Executive Summary
Asset risk and identification play a crucial role in organizational threat mitigation. The type, level, and potential impacts of treatment are understood through risk identification and classification. This report demonstrates how the risks associated with each department were analyzed through a risk-value assessment based on qualitative and quantitative metrics. The threat mitigation technique is shown to be the most effective risk control approach in this case study.
Introduction
Risk assessment is the combined method of risk management, evaluation, and analysis. An asset-based risk evaluation analyzes threats by monitoring the assets of an organization. Developing an outline of relevant assets presents a foundation on which a thorough examination of threat levels is conducted, revealing the efficiency of the current controls. The risk assessment method aims to identify risks, eliminate them when needed, or reduce the threat level posed by implementing management approaches (Li, Zhou, Tian, Xiong & Qin, 2018). However, asset assessment is evaluated through different sections, including asset identification and classification, threat identification and classification, and risk analysis involving vulnerabilities and risk control.
Asset Identification and Classification
Assets identification is categorized according to their sensitivity level, and the consequences for the establishment in case the information is revealed, changed, or destroyed without permission. The potential of an organization to effectively correlate varieties of data assets is greatly influenced by asset identification (Li et al., 2018). The goal of asset classification and recognition is to obtain all needed details of an organization’s assets in advance so that they might be used to respond to a risk impacting that asset. Some identified asset categories are information/data, people, and hardware.
An information asset is an organized collection of information handled as a single variable. The number of individuals who can use the information directly correlates with the asset’s increase in value (Li et al., 2018). According to this report, the information asset has been identified through the liability factor. This has been done through the company’s customer purchase, human resources and financial data evaluations. Therefore, the information asset has been achieved whereby the asset value has exceeded the liabilities hence better economic outcomes.
Another recognized asset category was the people category, which was identified through the criticality technique. This asset is available to one individual or associated with a specific task. It is simple to determine and assess the business’ most crucial assets through criticality assessment, enabling people to manage advertisements, inventory, and threats (Li et al., 2018). Hardware assets are any actual, physical corporate technology asset, such as those that are in use right now, those that are in packaging, and support facilities. It has been recognized from sales through personal classification schemes. The identification has been achieved through individual desktops, laptops and mobile phone assessments.
Threat Identification and Classification
The method of identifying threats looks at weaknesses and assesses how likely they are to damage a system. The ability to recognize risks enables an organization to conduct prevention measures. The business can get the data required to block illegal users and stop system intrusions. Threat classification enables the identification and organization of security risks and categories to examine their effects and to implement measures to prevent or minimize the risks threats to the system (Li et al., 2018). The primary goal of risk classification is to help clarify the aspect of threats. Some threat assets categories are; espionage or trespass, human errors and failures, and software attacks.
Human errors and failures are significant threats in identifying and classifying assets. This threat has been identified through analysis of intentional sabotage, illegal access, information gathering, intentional data theft, the threat of information sharing, damage of system applications or knowledge, and deliberate theft. Espionage or trespass is another threat involving an unauthorized person trying to acquire unauthorized access to the company’s information. According to Li et al. (2018), it is mainly used to collect confidential and sensitive information, company secrets, and other kinds of intellectual property that the attacker can exploit to achieve a competitive edge or sell for profit. It has been identified based on industrial espionage and cyberstalking.
Another identified threat is software attacks, which involve an unverified participant’s complete profile of all operations in any applications running on a particular process. The more surface area there is, the greater the possibility that a hacker will be able to acquire the target machine and run code via several vulnerabilities (Li et al., 2018). It exploits a security flaw to damage, destroy, or otherwise adversely impact a thing or subjects. The threat has been identified through attacks like Trojan Horses, worms, and viruses. Software attacks have the potential to crash networks, freeze computer and phone systems, and destroy information.
Risk Analysis
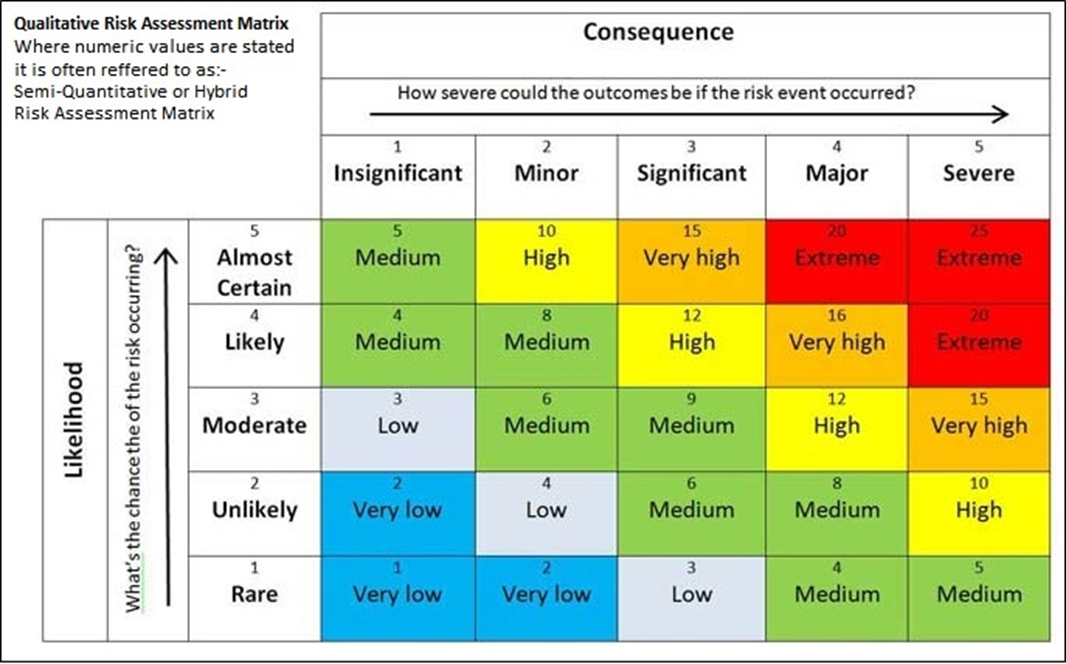
Risk analysis identifies and mitigates numerous threats that can significantly cripple businesses. It is crucial to begin with a risk assessment to have a basis for estimating the likelihood of risk occurrence to develop a practical risk measurement. Qualitative and quantitative risk assessment techniques are adopted for threat value evaluation in a bid to identify the most appropriate mitigation plan, which should be based on the risk level and available resources.
