In every organization, an information system is developed so that it may assist the management to carry out its transactions effectively. The process of producing a system specification that can be used to design and model a system is known as system analysis. An art gallery is a firm that deals with art and design items such as paintings that convey messages that are critical to the audience rather than rifles. It occupies spaces within it where different kinds of exhibitions are displayed such as paintings, sculptures, photographs, illustrations, and applied art objects. The artistic activities that are carried out within the organization involve music concerts and poetry readings. The items found in the gallery are gotten from; private collectors, others are loaned from other galleries while the management of an organization specifically buys others from the market.
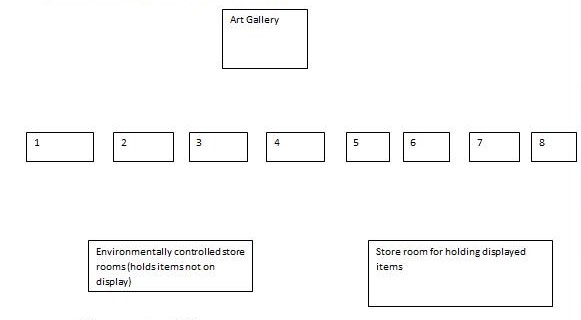
The company consists of eight exhibition rooms where items are displayed so that the public can easily view them at a convenient place. The four large environmentally controlled storerooms are used to store items that are not meant for public viewing. The items are changed after every three months so that their stocks can be evaluated hence the preparation of the necessary catalogs by the management of the organization. The catalog shows the present location of items stored within the gallery and the time the borrowed gallery items would be returned to the owners.
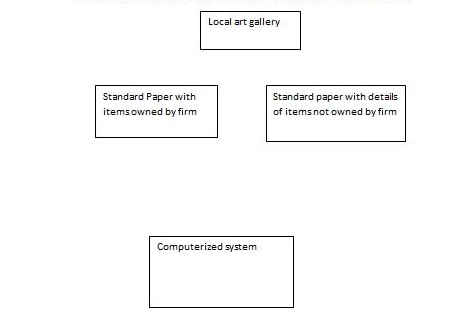
The curator is the person who is charged with the responsibility of managing all items within the gallery and those being returned to the owners. They also write, read, edit and delete processes after a system has been installed within an organization. The standard paper is used to help a curator to record all items found in the gallery and shows items’ names, location, owners so that they can be easily identified and insured against risks such as theft, fire, and risks that may cause damage to the items. It is also used to record items that are not found in the gallery that as those that have been loaned to parties outside the organization, where the date of receipts are recorded, the date when it’s due for return, and details of the owner of gallery items. The paper is written in handwriting although no standard format is followed when undertaking this task.
The computerized system is used to show how items within the gallery and the way they are presented in the catalog. It also shows information found in the current page system in order to transfer it to the computerized system. The management of the organization uses the website so that the public can access the information that is related to the operations of the organization (Wires-Brock Wilkerson and Wiener 1990).
Object-oriented analysis and design is a software engineering method that is used to model a system into groups of objects that can interact with other objects. The objects represent entities of systems being modeled, whose characteristics involve: class, data elements, and the behavioral factors of the units. The unified modeling language (UML) is a type of notation that represents models. Object modeling technique is a technique used in object-oriented analysis to analyze the system’s functional requirements. It mostly deals with defining a problem domain that is aimed at producing a conceptual model of information.
The sources of object-oriented analysis can be derived from the requirements statements, formal vision documents, interviews with stakeholders or other parties, whose results are generated as a result of carrying out the object-oriented analysis. The process shows how activities within the system are carried out. The processes within the analysis are presented in various forms such as the use of cases, unified modeling language (UML), class diagrams, and a number of interactive diagrams. The object-oriented design (OOD) is a model that changes the conceptual models found in object-oriented analysis to incorporate the constraints that are imposed by the architecture and other non-functional constraints such as transaction throughput, response time, run-time platform, development environment and the programming language (Wires-Brock Wilkerson and Wiener 1990).
