Introduction
Context of the Policy Problem
Centralization of big data has become a major trend in many developed economies as they move towards improving data security and effective sharing of intelligence among security organs, especially in major airports like Dubai International Airport that has annual traffic of 86.4 million passengers (Verhoeven 2018, p. 26). The shift towards the digital data has proven to be a more efficient way of enhancing national security.
The shift has made it easy for security organs to process and share data within a short period (Younies and Tareq 2020, p. 3). However, such changes can only be successful if the government puts in place data policies that can support the same. The rapid digitization can also influence data policy for national security, especially when the government realizes that there is an urgent need for change. In this paper, the aim is to analyze the impact of digitization on data policy for national security in the United Arab Emirates, specifically focusing on the correlation between digitization, cyber-security, and artificial intelligence (AI).
Definition of the Policy Problem
Rapid digitization has been seen as one of the best ways of enhancing national security in the country. Nurkin and Rodriguez (2019, p. 77) define digitization as “the process of converting information into a digital or computer-readable format”. Traditionally, intelligence report and other data would be recorded in paper and stored in physical files. Digitization offers national security agencies opportunity to share information irrespective of their location in the country. It has also redefined data policies in the country as the government is keen on moving to the new platform. The aim of the digital participation policy is to define rules and regulations in the use of digital participation tools.
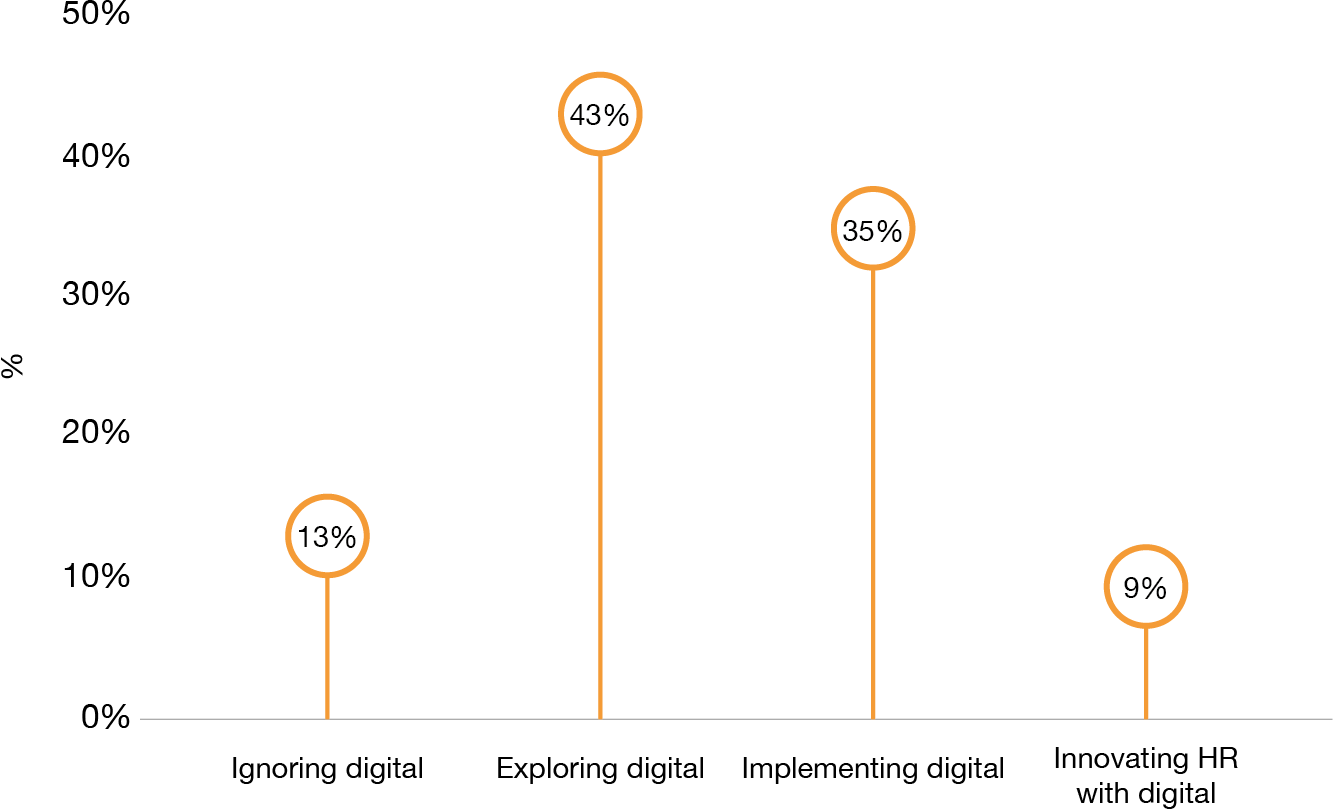
The rapid digitization has had a major impact on data policy for national security in the United Arab Emirates, which will be assessed in this study. It is also necessary to investigate the correlation between digitization, cyber-security, and artificial intelligence (AI). Figure 1 below shows that there is still a major gap in innovating HR with digital. However, a significant population is willing to explore and implement digital technologies.
