Abstract
Cloud computing is a relatively new approach of offering computing services on a shared hardware and software platform due to the benefits associated with the approach. That is the rationale for organizations such as Google and Amazon among others in shifting toward the cloud in their service provisions.
Typically, the entire system of cloud computing drawing from its definition provides the infrastructure for organizations to offer clients services dynamically responding to their needs based on the pay-as-use basis, and the economic benefits which include positive net present value, a positive value on the benefit to cost ratio (BCR) calculated based on the ratio between cloud benefits and discounted investment costs and the discounted payback period on the period it takes for a firm that has shifted its services into the cloud computing platform.
However, for organizations to shift to the new computing platform, it is crucial to draw in the principles of system engineering which also draws on the Capability Maturity Integrated (CMMI) model to integrate the service. A comparative study of Google vs Amazon, emerging technologies adopted by Google and Amazon EC2 are presented in addition to the impact of cloud computing on technologies with a focus on virtualization.
Introduction
Cloud computing is an approach organizations in the recent past have adopted of offering computing services to clients without the need for the client own dedicated software and hardware resources, but a computer to access the services on the cloud.
It is a computing approach defined as “internet based computing where virtual shared servers provide software, infrastructure, platform devices, and other resources and hosting to customers on a pay-as-use basis”. These computing services are offered on shared hardware and software platforms characterized by network access, virtualization, multitenant model, and resource pooling based on private, public, and hybrid clouds.
It is with significant success that many organizations, such as the giant Google and Amazon have migrated into offering their computing services based on the cloud. However, the successful migration to the cloud computing platform draws on the economic benefits derived from offering cloud computing services on the shared platform reflected in the above definition.
The migration approach is however, implemented base on the central system engineering and the capability maturity model play in the design, development and integration processes. However, despite the migrations, a number of security issues related to the cloud computing environment have unfolded with well-designed counter measures despite the differences existing in the approaches by Google and Amazon and impact cloud computing has had on technology such as facilitating the development of virtualization, and other new technologies including Amazon EC2 and Google drive technologies as discussed in the following sections.
Definition
Cloud computing is defined as “internet based computing where virtual shared servers provide software, infrastructure, platform devices, and other resources and hosting to customers on a pay-as-use basis” (Krutz & Vines, 2010). On the other hand, 11.pdf defines cloud computing as a “model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) “and adds that it “can be rapidly provisioned and released with minimal management effort or service provider interaction” (Krutz & Vines, 2010).
These definitions point to computing services offered on shared infrastructure and accessible on demand on the internet. In conclusion therefore, the definitions make us understand that the computing infrastructure referred to cloud computing offers services that can are tailored to meet user needs and expectations despite the shared platform. Typically, therefore, each user is transparent to the other users on the shared platform.
Working Context of the Definition
To meet the objectives of offering cloud computing services on a shared platform to enable “ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources”, the cloud computing platform is characterized by on-demand services which can be accessed without human intervention, thus providing any customer in need of the services server access and other services such as network storage regardless of the availability or unavailability of any of the service providers.
Typically, the “On-demand self-service” makes services available and accessible any time and from anywhere in the world, making cloud computing such a powerful tool in offering computing services. It is crucial to note that the cloud computing platform is a host to different services with varied characterized.
Characteristics
To address the varied needs and services offered on the cloud computing platform, the computing platform provides broad network access as one of its crucial characteristics. Thus, network access to the cloud is based on standard mechanisms on a homogeneous environment which can either be thin or thick clients.
These characterizing elements of loud computing are complimentary to other characteristics which include rapid elasticity, resource pooling, and measured services. According to Krutz & Vines (2010), cloud computing is characterized by resource poling where service providers pool their hardware and software resources to provide computing services to different clients based on a multi-tenant model.
The multi-tenant model constitutes services provisions to different clients on a similar platform, who are differentiated from one another based on access policies, data access protection, and application deployment to isolate customers in a cloud computing environment.
Under the subject of the multi-tenancy model, virtualized application servers, shared virtual servers, fully isolated business logic, and shared application servers play the central role in isolating different customers on the same cloud computing environment.
On the other hand, to support services provision on the same cloud computing environment, it is indispensable that the platform support rapid elasticity. Rapid elasticity operates on an underlying principle of elastic allocation and de-allocation of computing capabilities, which sometimes are executed automatically.
