Introduction
Arguably one of the most epic accomplishments of the 21st century was the invention of the computer and the subsequent creation of computer networks. These two entities have virtually transformed the world as far as information processing and communication are concerned. The interconnection capability of computer systems can arguably be described as the feature, which makes them most versatile and invaluable to their users. This being the case, the network functionality of computing systems has been exploited by organizations and individuals alike as efficient local and global communications became the defining attribute of success. As such, the creation of networks is key to any interconnected computing system. A network may be created that uses cables (fixed connection) or that uses radio waves (wireless network).
While fixed Internet networks continue to form the backbone of the communication system, wireless data transmission has become more favored for various reasons. Various forms of wireless technologies have come up to fulfill this role. Nuaymi asserts that WiMAX technology is at the present one of the most promising global telecommunication systems (2). WiMAX emerged as a Broadband Wireless Access System that has many applications ranging from the mobile cellular network to backhauling. Considering the prominence of WiMAX in networking, this paper will set out to give a detailed discussion on some of the specific aspects of WiMAX,
WiMAX Overview
WiMAX specifications have gained significant success in the provision of internet access and broadband services via wireless communication systems. WiMAX is defined as a technology that provides for mobile and stationary broadband wireless access to “IP-based services through a common radio technology, providing support for quality of service, roaming of mobile users and strong security” (Schmidt and Lian 253). Khosroshahy and Nguyen document that WiMAX is considered as the “Last Mile solution, which provides a fast local connection to the network” (3). Obvious merit of WiMAX over high-capacity cable/fiber is that it is less expensive to deploy and can be deployed in areas that lack a good telecommunication infrastructure.
WiMAX is a wireless transmission technology that can be used over two wireless network categories; Wide Area Network (WAN) and A Metropolitan Area Network (MAN). A MAN is a data network that may extend for several kilometers and is usually used for large campuses or a city. A WAN is a data network that spans a boar area and links various MANs. Scarfone, Tibbs, and Sexton reveal that WiMAX is the most commonly used form of WMAN and its promotion of interoperability between products based on the IEEE 802.16 standard makes it the model technology for this networks (2).
Interoperability is ensured by the WiMAX Forum, which is an “industry-led non-profit organization” boasting of a membership of over 500 as of the year 2008 (Roh and Yanover 3). Dowd asserts that WiMAX, in essence, provides a feasible and cheaper alternative to wired WAN technologies such as cable or leased lines (3).
The architectural components of a WiMAX include; a Base Station (BS), Subscriber Station (SS), Mobile Subscriber (MS), and a Relay Station (RS). The BS connects and governs access by the devices from the wireless network subscriber to the operator network. The BS is made up of physical devices such as antennas and transceivers, which are necessary for wireless data network communication. An SS is a fixed wireless node that communicates with the BS or forms a link between networks. AN MS is a wireless node that receives or transmits data through the Base Station. An RS is a Subscriber Station whose purpose is to retransmit traffic to the relay stations or subscriber stations.
Key MAC Features
Mobile WiMAX has certain key MAC (Medium Access Control) features that provide for the high efficiency and flexibility for which the technology is renowned. To begin with, WiMAX provides for connection-oriented services with certain classification rules being specified so as to define the traffic that is associated with a particular connection. In each connection, qualities of service parameters are defined, such as “minimum reserved rate and maximum sustained rate (Roh and Yanover 8).
The WiMAX technology also has mechanisms set in place to reduce the MAC overheads during transmission. In particular, the technology has support for general Purpose Header Suppression (PHS) as well as IP Header Compression (ROHC). Roh and Yanover reveal that these mechanisms are effective since data a packet being transmitted at the network level contain many repeated parts of the header, and by replacing this with short context identifiers, PHS greatly reduces the overhead that results from headers (8).
Another feature at the MAC layer that enhances the quality of service in WiMAX is the scheduling system specified by the IEEE 802.16 MAC. According to this scheduling, the subscriber station, which wishes to attach itself to a network has to compete with others when it initially joins the network. A time allocation is made by the Base station though this time slice can be expanded or reduced based on the needs of the SS. This slice remains assigned to the SS, therefore ensuring stability under overload and oversubscription. The scheduling also has more bandwidth efficiency, which results in the quality of service since the resources are well balanced among the needs of the various SSs.
