The convenience, speed, and anonymity provided by the internet have provided a new platform for criminals to extend their activities through cybercrime. The emergence of new advanced technologies has seen cybercrime taking new trends that are more secretive and dangerous to businesses and people. In fact, cybercrime leads to losses running into billions of dollars annually. Cybercrime takes many forms, including financial crimes like online fraud, abuse, computer attacks, and tolerance or encouragement of illegal activities such as gambling, child pornography, and copyright infringement. Unlike in the past, where a few individuals with criminal minds committed cybercrimes, the field is now run majorly by organized gangs with global networks. Some of them work under the very nose of law enforcement officers disguised as legal businesses or organizations.
The site I have chosen for this assignment is involved in the illegal sharing of files. Most files shared on the website are copyrighted and patented.
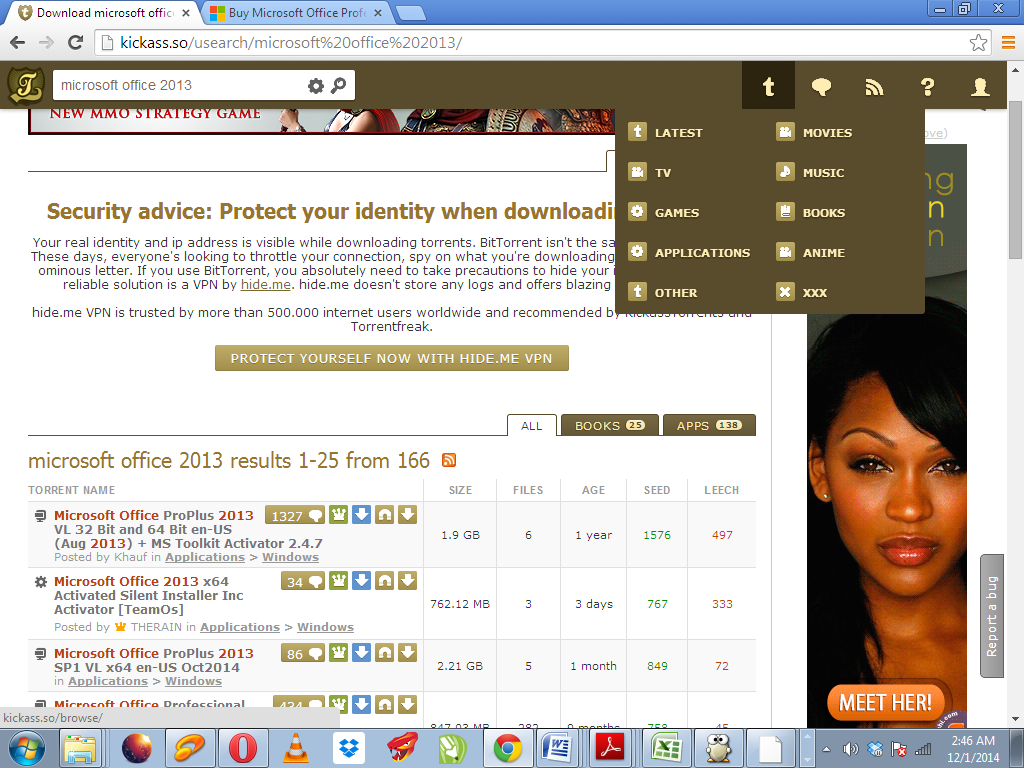
I believe the above site falls in the second category of websites that encourage young people to engage in dangerous or illegal behavior. It is a known fact that sharing of copyrighted files is both immoral and illegal. First, we realize that the website provides a platform for sharing copyrighted music files, software, and movie piracy. Its community page has seven broad download categories, including TV shows, games, applications, movies, music, books, anime, and others (Figure 1.)
