Summary
Wireshark is the network packet analyzer in this project, is a tool used to capture packet data in as much detail as possible. It introduces the aspects of network troubleshooting, security engineering, verification of network applications, debug protocol implementations, and learning network protocol internals. The compatibility of the Wireshark tool to run on Windows and Linux environments and live capture from many different network media has enhanced its use through the project. Other features include many protocol dissectors and import and export files from many other capture programs.
Objectives
The main objective of this project is to familiarize me with network monitoring and analyze the different protocols statistics.
Steps
Download and install Wireshark
Through any searching download of stable version stable release 3.4.9 windows installer 64 bit. The file has a capacity of 68mbs. Locate your download file and begin installation by starting up the wizard and agreeing to the terms and conditions.
Instructions
Startup any search engine, which will display your selected homepage. Startup the Wireshark software, which will initialize a window, and at this stage, Wireshark has not yet begun capturing packets. To begin packet capture, select the capture to pull-down menu and select Interfaces. This will cause the “Wireshark: Capture Interfaces” window to be displayed. While Wireshark is running, a URL of interest is run on the search bar, and that page is displayed in the browser. To display this page, your browser will contact the HTTP (Hypertext Transfer Protocols) server and exchange messages with the server to download the page. The Ethernet frames containing these messages, as well as all other frames passing through your Ethernet adapter, will be captured by Wireshark.
After your search engine has displayed the corresponding HTML page, stop Wireshark packet capture by selecting stop in the Wireshark capture window. Live packet data has now been captured, and it contains all protocol messages exchanged between your computer and other network entities. The HTTP message exchanges with the URL’s web server that you opened on the browser should appear somewhere in the listing of packets captured. But there will be many other types of packets displayed as well. Even though the only action was taken was to download a web page, many other protocols are running on the computer and are unseen by the user.
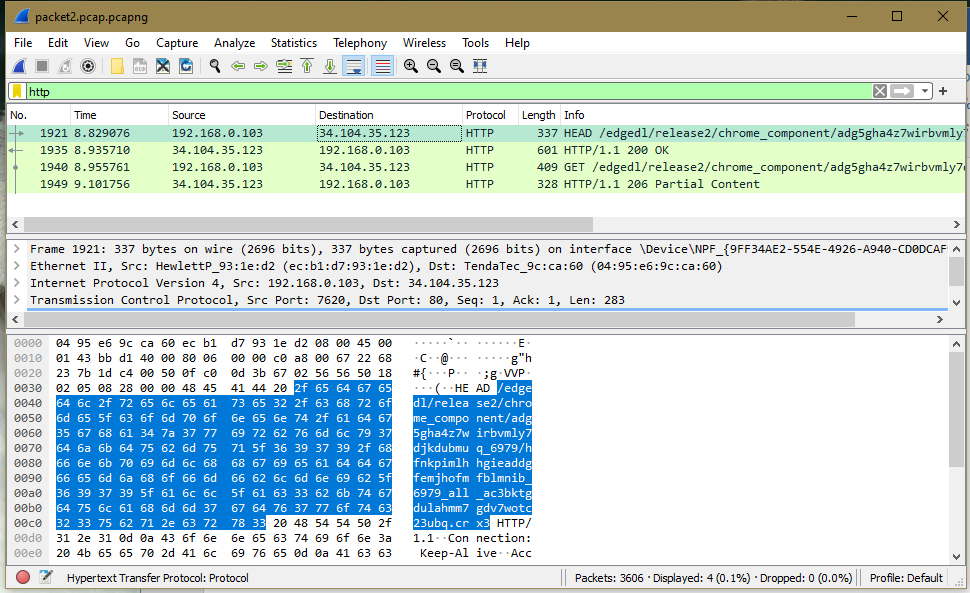
Analysing HTTP Packets
HTTP is an application layer used to enable communication between the HTTP client and the HTTP server. To analyze HTTP packets, we consider the captured traffic in the top Wireshark list pane and select and view details.
What is the number of HTTP packets captured?
The number of HTTP packets captured in the process is four due to the background processes from the browser to authenticate user logins and request protocols to configure the search engine since it is newly installed and synching of data processes.
Write the source and destination IP address of the first HTTP packet.
The source IP address is given by192.168.0.103, and the destination address is 34.104.35.123. From sorting the HTTP packets from all the captured ones, this is done by searching HTTP on the search bar to filter the packets. This enables keeping track of the host by the server and incoming connections to the data streams.