In addition to that, the provisions of the comput9ing capabilities scale either inwards or outwards in relation to demand for the services. These provisions are made effective based on the provision of measured services as one of the characteristics of cloud computing. Thus, measures services lead to resource optimization based on the capabilities to monitor resource utilization, ability to control the provision and resource usage, and making the series transparent to the client and the service provider.
To attain the main objective of provisioning services on a share hardware and software platform, studies show that the cloud computing operates on different service models that include platform as a services, software as a services, and infrastructure as a service. These models are further deployed on private cloud, public cloud, community cloud, and hybrid cloud. Having discussed briefly on the definition of cloud computing and the working context, it is crucial to discuss the Cloud Computing Infrastructure.
Cloud Computing Infrastructure
Different authors approach the subject of cloud computing infrastructure with varying views in relation to the services provided on the cloud and associated characteristics, while others merge the approach into cloud computing models that include cloud computing “Infrastructure as a Service (IaaS)”, “Software as a Service (SaaS)”, and “Platform as a Service (PaaS)” models (Krutz & Vines, 2010).
Typically, these models provide the basis for discussing cloud computing infrastructure in the context of the current study. On the other hand, one of the key underlying principles of operation of cloud computing is virtualization, elastic capacity, resource management as a single entity, and functionalities on applications that execute cloud computing tasks. The figure below (figure 1) shows interconnections between different applications and services illustrating cloud computing capabilities.
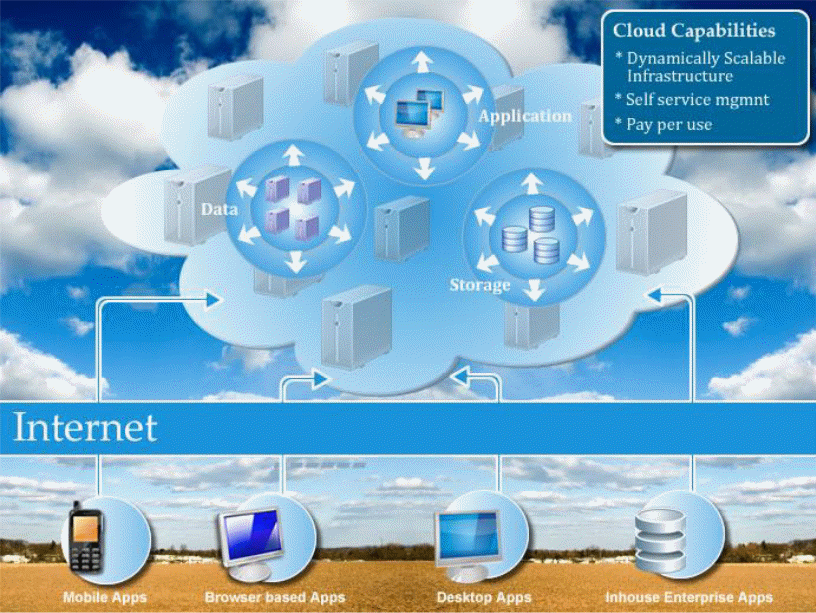
Infrastructure as a Service (IaaS)
One of the distinguishing characteristics of cloud computing infrastructure is the functionality associated with the provision of services on the cloud defined by Infrastructure as a Service (IaaS). Based on the fundamental definition of cloud computing and its functionality in the provision of services on a shared platform, Infrastructure as a Service (IaaS) provides hardware and software resources on a shared platform to provide computing services without any dedication or long term commitment of any of the resources to any specific individual, while enabling available resources to be dynamically provisioned in response to rising demand.
The underlying principle of operation is to enable the IaaS provider maintain and keep its data center operational while software maintenance remains the responsibility of the client (Krutz & Vines, 2010). IaaS is therefore a form of hosting that allows for network access, provides storage capabilities, and performs routing services. The latter functionalities are enabled on the cloud computing environment based on a pool of switches, servers, routers, and storage systems. The Infrastructure as a Service’s core function is to provide administrative services for the running and storage of applications when executing tasks in the cloud computing environment.