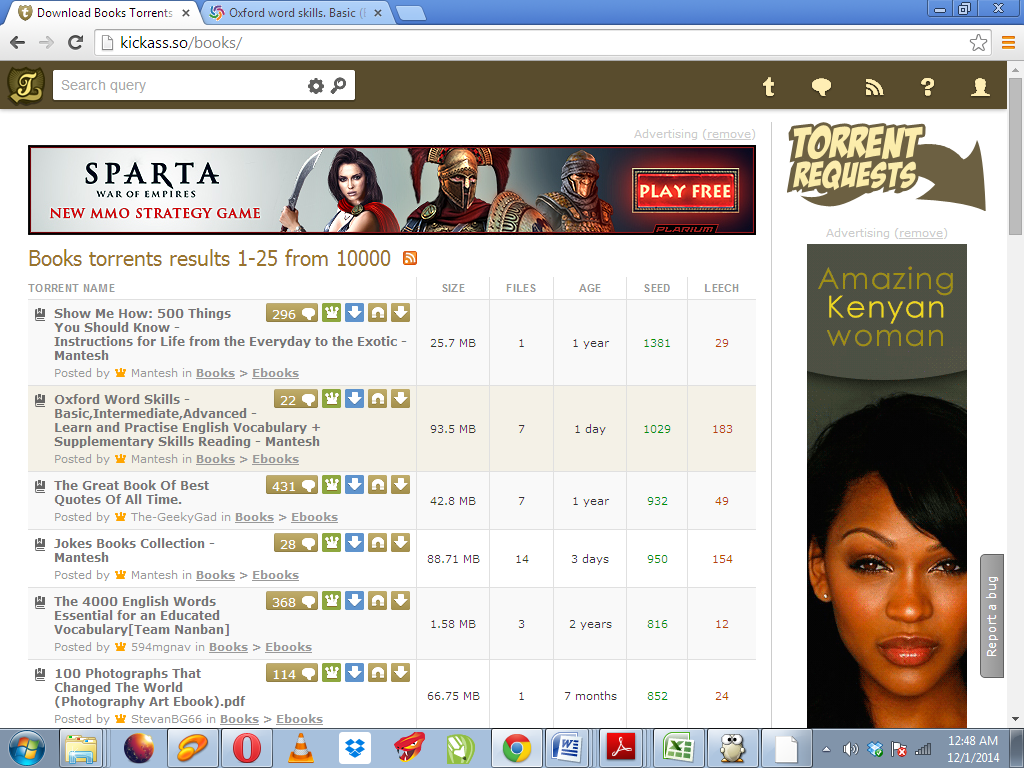
Most books being shared on the website are not available for free. In fact, by opening the book’s download link, I found “Oxford Word Skills – Basic, Intermediate, Advanced – Learn and Practise English Vocabulary + Supplementary Skills Reading” to be available for free, yet the book is on sale on Amazon.com for $55. The book was uploaded one day before my visit to the website and is already downloaded 1029 times (figure 2). I also believe the website is promoting piracy because even the latest Hollywood movies produced in 2014 that their producers have not earned enough money to settle the expenses incurred during production such as Horns, Fury, and Interstellar are available on the site for free download.
Things get worst when it comes to software. The website has almost all software files known to humans. A quick search of Microsoft Office 2013 returned 138 responses. One of the files had been downloaded 1576 times and seeded the same number of times. Microsoft Office 2013 has a market price of $400. Given that the first three links had been downloaded approximately 3,000 times, Microsoft Corporation had lost over $1.2 million on the illegal downloads. Many more companies suffer from such illegal downloads making losses running into billions of dollars annually. Even though the companies lose only money, the youth who are involved in downloading such illegal files lose much more in terms of character and responsibility.
Illegal Downloads, Copyright, File Sharing & Piracy
The international and national laws are clear on copyright and the penalties it may attract. Original authorship works such as music, drama, literary artworks, and intellectual property are often protected from unauthorized distribution for a given amount of time. During such periods, the only person who has the authority to distribute the work is its owner and his or her agents. Anyone who does not have the authority to redistribute the work but goes ahead to do so may be subjected to a civil or criminal case in a court of law. The internet and digital media have made the enforcement of copyright laws extremely difficult for law enforcement officers. File-sharing networks are difficult to monitor, thereby hindering the effectiveness of efforts put in place to curb such offenses. Just like the case in curbing other crimes, people should help law enforcement officers in curbing illegal sharing of files by refusing to participate in the crime and alerting the law enforcers of such activities immediately. People who take part in downloading illegal works cannot be absolved of any wrongdoing. In these criminals get a good chance of avoiding the cost of acquiring movies.