Purpose of the Policy Paper
The purpose of this policy paper is to assess and discuss the impact of rapid digitization on data policy for national security in the UAE, focusing on the correlation between digitization, cyber-security, and artificial intelligence. The government enacted policies and provided relevant resources to make it possible for security agents and organizations to shift from the use of traditional methods of data management to the digital platform as a way of enhancing instant data sharing and analysis towards strategic decision making for all UAE Federal agencies (Government of Dubai 2017, p. 1).
Digital participation policy is an example of the policies that the government has introduced to help improve data sharing and management among security agencies. Despite the obvious benefits of digitization, it is also possible that the rapid pace at which the process has taken may have negative impact. An example of a negative impact is the inability of individual security agents to operate effectively under the new system (Sari 2019, p. 68). The paper will discuss the policy options that can be embraced in the country.
Methodology
When planning to conduct a research, it is necessary for one to define the methods that will be used to collect and process data from various sources. In this study, the researcher intends to use secondary data sources. Information will be obtained from books, journal articles, and reliable secondary sources. The study will heavily rely on online databases to access the materials needed in the study. In this qualitative study, the researcher will conduct an explanatory case study.
As Romaniuk and Manjikian (2021, p. 91) observe, this type of data analysis makes it possible to explain cause-effect relationship, which is needed in this case to determine the impact of digitization on data policy for national security. The strategy will help in comparing the current trends and practices in the country with that of other countries which have been successful in enacting data policies for national security.
Limitations of the Study
It is important to identify limitations of this study and how each was addressed. One of the biggest limitations in the study was the scarcity of information on the issue being investigated. Most of the available sources focused on western economies. Having limited information on this issue affects various section of this Capstone, such as evaluation of policy options. The research would have benefited from abundant literature by making references to policy suggestions that other scholars have made. The recommendation section also had to rely wholly on the data that the researcher was able to obtain from the sources identified above.
Problem Description
Background of the Problem
The UAE government has invested a significant amount of money to help improve the security of its cyberspace. It has put in place critical infrastructure to enable it tackle any upcoming threats due to shortcomings in data policy formulation. Davis (2021, p. 133) notes that the government understands that the current policies are not as effective as would be desired when it comes to protecting various government departments from any external online-based attacks. Currently, the UAE relies on data policies enacted before the transformation was made (Ali et al. 2019, p. 2805). For instance, one of the major current data policy in the UAE states that national security data is expected to flow in a strict chain of command, from top to bottom and back (Younies and Tareq 2020, p. 4). There is a policy gap on how different officers of varying cadre should share critical data that can enable them to effectively respond to security threats.
Recent incidences have been reported of cyber-attacks, which specifically target the oil and gas industry, the most critical industry to the country’s economy. In 2018, these criminals used Shamoon 3, a malware known to wipe data, to attack Saipem, which is the technology vendor of Saudi Aramco. The goal was to steal from Saudi Aramco by manipulating its data in favor of some of its clients working with these criminals. Studies have estimated that the GCC region is losing more $835 million every year to these criminals who have perfected their online attacks. They are also compromising the national security, which means that it is necessary to embrace new strategies and policies regarding digital data management (Langendorf 2020, p. 5).
These events have led to various policy changes in the UAE as the government is keen on protecting its critical infrastructures. One of the policy changes formulated to deal with the rapid digitization is the hiring of experts from the west, especially the United States. For a long time, the UAE government did not trust experts from the west, fearing that they could be intelligence officers working for their governments (Hartzog 2018, p. 18).
However, that perception is changing, and the government is embracing the idea of hiring these highly skilled experts to help protect its data infrastructure. Another policy change is the strategy of using offensive attacks against known threats instead of just remaining on the defensive. The government has been using its experts to enable it infiltrate criminal gangs and have access to information regarding their activities as a way of reducing the threat of attack.
Artificial intelligence offers solution to most of these security challenges that the federal government is facing. The simulation of human intelligence in machines makes it possible for computers to go beyond simple processing of data (Harvard Business Review 2019, p. 12). It allows these machines to think as humans when analyzing data, providing accurate forecasts and offering various alternative solutions based on information that it has. AI has made it possible for security agents all over the world to identify possible security threats, especially when an individual or a group of people have been classified as being more likely to engage in crime (Cappello 2019, p. 81). It provides rational decisions, providing possible solutions to a given problem, ranked based on their suitability
The rapid digitization, especially the shift towards the use of AI, has had a major impact on the UAE national security. It is evident that moving to the digital platform has enhance the ability of officers to share data and act upon it with greater efficiency. AI makes it easy to process data and make critical decisions that enables federal government officers to tackle cyber-security issues and other threats to national security (Verhoeven 2018, p. 39).