Which frame was the HTTP response received? Frame 1921:
The HTTP packet being the header was received on frame 1921 when the component URL was released. The frame helps indicate what time the frame was captured and is also referred to as a pseudo dissector. Information regarding the capacity in bytes is defined and the interface and which device it is running on.
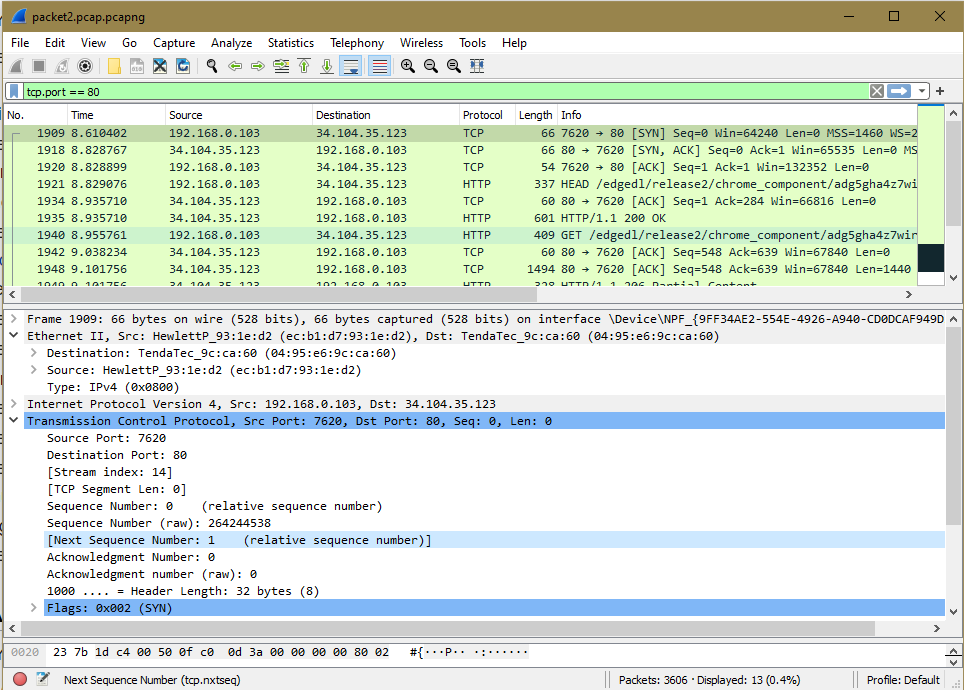
Analysing Tcp Packets
TCP packets are analyzed by observation of traffic in the top Wireshark list pane. On the filter box, TCP.port==80 is indicated to filter the packets to only the ones through port 80, and they should be in TCP format. The packet labeled SYN is selected. It will indicate to be ethernet II. The source and destination addresses are contained on expanding as well as the type of the IP version. The destination should be the default gateway’s MAC, and the source should be the user’s MAC address.
How many TCP packets were captured?
3606
What are source and destination port addresses?
- Source Port: 7620
- Destination Port: 80
Write the sequence and acknowledgment number:
- Sequence Number: 0
- Acknowledgment Number: 0
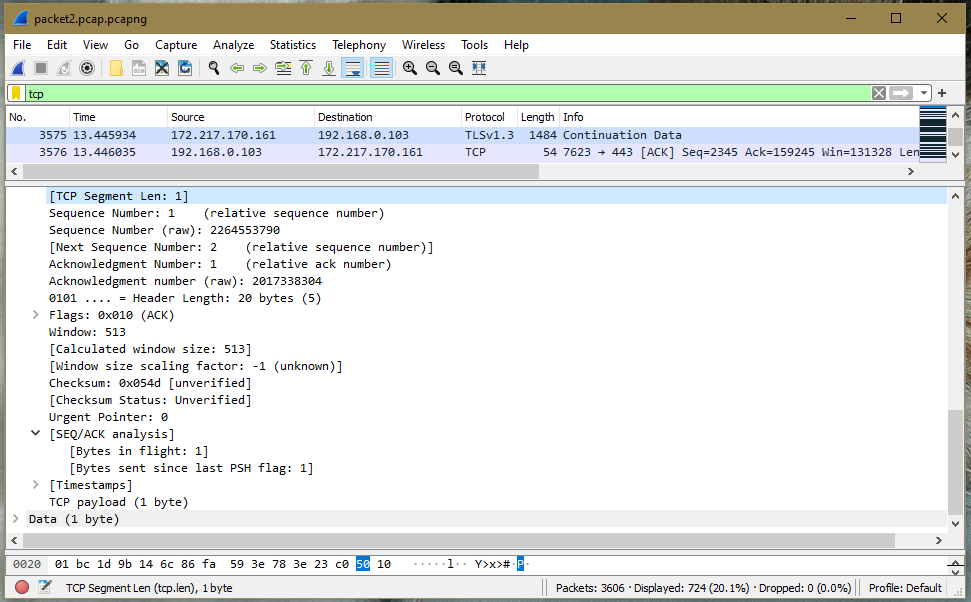
Tcp Checksum, Payload, and Segment
The TCP checksum is calculated by considering the TCP header, TCP body, and pseudo IP header. The main problem incurred is calculating it on the IP header as IP comes into the picture in the layer below the transport layer. A payload packet is the data portion of the packet. Configuration advances policy expressions to examine features of a packet, including the source and destination domains. A segment consists of data bytes to be sent and a header added to the data by TCP.
