Introduction
There are more and more digital usage applications emerging as new technologies are developed. Data, processing capabilities and memory requirements have increased as a consequence of the digital revolution of systems and software from devices to operating systems to programs. Meeting such needs is made possible through virtualization, which allows a single device to behave as several machines/settings. Virtualization has grown in popularity over the years and is now pervasive across the current information technology sector, owing to the multiple advantages to businesses and individual consumers. Nowadays, virtualization is a common technique in business information technology architectures. Additionally, it is the innovation that underlies the competitiveness of cloud computing. Thus, virtualization may be advantageous to proprietors of data centers and service companies.
Fundamentally, virtualization improves the adaptability, effectiveness, and scalability of computer systems and applications by allowing for the coexistence of many software-based ecosystems on one hardware. Each virtual machine is a stand-alone edition running on a simulated device independent of the underlying computer hardware (Balen et al., 2020). Virtualization tools control simulated hardware, which has fewer capabilities than actual hardware. The operating system (OS) has a significant impact on the performance of a virtual machine. A virtual machine’s efficiency on multiple operating systems must be evaluated to identify the most practical ones that can give the greatest usage of resources and maximize hardware performance.
Virtualization
Virtualization is a basis or technique for dividing up the infrastructure of computer equipment into several applications running through the use of one or many principles or technologies. This includes software and hardware separation, time-sharing, selective or total machine modeling, and simulation (Kulkarni et al., 2012). Virtualization creates a digital computer system by simulating actual hardware with software. Programs, hosts, storage, and networks can all be virtualized. The primary advantages of virtualization are that it may improve computer agility, flexibility, and scalability whilst considerably lowering costs (Balen et al., 2020). Tasks are delivered more quickly, output improves, and processes are automated, leading to a computer system that is less expensive to buy and maintain and much easier to control. In general, there are other advantages, which comprise:
- Cost reductions in capital and operational expenses,
- Reducing disruption,
- Boosting output, efficiency, and adaptability,
- Quick reconfiguring and rollout of servers,
- Facilitating incident response and enterprise sustainability.
Many virtual machines may be installed on a particular computer system, allowing for the simultaneous operation of a host machine’s parallel applications and operating systems. Typically, a thin overlay of software, known as a virtual machine manager (VMM) or hypervisor, sits between the host and the virtual machine (Kulkarni et al., 2012). This technology enables several operating systems to use the same host computer. The VMM manages resources and memory usage to keep virtual machines from interfering and communicating with higher-level management and tracking applications.
Windows 8.1 versus Windows 10
The most popular PC operating systems are Windows and Linux. Windows 8.1 keeps enhancing operating system efficiency and speed by introducing unique features and improving current ones. Additionally, it makes use of reconfigurable component architecture, in which each OS part is described as a distinct and separate module or unit that provides hardware autonomy (Balen et al., 2020). Further, it has a robust support design that incorporates built-in self-diagnosis and debugging. The major significant enhancements are faster startup and shutdown speeds due to the use of hybrid boot technology, an upgraded Unified Extensible Firmware Interface (UEFI) with increased security and CPU safeguard, USB 3.0 and DirectX 11.2 compatibility, and USB 3.0 and DirectX 11.2 functionality (Balen et al., 2020). Indeed, these are not the only improvements in Windows 8.1.
Others include the freshly designed Windows Imaging (WIM) configuration, which significantly decreases the size of picture files, and the new Hyper-V machine virtualization capability, which allows several 32-bit or 64-bit OS to run concurrently on a single IT (Balen et al., 2020). Likewise, device defect and computer disk malfunction identification are automated, as are efficiency concerns such as sluggish program launch, sluggish boot, sluggish standby/resume, sluggish shutoff, memory leaks, and faltering memory. MinWin, the latest Windows mini-kernel, lowers the Windows core to its bare essentials by removing all interconnections (Balen et al., 2020). Accordingly, Windows 8.1 a more polished OS compared to its predecessors.
Windows 10 adds dozens of new features to distribution, maintenance, administration, and networking, although protection is the main focus. Moreover, the new development strategy brings a new strategy to building, deploying, and servicing Windows with a “Windows as a service” method that will release incremental functionality upgrades twice a year rather than major feature changes every several years (Balen et al., 2020). Notable deployment enhancements comprise a self-service deployment tool for Windows 10 systems, Windows AutoPilot, Windows 10 Automated Redeployment, and a redesigned Hyper-V virtual machine gallery with fully automated intervals (Balen et al., 2020). Servicing is enhanced with the addition of revamped user satisfaction options for deployment efficiency and new rules in Windows updates for business. Control features comprise enhanced kiosk setup and administration capabilities (multi-app situations, easier lockdown settings), the capability to control Windows 10 systems concurrently using setup manager, Intune, and more (Balen et al., 2020). Always On VPN technology is an innovative networking function that allows distant desktops and gadgets to remain linked to the corporation’s network.
