Introduction
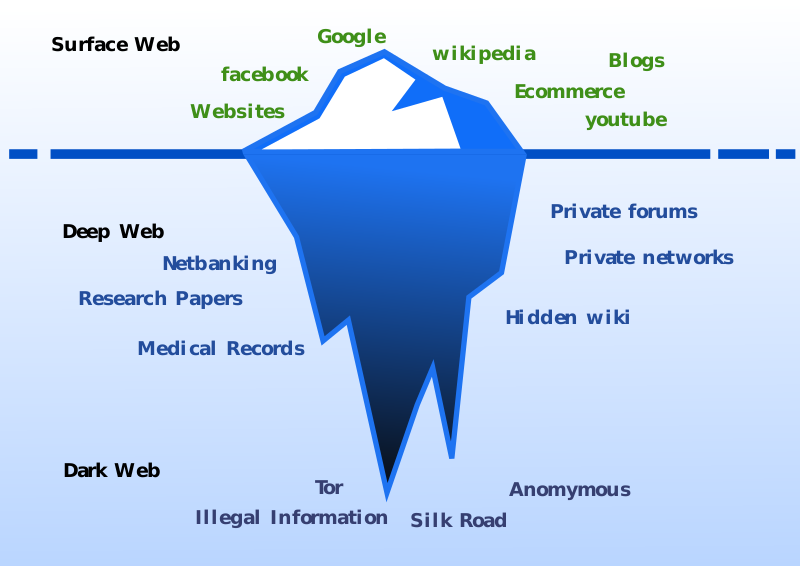
Millions of users are accessing information on the web every minute through their browsers, but very few pay attention to the type of web they are using. For any user accessing information on the web, there are a number of expansive services operating in the background and the “web” is only part of it (Coffey, 2020). Multiple layers that an average user encounters tangentially or never exist behind every web browser (Sultana & Jilani, 2021). The background is composed of three parts that make the web- Surface Web, the Dark Web, and the Deep Web as shown in figure 1. For an expert in cybersecurity, it is necessary to understand each of these layers and how they apply as risks and opportunities they present.
Discussion of the Types of the Web
The surface web is the is the region (or upper layer) of the Internet that contains publicly accessible web pages, which are largely indexed on the standard search engines such a Google. They allow regular daily activities and are accessible with standard browsers that requires no special configuration such as Edge, Mozilla Firefox, Google Chrome, and Safari.
On its part, the Deep Web is the portion of the web that is not indexed on standard search engines and cannot be searched with ordinary methods. Rather, it requires users to log in or have obtain special URLs and IP addresses to access a given website or service on the web (Elangovan, 2020). Most of these websites are content or data stored in databases for supporting daily services such banking or social media websites (Coffey, 2020). The information stored on such databases are updated frequently and presented in a different format based on the permissions given to specific users. For example, bankers are able to see all the information regarding all their clients and their transactions while customers can only see the information about personal transactions and not those done by other users (figure 1).
The Dark Web, on the contrary, is a subnet of the Deep Web that is less accessible to users and relies on connections between trusted peers. In addition, it requires specialized tools, software systems, and equipment for one to access. The Tor and I2P are the most common popular tools designed to access the Dark Web by providing user anonymity. First, a user must log into the Tor or I2P and then obtain a link to the specific page of interest from someone with knowledge about that part (Coffey, 2020). As such, only a few people with knowledge about the existence of a given web page, is content, and function are able to access. Consequently, it is the most popular web for individuals and groups with specific common interests such as illicit activities like trading in and distributing illegal drugs, weapons, stolen data, and malware. Nevertheless, it is also important to understand that several legitimate activities take place on the Dark Web, including sharing and accessing personal or group information that is private, protecting personal identity, and communication within a group (Coffey, 2020). As an example, many media organizations use the Dark Web to protect confidential sources in a legitimate way as shown in figure 1.
Reflection and Conclusion
Having looked at the three layers of the web, the question of interest regards how it matters to cybersecurity practitioners. A comprehensive understanding of the differences between the three parts of the web provides a framework for experts to build both reactive and proactive programs for cybersecurity (Coffey, 2020). For example, some forms of data such as voter, customer, and patient information require Deep Web to ensure than only the legit users have access. Similarly, government and media institutions may use Dark Web to protect their sensitive information such as military, voter, and other information. Furthermore, the practitioners need to understand how the Dark Web exists and functions and the channels through which they can be accessed to help organizations identify sources of cybersecurity threats.
References
Coffey, M. L. (2020). Library application of Deep Web and Dark Web technologies. School of Information Student Research Journal, 10(1). Web.
Elangovan, R. (2020). The Dark Web: Hidden Access to Internet Today. In Encyclopedia of Criminal Activities and the Deep Web (pp. 129-139). IGI Global.
Sultana, J., & Jilani, A. K. (2021). Exploring and Analysing Surface, Deep, Dark Web and Attacks. In Security Incidents & Response Against Cyber Attacks (pp. 85-96). Springer, Cham.