To attain the above objective, Infrastructure as a Service works on the principle that the owner is the sole provider of the resources required to provide computing services while the client can access the services by lease based on a flexible pricing mechanism (Krutz & Vines, 2010). That is made possible based on payments the client makes for the key components defining Infrastructure as a Service (IaaS). These components provide an enabling provision of services based on the Infrastructure as a Service (IaaS) model defined by policy based services, dynamic scaling, internet connectivity, automation of administrative services, and the utility computing services and billing model.
Thus, the central role of Infrastructure as a Service (IaaS) in this case is to provide an enabling environment for clients to execute tasks on a virtualized environment, thus optimizing virtualization using virtual machines built into the Infrastructure as a Service (IaaS) environment (Krutz & Vines, 2010).
Virtualization
While Infrastructure as a Service (IaaS) provides an enabling environment for clients to run their applications, to optimize the services and resources available on the environment, virtualization plays a significant role in optimizing the physical hardware and software platforms by extending these resources using a virtual machine, thus creating a virtualized environment (Wilde & Huber, n.d).
Virtualization “broadly describes the separation of a resource or request for a service from the underlying physical delivery of that service” (Wilde & Huber, n.d), while elsewhere, virtualization is defined as “the ability to run multiple operating systems on a single physical system and share the underlying hardware resources” (Wilde &Hubber, n.d).
While the definitions agree on the concept of providing some kind of resources abstraction, however, key to that is resource scaling based on a virtual environment. Thus, the virtual environment provides greater computing capabilities and resources than is physically available.
The rapid and seamless deployment of virtualization technologies into the Infrastructure as a Service (IaaS) model enables the provision of services based on Infrastructure as a Service (IaaS) model in its role. That enables clients to access the services from any part of the world that has internet connections.
In addition to that, the services provided based on the Infrastructure as a Service (IaaS) model are susceptible to incremental growth due to modularization. On the other hand, it is crucial to note the high degree of availability and resilience of the system, with little or no system failure. However, if system failure is experienced, system up time is minimal (Krutz & Vines, 2010).
In conclusion, from a technical perspective, however, Infrastructure as a Service (IaaS) model is seen as the underlying platforms that provides virtual infrastructure, easy deployment and dynamic provision of web-based applications with changing demand from clients, ensures load balancing is affected in the provision of resources for executing tasks on the cloud, provides service level leverages with clients, and pools resources for shared use.
However, it is important to distinguish Infrastructure as a Service (IaaS) with other services including Software as a Service (SaaS) in an attempt to crystalize cloud computing infrastructure (Krutz & Vines, 2010).
Software as a Service (SaaS)
Software as a Service (SaaS) is one of the cloud computing models with the underlying idea of centrally hosting software and associated data accessible by the customer on a web browser through a thin client. Software as a Service (SaaS) does not require the user or the client to create programs to use, but the client can configure the software to address their own needs and pay for their use based on the multi-tenant architecture (Mell & Grance, 2011).
Platform as a Service
On the other hand, Platform as a Service (PaaS) is a model that provides the required amount of hardware platform and application software based on client demands. A summary of the modes is tabulated in table 1 below.
By Krutz & Vines, 2010
However, there is need to evaluate the public, hybrid and private cloud models and the most appropriate for any organization to use in deploying its services and intergrading its application to the cloud.
Having discussed literature on cloud computing and its variants models, it is crucial to conduct a comparative study between Google.com and Amazon in industry application of the cloud computing concept and the rationale for firms migrating from the old models into the new cloud computing concept based on the role of system engineering and CMMI (Capability Maturity Modle Integrated).
Role of System Engineering and the Capability Maturity Model
Despite the security issues and vulnerabilities associated with cloud computing, many organizations have followed big organizations such as Google.com and Amazon.com in shifting their computing services from the old models to the new cloud computing model with the underlying migrations and integration into the cloud computing platform based on system engineering and the capability maturity model integrated CMMI) (Constantinescu, n.d).
That is partly due to the confidence inspired in many organizations on the security measures the computing platforms operates on besides the commercial benefits associated with cloud computing. Among the benefits include utility pricing, mobility of servers and data centers, flexible deployment of servers on demand, and fault tolerance support for alternative sourcing among others.