Data Transmission
WiMAX offers a number of coverage for its broadband wireless transmissions. SR Telecom notes that while most other technologies are limited to only providing line of sight (LOS) coverage, WiMAX technology provides for a nonoptimal line of sight (NLOS) coverage as well (2). When the WiMAX propagates signals between nodes at a frequency of 10-66 GHz, the signals are highly sensitive to radiofrequency (RF) obstacles, and as such, an unobstructed view between the nodes is required. This is known as the line of sight (LOS) link, where a signal has to “travel in an unobstructed path from the transmitter to the receiver” (R Telecom 1). If there is an obstruction in the line of sight between the transmitter and receiver, there will be a significant loss of signal strength resulting in poor performance. LOS employs relatively simpler RF modulation techniques as compared to NLOS. The power needed for transmission is also lower since the signal is propagated in a straight path.
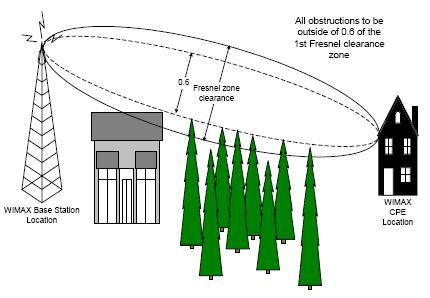
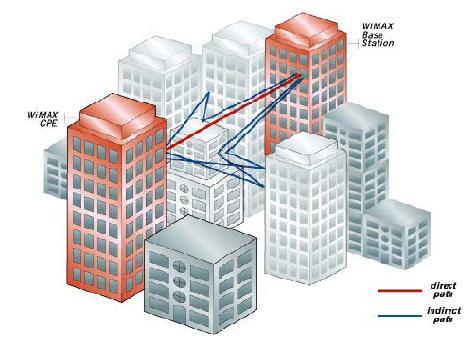
Non-line-of-sight (NLOS) coverage employs “advanced RF modulation techniques to compensate for RF signal changes caused by obstacles that would prevent LOS communication” (Scarfone, Tibbs, and Sexton 3). The operation frequency is 2-11GHz, depending on whether the link is being used for Mobile or fixed WiMAX operations. The NLOS signals on being transmitted reach the receiver through a combination of reflection, scattering, and diffractions.
NLOS signals are employed more often since the feasibility of LOS is hindered in many areas due to deployment costs, environmental, and licensing factors. WiMAX that employs NLOS technology offers certain obvious advantages as compared to a LOS technology implementation. An NLOS system does not require an antenna’s to be placed at the great heights that LOS systems call for. In addition to this, NLOS technology results in reduced costs since extensive pre-installation site surveys are not necessitated before the system is installed. NLOS also enables WiMAX technology to deliver services to a wider range of customers.
There are two main techniques that are used to deliver broadband data at the physical layer, namely the: Orthogonal Frequency Division Multiplexing (OFDM) and Orthogonal Frequency Division Multiple Access (OFDMA). Khosroshahy and Nguyen document that these techniques, which have only been developed in the past few years, “deliver broadband services that can be compared to those of wired services in terms of data rates” (6).
In the OFDM technique, a single transmitter sends out a signal at different orthogonal frequencies using advanced modulation techniques to ensure that the signal has a high resistance to interference. This technique is favored by most operators since it has a superior NLOS performance due to its high spectral efficiency (Khosroshahy and Nguyen 7). OFDMA has the same operating principle as OFDM with the added advantage that it allows for multiple users to transmit data using the same spectrum simultaneously. This is achieved through the sharing of sub-channels among multiple users.
Mobility
WiMAX gives full mobility support for devices that may be moving below certain threshold speeds. Naomi goes on to illustrate that WiMAX also allows for portability since a user can move at a reasonable over a large area that is covered by multiple BSs without interruption of the current session or communication. The speed at which a mobile WiMAX device can move between cells in a seamless session is valued at 120km/h. Roh and Yanover state that WiMAX systems can “detect the mobile speed and automatically switch between different types of resource blocks to optimally support the mobile user” (7). In addition to this, WiMAX technology employs the Hybrid Automatic Repeat Request, which assists in the mitigation of the effect of the fast channel and interference fluctuation.