Task 1
Functional model is a model that is used to show how data flows within a system and describes what the system does and does not do. It shows the relationship of values that are computed within the system. It also shows the aspects of the system that have references to other models within the system. This model consists of dataflow diagrams and constraints, dataflows, actors and data stores of the system
Use case diagrams
These are the diagrams that are used to identify the activities that are performed by the users of the system. They also show the external view of the system and models that can interact with the environment. It also shows how the user interacts with it and the way the system responds to it. It doesn’t indicate the details of messages passed within the system. They are described in both words and diagrams that show how the user interacts with the system and how the system responds to it.
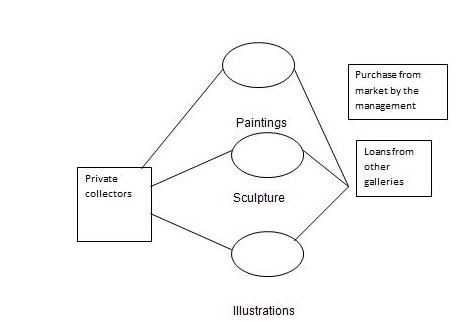
In the art gallery firm the sources of items for the firm are derived from private collectors, loaned from the customers and others are bought by management of the organization.
Use case specifications
These are use a summary of the use case description that consists of more than 5 lines. It shows the conditions that must be fulfilled in order to ensure that use case is completed and rules that relate to the use case are implemented appropriately.
Activity diagrams
These are diagrams that show how the processes within a system are performed and the way data moves within the proceses. They show the use-case that occurs within the business and how the system interacts with the external environment. They also identify user cases that occur in the businesses and also model the business processes that are independent of the objects. They model individual methods and the high-level business models of a system.
The main element found in the activity diagrams involves; actions and activities, control flows, control nodes and fork and merge nodes.
Actions and activities are used to show the manual and computerized events that may happen within the computer system. Action refers to the behavior that can be further decomposed by a system. Activities are decomposed into other activities and actions within a system. Control flows are flows that indicate the path of executing a business process which is shown by a solid line that has an arrowhead that show the direction of the flow of data within the system.
Control codes are the code that shows how a control is exercised within the system. They include: initial node that indicates the start of the process. A final node indicates the exits of all activities and actions. Decision nodes are the nodes that indicate decisions made within the system while the path followed depends on the test of the process that is been operated on the computer system. Guard conditions are added so as to indicate the value of the test that should be followed within the system. The forge and merge nodes are the nodes are run parallel to one another.
The events that take place within the art gallery system involve:
Task 2
Art gallery system using object oriented method and structural model involving
Class diagrams
Art Gallery These are the diagrams the static structure of the system. These diagrams show the functional requirements of a system. The class is used to represent a rectangle that consists of three compartments. Objects indicate a relationship that exists between objects that are of the same class of operation.
Attributes and operations
Attributes are kinds of information that indicate the description of an object, for example name, date of birth, address and year of the course taken by the students.
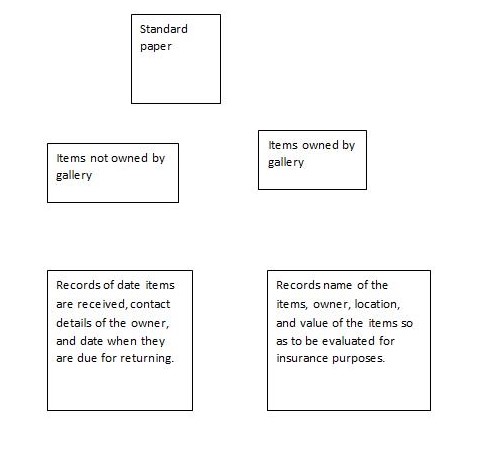
Records of date items are received, contact details of the owner, and date when they are due for returning.
Records name of the items, owner, location, and value of the items so as to be evaluated for insurance purposes.
Task 3
Behavioral models are the models that are used to indicate the internal aspects of an information system that can be in a position to support the business processes within the organization. It consists of sequence diagram, state machines and communication diagrams.
