Introduction
The Palestine Islamic Jihad (PIJ) is the potential radical terrorist organization operating in the Palestinian arena. The Palestinian Islamic Jihad (PIJ) is a vicious creature among Palestine’s extremist groups like that of Hamas. Islamic Jihad launched suicide attacks against Israeli targets with a view to establish an independent Palestinian state. The PIJ nourished the ideology of jihad in its spontaneous endeavors to liberate considered as a holy struggle. Palestine from the yoke of Israel. The PIJ was little more than a shapeless collection of factions like that of Hamas in the mid 1970. The group maintains nexus to the Muslim brotherhood in Palestine and Egypt.
The PIJ received spontaneous enthusiasm from the Jihad movement in Egypt which dreamt to install the secular government in Cairo as an Islamic alternative force. The Jihad movements abnegated the political ideology that was prevalent in the Middle East. It is a unification of the Islamic world as a pre condition for the salvation of Palestine. Palestinian nationalist’s optimist that the struggle against the “Zionist entity” would forge broad based unity among Arab states.
Group Ideology
Czwarno, M., (2006) addressed that the Islamic Jihad holds the view that it is in the precursor of a pan-Islamic revolution that instigated the revolution in Iran. In spite of Shia orientation, the Iranian revolution provided insight a potential prototype for the PIJ. The PIJ opposes moderate secular Arab administration. Two demagogues have played vital roles in the PIJ’s history. Fathi Shaqaqi was despaired by the moderation of the Muslim Brotherhood. Egyptian administration expelled Shaqaqi from Egypt after the assassination of President Anwar Sadat in 1981. He repatriated to the Gaza Strip to form the Palestinian Islamic Jihad.
Subsequently, Israeli authorities expelled Shaqaqi to Lebanon in 1988. During his stay in Lebanon, he maintained political nexus with Syria and Iran, as well as Hezbollah. The group received training and armaments from the Iranian Revolutionary Guards. The PIJ returned to Lebanon in support of Hezbollah. Shaqiqi was assassinated by Israeli intelligence agents in Malta in 1995.
Arquilla, J., and Ronfeldt, D. (2001) mentioned that Dr. Ramadan Abdallah Shalah, a close associate of Fathi Shaqaqi took over the responsibility of PIJ after Shaqaqi’s demise. At the onset of the first Intifada, there are as many as 250 militants in PIJ. The PIJ introduced the use of suicide bombers following their contact with Hezbollah. The group is liable for dozens of attacks at Israeli targets on the anniversary of Fathi Shaqaqi’s demise.
Harakat al-Jihad al-Islami al-Filastini is known as Palestinian Islamic Jihad (PIJ). It was established in 1979 by Islamic fundamentalist Fathi Shaqaqi. The 1979 Islamic revolution in Iran influenced the group’s founder Shaqaqi influenced Iran Islamic revolution in 1979. The PIJ is committed to create of an independent Islamic Palestinian state and the devastation of Israel through a jihad.
Targeting & tactics
The Whitehouse (2008) cited that the PIJ members remained active in Egypt launched attack a tour bus in Egypt in February 1990 killing 11 people. PIJ agents were arrested in Egypt in September 1991 while attempting to launch terrorist attack. The PIJ launched its terrorist attack against Israel in the 1980s. Before the intifada in 1987, it carried out several terrorist attacks in the Gaza Strip. The factions leaders, Shaqaqi and Abd al-Aziz Odah, were expelled to Lebanon in 1988.. After Olso peace treaty in 1993 between Israeli and the Palestinians, Shaqaqi expanded the political network of the organization to become a member of the new Syrian influenced Rejection Front.
The group is patronized from Damascus and its financial assistance from Damascus and Iran. The PIJ also located offices in Beirut, Tehran and Khartoum. Except Israel, PIJ deems the United States as an enemy because of its support to Israel. The PIJ also opposes moderate Arab regime.Since September 2000; The PIJ has been liable for scores of terrorist attacks since September 2000.