Digital Music and Software
The music industry is now fighting a huge battle against the illegal downloading of music via the internet. Kickass. So provides its users with a framework through which they can request and receive music files from other users in the network despite the files being copyrighted. When a user searches for a music file by title or a musician’s name, the user’s request is sent out to all computers in the network, and a response list is generated to the user in order of relevance. It takes only a few seconds for the file to be downloaded to the user’s computer or device. The same happens with software. Pirated software is requested from network members and downloaded in no time. The site provides serial numbers and program keys for all software downloaded from it to enable its users to enjoy software functionalities reserved only for those who have paid for the full versions of the software. Other software is cracked to allow users to gain functionalities limited by the software’s developers. These limitations are created to prevent people from benefiting from the software when they have not paid for them. Therefore, cracking the software and providing the crack to others is not only immoral but also illegal. It is even worse for people who shamelessly download the files for personal use, knowing very well that they have not paid for them.
Risks of File Sharing
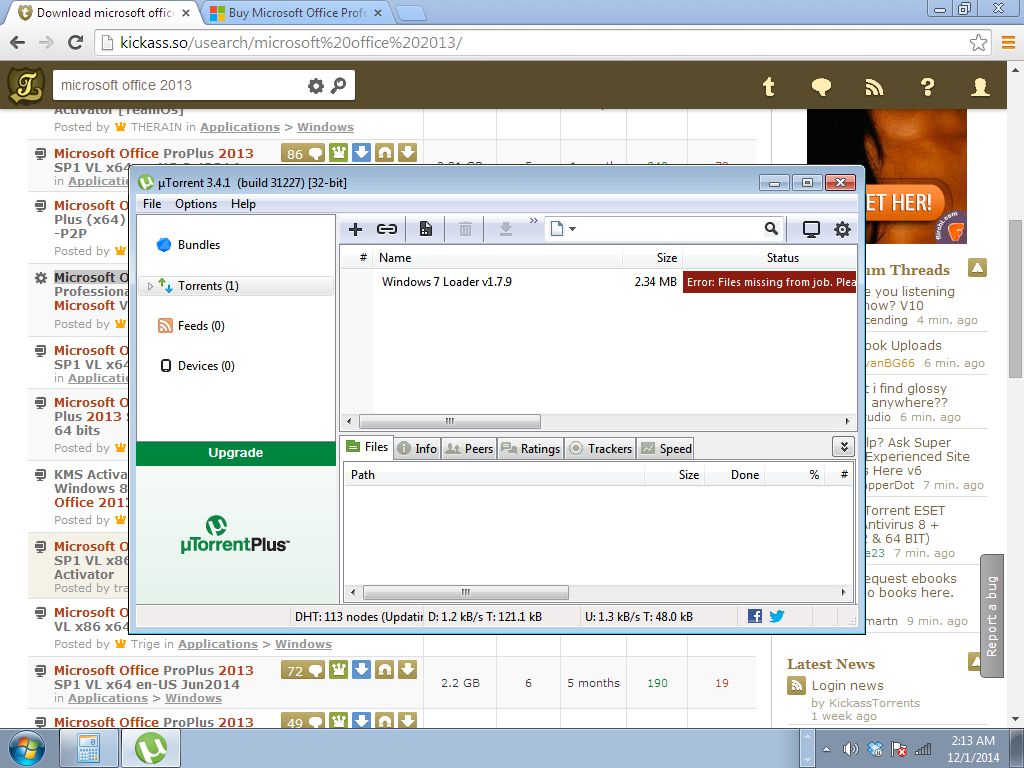
When you try downloading a file from the site, you are advised to first download and install ύTorrent, software used for direct torrents download (Figure 3). After installation, the software segments a reasonable size of the installer’s hard drive. The segmented section is then used to store downloaded and uploaded files. In fact, according to some analysts, the software has the ability to scan your computer for any information searched by other network users and then upload them to the user. For instance, if a user is looking for Microsoft Office 2013 and you happen to have the software on your hard drive, it could upload the file for the user to download. In such a case, private data and sensitive information become threatened by unauthorized access. Furthermore, the software could expose a user to attacks from malware and Trojan horses hidden in files.
The website gives assurance to their user that using its updated software for hiding IP addresses of computers makes their activities completely secured and untraceable (Figure 4). However, such IP hiding software has failed in the past and exposed users’ activities. If caught, a person involved in the illegal transfer of unauthorized files can face a jail term of up to five years and a fine of $250,000. Young or minor offenders are no exception. Their parents may face criminal charges for their involvement in the crime.
Responsibility defines a person. As consumers, we must be responsible for what we consume. Stealing from the people who make our lives easier by inventing new programs and creating new music and movies is a sure way of killing the very movies and music that entertain us and programs that make life easier. It is unacceptable to download unauthorized files, and the sites that promote such activities should be shut down and their members punished.