure communication platforms.
Background
As of 2008, the US government secure communications are based on Secure Terminal Equipment (STE), which replaced the Secure Telephone Unit – Third Generation (STU- III). STE are capable to operate in PSTN, Tri-TAC, or direct connections to Radio Frequency (RF), although are mostly used through Integrated Services Digital Network (ISDN). (NSA, 2007)The current implementation of secure communications using STE and STU III considers the specifications listed in table1.
Following security as the main factor, the technical characteristics of STU III and even STE comprise of a lot of shortcomings that do not comply with modern communications features. Such shortcomings are apparent through the following outlines:
- Specific equipment and vendor requirements.
- Slow connectivity rates, where comparing to the mass implementation of broad band connection, ISDN’s maximum of 128kbs does not satisfy communication demands. These demands include, but not limited to voice clarity, caller id, video transmission, and etc.
- The requirements for additional efforts and investments to secure the calls.
- High price.
Following the progress of secure communications, it can be seen that the choice is limited. Although the encryption of STU-III and STE is solid, the reliance on outdated characteristics prevents the security government communication sector to be updated accordingly. STU-III, for example is still relying on public switched telephone network (PSTN) the drawbacks of which can be summarized as following:
- Developed specifically for voice transmission, the data traffic is following voice data.
- The inability of fast development and implementation of new capabilities. The PSTN network is based on infrastructure the owners of which independently develop application for the hardware. The monopolization prevents satisfying all clients’ needs.
- The impossibility to merge data, voice and video networks within the PSTN. Although broad band access seems to solve this issue with bandwidth merging different networks require a whole restructure of the PSTN for the change to occur at end users’ terminal.(Davidson, 2007)
Thus, it is recommended to use IP networks for establishing secure communications. This implementation is commonly called Voice over Internet Protocol, better known as VOIP. The recommendation is specified to using encrypted networks for making calls. Addressing the disadvantages of STU-III and STE, VOIP characteristics consider the following:
- Minimal maintenance, none on the user
- Implementing such features as Caller id for all parties in the special programs database
- High connection rates, and accordingly higher voice clarity
- Phone’s slim design saves space
- Cheaper required equipments which lead to less long term costs
- Operational rate is much faster than the STU III’s and STE’s
- Reducing call bills costs
Proposed solution
Overview
The proposed solution implies the usage of a technology commonly known as VOIP. According to how and where the connection is formed, there are several directions that could be distinguished, such as Internet Protocol telephony (IP telephony), internet telephony, and LAN telephony, and often DSL telephony. The technical implementation in all the cases is identical and has the designation of VOIP.
In VOIP the main aspect is not as much using the internet as a medium for speech transfer, as it is using the IP protocol and supporting technologies to provide reliable and high-performance transferring voice data in packet networks. Originally, VOIP was implemented as a voice data transfer between software installed on two personal computers. Today the application of VOIP is mostly concerned with functioning within a private network and the application of VOIP over public networks. The technology of transferring voice data on networks with IP routing is attractive, first of all, because of its universality – speech can be transformed to a stream of IP-packages in any point of the network infrastructure: in operators’ backbone network , on the borders of territorially distributed network, in a corporate network and even in end user terminal. Eventually, it will become the most widespread technology of package telephony, as it is capable of capturing all market segments, being thus well adapted for new conditions of deployment.(Witowsky, 1998)
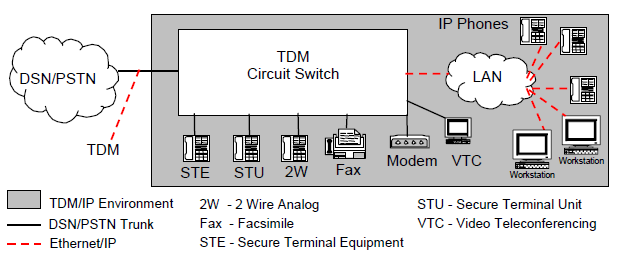
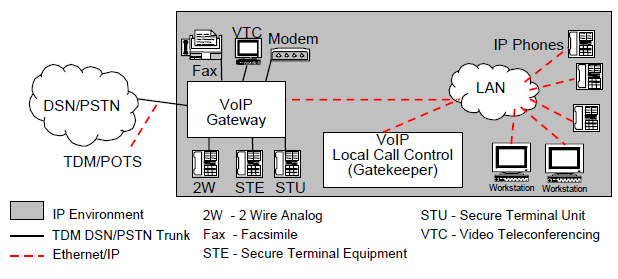
In the reliance over IP networks VoIP can be categorized into two approaches, i.e. IP centric and IP enabled. The IP enabled architecture can be considered as combined solution where VoIP terminals are provided to the end user while the core processing and switching is based on Time-division multiplexing (TDM) circuit switch, see fig 1. IP centric, on the other hand, TDM functions are performed solely by an IP based core switching system. Connectivity to TDM, PSTN, and others is implemented through dedicated channels, see fig 2. (DISA, 2006)
Potential Areas of Concern
VoIP Technology as a transfer of voice data using IP protocol is not only a prospective technology, but also a reality. More often the companies use it as a cheap way to communicate with remote departments. Conferences using these protocols are being used more often. Specific figures of market coverage differ for analysts, but converge in one – VoIP grows at tremendous rates and becoming a more significant service. In particular, according IDC, it is estimated for “residential VoIP customers to be anywhere between 12 million to 44 million in the US by 2010.”(“VoIP by the Numbers – Subscribers, Revenues, Top Service Providers, Blogs and more…”, 2006).
