Due to the increase in internet usage, emphasis on data security and integrity has been escalated. Better measures in relation to software and hardware based mechanisms are still being invented and put into practice. All information regarding an organization’s business processes is of critical importance.
Information security and integrity is therefore, a vital consideration in all planning and implementation of processes in an organization. Data security ensures that all data is free from damage, erasure, theft, corruption, unauthorized access or modification, (Summers, 2004).
Data integrity on the other hand ensures that data is not altered in any way either by addition or substitution. In this essay we look at how to achieve security and integrity of data, in transit and in storage.
Considering the case for StoreItRite Inc, the business may be classified as data warehousing. There is need to secure data during transmission and storage. Another issue that arises is how to carry out communication between the staff members effectively yet securely over insecure communication channels.
First, we look at data transmission from the client to the database; data should be transmitted as ciphertext to avoid man- in- the- middle attacks. StoreItRite has no business accessing the data that is held in their hard disks for the customers; its sole business is to store data securely on behalf of its clients. A private key scheme will therefore, work effectively in this setting.
Each of the clients will generate a key which will be known only to the particular client. The key will be used to encrypt data for sending to the warehouse and the same key will be used to decrypt data on receipt from the warehouse, (Katz and Lindell, 2007).
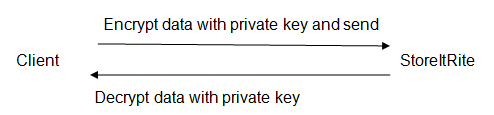
Secondly, to transmit the daily data back up, the warehouse needs to combine all the data received throughout the day. To enhance cost effectiveness of the scheme, the combined data files should be compressed and then encrypted with StoreItRite’s private key.
This will reduce the size of the file being transmitted, (Gollmann, 2006). When a client requires the stored data, it will just be retrieved and transmitted to them as ciphertext just the way it came in. On receiving the data from the warehouse, the client decrypts the data using his private key to obtain it in plaintext, (Smith, 2011).
In the office, the warehouse staff need to each generate a key pair, . The public key is given out to all other staff members and each of them keeps their private keys secret. When sending emails, the sender will encrypt the outgoing mail with the recipient’s public key, (Diffie, 1988). To verify the authenticity of the sender, the sender will attach a digital signature to the message.
This signature will also serve to prove the integrity of the email. It will be created by first generating a hash of the entire mail and then encrypting it with the sender’s private key. The resulting ciphertext is attached to the email being sent. On receipt the recipient will decrypt the signature with the sender’s public key. If it works that verifies the originator since he alone has his private key.
Then he will decrypt the message with his private key and generate a hash of that message. This is then compared with the hash in the signature. If they match the message is original from the sender, (Ferguson and Schneier 2003).
Email security at StoreItRite.
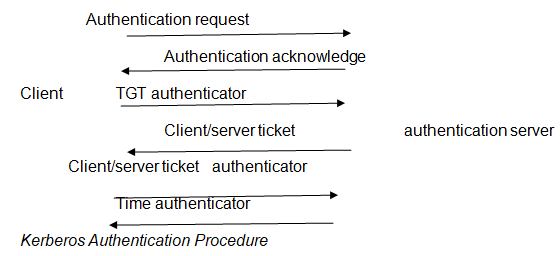
Kerberos and Public Key Infrastructure (PKI) are the two most widely used architectures for securing communication networks. Kerberos enables two communicating parties to exchange confidential information over an insecure network. In this scheme each user is assigned a secret key which is inserted in the messages sent by that user. This key serves to identify the sender.
The Key Distribution Center (KDC) serves to authenticate parties in a transaction that is to be carried out over the network communication channels. On the other hand, Public Key Infrastructure employs a combination of public and private keys. It does not require any preceding key exchange. With the use of public-private key pair, a centralized hub is not necessary.
Due to the use of a centralized hub, Kerberos is limited to a local intranet due to the management issues attached to a centrally managed KDC in widely distributed networks. The centralization of KDC makes Kerberos an easy to attack network architecture due to the single point of entry. KDC is also a throughput bottleneck in network performance and in case of its failure the whole network fails.
PKI on the other hand has its keys distributed using a certificate repository that publicly accessible. This eliminates the risk of PKI becoming a performance bottle neck as well as that of it acting as a single point of failure, (Neuman and Ts’o 1994). While Kerberos is best suited for centralized platforms PKI is effectively applied in multi-platform and distributed computing.
Message encryption and digital signatures are well supported in KPI enhancing the security and integrity of the messages sent and received throughout the network. Kerberos does not support these technologies hence, information security is questionable, (Kohl, Neuman, and T’so 1994).
References
Diffie, W. (1988). The first ten years of public-key cryptography. Proceedings of the IEEE. 76(2). 560-577.
Ferguson, N., & Schneier B. (2003). Practical Cryptography. England: John Wiley & Sons, Ltd.
Gollmann, D (2006). Computer Security. (2nd Ed) West Sussex, England: John Wiley & Sons, Ltd.
Katz, J., &Lindell, Y. (2007). Introduction to Modern Cryptography. CRC Press.
Kohl, J., Neuman, B., &T’so, T. (1994). “The Evolution of the Kerberos Authentication System”, Distributed open systems. 78–94. Washington: IEEE Computer Society Press.
Neuman, B., & Ts’o, T. (1994). “Kerberos: An Authentication Service for Computer Networks“. IEEE Communications 32 (9): 33–8. Web.
Smith, H. (2011). Data Center Storage: Cost-Effective Strategies, Implementation, and Management. CRC Press.
Summers, G. (2004). Data and databases. In: Koehne, H Developing Databases with Access: Nelson Australia Pty Limited. P4-5.