Strategic changes that have been witnessed in the security management at major airports in the country, especially the Dubai International Airport demonstrates some of the benefits of the shift towards the use of AI. Cappello (2019, p. 127) explains that local security agents at this airport can easily share intelligence with their counterparts in other parts of the world to help fight various forms of security threats. Andrews et al. (2019, p. 5) emphasize the fact that airports have benefitted a lot from this initiative. It has become difficult for extremists and criminals to pass through major airports in the country because their identity will be revealed and arrest made before they expose others to danger.
Despite these obvious benefits of digitization and artificial intelligence in enhancing national security and fighting cyber-attacks, there has also been challenges with the new system. Brooks et al. (2018, p. 56) argue that the digitization of data was embraced with enthusiasm by most of the stakeholders, but they failed to take into consideration various policy options that would directly affect its implementation. Understanding these challenges makes it possible for the government develop ways of making this digitization process a success. To help keep pace with rapid digitization the report suggests 3 policy options as discussed in the section below.
Problem within its Current Policy Environment
The policy that introduced digitization of information management within the national security system in the country was well received among stakeholders. However, one of the issues that soon emerged within the current policy environment is cybercrime. As data moved from traditional platforms, criminals changed their approach to targeting security organs. In a report released by the UAE’s National Cyber-security Strategy, it is estimated that the cost of data breach in 2017-2018 was more than 3.9 million dollars (Sanad 2020, p. 2).
These cybercriminals use sophisticated strategies to have access to confidential information in the databases of security agencies for various reasons. Some have the goal of accessing the information about security operations in the country and selling it to extremists or criminals who may need the same. Others gain access to these databases with the aim of accessing information and distorting the data by deleting some information or adding irrelevant data with the aim of achieving specific goals.
A report by CIA illustrates the threat that extremists pose to cyber security, especially when policies and digital data infrastructure are weak. Soesanto (2020, p. 3) argues that the use of cyber technologies to conduct disruptive and destructive militant operations in cyberspace to create fear and violence in the pursuit of political change is becoming common. The rapid digitization that has been witnessed in the country’s public sector may face major challenges because of policy issues.
The process has been going on in the developed economies for about two decades, especially in the United States and European countries. However, the migration in the UAE has been in on going for less than a decade. It means that its policy environment and the digital infrastructure is still weak, making it vulnerable for attacks by extremists within the region and those in the international community. Such attacks may have devastating consequences on both the public and private sector players.
Cyber security has continued to be a major impact that the rapid digitization has had on the UAE’s national security. The government had the resources to put up the new system within the shortest period possible. However, its human resource was not adequately prepared to make that sudden shift within the shortest period possible. It was not easy for some of these officers to shift from using papers and physical files to record and store data to the new digital platform. With time, they came to understand the process and how they could process and share data. However, many of them still find cyber-security to be a relatively new concept.
A study by PricewaterhouseCoopers gives a detailed explanation and examples of the weaknesses in data digitization within the Middle East as regional countries make the shift. The report indicates that “the survey responses showed a lack of awareness of the emerging technologies that exist, and their potential impact on businesses, beyond automation and cost reduction” (PricewaterhouseCoopers 2020, p. 8).
Most of those who are expected to implement these policies believe that the digitization is meant to improve efficiency through data automation. They fail to understand the fact that there is a security threat that they need to know how to manage. The problem also affects those who are at the top level of policy management. They have failed to understand the fact that digitization goes beyond putting in place the needed infrastructure.
As such, policy issues have largely been ignored, creating a gap that criminals can exploit. Some of the laws and regulations which have been put in place in the country cannot effectively address this issue. Some of these cybercrimes are not clearly defined in the existing laws, making it difficult to punish these criminals effectively (Coulthart, Landon-Murray, and Van 2019, p. 86). It is taking long for the government to develop effective legislations that can help in combating this problem.
Most of these criminals operating in the cyberspace are techno savvy individuals who have great knowledge on issues about digital data. On the other hand, most of the officers handling data in the country are security experts with limited knowledge about digital data management (Langendorf 2020, p. 9). The knowledge gap has made it easy for these criminals to target security agencies and have access to critical information that may compromise national security. The government has increased its expenditure on training of individuals involved in managing of data. However, the rapid shift means that it may take some time for these individuals to understand and effectively operate under the new system, which puts government entities and large companies at risk of major attacks.
