Procedures for an Upgrade of VMware Tools
According to McCain (2010), the method for upgrading VMware Tools varies between Windows and Linux guest operating systems. It is important to note that upgrades are done either manually or automatically. Besides, Windows “virtual machines are configured to notify you when upgrades that are installed by selecting VM>Upgrade to upgrade the virtual machine, are available” (McCain, 2010, p.2).
It is crucial to understand that the update process cannot be stopped or reversed once it starts. In summary, the entire procedure is summed up in powering the virtual machine to install and upgrade the VMware Tools. All menus commands must be selected and used properly.
Converting a Physical Machine (PC) to a Virtual Machine using VMware vCenter
The procedure involves ensuring that the virtual machine’s infrastructure for accommodating the new machine and the physical machine to be converted are both available (Mishchenko, 2010). To start the conversion process, turn on the conversion wizard by first selecting and configuring the hardware and software of the physical machine to and by creating a destination folder to house the new virtual machine. Configuration is necessary to achieve the desired hardware and software behavior. Ensure that all windows and Linux environment prerequisites are followed.
Procedures for creating a vApp
The process includes firing a new vApp wizard to start building the new vApp. It is important to use a new name for the just created vApp (McCain, 2010). The next step includes running the software after all the necessary preparations have been done successfully. McCain (2010) notes that establishing the destination folder and assigning resources such as the CPU, and memory to complete the steps enables one to create the necessary environment for the new application.
However, once the new vApp has been established, it must be populated with new vApp elements. It is important to add the new name to the ‘Name and Folder’ page to distinguish it from other vApps. Ensure that you click next when each configuration and naming is through to continue to the next step. The destination folder is only selected on a standalone host cluster. However, ensure that the target folder is validated so that the creation and installation rules are adhered to.
Procedures for Cloning a vApp
The cloning process depends on the status of the deployment situation of the vApp. The prerequisite is to ensure that a connection is established between the vCenter Server system and the vSphere client (McCain, 2010). Also, ensure that the ESX 3.0 provides an environment for a running inventory for the host machine. Select the host list using the clone wizard and ensure that the clone wizard is properly configured. Identify the destination address by selecting the host and clicking next for the installation to occur. Assign it with a name and complete the clone.
Procedures for Configuring IP Tools
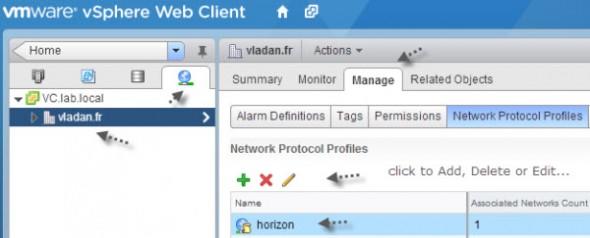
Different methods are used to configure the IP Tools on vCenter depending on the operating system environment (McCain, 2010). The procedure includes specifying the range of IPv4 and IPv6 addresses in the IP pool at the Datacenter level using the method, Home > Networking > Manage > Network Protocol Profiles on the Windows operating system.
The IP pool enables one to select the range of addresses required to be used. Ensure that a configuration for port group association is done by associating the IP pool correctly to allow for the use of built-in vCenter server to configure the tools as shown in figure 1 below.
References
McCain, C. (2010). Mastering VMware Infrastructure 3. J New York: John Wiley & Sons.
Mishchenko, D. (2010). VMware ESXi: Planning, Implementation, and Security. New York: Cengage Learning.