These benefits translate economically to positive net present value, a positive value on the benefit to cost ratio (BCR) calculated based on the ratio between cloud benefits and discounted investment costs. In addition to that, the discounted payback period on the period it takes for a firm that has shifted its services into the cloud computing platform (Constantinescu, n.d). However, it is recommended that further research be conducted on the economics of cloud computing to establish the economic rationale of investing and shifting toward the cloud.
It is however important to note that the migration process with system engineering and the capability maturity model integrated CMMI) underpinning the migration and integration strategies draw on the operational principles the CMMI and system engineering as discussed below.
To attain the objective of migrating from the old computing models into the cloud computing models by integrating their services, organizations follow the system engineering model consisting of system engineering management and the technical domain with the CMMI underlying the entire process being complimentary.
However, this paper focuses on the role of system engineering management in the migration and integration process with the CMMI playing a crucial role in the integration process. In the migration process, the system engineering management the system engineering processes, the development phase, and the lifecycle integration phases which is comprehensive top down approach (Constantinescu, n.d).
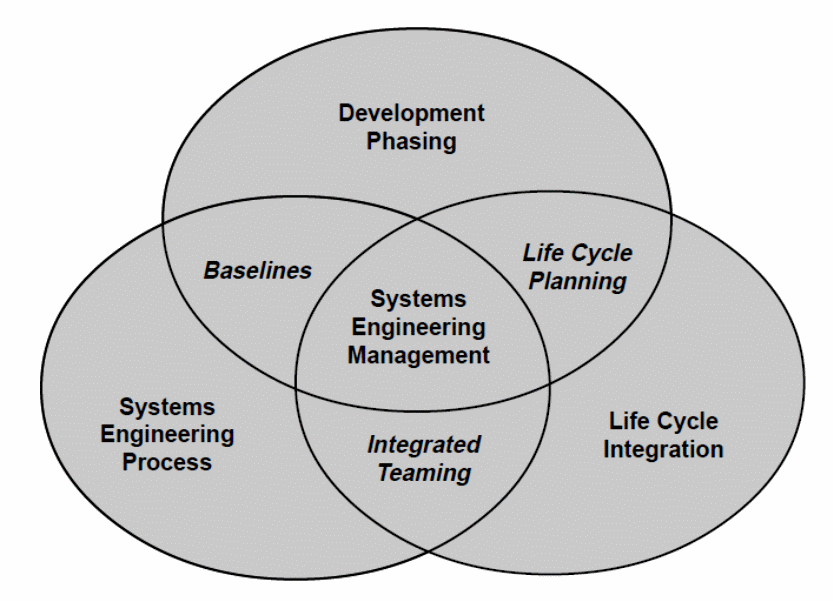
The migration process begins based on the system engineering approach, begins with the development phase, organizations focus on the system engineering concept in imitating migration into the cloud by descripting the system (Systems engineering fundamentals, 2001). That entails borrowing from the CMMI model that includes identifying people, methods, procedures, equipment, and tools. That is illustrated in figure 4 below.
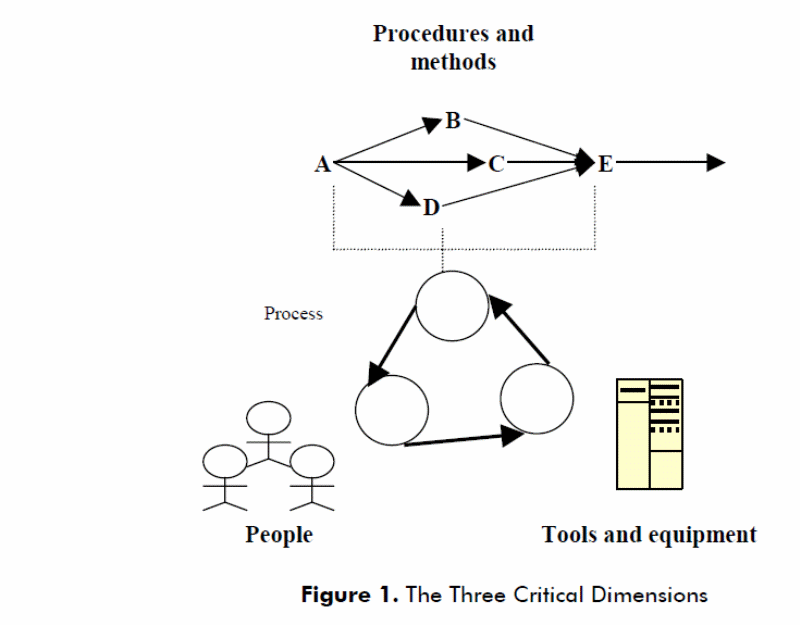
In addition to that, sub system components are considered with the system engineering process crucial ate every phase of the development and migration process (Constantinescu, n.d). The process phase is illustrated in figure 5 below.