Capability and overall goals
Office of Homeland Security (2008) stated that Shiqaqi admired Ayatollah Khomeini for being the first Muslim leader to bestow Palestine its proper place in his Islamic ideology. The PIJ began its armed operations in 1984. The PIJ consolidated relationship with Hamas during the 1987 to 1993 intifada, but subsequently the policy was discarded. Shiqaqi’s exile to Lebanon consolidated the movement’s ties with Hizballah and Iran.
Iran became the movement’s major financial sponsor. Hezbollah provided it with training facilities and logistical support.. The PIJ expanded its network in the Palestinian refugee camps in Lebanon. Hamas was always an independent Palestinian movement. Islamic Jihad became a tool of Iranian policy in the Arab-Israeli disputes. The outset of the Israeli-Palestinian confrontation boosted the morale of Islamic Jihad in September 2000.
The American-Israeli Cooperative Enterprise (2008) stated that the genesis of PIJ is from among Palestinian fundamentalists in the Gaza Strip during the 1970s. The PIJ is committed to create of an Islamic Palestinian state and the devastation of Israel through jahad. The PIJ showed its terrorist identity when it attacked a tour bus in Egypt killing 11 people including nine Israelis in 1990. The PIJ has launched cross border raids against Israeli targets in the West Bank and Gaza Strip.
The PIJ has threatened to attack US interests in Jordan. PIJ agents were arrested in Egypt while trying to enter the country to instigate terrorism in September 1991. The PIJ receives massive financial assistance from Iran. The PIJ’s annual budget has been calculated at several million dollars, a lion share of which is earmarked for funding terrorist attacks against Israel.
A terrorist organization that threatens the U.S. homeland
Basics Project, (2008) mentioned that on Sept. 11, 2006, al-Qaida deputy leader Ayman al-Zawahiri announced the merger of al-Qaida and the GSPC on sept11, 2006. The GSPC changed its name to the Organization of al-Qaida in the Islamic Maghreb on Jan. 26, 2007, after receiving permission by Osama bin Laden. Al-Qaida was established by Usama Bin Ladin in the late 1980s with a view to liberate Afghanistan against the Soviet invasion. The present objective is to establish a pan-Islamic Caliphate throughout the world by working with allied Islamic extremist groups’.Under the leadership of Osama bin Laden; Al Qaeda operated military training camps in Afghanistan from 1996 to 2001. The U.S. attack on Afghanistan and subsequent collapse of the Taliban regime eliminated this presence.
Tom, R., (2008) added that the newly renamed organization of al-Qaida in the Islamic Maghreb (AQIM) — formerly the Salafist Group for Call and Combat (GSPC) — recently killed approximately 30 people and wounded more than 220 in two suicide attacks in Algiers. The AQIM also launched attack in Algeria killing four people on Feb. 13, 2007. The implications for international security as al-Qaida and the AQIM take advantage of their extensive network and export operatives to the European continent and the United States. In January 2007, French intelligence gave the evidence of possibility of a terrorist attack within France during the elections in April and May 2007. The purpose of the attack would be to influence the outcome of the elections.
Steve K., (2005) argued that the escalation will prevail steadily in Algeria will depend on a few factors, including
- al-Qaida’s ability to inspire more fighters to help sustain AQIMs offensive in the long term,
- the strength of Algerian counter and anti-terrorist methods, and
- whether a significant portion of the former GSPC will join the global jihad and export themselves to foreign theaters to fight.
According to some sources, many AQIM members have joined the insurgency in Iraq. The use of suicide bombers is the first introduction of al-Qaida’s methods in Algiers. There is no reason to believe that AQIM will not export these tactics to the western arena.