The attack on Saudi Arabian Oil Company, popularly known as Saudi Aramco, illustrates the threat that the major companies face as the country embraces digitization of data. In August 2012, the company, which produces 10% of the global oil supply, experienced a major cyber-attack when criminals used Shamoon virus that damaged more than 30,000 computers responsible for controlling various operations (Rashad, 2020, p. 2).
The goal of these criminals was to paralyze operations of this giant firm, which they partially succeeded. It took a while for the government to respond to the threat and restore operations at the company. The report shows that the government has been unable to punish criminals involved in the attack. It has not been easy tracking the culprits because of the inadequate counter-attack digital infrastructure that was in place at that time. At the same time, policies that were in place had not envisaged such a major attack happening to one of the most important infrastructure in the country (Faruqui 2017, p. 55). It has created an environment where security organs are not aware of the best response that they need to take following this attack.
The Arab Spring also had a major effect on data policies for national security in the UAE although the country was not directly affected by the revolt. The government realized that it needed to redefine its policies, taking into considerations concerns of the masses and internal civil disobedience (Hartzog 2018, p. 21). It created a need to have a delicate balance between national security and the need to be seen as a government that is committed to serving its citizens.
When enacting new data policies, the government developed a unique interest to monitor and understand emerging public concerns. Of great interest has always been to identify specific factors that define public discourse and how they can influence national security and general political stability in the country (Chakraborty 2020, p. 77). These steps have helped in transforming the approach to intelligence gathering and sharing among security agencies in the country. New policies currently emphasize the need for these agencies to identify major threats to national security and to make reports to the relevant agencies with the aim of averting any civil strife.
Policy Options
The Supreme Council of National Security has the responsibility of ensuring that the shift that has been made from traditional to digital platforms of data management is a success. Challenges discussed above have the potential of crippling operations at various security organs across the country. Criminals may have the capacity to have access to intelligence that may compromise national security. It is necessary to have policy options that will enable these organs to achieve their mandates in the most effective way possible.
Framework of Analysis
The analysis framework of the challenge that the Supreme Council of National Security should be based on the impact of digitization. The researcher suggests that the analysis should first assess the impact of rapid digitization on data policy for the UAE, explaining the correlation between digitization, cyber-security, and artificial intelligence. It is less likely that the government may reconsider moving back to the traditional approach of managing data (UAE Government 2011, p. 1). As such, it is necessary for the federal security agencies to find effective ways of addressing policy gaps to enhance the implementation of the new system.
Using a framework for analysis will help define the relationship among rapid digitization, artificial intelligence, and cyber-security, and how their implementation relies on effective policies set by the federal government. As Wade (2019, p. 3) explains, the rapid digitization has led to the emergence of AI, which is seen as a more effective way of managing data and using it to make accurate predictions. Using AI enables security agents to predict and identify potential national security threats. Activities of cyber-criminals can be tracked in real time, allowing security agents to accurately predict their possible goals. Actions can then be taken to ensure that activities of these criminals are halted in time before they can launch their attack. It means that AI provides an effective way of enhancing cyber-security.
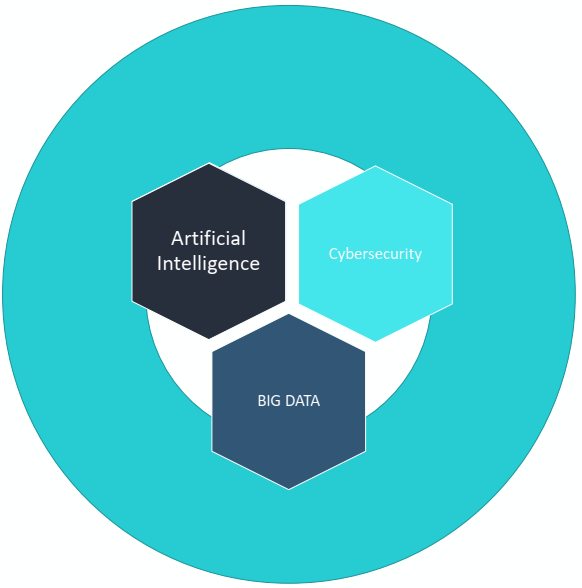
Figure 2 below shows the correlation between big data, artificial intelligence, and cyber security. Teoh and Mahmood (2017, p. 4) explain that the growing relevance of big data has led to the emergence of artificial intelligence. The increasing centralization of data using sophisticated machines has made it possible to make quick decisions on issues about the national security. Highly advanced computer programs (AI) are now used to make decisions and predictions when fighting security threats. Once they are fed the data, they have the capacity of making accurate predictions and decisions regarding a given threat (Urbach and Röglinger 2019, p. 141). Law enforcement agencies can then use the information to act accordingly.