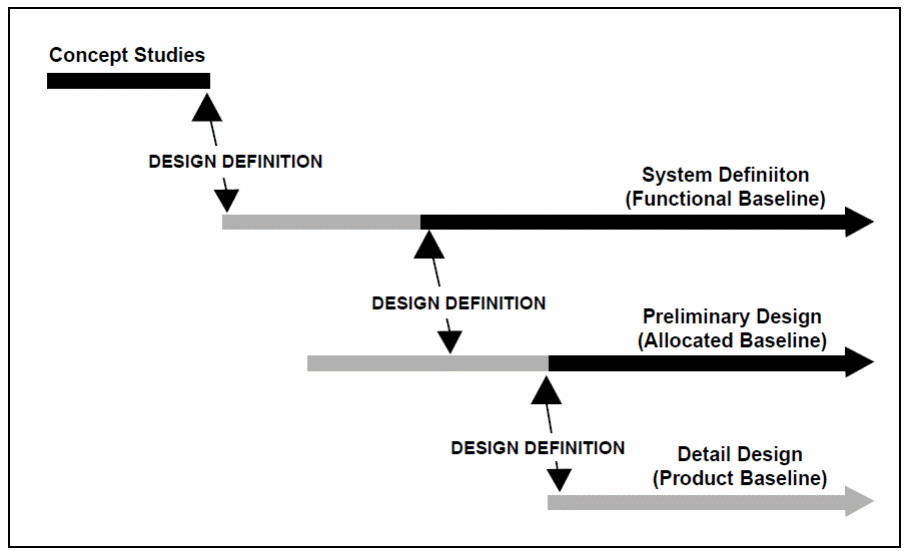
The entire process phase is characterized by concept studies, system definitions with underlying functional capabilities, preliminary design, and detailed design as shown in the above figure. Typically, the entire process bows from the CMMI process model with a multidisciplinary nature. Each of the elements in the system engineering process can be evaluated against the CMMI model characterized by the elements in table 1 below as a continuous representation of the process elements (Constantinescu, n.d).
Table 1.
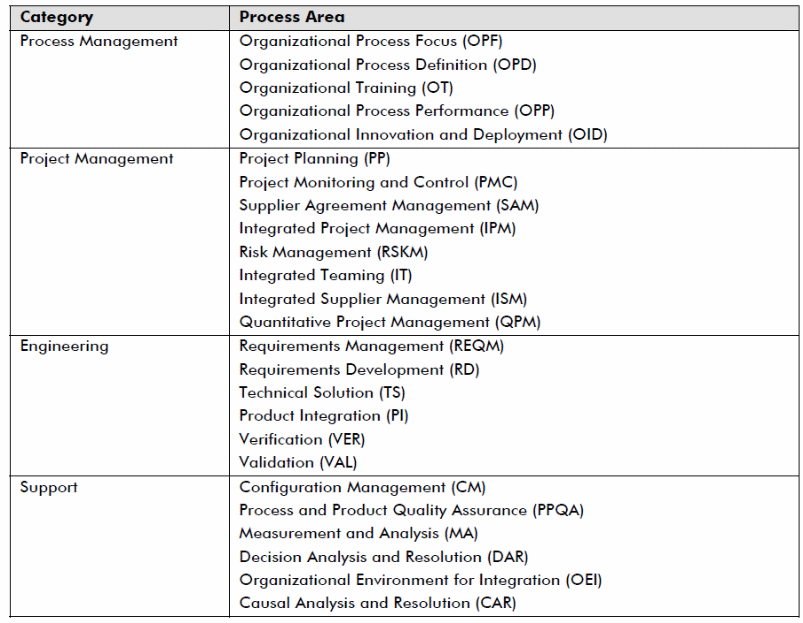
Each of the elements fit into the system engineering process with its core activities illustrated in figure 6 below.