Sequence diagram
It is a diagram that is used to depict how the object of a system interacts with each other during certain periods of time. Activation is the period where an object performs its operations and shows how communication takes place within a system. There are two kinds of messages that are conveyed by the system such as synchronous and simple messages. Synchronous messages are the messages where the caller waits for the receiving object to complete executing its operations before the start of the operation. Simple messages are the messages that can transfer the control from the sender to recipient of information before describing the details in which the communication takes place within a system.
The management of art gallery prepares the standard paper to enter details about items within the art gallery.The information within the standard paper are transferred to the computerized system where a website is created so that the public can easily access information about the exhibitions in the gallery and items that are displayed on it.
State machines
The state machines are the diagrams that are used to show how the different state of objects and events causes the objects to change to different states together with their responses and actions that are associated with them.
The suppliers of the art gallery first check the items that are ordered to verify whether they are the right orders ,then after the right stocks are received they are dispatched and dispatched to their clients
Communication diagrams
These are the diagrams that are used to represent the combination of information that is taken from the class, sequence and the use case diagrams that are described using the static structure and the dynamic behavior of the system.
Task 4
a) Methods used for adding current paper based information to the system
The methods that are used in order to transfer information from the current paper based system to the computer system involve:
Visual display unit
It is an input device that consists of the keyboard and instructions.It consists of keys used for controlling and editing the input data to the system. It has a screen that displays information in a page of 24 rows and 80 columns. The displayed information is non- permanent in nature and can disappear any time when power is switched of.The data is edited through moving the cursor on the screen while using the special editing keys. The cursor is a small blinking device that is used to ensure that work is edited properly.
Terminal typewriter is an input device that has a keyboard to input data and instructions and printer to act as an output device that gives results of the operating system. Printer produces information in terms of printed documents known as hardcopy print outs. The correction process can be carried out through cross checking the source documents against the printed input data; in case of any mistakes they are rectified immediately as they are noted.
The other types of input devices consists of document readers that sense data and instructions from the source documents and later on conveys them as computer input that use electronic signal and thus require no verification in order to undertake their tasks. They are classified into optical character reader and optical mark readers.
Optical character readers
These are input devices whose characters are formed on the document while using the typewriter or the computer printer. The characters are in form of alphabetic, numeric or special characters that are formed in human machine sensible form. It is connected directly to the computer system as it operates using the principles of light. The characters reflect different amounts of light as they are sensed by the devices. The optical character recognition it’s a data capture technique enables a computer to read the printed information appropriately. The optical mark reader is an input device that uses the principle of light to sense the positional marks that are interpreted using the reflected light and later on conveyed to computer as electronic signals.
Magnetic ink character reader (MICR)
It is another input device that is used to read data. Document characters are typed using the ink that consists of particles that contain iron 2 oxide that makes it to have the magnetic property. The magnetic ink characters are later on passed through the strong magnetic field so as to read data effectively.
The advantages and the disadvantages of the methods
Advantages of magnetic ink character reader, optical mark reader, optical character reader: there are no typing or the transcription requirements therefore fewer chances of errors, documents can be turned around hence the user can save on stationery used, the contents of the documents are in form of human and machine sensible form and they provide faster inputting of data into the system than use of the keyboard devices that take a longer period to accomplish their tasks. An advantage of the visual display unit is that the user can rectify mistakes when they arise on the computer and it’s a cheap way of displaying information for the user
The disadvantages of the methods include
They are expensive methods since they require use of specialized techniques and equipments, it is important to handle them carefully so that data can be read appropriately , the size of and type of the documents can determine how well information can be read from them. Special typing or characters are used in order to undertake the tasks while using these devices thus posing as a major challenge to the users of the system. Visual display unit disadvantages involve lose of data when power is switched of abruptly and data cannot be stored for a longer period of time since its storage capacity is small.
c) The methods that should be used are the document readers this is because they are faster methods of transferring information to the computer system, there is less wastage of time, and stationery is saved since the user doesn’t require lots of documents in order to undertake his tasks. There are fewer chances of typing errors since the document readers carry out their tasks effectively. It is also a convenient way of transferring information from one place to another.