In the UAE, cyber-attacks have continued to be a major cause of concern to the government. Big data worsened the problem because it became easy for cybercriminals to target the centralized data and obtain a wide range of information that compromises national security. However, the emergence of AI is promising to solve this problem. The fact that these complex computers can monitor activities of these criminals and predict their objective and possible actions makes it easy to counteract them before they threaten the national security (Gartner 2020, p. 22). As such, it minimizes the threat and empowers security agencies to be proactive. The digital footprint that these criminals leave behind is captured by the AI, making it easy to trace and arrest these criminals.
Evaluation of Policy Alternatives
The rapid digitization has had various impacts on the UAE National Security. As the assessment above shows, the transformation has improved the ability of security agencies to manage and share important information. However, it has also led to the emergence of some challenges that must be addressed to enhance the ability of security organs to achieve their mandate. When developing evaluation policy alternatives, it is important to develop criteria upon which the chosen policy problem will be analyzed. The criteria will include the effectiveness and sophistication of the policy option, its financial viability, availability of technical knowhow and relevant infrastructure, and the likelihood of government officials accepting it. The following are the criteria that should be considered.
The first criterion focuses on the effectiveness and sophistication of the policy option. The selected option should be effective in terms of addressing a specific weakness identified with the current policy. For instance, lack of clearly articulated laws and regulations were identified as a major concern that should be addressed based on the discussion above. The policy option should be capable of addressing this specific problem (Organisation for Economic Co-operation and Development 2019, p. 53).
In terms of sophistication, the policy option should articulate these solutions in a way that is in line with the changing environmental forces and threats. The case of Saudi Aramco attack, discussed above, demonstrated how lack of proper legislations and policies can inhibit the fight against cyber-attacks. The first policy option discussed below will satisfy this criteria to a great degree.
The second criteria focuses on financial viability, which the policy options must satisfy to a high level. When proposing a solution to the current problem, policy-makers must put into consideration the financial capacity of the relevant agencies expected to implement it. For instance, a weak digital infrastructure was identified as a major concern that needs to be addressed. Stanzel (2019, p. 56) explains that one of the common challenges that many countries face is trying to adopt practices that are successful in the western countries without taking into consideration the financial capacity to implement them effectively.
The availability of technical knowhow and relevant infrastructure are some of the important criteria identified above that should be observed. The criteria should be met to a medium level because the country is just making the shift and is likely to encounter challenges in finding experts locally. When enacting data policy for national security, policy-makers should ensure that those who will be responsible for the implementation have the technical capacity (United Nations Conference on Trade and Development 2019, p. 44). Although there may be the temptation to use a blueprint that has proven successful in other countries, care should be taken to assess the local capacity first.
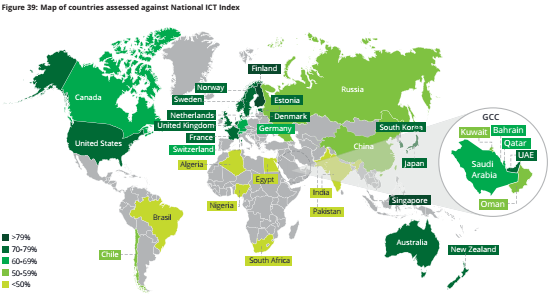
A case study of the application of big data and AI in Singapore may help in determining how the same can be applied locally. As shown in figure 3 below, Singapore has one of the most advanced national ICT indexes in the world. It has created a system where closed-circuit television (CCTV) cameras can easily identify a criminal in the streets and predict their possible intention (Deloitte 2017, p. 65). Facial data of all criminals are stored centrally.
Through AI, the machines can recognize a face of a past offender, monitor their actions, make predictions about their possible intentions, and alert relevant authorities for appropriate action to be taken. It is advisable to take officers and all the stakeholders who will be involved in the data management through some form of training. The data management infrastructure should also be improved to meet the expected standards based on the goal that should be achieved. As Stanzel (2019, p. 37) observes, before enacting a new data policy for national security, the policy-makers should ensure that the government is willing and capable of providing the relevant resources that will be needed for the implementation.
The likelihood of government officials accepting it based on the current foreign policies has been identified as another criterion that has to be considered when identifying policy alternatives. According to Chakraborty (2020, p. 43), one of the most defining factors when developing data policy for national security is the ability to protect critical information that can be accessed by intelligence agencies. There is always the fear that the Central Intelligence Agency of the United States, Federal Counterintelligence Service of Russia, the Mossad of Israel or any other intelligence or counterintelligence agency may access critical information that may compromise the UAE’s national security.
Foreign policies that the country has embraced will also define the policy alternative. The UAE currently enjoys a strong bilateral cooperation with the United States on a wide range of issues, from trade, energy policies, and cultural exchange to defense, law enforcement, and non-proliferation (United Nations Conference on Trade and Development 2017, p. 50). The government, through the Supreme Council of National Security, has various policy alternatives that can enable it to deal with this problem.
