Abstract
This work is on the communication protocol engineering. The protocol can have many different parts and this has been discussed in this work. The frameworks and the languages for the protocol implementation have been discussed also in this report. The communication engineering history is discussed. A brief discussion has been made also on the standards of the computer network.
Introduction
There are parts that are similar in protocol of communication. They are not same as the protocol specification. They are on their own and are known as the patterns of the design. The protocols for communication can give the very specific ways in which the two components can engage in communication for example the way different messages can be passed between the two components and which rules are used in guiding the communication. The parts which are same and the similarities between two different protocols can be obtained if the communication protocols are looked into in details (Neves et al. 2007).
The parts and the way they are associated is not connected to other components of other specification. Is very important, to have knowledge on the patterns which are involved in the protocol system. The architecture is very important and very useful in keeping in order of the protocols. The architecture is important in the merging of the different parts of the protocol. The examples of the frameworks are the Specification and Description Language (SDL) and the Conduits+ (Consorzio 2004).
The protocol system
The protocol systems give many and different services on the different networks and where many service options are engaged. So as to handle this complicated task, the protocol systems are divided into subsets of the system which are commonly known as the layers of the protocols or the entities of the protocol. The different commitments of the protocols are also put into different layers and which are used differently from each other. This will be more advantageous than if the whole protocol is implemented at the same time. Each component is made in such a way that it will deal with a specific problem or a number of problems. This component have major connections and when are used together, they form a protocol system which is commonly known as the protocol stack. Any component should be able to communicate with the next or the associated components (Salkintzis 2006).
Protocol engineering
In the engineering of the protocol, an interface gives a definition of two different sets of messages. These are the messages which are incoming set and the outgoing set of the messages. There is connection and the non-connection components in communication of the protocol. The communication without connection is just a simple response of a request. The communication with a connection has an installed connection which is used in the exchange of the messages (Salkintzis 2006).
There can be communications which follow each other in sequence and which also occur in different phases. Different protocol components communicate to one another through messages which are sent to each other. A physical connection can be applied in the connection of the protocol’s stacks. This will provide the identity of the network. The components which are fond in the same stack are combined together by the paths of the message. The messages which are inside the system are sent through the paths of the message inside. The components are connected to their fellow components by the paths of the messages. Messages which are located outside the system are sent by these paths. This is because the messages which are sent to the peer component are transferred using the provided interface which is given by the protocol component which is lower (Neves et al. 2007).
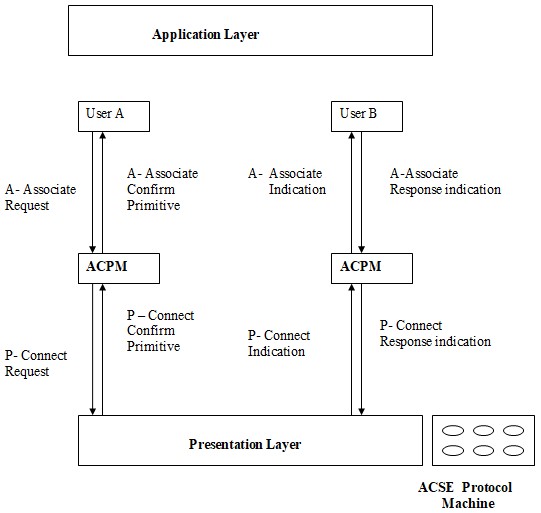
There are the functional components which are to be established in the implementation of the protocols. The interaction and the communication between the components in the protocol system show that it is a common work which is being done by all the people dealing with the protocol. The frameworks of the protocol give a very good and an easy way of the creation and the configuration of the working of the known tasks. They also give aid to the implementation which is of a lower level such as scheduling (Consorzio 2004).
Languages for protocol implementation
There are many frameworks which are different which have been made and also many languages for the implementation of the protocol. One of them is the Conduits+ is based on the orientation of the object. The implementation of the Conduits+ is by the specification and the description language (SDL) of the patterns of the design. This is a language which can be applied in the communication systems modeling. SDL can have its description made by using texts or graphics. It has a background which has a process orientation (Salkintzis 2006).
The conduits framework was useful in the implementation of the TCP/IP stack. Some improvements were done on it later and it was then given the name Conduits+. The parts of the Conduits+ have two major components, the conduits and the information chunks which are also known as the messages. These conduits can have a connection made resulting into a conduit graph which gives a real picture of the protocol stack. The information which passes through the stack is given by the messages. The different conduits include: Adapter, Mux, Protocol and the Conduit Factory (Neves et al. 2007).