Steve K., (2005) also added that the Al Qaeda’s financing model appears to be result-oriented rather than rule oriented. Al Qaeda works on multiple levels, which is what makes it such a formidable opponent. Sometimes it operates top-down, with orders coming from the CEO,” The Washington Post. 17 February, 2002.Al Qaeda recruits and trains its own cells, and retains complete operation control over them. Al Qaeda would send funds to conduct the operation.
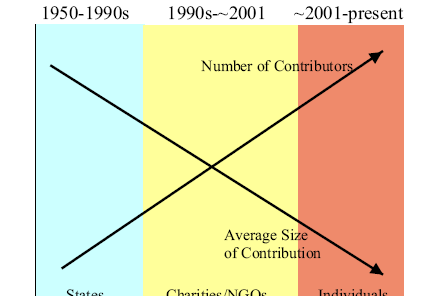
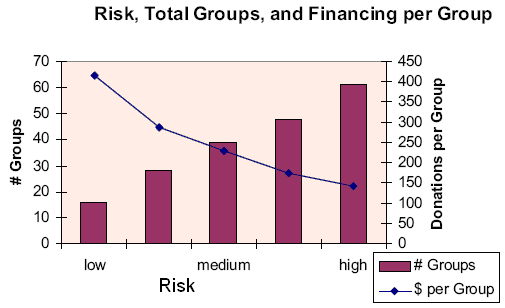
Breinholt, J. (2004) argued if the funds move internationally, the number of terrorist groups increases but decreases their size. As the risk of moving money increases, terrorist groups make the decision to launch attack in order to continue operation below the new risk verge. If the capacity remains the same, the supply of terrorist dollars will not decrease. In the introduction of the baseline model for donations, various risk levels emerged different numbers of groups (fig- 2).
If the risk of soliciting and holding donations increases, there will be possibility of financial fractionalization of terrorist groups.
Breinholt, J. (2004) also mentioned that terrorist groups respond to a scarce resource through a corresponding decrease in the scope of operations. A terrorist group could conduct fewer operations, less expensive operation. The terrorist group looks for alternative scope to maintain the current pace of operations, but trim costs elsewhere such as in recruiting, propaganda, and training. (Figure- 3)
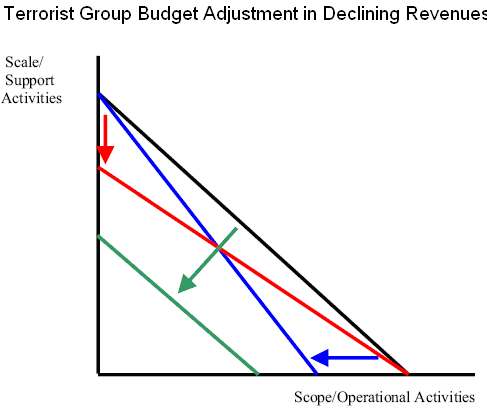
Basics Project, (2008) stated the standard economic assumptions of utility curves, any of the adjustments mentioned above necessarily lead to a loss of utility. The extremist group could respond in multiple ways if they expect to minimize such a utility loss. Al Qaeda’s use of airliners as missiles against buildings rather than as simple hijackings represents successful achievement. The extent of economic and symbolic damage and number of casualties from this different operation immensely increased the group’s utility with little cost.
The strategic doctrine and targets of Al-Qaida’s to launch attack on the United States. Al-Qaida mastermind planning against US railways after observing the economic impact of the 11 September attacks on the US airline industry. The rail or subway terminals present same attractions as airport terminal. The huge crowds help them to move freely. Al-Qaida’s preferred to use a valid passport containing a legitimate US visa. Al-Qaida has instructed operatives to travel to the United States on original passports with no indications of suspicious travel.
Basics Project, (2008) addressed that terrorist networks pose the national security threat to the United States. The greatest threat of most wanted terrorists come from the al-Qaida (AQ) network. This forum included a core al-Qaida organization and numerous confederated extremist factions. The al-Qaida network has been characterized as a “globalize insurgency”, sabotage, open warfare and terrorism. It strives to procure armaments of mass destruction and other mechanism to cause massive damage on the United States.
