Abstract
Computer forensics also known as digital forensics is one of the most exciting fields of science. This field has tremendously grown from a comparatively murky tradecraft into an important platform for carrying out investigations. Various departments use computer forensic tools to carry out investigations and research.
For example, experts use computer forensic tools to carry investigations on crime. Additionally, computer forensic tools are also common in military applications. Researchers and experts are busy developing new computer forensic tools in order to retrieve actionable information, which is vital in investigations and problem solving.
However, the development of new technologies has brought new ways of capture and analysis in computer forensics. This paper discusses the single most technology that affects digital forensics known as the Virtual Machine Hypervisor Technology (Peterson & Shenoi, 2009).
Introduction
There is no doubt that digital forensics is one of the most exciting fields of science that many people like working in but not for the obvious reasons. Indeed, over the last two decades, people have been relying on digital forensics so much. Digital forensics has made crime investigation easier.
By relying on live evidence, experts have managed to unravel secrets behind certain activities. However, due to the evolving technology, scientists have encountered new challenges that require advanced tools to investigate. For instance, new file systems that require a different approach and operation is an example of how emerging technologies are affecting digital forensics.
These game changer technologies are not only instrumental in investigations, but also advantageous to the digital forensics industry. Since the development of solid-state hard drives, new technologies have emerged in the field of digital forensics that have made the field more interesting (Mocas, 2004).
Virtual Machine Hypervisor Technology
Over the past five years, experts managed to develop one of the most exciting technologies, which is instrumental in digital forensics. Indeed, the development of the virtual machine hypervisor technology has brought many changes in digital forensic analysis and operations.
Many IT and security experts may be quick to point out security concerns and condemn this technology. However, this technology is important in digital forensic analysis. Thus, this paper calls upon all stakeholders in digital forensics to pay attention to this new technology because it is vital in carrying out capture and analysis techniques.
A virtual machine is a computer-generated operating system developed to perform certain functions in digital forensics science. We understand that Virtualization helps an operating system to run on server hardware or sometimes on the computer desktop. However, for this to happen we must have software.
The “hypervisor” software directs and manages all activities within the system. In particular, this software performs three major functions. To start with, the software generates different independent partitions comprising of operating systems, software operations and appliances. Secondly, the hypervisor software creates boundaries that separate the partitions. Lastly, the software is able to entrap and direct commands among the three partitions (Casey & Stellatos, 2008).
In some articles, some writers use “virtual machine monitor” (VMM) instead of hypervisor. The two are similar. Although developed over three decades ago for mainframe computers, VMMs have been instrumental in digital forensic investigations. For example, their role in addressing security is undoubtedly great.
Additionally, VMMs are useful in addressing administrative and reliability issues that are dominant in distributed computing systems. The main task of the hypervisor is to perform decoupling. This is important in generating live-state images for forensic analysis.
In other words, the hypervisor provides channels of communication between the computer hardware and the installed software. In this way, the VMM has control over all operating systems running on the machine. The software also ensures that the system utilizes the available hardware resources effectively (Sutherland, Tryfonas & Blyth, 2008).
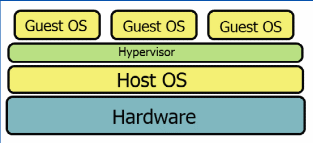
Source: (Sutherland, Tryfonas & Blyth, 2008)
Live-state analysis vs. Capture and Analysis Technique
Many forensic experts believe that the virtual machine hypervisor technology is a march towards obsolescence. In digital forensics science, these experts agree that it is important to adopt the live-state analysis and do away with static digital forensics.
In fact, since the development of the virtual machine monitors, the live-state analysis in digital forensics has become common and easy to understand. Although many research institutions across the globe still emphasize on capture and analysis techniques for search and seizure processes, they perform investigations on stored information under offline mode.
This is because they want to protect the original sample. Nevertheless, due to the ever-growing memory capacities, anti-forensics and drive encryption, there is big chances of losing the original sample of evidence because of pulling or plugging. This will undoubtedly affect the case under investigation.