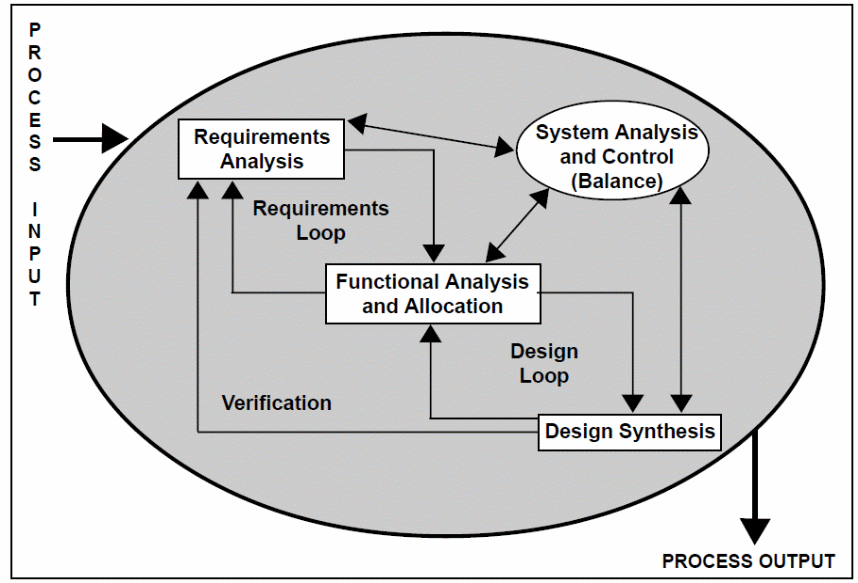
The entire process begins with the requirements analysis phase organizational experts make, functional analysis of the requirements, system analysis and control, and design and synthesis. However, reach of the phases are iterative and allows a high degree of looping, thus allowing modifications where necessary.
According to Bhardwaj, Jain and Jain (2010), the entire process culminates with the lifecycle integration process that allows for integrated development. At this stage, the design solutions are evaluated against initially defined requirements, for clarity, and if the process fits into the cloud computing model of the migrating firm.
System functionalities, operations, training, deployment, development, and verification of the entire system are evaluated for consistence with the original requirements in the lifecycle integration before tests are conducted and the platform ready for commercial use. However, there is need for further research in this area as different models fit into different system approaches and organizational needs (Bhardwaj, Jain & Jain, 2010). A typical example of the use of the capability maturity models is illustrated in figure 7 below. The process draws from different expertise from different disciplines before an organization adopts each capability from each discipline.
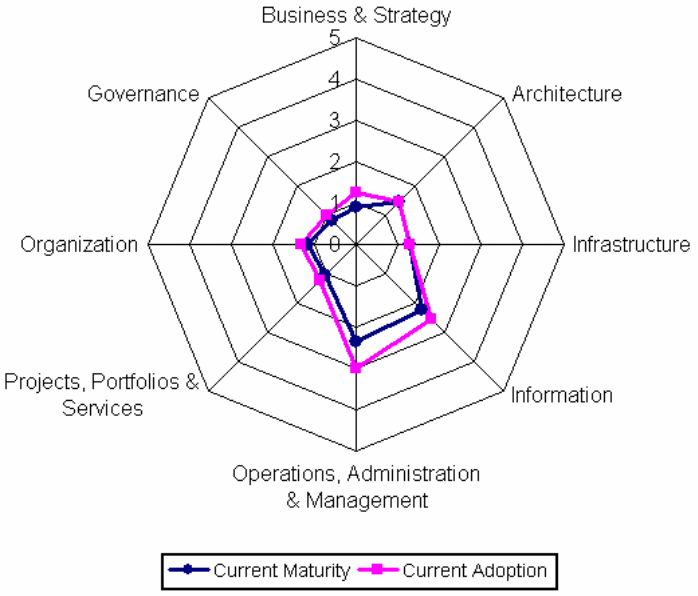
Typical examples of firms that have shifted into cloud include Google.com, which has innovatively developed the Google Drive as new technology.
Google Drive as New Technology
Google Drive as new technology is the current trend Google.com has adopted in offering cloud computing services based on a cloud storage service. Goggle drive is a technology that relies heavily on Google search in the provision of storage services on the cloud. Google drive as a new technology “is a cloud service that enables you to store documents, music, photos, and videos in one place” (Siddiqui, 2012).