Policy Alternative 1: Decentralize Data and Empower Local Officers
The first policy alternative is to decentralize data that allows officers to access information they need within the shortest time possible without having to wait for approval from the central command unit. This policy will ensure that law enforcement officers can act swiftly to deal with any security threats. This policy will require local officers to be trained on how to manage data in online platforms without leaving footprints that criminals can use to trace their activities and launch attacks. This alternative will involve training these officers while they are on job. Relying on services of top cyber-security companies such as that of Palo Alto Networks may be needed if this alternative is chosen.
These firms have worked closely with government agencies and large multinational corporations around the world to ensure that digital data is protected from various forms of threat (Thouveninet al. 2018, p. 28). They can help local officers to gain more knowledge about detecting and responding to various forms of cyber threats.
Policy Alternative 2: Empowering Locals through Advanced Education
Another policy alternative recommended for the government would be to invest in furthering the education of a section of the officers in local and international institutions of higher education. The government should consider sponsoring their education so that they can gain technical knowledge needed to protect data in various security organs around the country. Local institutions of higher learning offer a wide range of courses that can equip students with the right skills needed to manage digital data.
However, the government can consider sponsoring a small team of talented officers to seek further education abroad in institutions such as Massachusetts Institute of Technology (MIT), Stanford University, or University of Cambridge which are known for their high standard in technology-related courses (Thouveninet al. 2018, p. 83). Once trained, these officers can then assist local law enforcement agencies to work effectively under the new system. As Efthymiopoulos (2016, p. 7) suggests, major shifts in operations within the security sector should always be conducted in a systematic way.
Policy Alternative 3: Enact Policies That Allows Expatriates to Work in Local Security Agencies
The third alternative would be to hire foreign experts to work alongside local law enforcement agencies and communication officials. Foreign policy changes witnessed over the recent past means that the government has become more trusting than before towards foreign experts, especially from the west (Chakraborty 2020, p. 87). As such, the government may opt to install these foreign experts in different government departments to help protect data infrastructure. During that period, they will also be equipping local officers with necessary skills that can enable them to detect and neutralize any form of security threat.
When this option is considered, it is important to ensure that these foreign experts do not compromise the country intelligence and counterintelligence agencies. The interest of these foreign officers should be to help strengthen the capacity of the local forces to manage national security without leaking critical information to foreign nations or organizations that may pose a threat to the country’s security (Thouveninet al. 2018, p. 59). As such, it is advisable to work with specific reputable agencies that can be trusted with critical information.
Conclusion and Recommendations
The United Arab Emirates, just like many other countries around the world, is embracing the concept of data digitization. Emerging threats posed by cybercriminals and techno savvy extremists has forced security agencies to embrace new ways of collecting, processing, storing, and sharing of data. Such a strategy helps in detecting, monitoring, and neutralizing threats that may emerge in the country. Dubai International Airport has emerged as one of the most sensitive installation in the country that is used by tens of millions of people every year, making it one of the major targets of these criminals (Thouveninet al. 2018, p. 98).
Other installations and infrastructural developments also needs effective security system that can thwart any form of threat that may emerge. In this section of the report, the focus is to provide a synthesis of major findings, a set of policy recommendations, and concluding remarks.
The researcher recommends the first policy option that will allow the government to decentralize data and hire foreign experts to help in empowering the local talents. These experts will be responsible for the initial implementations and they will be training the locals in the process. This option will require the government to redefine its employment policies to be friendly to expatriates with the necessary skills. The main disadvantage of this option is that it may be expensive to implement. It may also mean that the country will have to rely on foreigners for some time until the locals are empowered. However, it is less time consuming and effective in facilitating the digitization process.
Synthesis of Major Findings
Centralization of big data is the new norm that is gaining popularity in various countries around the world. However, the study shows that effective implementation of such an initiative requires proper data policies. The government of the UAE has embraced rapid digitization of data as a way of improving national security. For a long time, security agencies relied on traditional methods of data collection and management. These traditional methods have proven to be less effective when dealing with modern threats to national security. In highly sensitive places such as the airport, it has become critical to have real-time data that can help detect and effectively neutralize any form of threat. The analogue approach significantly minimized the ability of security officers to have access to information that would enable them effectively fight criminals.
The shift to the digital data, especially the centralization of big data, has been a major breakthrough in addressing various weaknesses that the previous system had. It has created a system where the Signals Intelligence Agency (SIA) can collect sensitive data, process it, and provide intelligence to various security agencies across the country in real time (Hartzog 2018, p. 32). The ability to share critical information has been considered as one of the best ways of neutralizing threats, especially in an era where radicalization is becoming a major problem around the world. The government has continued to invest in this digitization efforts through training of its officers in the security sector, improving the infrastructure, and working with various foreign agencies to improve the digitization and centralization of data.