The roles and the functions of the conduits as given: the first one is a Mux conduit do the multiplexing of the messages from the many conduits to the single and the other way round for instance, in a case where there is connection-oriented protocol, a Mux will give the direction for the messages which are coming in towards the direction of the connection which is holding the conduit protocol. The second one is that the protocol conduit is the inner part of the implementation of the protocol layer. It gives the nature of the protocol for example the incoming messages reactions at the time which is given. A Conduit Factory develops new chances of conduits for example to enable a new communication session. An Adapter conduit is made use of as an interface to the outside of a conduits graph, just in the same way as other software or hardware (Neves et al. 2007).
History of protocol engineering
The first networks for the computer communication were made in the 1970s and 1980s in the commercial and the research sectors. Many of these early protocols are still being used currently. The primary concepts are still the same that are being used only that more information has been added to produce new developments in technology. The 1970s and the 1980s were the very esteemed times for the individuals that were working in the field of the computer communications. By the end of the 1960s, the first link-level protocols were implemented for the minor access, from the ends to centre computers. In 1968, a protocol was defined with positive and negative recognitions which could not be relied on completely. Just at around the same time, IBM did the introduction of the Bisync protocol which was put in use for the longest period of time. In 1970s, a new modern of link protocols was developed with bit-oriented framing and also contained the sequence numbering (Neves et al. 2007).
This protocol was used in 1976 by the International Telegraph and Telephone Consultative Committee (CCITT) for the standardization of their protocol network access. In the 1960s, there were many projects for research which had been developed to make trials with the concept of the packet switching. The packet switching networks which were in use were ARPANET in the USA and the NPL network at the National Physical Laboratory in the UK. Larry Roberts guided the ARPANET team that had the first nodes of a wide area network operating in 1969. Donald Davies gave guidance the NPL team that had the world’s first local area network operational by 1970. Donald Davies formed the term “packet switching” in 1966 and made the invention of the concept together with Paul Baran who came from the ARPANET team. ARPANET is seen as being on the front line in the current Internet (Neves et al. 2007).
Computer network standards
At the same time, the common carrier companies and governmental post-telephone telegraph, organizations had discovered that standards for commercial packet-switched networks were needed and began to do some possible discussion approaches inside CCITT that with time became ITUT. During the mid-1970s, there was much discussion concerning the question whether a datagram or a virtual circuit network service would work well for packet-switched networks (Consorzio 2004).
In 1974 IBM made an announcement on Systems Network Architecture (SNA) as its general methodology to assist users to get data processing services and also obtain the devices in a computer network. SNA was described as a layered architecture which includes data link control, routing, flow control, management of resources which are shared and presentation services.
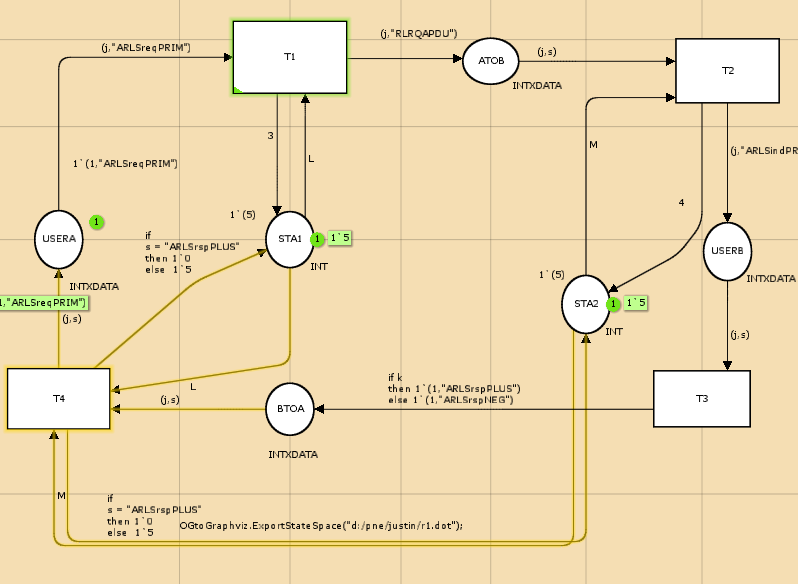
A Conduit
A conduit is a subset of the Conduit base set and is able to both interconnect with other conduits, and handle messages which are coming in. A conduit contains two points of connection which are important, Connection A and Connection B. Two conduits can be connected together by connecting their sides. There is the occurrence of the message sending and the receiving of the messages by the means of the two connection points. Messages are carried by Message Transporters, and they traverse the conduit graph and can trigger actions in the conduits. Behavior can be defined as a finite state automaton that recognizes the present state of communication and that is able to receive, create and respond to the control messages. It also gives some added services, such as counters, timers and storage, e.g. for protocol messages which are not fully received (Consorzio 2004).