As the area of concern should be directed toward security, in order to understand potential threats it is necessary to distinguish accurately VoIP’s two main components: Voice – a vocal component, important from the point of view of the end user (quality of a and clarity of voice data, delays, and etc), and IP – a network component. That is the basic difference between VoIP technology and the traditional telephone system which is separated from the remaining infrastructure. Certainly, the connection of external modems etc is limited. However, it is seldom that regular checks of the configuration of a telephone exchange are conducted. Besides, security management poorly interferes with traditional telephone system work. In a case of a traditional IP-network there are some areas of concerns.
When building the infrastructure of VoIP, a set of devices is added to the existing network topology: gateways, proxies, registrators, locators, and the actual IP-telephones, where to each of these elements irrespective of, whether it is a specialized device with software built-in or usual computer with general OS and any additional software, it is possible to access this device on the network as a usual computer.
Each VoIP element has its own processor, software, TCP/IP stack which can be attacked. Attacks can be organized on the device as well as on the transmission. Attacks such as Denial of Service (DoS) are capable of overloading the network with false voice packages, reducing the productivity or even preventing the transfer of voice and data.
The attacked gateway can be used for the organization of unauthorized calls. In case of process vulnerability establishing a connection, the call can be intercepted, and sent to different address. Vocal packages can be intercepted and all communication session is restored and heard in real time. Software telephones organized on computers by corresponding software can be attacked where it is possible to install Trojan programs that will allow the attacker not only to make unauthorized calls, but also to develop an attack on VoIP infrastructure. In general VoIP threats can be summarized in table 2.
Solution
The proposed VoIP solution, considering the security concerns, can be divided into several approaches that can be summarized as follows:
Encryption
Encryption is an approach similar to the one implemented in STE and STU-III. There are numerous encryption options that can deal with securing the voice data in VoIP, such as TACLANE Encryption(Tanase, 2004), VPN setups, IPSec protocol, and Secure RTP protocol. Encrypting the voice data is also known as Secure Voice over IP (SVoIP). The key factor for the protocol is fast, as the speed and efficiency advantage of VoIP can be eliminated by the encryption reducing bandwidth. Such a solution can be characterized by the necessity of using compatible encryption algorithms among all terminals.
All inclusive platforms
All inclusive platforms are commercial products for integrating and migrating to VoIP such as HDX and SLICE 2100 proposed by REDCOM. (REDCOM, 2009) These platforms facilitate the process of installing VoIP solutions additionally providing security over the communication lines. The disadvantages of such solutions can be seen in their cost, as switching the entire network can be consuming, although the installation and setting of the system can be easier in the process of migration.
Voice over Secure Internet Protocol (VoSIP)
This solution is based on securing each element of a VoIP network. The recommendations for building secure VoIP network can be by securing the transport device within the IP centric VoIP network. This includes the physical security of components such as routers, switches, gateways and servers. Additional security measures include standard safety procedures within the network such as applying the latest security patches, updates and the software and hardware firewalls. (McCarthy, 2007)
Implementation
Installing VoIP can be determined via selecting appropriate network architecture, or in case adjusting existing networks to fulfill VoIP demands. Building the network from scratch implies the necessity of equipment which is not limited to the proposed below.
Equipment
One Closed Partition
A partition forces mandatory access control. An open partition refers to systems that not have a specifically enforced access control. Closed means that mandatory access controls are enforced. Only specified accounts can download data from that partition. Source will provide a closed partition at a predetermined level.