Give the TCP checksum, TCP payload size, and TCP segment size:
- Checksum: 0x054d
- TCP payload (1 byte)
- [TCP Segment Len: 1]
Syn and Ack Packets
At the top of the Wireshark packet list pane, the second TCP packet labeled SYN; ACK is selected. Details of the selected packets are then observed in the details pane. Notice that it’s at ethernet II, internet protocol version 4, and the transmission control protocol frame. Expand ethernet II to view the details. The destination is the MAC address, and the source is the default gateway MAC address. Expansion of the internet protocol to view IP details. The source address is the google web server IP address and the destination IP address of the local computer.
The source port is 80.
What are total SYN packets and ACK packets?
- 2 packets SYN
- 2 Packets ACK
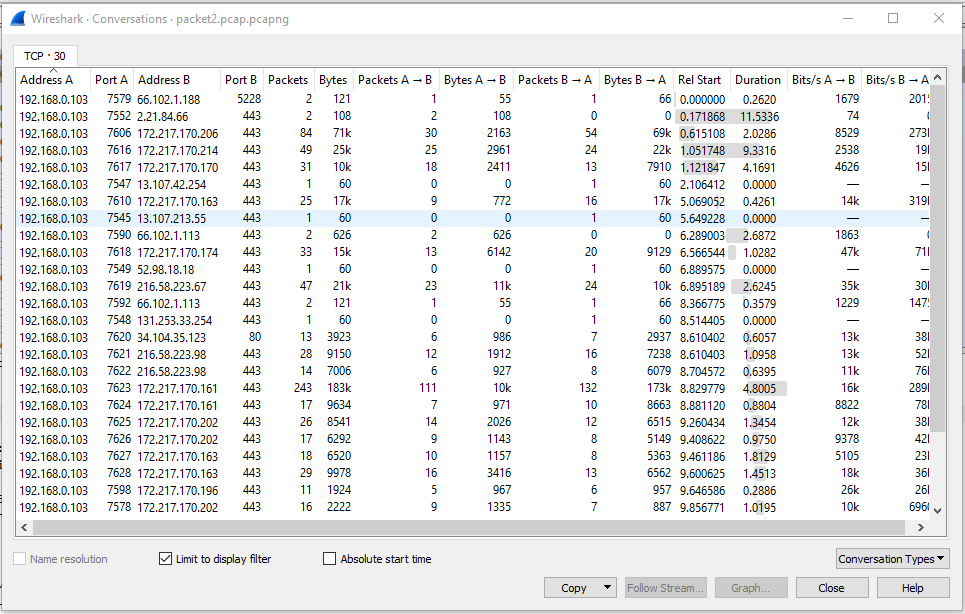
Tcp Streams
TCP is a connection-oriented protocol that first sets up a connection to the receiver and then sends the data in segments through the transport layer carried by IP packets. This way, it keeps a stream of data between to ends during transfer. This feature allows you to follow particular TCP conversations between two or more hosts by finding a particular source and destination and reassembling the data transferred in a particular exchange into something parsable.
What is the number of open TCP streams?