Without a doubt, the organization will gain immensely if it upgrades its corporate Operating Systems from Windows 8.1 to Windows 10, mainly due to its advanced security and malware protection features. The most critical security capabilities are shown in the table below:
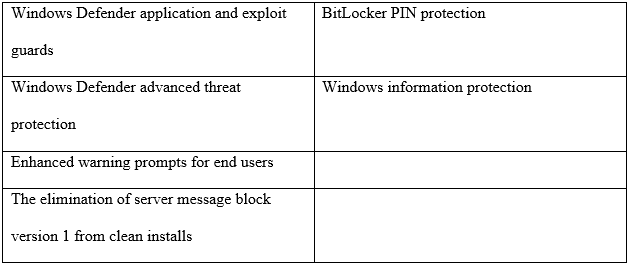
Note. Windows 10 comes with Windows Security, containing the most up-to-date malware safeguards. The computer(s) will be proactively secured from the minute the company launches Windows. Windows Security checks for viruses, malware, and security risks regularly. Apart from real-time security, updates are likewise fetched automatically to protect devices from vulnerabilities.
Many of the features above are missing in Windows 8.1. Thus, with Windows 10, it is not only the business and its people who will benefit from enhanced productivity tools. Moreover, the firm’s IT Support employees will gain exposure to a modern package of technologies that will increase their efficiency and provide enhanced security. Windows 10 has security capabilities that significantly improve the safety of computer systems while users surf the internet, read emails, share files across devices, and execute routine activities. Users will experience fewer security breaches as an outcome of these unique updates, which will result in reduced outages. If a virus or ransomware compromises a computer, the company’s IT Support has recourse to revamped and enhanced rebuilding and deployment capabilities to quickly patch the device or push out a custom Windows image tailored to the business’s requirements.
Deadlock
A deadlock may arise in practically any circumstance involving the sharing of resources by processes. It may develop in any computer setting, although it is most prevalent in decentralized systems, in which numerous functions share the same assets (Payal & Taneja, 2015). In this case, one operation may be queuing for an asset that has been allocated to another function. Consider K1, K 2, and K as three operations and L1, L 2, and L 3 as three assets. In this scenario, assume that P1 asks for L 2, which K2 owns. As a result, K1 will be unable to continue without L 2 and will wait endlessly for L 3, which P3 reserves since K2 cannot surrender L2 until it receives L3. A similar scenario may be drawn for K1 and k3. Hence, it perfectly illustrates a deadlock problem in an operating system. A deadlock may occur if the below four criteria are met concurrently:
Condition 1: Mutual exclusion – Users cannot share a resource among many processes in this state (Payal & Taneja, 2015). For instance, this operation is impossible if two persons want to photocopy a page concurrently. One must wait till the system makes the photocopier (resource) available. Accordingly, users may allocate a resource to a single operation at a time.
Condition 2: Resource holding or the hold and wait – At least one resource is being maintained, and another is delayed concurrently (Payal & Taneja, 2015). In this case, the operation has not yet begun; hence the system is in a condition of inactivity.
Condition 3: No preemption – It is impossible to forcibly remove a resource from a function holding it unless the operation leaves the resource first (Payal & Taneja, 2015). This assertion is equally true while the operation is waiting.
Condition 4: The circular wait – Assume that procedure K1 is awaiting a resource L2. Thus, that specific resource L2 is presently in possession of an operation K2. Function K2 is awaiting the resource, which is being held by the following operation. This will persist until the final process asks for the resource that the first function is holding. The circular wait situation initiates a continuous loop and places all operations in a delayed state (Payal & Taneja, 2015). The OS will stop a deadlock from happening during the deadlock avoidance phase by evading any of the circumstances mentioned above that created it.
If the operating system can evade one of the criteria listed, a deadlock cannot arise. Strategies for avoiding deadlock enable the operating system to prevent the incidence of deadlock. The OS will keep track of the highest resources necessary for a function throughout its life span before initiating operation. Prior to assigning any freshly demanded resources to any operation, the OS will verify the current condition of the system (Payal & Taneja, 2015). The OS will seek to prevent a circular wait state to escape a deadlock. The OS is said to be in a “safe state” if it can distribute all required inputs to the operation without generating a deadlock in the long term. An unsafe state is achieved when the operating system is unable to distribute all of the required inputs without creating a deadlock in the foreseeable.
The Linux Network-Attached Storage (NAS) Advantage
Each NAS file database has an integrated OS that allows for the plug-and-play network connection characteristic of a NAS framework. Although some companies have created their customized operating systems, they are mainly found exclusively in higher-end corporate NAS equipment (Vista Storage Corporation, 2022). The most popular operating systems for mid-range NAS systems are Linux and Microsoft Windows Storage Server. While Microsoft Windows remains the dominant server and desktop operating system for small and medium-sized businesses, using a Linux-based NAS filer has distinct advantages over Microsoft Storage Server.