Moreover, retrieving data from the volatile memory requires enormous expertise. Otherwise, it is easy to lose original information. Most importantly, the volatile memory has miscellany of anti-forensic techniques, which are useful in investigations. Moreover, the volatile memory has malware that is important in investigations but can easily disappear in case of a power outage (Rosenblum & Garfinkel, 2005).
These are some of the concerns that the live-state analysis technique addresses using the virtual machine hypervisor technology. Furthermore, the need to observe privacy of information is pushing many digital forensic institutions to encrypt their mobile computing devices in order to protect vital information from damage.
In fact, many of them are doing this by encrypting the entire disk of their systems using tools such as Pretty Good Privacy and TrueCrypt. Indeed, the best way to access information is to retrieve the forensic picture of a live-state system while leaving the data in untouched or unencrypted condition.
Before the development of virtual machine monitors, forensic investigator relied heavily on traditional techniques to carry out investigations on the sample of evidence. For instance, from the sample source, they created a bit-by-bit replica while at the same time making sure that they do not tamper with the original data.
However, in the current virtual environment, it is not possible to carry out forensic analysis on the original data without tampering with it. This is simply because there are numerous virtual machines that scurry concurrently on a huddled storage area network. Thus, many organizations have adopted virtualization technology on their enterprise server backgrounds in order to improve efficiency of investigations and protect the original data.
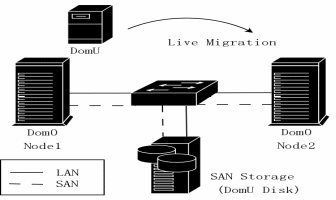
Source: (Rosenblum & Garfinkel, 2005)
Elimination of legal huddles to pave the way for live-state analysis
Although this emerging technology is the most effective in digital forensics, many players (including courts and echelon society) are yet to accept VMM images as the primary source files for carrying out forensic analysis. However, as the world continues to experience digital revolution and virtual machines become increasingly popular in forensic analysis; those opposed to this technique will finally accept it.
It is also possible to adopt new and efficient dimension techniques, which are analogous to those deployed in forensic DNA analysis. In forensic DNA analysis, the technique blotches biological evidence. Consequently, this can protect original data from damage. Nonetheless, according to research experts, forensic DNA tests always destroy the original sample.
However, these experts believe that the evidence is still important for future analyses. In most cases, enhanced flash memory faculties, drive encryption and providential anti-forensics make virtual machine hypervisor technology important in the current digital age. Undoubtedly, these three characteristics have moved digital forensics science into another level of efficient live-state analysis (Bill, Amelia & Steuart 2010).
Virtual Machines and Captured Image Analysis
In 2006, researchers came up with one of the most popular tools in digital forensics science known as LiveView. This is a Java-based tool that is able to generate VMware virtual machine from the normal disk. It does this freely on the VMware desktop by generating swiftly and effortlessly numerous images for forensic analysis.
In fact, many organizations have adopted this program and encapsulated it into their systems that run on virtual machines. Therefore, forensic experts will not require LiveView tools for their analyses in the future. Instead, virtual machine technology will provide the most efficient and faster way of obtaining images for forensic investigation and analysis.
This will also enable forensic experts to generate more copies for forensic analysis within a short period compared to traditional methods. Additionally, this technology enables the incarceration of malware and root kits within the exchange file of the perched operating system of a virtual machine picture.
Many traditional computers that have their operating systems running on hardware make it exceptionally intricate and unfeasible to evaluate the fortifications or vulnerabilities, which are common in very many virtual machine environments. This is the reason why it is vital to separate processes and leave them to work separately. In fact, similar processes running on a single platform means that these processes enjoy some similarities.
This is dangerous because shared processes not only share similar vulnerabilities, but also make the system weak and vulnerable. On the other hand, virtual machines isolate processes into different partitions. This means that there is enhanced consistency and security of all applications. Moreover, ports and process identities are always active when they work in isolation. This makes forensic analysis easier as experts can locate with easiness the information they need for analysis (Anson, et al., 2007).