- 2 client packets
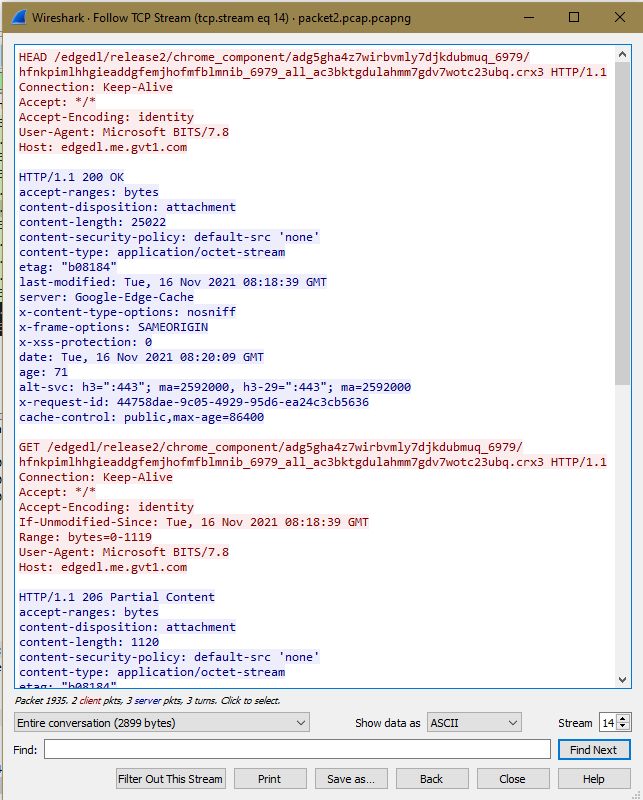
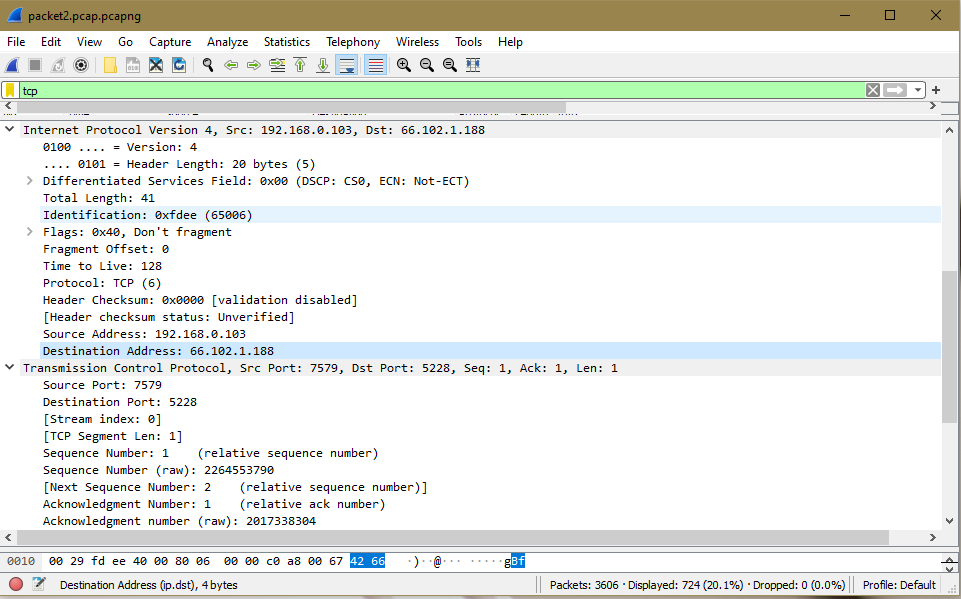
Analyze the IP packet and answer the following questions.
What is the total number of IP packets exchanged?
3606
The figure below is the IP header format. Fill in the header details from analyzing the IP packet from Wireshark.
Version: 4
…. 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
Total Length: 41
Flags: 0x40
Fragment Offset: 0
Time to Live: 128
Protocol: TCP (6)
Header Checksum: 0x0000
Give the screenshot of the I/O graphs and give your observations as a group.