Security
Securing a network is, at best, a very challenging task due to the fact that new software and hardware keep being developed by the wireless industry and threats and vulnerabilities keep changing. As such, the security implementations of the previous year might prove to be grossly inadequate for the current year. With these considerations, the WiMAX technology has an intricate security architecture that is meant to ensure that the network is secure both for Fixed and mobile wireless access. Schmidt and Lian assert that the overall goal of the security architecture employed by WiMAX is to create an interoperable security solution that is stable but also accepts the common security protocols (263).
At the very basic level, all WiMAX links are encrypted, and for one to read the information, they need to employ some decryption mechanism. Extensible Authentication Protocol (EAP), which is based on mutual authentication between the Mobile and the network, is used at the security level of the WiMAX to ensure security. For fixed wireless access, WiMAX uses a “single network access authentication and authorization key established protocol Privacy Key Management” (Schmidt and Lian 255).
Mobile WiMAX networks require secure access and authentication is mandatory before communication can commence (Schmidt and Lian 258). WiMAX employs authentication and authorization processes in communication between nodes. Authorization is the process of determining the level of access that a node is given after it has been identified and authenticated. WiMAX uses the public-key infrastructure for device authentication purposes. To provide for secure communication, the WiMAX system performs the three steps of; authentication, key establishment, and data encryption.
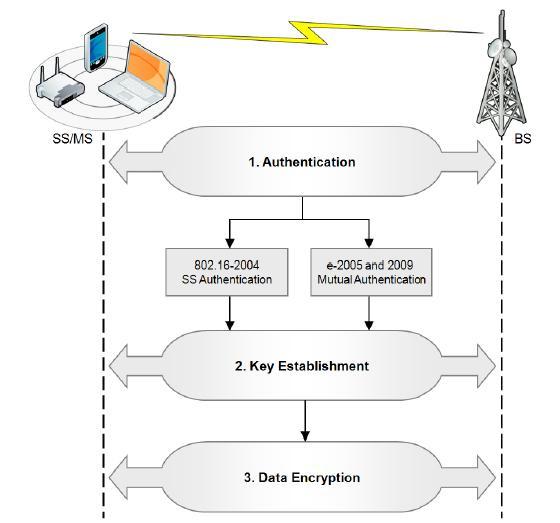
It is worthy to note that WiMAX network specifications are constantly evolving, and as such, the security architecture is expanding as well. Roh and Yanover state that the Basic security mechanisms are strengthened by adding digital-certificate-based Subscriber Station device authentication to the key management protocol (9).
Conclusion
This paper set out to analyze WiMAX, which is increasingly becoming the preferred wireless technology for Broadband Wireless Access systems. The paper has discussed various aspects of technology, including its mode of transmission, mobility, and security. From the discussions undertaken, it can be seen that WiMAX technology is secure as a result of the authentication and encryption capabilities employed. A major strength of WiMAX has been seen to be its promotion of interoperability of broadband wireless products, therefore, allowing products from various manufactures to operate seamlessly on a network, as well as its employing of NLOS technology, which allows RF signals to be transmitted regardless of obstacles.
From this paper, it can be suggested that WiMAX technology is the future of wireless communication over WMANS since it provides quality broadband services. As it currently stands, WiMAX specifications have gained significant success all over the world. It can, therefore, be projected that WiMAX technology will continue to be used as the technology of choice in wireless networks.
Works Cited
Dowd, Kevin. Wireless WAN/LAN solutions for schools using WiMax, WiFi and Secured Access and Content. Halestar, Inc, 2008.
Khosroshahy, Massod and Nguyen, Vivien. A study of WiMAX QoS mechanisms. Telecom Paris, 2006.
Roh, Wonil and Yanover, Vladimir. Introduction to WiMAX Technology. John Wiley & Sons, Ltd, 2009.
Scarfone, Karen., Tibbs, Cyrus and Sexton, Matthew. Guide to Security for WiMAX Technologies. National Institute of Standards and Technology. Special Publication 800-127, 2009m.
SR Telecom. WiMAX Technology LOS and NLOS Environments. SR Telecom Inc, 2004.