The objective of AQ is to overthrow the existing world order and install it with a reactionary, authoritarian and fundamentalist regime.. This intimidation and menace will be sustained over a protracted period and will require a global response to foil its move regionally and nationally decades not years.
Czwarno, M., (2006) pointed out that nineteen hijackers usurped multiple planes on September 11, 2001 and used them as an instrument to destroy the World Trade Center in New York and to attack Washington, DC. The United States took retaliation by launching war against al-Qaida. The U.S.A is using every instrument of national power such as diplomacy, intelligence, law enforcement, financial and military tools with a view to disrupt the global network. Consequently, the U.S.A has made significant strides in making America and its allies more safe and secure.
Arquilla, J., and Ronfeldt, D. (2001) stated that Al-Qaida carries out terrorist operations against US and Israeli tourists visiting Jordan for millennial celebrations. This terrorist organization launched attack in the US Embassies in Nairobi, Kenya, and Dar-es Salaam, Tanzania in 1998 killing at least 301 persons and injured more than 5,000 others. It has shot down US helicopters and killed US servicemen in Somalia in 1993 and conducted three bombings that targeted US troops in Aden, Yemen, in December 1992. Al-Qaida has masterminded plan to assassinate Pope John Paul II during his visit to Manila in late 1994.
Arquilla, J., and Ronfeldt, D. (2001) also argued that there are several thousand Al-Qaida members. It has also serves an umbrella organization for a worldwide network that includes many Sunni Islamic extremist groups. Bin Ladin, son of a billionaire Saudi family provided is said to have inherited approximately $300 million to finance the group. Al-Qaida also maintains moneymaking front organizations, receives donations from like-minded supporters.
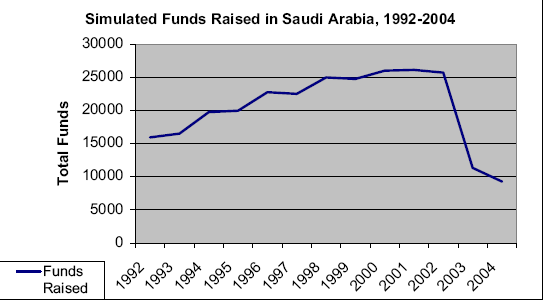
The Whitehouse (2008) pointed out that Al-Qaeda continues the war by conducting bombing attack in Riyadh on 9 November 2003. The attack killed a large number of Muslims. According to the Saudi security forces killed many al-Qaeda extremists. These actions reduce al-Qaeda’s competence as well as decrease the acceptance of al-Qaeda’s message, two of the vital variables in the simulation. A time-series of simulation depicts historical scenario of fundraising within Saudi Arabia that is reasonable. The simulation offers a total sum of money for al-Qaeda raised from 1992-2003 in figure- 4.
The U.S homeland security policy
The Whitehouse (2008) addressed the proposal of president is to establish a single department whose primary mission to safeguard the American people and their homeland. It has been emphasized on principal border and transportation security agencies; coordination a cohesive network of disaster response capabilities; dissemination of intelligence and other information pertaining to terrorist threats to safeguard America’s critical infrastructure from terrorist attack. It is integrating the existing border security and interior enforcement functions; sharing information and counterterrorism cooperation with other responsible federal agencies.
Office of Homeland Security (2008) carried out that the U.S.A suffered immensely on September 11, 2001. Since then, the President and his colleague made hard and untiring endeavor to safeguard America against another such terrorist attack. The emergence of the new Department of Homeland Security (DHS) is one of the courageous and potential steps. The new department will execute the federal government’s plan to extricate the homeland with the objective of building stronger, safe and secure America.