Task 5
User interface
It is the prototyping technique that is used in the system to explore a problem space of the stakeholders provides the solutions for problems that are faced by the system and used to develop the system from the place its being developed in. The step followed in ensuring that this process is accomplished involves analyzing the user interface needs. User interface modeling involves determining the requirements definitions into the analysis where one decides to develop some essential user interface prototype into a traditional one. It involves making decisions that can make a substantial system for the user. The other step involves building a prototype that is as per users requirements. The model should use the prototyping tools or the high level language that can develop screens, pages and reports that may be needed by the user from the point where one can convert individual aspects of the user interface into the traditional user interface.The user interface is evaluated so as to verify that all the user needs are met. After the evaluation one can realize that they should scrap some parts, modify other and add the new brand new parts so as to undertake tasks effectively.
In the art gallery, the manager determines the needs of the customers before he operates his business so as to understand the kind of items that should be displayed that will attract their attention. It’s after determining their needs that one builds a prototype that resembles the system that should be developed for the organization.
Relational database design for art gallery catalogue system
Relational database refers to the database that is used to store information in tables. The tables are created as operations on data are being carried out. Tables consists of rows and columns.The rows are in form of set that hold only one value with the same number of columns ,although some columns may not contain any values at all. The goal of relational database is store information in one place as to avoid redundancy of work and to retrieve information when it’s required easily and accurately.
Normalization refers to process of ensuring that data is organized appropriately so as to apply data dependencies effectively. It involves specifying, defining tables, keys, columns and relationships in order to establish a proper database that is efficient and functional. Normalizations objectives involve the process of averaging data into legal groups that describe each small part of the whole objects. It is used to minimize the chances of having duplicated data that are stored in the databases. It builds a database that one can access and manipulate quickly and efficiently without compromising the integrity of stored data. It helps in organizing data in a way that one can modify make changes that may take place. There are three normal forms that are followed so as to ensure that the process normalization process is completed effectively.
First Normal Form
It involves the process of reducing the number of the groups that are similar through making separate tables that have related attributes and primary keys for each table. Tables do not contain any duplicated rows where data are considered to be single spaced hence no repetition of any groups or arrays. If the entries in column are of the same kind and row contains the same columns. The order of rows and columns are irrevant. The primary key is used to show the differences between this groups of data and also identify the occurrences that are within the same new relation. It consists of two dimensional tables that have rows and columns. Columns correspond to the sub-subject or the attributes that are represented by the entire table.
Second normal form
It involves the process of creating the relations that are in the first normal form. It affects the relations that have more than one attribute that are within the same key. The tables created do not contain all the atomic data items, they don’t require repeating groups and a designated primary key. Tables contain the non-primary key attributes that are fully functional and depend on the whole primary key.
Third Normal form
It is the form that is used to eliminate the number of columns that do not depend on the keys. There is removal of attributes that don’t contribute to the description of the separate tables. Each column depends on the primary key all attributes that are not dependent on the primary key are excluded from the list in the group. For instance the attributes that are derived from the data are found in other field and tables that must be eliminated. The criteria followed for establishing this form involves tables that should contain all the atomic data items that have repeating groups that are designated by the primary key. Tables have non-primary key attributes that are fully dependent on the whole primary key. The transitive dependencies are eliminated from the table in the system. It takes into account the relations that exists within the second normal form and considers dependencies found in the non-key items.
Data dictionary
It is used by system analyst to store information that is used to develop the system. The information kept involves the length and valid values of the customer number, list of processes within the set of data flow diagrams and the content of all the data stores that are held in the data dictionary. It also involves holding information that can define the products of the system that is to be developed such as the dataflow diagram entity relationship diagrams and the physical design stage that can be reached. It consists of objects that include data flows, datastores, processes entities and the minispecifics.
The data dictionary entries in the data base design
The common parts of the data dictionary entity involves the name of the object that is created by the analyst, that should be meaningful to the analyst and users. The major elements and structures that are used to define the objects are the recorder that is within the computer system.