RAID Capability That Is Less Difficult and Less Costly
All NAS systems rely on Redundant Array of Inexpensive Disks (RAID) functionality to ensure continuous operation in a disk failure. Linux includes a RAID capability that is both flexible and dependable. On the other hand, RAID capabilities were added to the Microsoft operating system only recently. Since RAID implementation is less mature, all current NAS systems running Microsoft OS use a second RAID controller to offload mission-critical RAID operations (Vista Storage Corporation, 2022). The requirement for an additional board in Microsoft-based NAS products adds complexity and cost to the system, which can be avoided entirely in a Linux-based system.
Support for a Wide Range of Users
The Linux operating system supports network protocols such as FTP, NFS, and CIFS. This feature allows a Linux-based NAS system to share file access with Unix (NFS) and Windows clients (CIFS). RAID shares on a Linux system can be created completely independently and then enabled for the required protocol (Vista Storage Corporation, 2022). Microsoft-based NAS systems are typically designed to support Windows clients and do not support file sharing with Unix clients. Even if customers are primarily interested in Microsoft, a Linux-based NAS solution allows for future Linux installations in a way that a Microsoft OS environment does not (Vista Storage Corporation, 2022). Given the significant inroads that Linux technology is making in many organizations, this is an important consideration.
Support for Optimized File Systems
When using Microsoft OS in a NAS filer, the system is limited to the native NTFS file system. While NTFS is suitable for small server and desktop applications, it has file volume restrictions that can render a NAS system inoperable. The Linux operating system supports specially optimized file systems such as XFS. This file system was designed to support large file sets in the tens of millions, which is essential for a file-sharing product (Vista Storage Corporation, 2022). Moreover, because XFS is a journaled file system, it is more resilient and recovers faster than NTFS.
NAS with Improved Features
Linux is an open standard, so NAS vendors can easily customize it to provide advanced performance and management features tailored to network file serving. Since customization is complicated to develop and support in a Microsoft environment, most vendors are limited by the operating system’s feature set (Vista Storage Corporation, 2022). As a result of this restriction, customers may find it difficult to distinguish between different Microsoft OS-based NAS solutions, limiting the range of product functionality.
POSIX Standards Are Supported
Many open system standards, such as POSIX, are supported by the Linux operating system (Portable Operating System Interface). The POSIX standard, for example, provides an industry-accepted interface for managing ACLs (Access Control Lists) on various file systems (Vista Storage Corporation, 2022). ACLs are a vital file security capability because they control the access rights assigned to files stored on the NAS system. Due to the POSIX standard, Linux-based NAS systems can provide entire administration for Unix ACLs as well as the most common Microsoft OS ACLs (read and write for users and groups) (read and write for users and groups) (Vista Storage Corporation, 2022). This level of ACL support flexibility is not possible with the Microsoft OS.
Outstanding Diagnosis
Unlike the Microsoft operating system, the Linux operating system can be loaded into the flash memory of the onboard NAS processor. While this may appear esoteric, it is critical when troubleshooting system errors. Because the operating system can be loaded into flash, the NAS system can still be accessed if serious hardware problems arise (Vista Storage Corporation, 2022). As a result, diagnostics are improved, problem resolution is faster, and system uptime is increased. Savings on Software. Unlike Microsoft’s operating system, the Linux operating system’s runtime licenses are free. Lowering the cost of software licensing reduces the overall cost of the system.
Summary
It is critical for businesses looking to buy a new NAS filer to understand which operating system is built into the products they are considering. Some IT administrators believe that they must use a Microsoft operating system-based solution if they run a Windows environment. This is not always a reasonable assumption to make. Aside from obvious cost advantages, the open architecture of the Linux operating system provides a level of flexibility that no dedicated Microsoft product can match. Linux-based NAS solutions are frequently the best choice for existing and future network file sharing needs due to features such as native RAID functionality, heterogeneous client support, optimized file systems, and superior diagnostics.
References
Balen, J., Vdovjak, K., & Martinović, G. (2020). Performance evaluation of windows virtual machines on a Linux host.Automatika, 61(3), 425-435. Web.
Kulkarni, O., Bagul, S., Gawali, D., & Swamy, P. (2012). Virtualization technology: A leading edge. International Journal of Computer Application, 2(2), 272-287. Web.
Payal, S., & Taneja, R. (2015). Deadlock: A problem of computer system. International Journal, 5(8). Web.
Vista Storage Corporation. (2022). The Advantage of Linux-Based NAS Over Windows-Based NAS. (2022). Premisesnetworks.com. Web.