The Protocol System pattern is the greatest pattern in the pattern language for protocol system. It defines a protocol system structure in high level by giving the specifications of what are the components that a system is made of, and how they are related to each other. The Protocol System pattern give the models of a protocol system by making specific: what are the components that a system is made of, which are the tasks of the components, how the components are connected to each other, and how a system can make communication with its environment. The component Interface gives a description of the allowed set of incoming and outgoing messages. It is these bindings between Entity Interfaces that gives the specification of how system components are interconnected.
An Environment Interface models interfaces to system’s environment. Viewing this from a protocol system, an Environment Interface acts as a message source for external messages coming in and as a message sink for the messages going out.
An Environment Interface can be with different tasks. The subset, Communication Interface and Auxiliary Interface, give a representation of the tasks above.
A Communication Interface takes care of the communication with a low level service (i.e. hardware) and this is also with system users (i.e. applications). It takes care of Protocol System’s normal communication. An Auxiliary Interface is concerned with communication that is outright relationship to Protocol System’s normal communication.
The use of interface does not reveal the lower layer from layers above it. This serves three related goals: organization of standardization effort, modular, component based, implementation, testing and maintenance process, and transparent and reliable system for user. These three cases are major sources of forces of this pattern. Effort which is applied in the standardization organization brings about the following forces: Some parts of a protocol system are standardized and some do not undergo standardization. An interface between peers is at all times standardized. Interface between entities in the same system is not always standardized, but there is always a recommended or informal interface (Consorzio 2004).
This recommended interface is known as a non-normative interface. An interface in standardization terms means detailed specification of coming in and outgoing messages. Interface in object-orientation means only messages coming in (i.e. method calls). Realization of modular implementation, testing, and maintenance process brings following forces: Time to market is short. When a standard (in some acceptance level; de-facto/de-jure etc.). In normal case there are more possible combinations of message exchange than it is feasible to test. Implementation of complicated communication software is slow and error-prone. Parts of a protocol system are legacy and they are implemented using some old technology. Reuse of old existing parts is used to improve implementation time and save old investments. Maintenance and updating of a protocol system must be easy and low cost. The implementation of a system is quicker and less error-prone if used implementation language or platform support repetitive tasks of protocol system implementation.
Transparent and reliable communication system for user brings following forces: There is a big gap between a user of a protocol system and an environment, or hardware, which a communication system should fill. If there are changes in environment, the user doesn’t want to know it. He or she wants just to use his or her application above the communication system. A protocol system has to work long time without any defect.
It should also recover almost all possible defects automatically and notify this to maintenance.
A protocol system should never lose any important data (Salkintzis 2006).
One example of important data is accounting information for an operator. The communication media (i.e. environment) is not always reliable. A protocol implementation has to be as efficient as possible. Especially video conference and other real-time multimedia applications are very sensitive for even small delays. However, in mobile computing communication is usually bounded by wireless network, not
Conclusion
We can conclude that, there are many communication protocol systems. The subsets of the communication systems can work independently but must have a relation to the nearby components. The frameworks can control the messages that are coming in and the outgoing messages. Is a fact that the principles of the early developed communication protocol are still being used presently only that there is improvement in the technology.
Reference List
Consorzio, B., 2004. IEEE Standard for Local and Metropolitan Networks of an Area. Michigan: Metropolitan Area Networks.
Neves, P. et al., 2007. WiMAX for Emergency Services: An Empirical Evaluation. In: International Conference Next Generation Mobile Applications Services and Technologies NGMAST. IEEE, pp. 340-345.
Salkintzis A.K., 2006. Evolving public safety communication systems by integrating WLAN and TETRA networks. IEEE Communication Magazine, 44(1), pp.38–46.