Data element entries
It consists of the data element that describes what the elements are and what they represent. It shows occurrences of the elements their relationship to other entries in the data dictionary shown. A data element consists of the pictures that show the details of the format of elements and range of values that it has. The format is defined using the knowledge used into the project. Notes contain any information of elements that is to be used such as the design and programming considerations that are stored on the disk pack in the decimals.
Data structure entities
The entry involved consists of the definition of data element and structures. Notes show information about the values that are used to control the logistics for the process that are used within the structure.
Data flow entries
It shows a data structures that are in motion. The entries made by the data flows involve the definition that show the structures and forms of dataflow, occurrences that summaries the operational information such as the maximum, minimum per day and the projected increases of inflows of information. Notes indicate the origin and the destination of the flow of information together with the operation information such as the response time taken.
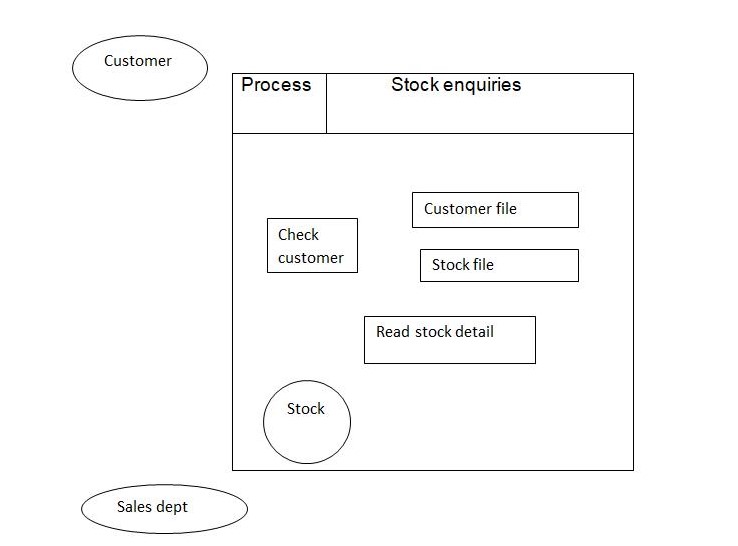
Data stores entries
These are the entries that show the data elements and the structures of the system. It involves the definitions that identify the data structures that are held in the data stores and the information about the organization in the store. The entries involves the details of the size of the store that should be used and its expected growth.The notes indicate the details of data flow that may enter and leave the store.
Process definitions
They are used to describe the functions of the process that involve the unambiguous description of logic that should be expanded in the analysis stage. The references to the procedure specification are prepared in order to indicate all the documents that are shown in the data dictionary. Notes are used to indicate the input and output that flows within the process. Entity entries are sources and links that are used to indicate the name and data flows that can be linked to the entity.
In the art gallery the information that is stored in the data dictionary involves items that are displayed in the art gallery, source of the items for example some are derived from private collectors, other loaned from other galleries while the rest are bought by the management as part of its stock.
Task 7
Threats to computer system and security
a) Threats are classified into two internal and external threats. The internal threats are caused by factors that are within an organization while the external threats are factors that occur as a result of variables that are outside the control of the management of an organization. They are further classified into environmental threats and threats posed by people.
Environmental threats
These are the threats that occur as a result of the environment in which a computer system is located.It also results from power and communication lines that are connected a computer that is outside world that make the computer system to function effectively. The factors that are result from the environmental threats involve;
Location of a building
The place where the building is located can be a major factor that can pose as a major challenge to an organization. For instance the site where the computer system is located can affect its operation such as in harsh climatic conditions as nearness to the flood plains or river may be a challenge during the heavy rainy seasons. The stability of a ground in which the computer system is located for example in the earth tremors may occur due to salt mines or extractions that can break the communication lines. The activities that take place near computer system can affect its security for instance if there is a power output from a radar transmitter that is near the airport may lead to corruption of magnetic media that may be caused by the aircraft in the computer room.
The building in which the computer system is housed can cause a major problem to the security of the computer system. The features within the building such as building design, height, drainage, fire resistance and the number of buildings that are within it can have adverse effects on the system.