Typically, “Uploading and accessing all your files is made simple as Google Drive syncs to all your mobile computer devices, essentially providing you with access to your stored files on any device” (Siddiqui, 2012). “With the incorporation of Google Docs in Google Drive, the process of transferring your Google Docs files is pretty much automatic” (Siddiqui, 2012).
The storage capacity provided varies on demand with 5 GB of storage given free of charge, while other chargeable storage services offered at a very low cost. it is worth mentioning the storage cost where “Google is offering plans of 25 GB for $2.49 a month and 100 GB for $4.99 a month” (Siddiqui, 2012).
Typcially, it is argued that “there are other amounts available as well with the highest storage plan at 16 TB for $800 a month” (Siddiqui, 2012). However, “for the types of files you can store, Google Drive supports up to 30 types of files and has support for third-party programs, allowing you to open up your files in any program of your choosing”. (Siddiqui, 2012).
Google drive is compatible with several technologies that include windows operating systems, and the Android operating systems with future projections of Google developing Google Drive iOS client. However, there are many competitors in the market offering cloud computing services including Amazon.com as comparatively examined below.
Google vs Amazon
Google and Amazon have been identified as some of the computing giants, which had migrated their services into the cloud computing platform with each organization providing the services with different approaches as illustrated in figure 8 below
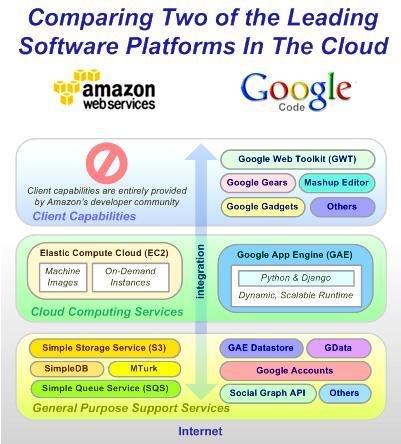
Research studies show Amazon to be the main competitor with Google based on different technology platforms. Amazon’s competition thrives on the elastic cloud compute that Google has strategized to combat using the recently unveiled Google App Engine. The Google App Engine provides services to application developers allowing them develop their own applications on the firm’s scalable systems that have fully integrated development environments.
However, the field had been dominated by Amazon based on its elastic compute cloud which is a web based service with the flexibility of allowing developers access resources to develop applications. One of the benefits associated with Amazon’s elastic cloud compute cloud (Amazon EC2) is the small up time required to boot its servers while scaling in a small amount of time.
In addition to that, the Amazon EC2 allows for quick scalability in response to dynamically changing client demands for computing space and power and provides “developers the tools to build failure resilient applications and isolate themselves from common failure scenarios” (Amazon Web Services, 2012). Base on that argument, it is crucial to discuss the Amazon EC2 business environment below.
Amazon EC2
Amazon EC2 is a cloud computing web service that provides computing capabilities that can be scaled and respond to dynamic changes in client computing needs within minimal time. In addition to that, users have absolute control of their instances with interactive direct access. That enables the user direct control and ability to stop an instance and restart or reboot the instance using appropriate APIs (Amazon Web Services, 2012).
It is crucial, however, to note that Amazon EC2 provides a wide variety of capabilities and benefits which include reliability, flexibility where multiple instances can be run with multiple operating systems without any conflicts on a secure environment.
One economic characteristic of Amazon EC2 is its low cost associated with on-demand services, spot instances, and reserved instances. These capabilities are attained based on the powerful features integrated into Amazon EC2. These features include the Amazon Elastic Block Store, Elastic IP Addresses, Auto Scaling, VM Import, High Performance Computing (HPC) Clusters, Elastic Load Balancing, and Multiple Locations. On the other hand, instances provides on the Amazon EC2 include Cluster GPU Instances, High-Memory Instances, Cluster Compute Instances, and High-CPU Instances (Amazon Web Services, 2012).
Cloud Computing’s Impact on Technology
Cloud Computing’s has had a significant impact on technology. One of the compelling innovations and development of technologies that enhance the services offered on the cloud. One such is the development and integration of virtualization as a technology that enhances the capabilities of hardware and software in the cloud. Thus, virtualization, besides the radical departure from old computing models to the cloud computing model is one of the new developments related to the impact of cloud computing.