The National Strategy for Homeland Security was unearthed by the President on July 16, 2002. It is a massive plan for using America’s talents and resources to provide our protection and reduce our vulnerability from terrorism. The budget for the year 2004 provided unstinted supports in the homeland security policy.
The Primary Mission of homeland security policy is to prevent terrorist attacks within the United States and reduce the vulnerability of the United States from terrorism, minimize the colossal damage, and assist in the recovery from terrorist attacks within the United States. It will carry out all functions of entities to the Department regarding natural and manmade crises and emergency planning. It also ensure that the function of the agencies and subdivisions within the Department that are not related directly to safeguard the homeland and supervise nexus between illegal drug trafficking and terrorism.
After September 11th, the President acted quickly to safeguard the nation. He immediately provided $40 billion in emergency funding and created the Office of Homeland Security, to coordinate the implementation of a comprehensive national strategy to safeguard the United States from terrorist threats. Consequently, on June 6, 2002, the President proposed creating a new cabinet-level department with the primary mission of safeguarding the American people on June 6, 2002. The President signed the Homeland Security Act of 2002 creating the new department.
The American-Israeli Cooperative Enterprise (2008) addressed that the department of homeland security (DHS) upholds communication and accountability vacuum by consolidating border and transportation security arrangement. It is creating a focal point to foil terrorist move against vulnerabilities, coordinating homeland security strategy. The President and the Administration are acting speedily swiftly to address the problems of the past and highlight on protection of the American people.
The Department will put into place an organizational structure that meets the dual needs of centralized planning and decentralized operation. Headquarters will be liable for functions such as planning, policy, budgeting, strategy, integrated intelligence and analysis, integrated research and development, information technology, and legal affairs. According to the Homeland Security Act of 2002, DHS is responsible for “providing the Federal Government’s response to terrorist attacks and major disasters.
Policy Recommendations
The Whitehouse (2008) argued that it is not possible to deprive terrorist organization of raising fund. The aim of policies at disrupting terror money does not appear to be effective. The sequel of such policies is understandable. This course work analysis depicts law enforcement information; case studies and simulation lead to recommend a variety of policy recommendations. This analysis launched operations at tracking terrorist funds.
The impacts of counter finance categories can fall in four different categories:
- Decreasing supply of terror funds;
- Decreasing demand of terror funds;
- Collapsing the mechanisms which enable supply to meet demand;
- Decreasing the utility of money by increasing the obstacle, terrorist organizations have in making it accessible to those individuals who will use it for launching terrorist insurgency.
It depicts primary counter-finance policies and these policies affect. It provides assessment as to how the US and international community has sought such strategy.
The first and foremost duty of these organizations is the Financial Action Task Force (FATF). It basically created to combat money laundering. The FATF was established in 1989 in response to the G-7’s recognition of the threat posed by drug money laundering. The result was FATF’s recommendations, which include the following core suggestion.
- It needs to criminalize the laundering of criminal proceeds and enacting laws to seize them.
- It needs to obliging financial institutions to identify all clients and keep appropriate records.
- It needs to requiring financial institutions to report suspicious transactions to the appropriate national authorities.
- It had better create and put into place adequate systems for controlling and supervising financial institutions.
- It needs to emphasize on agreements to permit each financial jurisdiction to provide effective international cooperation, especially with respect to exchanging financial information and other evidence of a financial crime.
Tom, R., (2008) added that the impacts of these policies include the reactions by terrorist groups to exerting more endeavors to maintain revenue flows. These impacts are reducing scope of operations. The exploiting of these second order impacts is a significant progress regarding counter-terrorism policy.
Incomplete and unaddressed recommendations
The 9/11 Commission completed its investigation after two years and a half years since its emergence. It offered its recommendations for safeguarding U.S.A from terrorist threats. Nearly half of the recommendations have gone unaddressed. Many of the recommendations have not been effectively or fully implemented. The following report depicts the status of some of the key 9/11 recommendations.