The UAE made the move to digitize its data, but the analysis shows that the current data policies on national security are generally weak. It is still unclear how the country intends to work with friendly western powers such as the United Kingdom and the United States to strengthen its digital data platforms (Thouveninet al. 2018, p. 74). There has been some form of corporation, but the analysis shows that these partnerships are not based on solid national policies. For example, while SIA has been keen on recruiting individual cyber-security experts from the United Kingdom, the same agency has developed a close working relationship with the American CIA (Chakraborty 2020, p. 29).
Such an arrangement shows that the government is still unclear whether it needs to use individuals or government agencies of these foreign nations. The best strategy of equipping and empowering local security and intelligence agents also remains to be a policy issue. The government has invested a significant amount of resources in recruiting foreign experts to work with local officers as a way of creating capacity (Faruqui 2017, p. 78). In other cases, it has sponsored some of these agents to pursue further education in foreign institutions of higher education as a way of empowering them.
Set of Policy Recommendations
The strategic move to centralize big data as a way of enhancing national security in the UAE has helped in general improvement of security in the country. However, it is important to note that it has also had a major impact on data policy for national security. The government has been forced to adjust its national security policies to reflect these new changes (Hartzog 2018, p. 48). The goal has been to address emerging weaknesses with the current system while at the same time developing capacity in the local agencies to ensure that they can operate effectively in detecting and neutralizing any form of threat to national security. The following is a set of policy recommendations that stakeholders should consider to ensure that they can achieve these goals.
Decentralizing decision-making while centralizing big data to eliminate bureaucracy and improve efficiency. The current decision of centralizing big data may create the impression that decision-making should be centralized as well. However, Stanzel (2019, p. 115) warns that centralizing decision-making may compromise the ability of individual agencies to make quick actions to neutralize threats once detected. As such, while big data is centralized, decision-making should be left to individual agencies so that they can act accordingly based on the issue that they are facing. The government should enact a policy that would empower each of these individual security organs in their own jurisdictions.
For instance, once Dubai National Police receives intelligence from SIA, it should have the capacity to act accordingly and within the shortest time possible to address the threat based on the information provided. As Stanzel (2019, p. 90) explains, decentralization of decision making in the national security sector does not mean each agency should ignore commands from higher authorities. It involves allowing each individual units to act accordingly and in a timely manner to address a threat, unless it is necessary to wait for the approval of a higher authority.
Policies on cooperation with foreign nations in battling common security threats within the region and internationally will be needed. According to Chakraborty (2020, p. 60), cooperation among different states within a given region require trust and the desire to address a common problem. However, sometimes it may not be easy to develop the needed trust. The UAE has had a diplomatic row over the recent past because of foreign policies that each has embraced (Faruqui 2017, p. 108).
Both countries are members of the GCC and share a naval border. It means that they face common security threats, especially from regional extremists. However, their ability to work as a unit to address these problems is compromised because of the mistrust. The government may need to redefine its policies to ensure that the two countries can work together to address security concerns under the new digitized data management system.
The government will need to enact policies that will define how to fund big data centralization and artificial intelligence (AI) integration. As discussed above, the government initiated rapid digitization of data to enhance operational activities in national security agencies (Hartzog 2018, p. 51). It is necessary to have clearly defined policies on how to fund different activities such as training of the personnel, improving the infrastructure, and effective collection of data from various sources. This policy will eliminate the problem of underfunding this department at a time when it expects to modernize its operations.
Concluding Remarks
The government of the UAE has promoted rapid digitization of data in its national security sector. The initiative is meant to improve intelligence gathering and sharing of critical information to enable various security organs to act accordingly. It is viewed as a major shift from traditional methods and effective way of dealing with emerging threats to national security. However, the paper shows that the rapid digitization has had a major impact on data policy for national security. The government has been forced to redefine its policies to reflect these new strategies and to address weaknesses identified with the system.
Policy-makers should remain flexible and responsive to the changing forces that define national security. The three policy options are effective in addressing different problems identified with the current data policies in the country. However, decentralizing decision-making while centralizing big data to eliminate bureaucracy and improve efficiency should be given priority because it addresses most of the current problems.
Bibliography
Ali, Iman, Geetanjali Chandra, and Bhoopesh Sharma. 2019. “UAE‘s Strategy Towards Most Cyber Resilient Nation.” International Journal of Innovative Technology and Exploring Engineering 8 (12): 2803–9. Web.
Andrews, Whit, Bern Elliot, Jim Hare, and Anthony Mullen. 2019. “Pursue a Pragmatic Center of Excellence to Boost Your Artificial Intelligence Strategy.” Gartner.