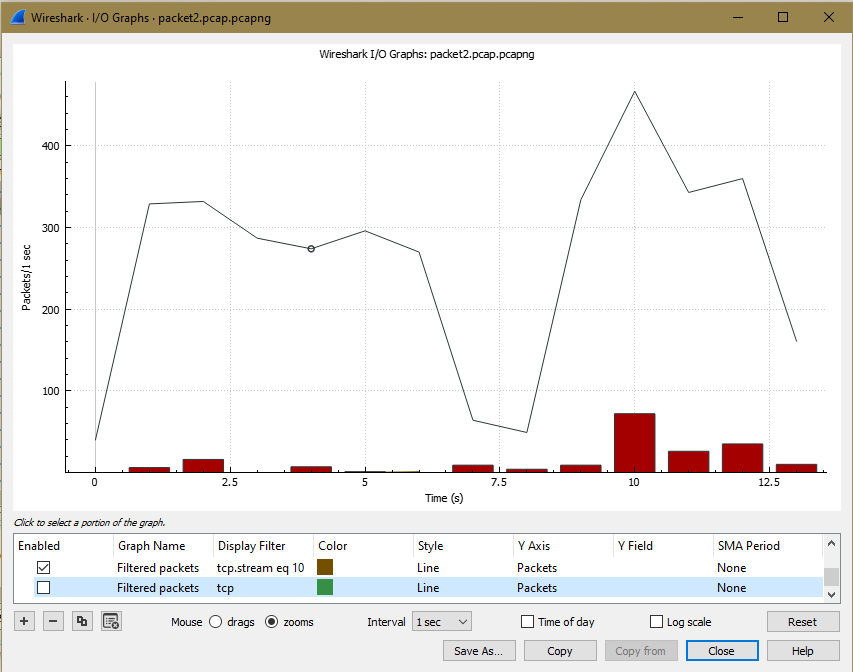
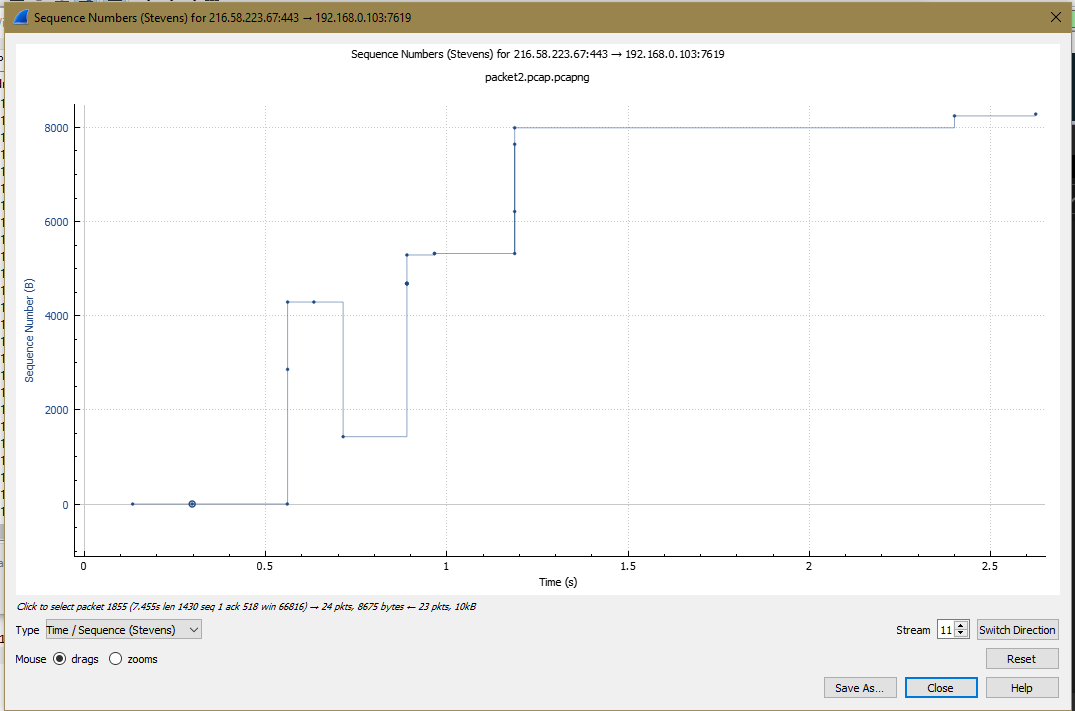
Observation
The Hypertext Transfer Protocol is an application protocol for distributed, collaborative, hypermedia information systems that allow users to communicate across World Wide Web. The purpose of HTTP is alongside HTML to create the first interactive, text-based web browser. Today, the protocol remains one of the primary means of using the Internet. HTTP works As a request-response protocol, HTTP gives users a way to interact with web resources such as HTML files by transmitting hypertext messages between clients and servers. HTTP clients generally use Transmission Control Protocol (TCP) connections to communicate with servers. body content
Key aspects:
- GET requests a specified resource in its entirety
- HEAD requests a specific resource without the body content
- POST adds content, messages, or data to a new page under an existing web resource
- PUT directly modifies an existing web resource or creates a new URI if need be
- DELETE gets rid of a specified resource
- TRACE shows users any changes or additions made to a web resource
- OPTIONS shows users which HTTP methods are available for a specific URL
- to CONNECT converts the request connection to a transparent TCP/IP tunnel
- PATCH partially modifies a web resource
Below is an attached pcap file to verify the answers given in the project analysis.