- The limited homeland security funds are not being allocated wisely.
- The first responders do not have the tools they need to effectively respond to terrorist attacks.
- The nation’s borders remain porous and vulnerable to terrorist threats.
- The significant security gaps remain in the transportation systems.
- The information sharing remains inadequate.
- The current strategy in the war on terrorism is not effectively confronting terrorist threats.
- The initiatives to address the threat of nuclear weapons are not as aggressive as they need to be.
- The civil liberties guarantees are not being adequately balanced against national security requirements.
Assessment
The Whitehouse (2008) mentioned that the structure in which both the United States and international community approaches terrorist financing has unearthed. These two communities have achieved nominal success in foiling al Qaeda’s finances. The endeavors to disrupt terrorist financing were introduced in antiterrorism strategies. With in a short span of time, the US moved beyond its state-centric approach to terrorist financing in 1995. All terrorist groups had diversified their revenue streams beyond exclusive state financing. Realizing the vulnerabilities of keeping assets in the international banking system, al Qaeda mobilized its assets into other areas shortly.
The voluminous funds seized after 9/11 were seized within the first three months after President Bush’s directive (see Figure- 5).
Office of Counterterrorism, (2005) mentioned that there has been indication that $136 million in terrorist funds have been seized since 9/11. The claim of seizing $136 million is technically true, it is not authentic. This figure depicts that the total amount of new funds permanently denied to organizations connected with terrorist groups since President Bush issued EO 13924 is less than $50 million that was a negligible amount.
Conclusion
Various dissident groups’ adopt strategy of attacking by targeting its assets. The new information system has developed regarding both the target and the strategy’s ability to wield influence the target. It would enable policy analysts and policymakers to be fully aware of changes within the greater terrorism phenomenon. Al Qaeda’s financial infrastructure has shown an impressive ability to adapt to adverse conditions.
It will take advantage of available opportunities; pursue creative, non-traditional and unorthodox methods of money management. It geographically launches operations to areas where laws are non-existent. The expanded international endeavors to foil those financial networks face the great challenge for Al Qaeda. It has been portrayed the terrorist activities of Palestine Islamic Jihad (PIJ) especially on Al-Qaida in the Islamic Maghreb (AQIM) in this assignment. We highlighted on U.S. homeland security policy and how to extricate international community from Islamic terrorist militants.
Bibliography
Arquilla, J., and Ronfeldt, D. (2001), Networks and Netwars: The Future of Terror, Crime, and Militancy. Web.
Algiers Le Jeune (2006), Algerian Security Forces Break Up ‘Major’ Terrorist Support Network in Boundaries, FBIS report, Independent.
Breinholt, J. (2004), Counterterrorism Enforcement: A Lawyer’s Guide. Columbia, SC: Office of Legal Education.
Basics Project, (2008), Terrorism. Web.
Czwarno, M., (2006), In the Spotlight: Organization of Al-Qaida in the Islamic Maghreb. Web.
Office of Counterterrorism, (2005), Fact Sheet: Foreign Terrorist Organizations (FTOs). Web.
Office of Homeland Security (2008), Fact Sheet: Third World Traveler. Web.
Office of Homeland Security (2002), National Strategy for Homeland Security. Web.
Office of the Press Secretary, (2001), Executive Order Establishing Office of Homeland Security. Web.
James J, C., (2004), Department of Homeland Security Needs Under Secretary for Policy. Web.
Strategic Forecasting Inc, (2007), Algeria: The GSPC Fingerprints on the Oct. 30 Bombings. Web.
Steve K., (2005), Financing Terror an Analysis and Simulation for Affecting Al Qaeda’s Financial Infrastructure. Web.
The American-Israeli Cooperative Enterprise (2008), Fathi Shiqaqi. Web.
The Whitehouse (2008), Retroactive Liability Protection Is Critical to Our National Security. Web.
Tom, R., (2008), Department of Homeland Security. Web.