Brooks, Charles, Christopher Grow, Philip Craig, and Donald Short. 2018. Cybersecurity Essentials. Hoboken, NJ: John Wiley & Sons.
Cappello, Lawrence. 2019. None of Your Damn Business: Privacy in the United States from the Gilded Age to the Digital Age. Chicago, IL: The University of Chicago Press.
Chakraborty, Utpal. 2020. Artificial Intelligence for All. New Delhi: BPB Publications.
Coulthart, Stephen, Michael Landon-Murray, and Puyvelde Van. 2019. Researching National Security Intelligence: Multidisciplinary Approaches. Washington, DC: Georgetown University Press.
Deloitte. 2017. “National Transformation in the Middle East A Digital Journey.”. Web.
Davis, Elizabeth. 2021. Shadow Warfare: Cyberwar Policy in the United States, Russia, and China. Lanham: Rowman & Littlefield.
Efthymiopoulos, Marios-Panagiotis. 2016. “Cyber-Security in Smart Cities: The Case of Dubai.” Journal of Innovation and Entrepreneurship 5 (1). Web.
Faruqui, Ahmad. 2017. Rethinking the National Security of Pakistan: The Price of Strategic Myopia. London: Taylor and Francis.
Gartner. 2020. “To Transform, Government.” In Gartner EMEA Symposium. Gartner.
Government of Dubai. 2017. “Dubai Cybersecurity Strategy.”. Web.
Hartzog, Woodrow. 2018. Privacy’s Blueprint: The Battle to Control the Design of New Technologies. Cambridge, Massachusetts: Harvard University Press.
Harvard Business Review. 2019. Cybersecurity : The Insights You Need from Harvard Business Review. Boston, Massachusetts: Harvard Business Review Press.
Langendorf, Manuel. 2020. “Digital Stability: How Technology Can Empower Future Generations in The Middle East.” Ecfr.Eu. Web.
Nurkin, Tate, and Stephen Rodriguez. 2019. A Candle in the Dark: US National Security Strategy for Artificial Intelligence. Washington, DC: Atlantic Council of the United States.
Organisation for Economic Co-operation and Development. 2019. Going Digital: Shaping Policies, Improving Lives. Paris: OECD Publishing.
PricewaterhouseCoopers. 2020. “Digital HR Survey 2020: Challenges and opportunities for Middle East companies.” PWC Middle East. Web.
Rashad, Marwa. 2020. “Saudi Aramco Sees Increase in Attempted Cyber Attacks.” U.S. News. Web.
Romaniuk, Scott, and Mary Manjikian. 2021. Routledge Companion to Global Cyber-Security Strategy. London: Routledge.
Sanad, Jamal. 2020. “How the UAE Faces Its National Security Challenges.” Gulf News. Web.
Sari, Arif. 2019. Applying Methods of Scientific Inquiry into Intelligence, Security, and Counterterrorism. Hershey, PA: Information Science Reference.
Soesanto, Stefan. 2020. “Cyber Terrorism. Why it Exists, Why it Doesn’t, and Why it Will.” Elcano Royal Institute. Web.
Stanzel, Volker. 2019. New Realities in Foreign Affairs: Diplomacy in the 21st Century. Baden-Baden: Nomos Verlagsgesellschaft mbH & Co. KG.
Teoh, Chooi Shi, and Ahmad Kamil Mahmood. 2017. “National Cyber Security Strategies for Digital Economy.” Journal of Theoretical and Applied Information Technology 95 (23). Web.
Thouvenin, Florent, Peter Hettich, Herbert Burkert, and Urs Gasser. 2018. Remembering and Forgetting in the Digital Age. Cham: Springer.
UAE Government. 2011. “Vision 2021 and Emiratisation.” UAE. Web.
United Nations Conference on Trade and Development. 2019. Digital Economy Report 2019: Value Creation and Capture: Implications for Developing Countries. Geneva: United Nations.
United Nations Conference on Trade and Development. 2017. Investment and the Digital Economy. New York, NY: United Nations.
Urbach, Nils, and Maximilian Röglinger. 2019. Digitalization Cases: How Organizations Rethink Their Business for the Digital Age. Cham: Springer.
Verhoeven, Harry. 2018. Environmental Politics in the Middle East: Local Struggles, Global Connections. New York, NY: Oxford University Press.
Wade, Gordon. 2019. “UAE: Cybersecurity Regulations and Their Impacts.” One Trust Data Guidance. Web.
Younies, Hassan, and Tareq Na’el Al-Tawil. 2020. “Effect of Cybercrime Laws on Protecting Citizens and Businesses in the United Arab Emirates (UAE).” Journal of Financial Crime. Web.