Source: (Sutherland, Tryfonas & Blyth, 2008)
Virtual Machines enhance Intrusion Detection and Network Isolation
Virtual machine monitors enhance intrusion detection by creating channels of indirection and interaction between the hardware and the virtual machine software. This isolates networks and makes them effective. In other words, virtual machine monitors have the ability to run adjacent to the operating system in order to ensure that the processes remain separated (Carrier, 2006).
Virtual Introspection
Since the development of the virtual machine hypervisor technology or the virtual machine monitors (VMM), many experts believe that virtual introspection will control future digital forensic investigations. Across the globe, forensic experts and researchers continue to explore the efficiency of virtual introspection in digital forensics science. To start with, virtual introspection is principal in digital forensics because it enables live system analysis.
Forensic analysis methodologies together with the virtual machine systems are important in ensuring that evidences remain unchanged even after performing forensic analysis. Remarkably, this cannot occur in traditional forensic tests were tampering of original data is so common.
Nonetheless, by using the virtual machine hypervisor technology, experts can stop the virtual machine for a while and retrieve the information they want and then continue it. Definitely, the state of the virtual machine remains unchanged during data acquirement even if one suspends the process for a while (Bem & Huebner, 2007).
Challenge facing the virtual machine environment
Just like any other emerging technology, virtualization also has high-tech challenges that may be quite demanding. We have seen that while some digital forensics investigations are easy to perform, others are complex and need intricate methods of analysis. For instance, virtual introspection enhances forensic analysis through live-state analysis.
However, many scientists concur that it is not easy to carry out forensic investigations using this technique. In fact, due to its complexity, it requires advanced knowledge and expertise. The hypervisor software is an example of a central processing unit micro cipher. It therefore, means that it does not appear on the operating system.
Thus, it is complex to operate. On the other hand, although it exercises jurisdiction on the hardware, this can pose security challenges. In case, an attacker encounters a flaw in the virtual machine environment, entry into the system becomes easier, and someone can perform malicious damages compared to other technologies. Nevertheless, virtual machine environment tools such as software as a service (SaaS) can help in protecting the systems from hacking (Carpenter, Liston & Skoudis, 2007).
Conclusion
New technologies such as the virtual machine monitors have taken the world of digital forensics by surprise. There is no doubt that virtual machine monitors are more effective in forensic analysis than traditional methods. Unlike the traditional forensic images, virtual machine images are portable and easy to analyze. Moreover, the development of virtual introspection products has forced many organizations to adopt new technologies for forensic capture and analyses.
Reference List
Anson, S., Bunting, S., Ryan, J. & Scott, P. (2007). Mastering Windows Network Forensic and Investigation. New York, NY: John Wiley and Sons.
Bem, D. & Huebner, E. (2007). Computer Forensic Analysis in a Virtual Environment. International Journal of Digital Evidence, 6(2), 1-8.
Bill, N., Amelia, P. & Steuart, C. (2010). Guide to Computer Forensics and Investigations (4th ed.). New York, NY: Cengage Learning.
Carpenter, M., Liston, T. & Skoudis, E. (2007). Hiding Virtualization from Attackers and Malware. IEEE Security and Privacy, 5(3), 62-65.
Carrier, B. D. (2006). Risks of live digital forensic analysis. Communications of the ACM, 49(2), 56–61.
Casey, E. & Stellatos, G. (2008). The impact of full disk encryption on digital forensics. SIGOPS Operating System Review, 42 (3), 93-98.
Mocas, S. (2004). Building theoretical underpinnings for digital forensics research. Digit Invest, 1(1), 61-68.
Peterson, G. & Shenoi, S. (2009). Digital Forensic Research: The Good, the Bad and the Unaddressed. Advances in Digital Forensics, 306, 17–36.
Rosenblum, M. & Garfinkel, T. (2005). Virtual Machine Monitors: Current Technology and Future Trends. Computer, 38(5), 40-46.
Sutherland, I., Tryfonas, T. & Blyth, A. (2008). Acquiring Volatile Operating System Data Tools and Techniques. SIGOPS Operating System Review, 42(3), 65-73.