Virtualization this case is “the ability to run multiple operating systems on a single physical system and share the underlying hardware resources” (Wilde &Hubber, n.d). Virtualization as provides a virtual environment that integrates virtual machines for executing applications on the cloud computing platform. That has also led to the development of a virtual PC. A virtual PC is a tool that enables users to exploit the services provided on a virtualized platform to access services from the cloud.
That comes with additional benefits to the cloud computing environment where Virtualization focuses on security issues that span users and service providers. Typically, all forms of external services, customers, and service providers need to work in a secure environment.
Security Issues with Cloud Computing
In answer to the above question, studies show the vulnerability of cloud computing in the context of its services on a shared platform. These include high tech crime, data loss, organized crime, and internal threats (NIST FIPS Publication 200, 2006). Organizations endeavor to provide solutions by use of separation of duties that draws on the plurality of conditions when satisfaction is derived from an execution of a specific task such as appending a signature on a sensitive object and data.
Furthermore, another security principle embraced includes defense in-depth. Defense in-depth includes use of multiple layers to enforce security. Typically, multiple layers provide additional security in the event the previous layer is fails (NIST FIPS Publication 200, 2006).
Thus, multiple locations are used to enforce security to ensure security robustness, and use of intrusion detection mechanisms to ward off attempts for unauthorized access to data and information. As organizations grapple with the idea of security, there is, need to comprehend other related security issues including fail-safe.
System on the cloud is designed to fail-safe should a catastrophic event occur. Fail safe is a concept integrated into the cloud computing and virtualization environment to inspire confidence in service providers using the technological platform by ensuring data and information remains safe without any modifications should the cloud and the virtualized platform fail (NIST FIPS Publication 200, 2006).
Thus, during recovery, the system recovers to a secure and safe state and the administrator only does access to system information. In conjunction with, economy of scale where system development and deployment remains simple, bit ensures on insecure and unauthorized paths exists (NIST FIPS Publication 200, 2006)
Conclusion
In conclusion, cloud computing is relatively new in the computing world with giant organizations having taken the leap toward the adoption of the technology based on benefits associated with the technology in the provision of computing services. These include utility pricing, mobility of servers and data centers, flexible deployment of servers on demand, and fault tolerance support for alternative sourcing.
Typically, these benefits translate economically to positive net present value, a positive value on the benefit to cost ratio (BCR) which can be obtained from the ratio between cloud benefits and discounted investment costs.
In addition, other computing platforms provide benefits which include reliability, flexibility where multiple instances can be run with multiple operating systems without any conflicts on a secure environment, with that of Amazon EC2 based on low cost associated with on-demand services, spot instances, and reserved instances. However, it is recommended that further research be conducted on areas economic benefits specifically for smaller organizations.
References
Amazon Web Services (2012). Amazon Elastic Compute Cloud (Amazon EC2). Web.
Bhardwaj, S., Jain, L., & Jain, S. (2010). Cloud Computing: A Study Of Infrastructure As A Service (Iaas). International Journal of Engineering and Information Technology. IJEIT 2010, 2(1), 60-63.
Constantinescu, R. (n.d). Capability Maturity Model Integration. Reliability and Quality Control – Practice and Experience Journal of Applied Quantitative Methods. Academy of Economic Studies, Bucharest, Romania.
Krutz, R. L., & Vines, R.D. (2010). Cloud Security. A comprehensive Guide to Secure Cloud Computing. New York: Wiley Publishing, Inc.
Mell, P., & Grance, T. (2011). Recommendations of the National Institute of Standards and Technology. Computer Security. Special Publication 800-145. National Institute of Standards and technology U.S. department of Commerce.
NIST FIPS Publication 200. (2006). Minimum Security Requirements for Federal Information and Information Systems
Systems engineering fundamentals (2001). Supplementary text Prepared by the defense acquisition university press fort Belvoir, Virginia 22060-5565.
Siddiqui, Z. (2012). Google Drive: What is It and Can Other Cloud Providers Compete? Web.
Wilde, N., & Huber, T. (n.d). Virtualization and Cloud Computing. New York: Wiley Publishing.