Interruption of services
Where there is loss of important services they can pose as a threat to the integrity and availability of any computer system. When the electricity supply is not efficient to ensure that computer system is not operational then it can be a threat to the management of an organization. The systems within a system may not operate if systems such as air conditioning, lights, and smoke detectors are not supplied with the necessary power to run their operations. There can be corruption of files when there is loss of power this is because all business is carried out with the presence of the electricity.
Threats posed by people
The persons employed within an organization can pose as great threats within a computer system since they may not take care of the systems departments as expected of them. For instance they may allow an authorized person within their premises that may use their confidential information to invade them in the future. The confidential information may be used by the opponents to attack the management of the system hence can corrupt data thus users may not be in a position to access data as required of them. The hackers may attack the programs through preparing programs that have viruses that can corrupt a whole system of operation thus affecting the whole system of the computer system (Salvendy2001).
Human error may affect the integrity of the computer system since it can occur due to lack of understanding on the part of the users of how to manage the system, lack of training, inadequate documentation of procedures, and lack of interest on how to undertake tasks within an organization. There are malpractices that may be practiced by people within an organization such as fraud that is practiced to benefit few individuals within an organization system. Industrial espionage occurs due to the acquisition of information by the competitors, casual disclosure as this can pose as a great challenge to the management of the computer system. The presence of so many pieces of computer system that are left idling for a longtime in the ordinary offices can lead to opportunity for theft of those equipments.
The consequences of breach of security
There are a variety of consequences that are associated with the breach of security these include: loss of income which occurs as a result of delay in providing invoices for the customers and payment of the workers in time and meeting costs as they arise. There may be loss of customers that occurs from failure of the management to provide the necessary services to the customers.It occurs due to failure of the management to keep proper records, there is reduced stock and the inability to control the production process of an organization.
There can be loss of confidential information this is because the officials may leak information to the rival parties hence leads to embarrassment to the individuals and organizations hence creates a competitive advantage among the business partners. Computers may be improperly installed thus may affect the way the operations are carried out within the organization since lack of security may jeopardize the operations of the organization. There may be loss of the whole business since it occurs as a result of loss of security, loss of income and customers may be affected by the operations as it may affect the survival of the business as a whole. Loss of integrity that occurs from the systems inability to perform all functions accurately due to loss of programs and data that are held in the computer which leads to deliberate unauthorized modification of the system. Loss may also occur due to physical disaster that may destroy the centralized computer system that supplies information to all organizations, branches and depots that are located in various parts of the country.
The methods that may be used to ensure that the curator and assistant curator have; edited, write and delete permissions.
The control that can be implemented that can ensure that the curator and the assistants curator are the only ones who can access the computer system involve: the persons use of the password or the personal magnetic card that give them the permission to open a computer system.The reason for using this method is to ensure that only the right person attend to the computer system otherwise it would lead to exposure of confidential information to the public who may be a threat to the organization. A utility software should be installed to ensure that a screen saver is implemented that can prevent outsider from accessing confidential information from the system otherwise outsiders would jeopardize effective operations of the organization (Butler, Esposito and Hebron 1999).
The other methods that can be used to distinguish persons working within the computer system involve the use of physical means to identify a person such as fingerprints, hand scans, voice recognition and the retina scan. This control method helps to prevent an authorized person from accessing confidential information from the computer system. Physical control is a method that can be imposed on the curator and non curator while performing their duties and responsibilities. This control involves defining all duties of personnel within an organization and assigning tasks to persons within organization so as to ensure that activities are carried out effectively it should be noted that no person should undertake all tasks without getting permission from the senior officers.
The ways in which one would allow the website to have read-only access to the relevant information is to ensure that restrictions are applied so that the users only read information but not to duplicate it without the permission of the users as that would amount to illegularities.
Task 8
The system design for art gallery involves
System design refers to the activities that are undertaken so as to produce a technical specification of a proposed system. The process involves writing of programs for the system, configuring the required hardware, implementing the operating software platform and communication networks required for the process. The system design of the art gallery involves; items owned by the gallery, items loaned from different parties and others borrowed from the private collectors (Cris 1999).