Computer and Peripherals
The computer providing VOIP will be used to access email, create office documents, and load data from CD or DVD to the network. These are the minimum computer requirements:
- Processor, monitor, anti-virus software, Microsoft Windows XP Professional, and Microsoft Office Professional, and a printer.
- Multiprocessor distributed processing
- Optional redundant control per shelf
- Computer Telephony Integration (CTI)
- Uninterruptible Power Supply
- Cabling
- Media Converters/Transceivers
- Power cables
- VOIP Capable Phones
System Capacity
- 4,000 ports (non-blocking)
- 16,000 ports (traffic engineered)
- Up to 512 ports per shelf
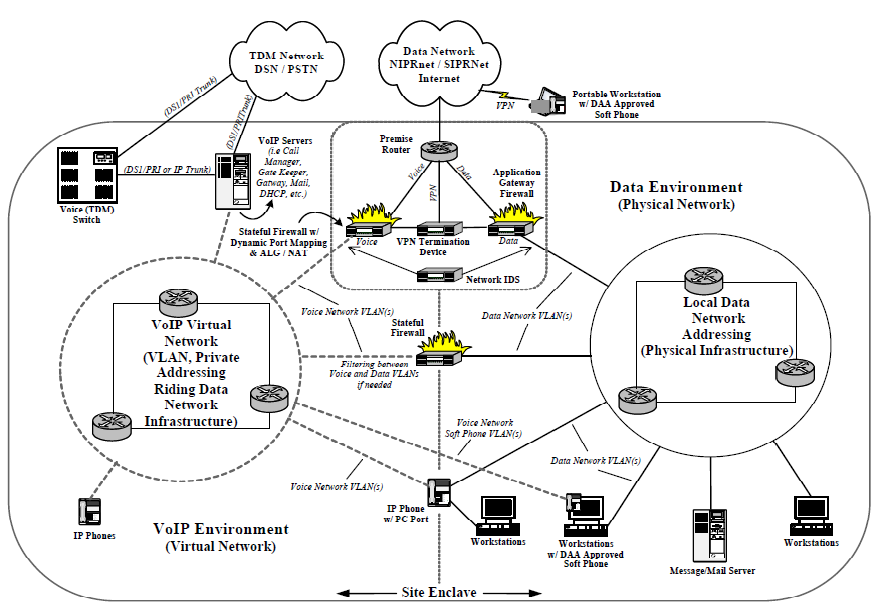
The recommended security implementation is a hybrid of the VoSIP and SVoIP which is Secure Voice over Secure Internet Protocol (SVoSIP).The aforementioned implementation is the most suitable as it would raise the security level to that satisfies the governmental needs. The network layout can be seen through the architecture implemented in the Department of Defense implementation guide which can be considered within the highest levels of security level, see fig. 3. (DISA, 2006)In such a way, it can be seen that the recommended installation of VoIP technology would satisfy the government’s special needs in terms of security.
List of Illustrations
Table 1(NSA, 2007).
Table 2(Porter, et al., 2006).
IP enabled VoIP architecture
IP centric VoIP architecture
VoIP Security Architecture
References
Davidson, J. (2007). Voice over IP fundamentals (2nd ed.). Indianapolis, Ind.: Cisco Press.
DISA (2006). INTERNET PROTOCOL TELEPHONY & VOICE OVER INTERNET PROTOCOL: SECURITY TECHNICAL IMPLEMENTATION GUIDE. Web.
Encryption Solutions from GD – TESSCO.com. (2008). In TESSCO Technologies – Your total source provider of products for the wireless industry. Web.
McCarthy, S. P. (2007). Voice over IP Security: Issues and Answers. Web.
NSA (2007). Secure Telephone Unit Third Generation (STU-III)/ Secure Terminal Equipment (STE). Web.
Porter, T., Kanclirz, J., Zmolek, A., Rosela, A., Cross, M., Chaffin, L., et al. (2006). Practical VoIP Security. Rockland, MA: Syngress.
REDCOM Laboratories. (2009). Web.
Tanase, M. (2004). Voice over IP Security. Web.
Thermos, P., & Takanen, A. (2008). Securing VoIP networks : threats, vulnerabilities, and countermeasures. Upper Saddle River, NJ: Addison-Wesley.
VoIP by the Numbers – Subscribers, Revenues, Top Service Providers, Blogs and more… (2006). Web.
Witowsky, W. E. (1998). IP Telephone Design and Implementation Issues.
Yip, W. Secure Telephone Unit, Third Generation (STU-III) and Secure Terminal Equipment (STE). Web.