Top Five Vulnerabilities from Quantitative Analysis
The impact of a risk on business processes provides a framework for selecting an evaluation technique. A quantitative analysis is an evaluation that assesses threats using precise financial descriptions (Li et al., 2018). It is carried out with an emphasis on the data variables of the existing threats. One can determine a program’s possible threat using quantitative risk analysis. This can assist in determining whether a project is worthwhile. Based on the report’s research, the top vulnerabilities from the quantitative analysis are cyber-warfare, lack of a recovery plan, evolving malware, ransomware, and the sale of stolen data. These risks are valued based on the potential impact on the business, including its financial and technical aspects. For instance, cyber-warfare is identified as the most significant risk in terms of quantitative impact since an organization may lose its financial resources and be rendered incapable of operating again.
Top Five Vulnerabilities from Qualitative Analysis
Some business risks may not be classified under quantitative terms, although they grossly impact corporate performance. Li et al. (2018) assert that a qualitative evaluation reveals how some threats may remain undetected due to their immeasurable effects while damaging an entire organization’s information system. According to the analysis, intellectual property theft, which entails wrong access to and use of other people’s resources, has the highest threat level (Li et al., 2018). Strategy and product exposure are rated second, while information leakage takes the third position. These two risks are significant because they expose the business to exploitation by competitors and malicious individuals who could use the information to extort and blackmail key business stakeholders. Spoofing and social media engineering take the fourth and fifth positions, respectively, in order of threat value. This ranking shows that information theft is extremely risky to business operations as it affects all its departments and creates a rift between stakeholders, potentially crippling its sustainability in the market.
Differences between the Qualitative and Quantitative Analysis
The main distinction between quantitative and qualitative data is that quantitative data refers to easily measurable or calculated information, such as the total number of product purchases. Representing ideas or thoughts through qualitative data is impossible through a numerical figure like the average. According to Li et al. (2018), how data is examined is another distinction between quantitative and qualitative research. While rates, means, and other statistical data points can be determined from quantitative data using statistical assessment, a more extensive method is required for qualitative data analysis.
Advantages and Disadvantages of Qualitative and Quantitative Analysis
User research techniques, including qualitative and quantitative methods, are crucial for developing new products. Each of these strategies has advantages and disadvantages, and it can be advantageous to mix them. The most significant advantage of quantitative research is that they exclusively concentrate on precise, dependable, and solid data rather than views. As Li et al. (2018) explain, the information collected is more trustworthy and less subject to debate. A disadvantage of quantitative research is the data the result shows cannot be accurately generalized. Current events may influence the thoughts and final result. It is part of the community context; as society advances, so do people’s perceptions, and the quantitative study does not consider this movement.
Qualitative research focuses more on words and meanings than quantitative research on numbers. Because qualitative research focuses on human experiences and observations, it has a more authentic feel. Li et al. (2018) explain that the researcher can collect accurate data with a more solid base. Another benefit is that the study can build on the initial information by asking follow-up questions regarding the responses. One disadvantage of qualitative analysis is the wrong emphasis on numbers. Researchers may miss more significant themes and connections due to quantitative research’s potential limitations in pursuing specific, statistical linkages. Researchers risk overlooking unexpected information that could help the organization if they only concentrate on the numbers.
Risk Control
Risk control is known as the collection of techniques used by businesses to assess possible losses and make efforts to lessen or remove them. Different organizations employ risk control techniques as protective ways to minimize vulnerabilities and control threats to a manageable level. As a form of defence, several approaches can be used. One of the best strategies to protect high-risk information assets is the mitigation technique, which uses safeguards to restrict a successful attack to lessen the harm caused by a vulnerability. Li et al. (2018) state that this can be accomplished by correcting a defect that exposes a project to danger or by implementing compensatory measures that lessen the probability that the flaw might eventually cause damage. It also reduces the effects of the threat connected with the fault materializing. The mitigation technique is vital for all the quantitative and qualitative risks analyzed in this case study. It protects data from theft and safeguards intellectual property while minimizing cyber-warfare chances.
Conclusion
The first and most crucial step in a security plan and security monitoring execution is managing risk and valuing an organization’s valued assets. The assessors’ careful planning and evaluation are vital for accurately assessing terms like vulnerability, risk, consequences of the risk, reduced risk, and applied control of an asset. Cyber-warfare and intellectual property theft are the most significant risks valued under quantitative and qualitative approaches. Threat mitigation techniques are the best methods for controlling high-risk issues since they entail identifying the likelihood of occurrence and initiating appropriate blocking methods.
Reference
Li, X., Zhou, C., Tian, Y., Xiong, N., & Qin, Y. (2018). Asset-based dynamic impact assessment of cyberattacks for risk analysis in industrial control systems.IEEE Transactions on Industrial Informatics, 14(2), 608-618.
Appendix