There is also the subdivision of the local art gallery into eight storerooms, where four of the largely controlled storerooms display the items that are not meant for public viewing while the rest are for public viewing. The class diagram can be used to show the structure of the art gallery.The sequence diagram can be used to indicate how events take place within the system from the beginning to the end. Relational database can be created so as avoid duplication of data as these would save on time and money that would be spent on searching for the relevant information within the computer system (Butler, Esposito and Hebron 1999).
The system analyst should determine the needs of the users through carrying a research on the type of needs that they have so as to avoid wastage of time and money. It also helps in building a prototype that can meet the needs of the users at an appropriate time. The system analyst later on stores his information for future reference through using the data dictionary. He controls the computer system through determining the kinds of threats that may hamper the proper functioning of the system. Once the threats are identified then operations within the organization can be carried out effectively.
The different kinds of hardware that may be required by this system include: Central processing unit, peripheral devices that are connected and controlled by the central processing unit. The peripherals include; data preparation equipment, input devices, additional secondary or the backing storage devices and the output devices. Input devices are the devices that are used to ensure that the data that should be processed is supplied to the computer. The processor is used to ensure that data is processed effectively while their results are output using the output devices.
The central processing unit is used to ensure that raw data is processed into meaningful information for the system. There are three components that make up the computer system these include; control unit, arithmetic and logic unit and the main memory unit. Control unit is used to supervise, oversee all the activities that are within the computer system and ensures that programs being processed are executed effectively. It also coordinates and controls all the activities carried out within the computer system. It also selects and interprets instructions and sends appropriate signals to the other units that can be executing activities within an organization.
Arithmetic and logic unit is the unit that is used to measure that arithmetic and logical functions within the computer system are carried out appropriately. The arithmetic operations involve addition, multiplications while the logical operations involve the rearrangement and arrangement of data such as sorting, matching and comparisons. The main memory unit is also referred to as the primary storage unit, internal memory, immediate access storage and the core memory. The different kinds of memory are used to ensure that data is stored in appropriate manner. The input devices that are used to interface the external environment with the computer system.Computer users communicate and receive instructions with the help of the input devices. The facilities communicate these inputs and the forms that are sensible to the user using the electronic pulses (Butler, Esposito and Hebron 1999).
Output devices are used to communicate the results generated during the processing period to the external environment. Computer users are the persons who receive the processed information by the computer the facilities communicates the information in the form that the users can comprehend.
Secondary storage is a storage facility that is used to ensure that data is stored at convenient places at cheaper prices. Data is stored in form of floppy disks; flash disks. The reasons for using these devices are to supplement the internal main memory of the computer that may be inadequate to store all the required data needed by the user. It is also expensive to store information with use of internal memory while at the same time it loses data easily as compared to the secondary storage device.
It has been noted that the establishment of a proper system can ease the work that is carried out by the management of the organization. The cost of running an organization can be reduced since the system can carry out all the activities as required at a faster and shorter period of time.
Appendix
The art gallery consists of eight exhibition rooms that are used to display items that can be viewed by the public. There are four large environmentally controlled store rooms where items that are on display are kept. The store rooms are further on divided into individual store areas that are identified using three unique letter codes that distinguish the store rooms from the others.
Assumptions of behavioral model
The behaviors of objects can be learnt at the same time with maladaptive behavior. It has been noted that the principles of conditioning and modeling are learnt with the model. The learnt topics can be contradicted by the same principles. These laws apply to both the learned and non-human animal behaviors.
In the process of normalizing the database the designer starts with the general work and later on works toward the specific tests that undergo a process that is referred decomposition.the goals of the normalizing the database may be referred to as: data intergirty, inferential integrity and the keyed data access process.
References
- Atkin, J. 2007, Object-oriented methods (G52OBJ Contents.
- Aurum, A. Cox, K. and Jeffery, 2004,” An experiment in inspecting the quality of use Case Descriptions. Journal of Research and Practice in Information Technology, 36(4):211–229,
- Brooch, G. 2007, “Object-oriented Analysis and Design with Applications, 3rd edition.
- Butler, K.A., Esposito, C. and Hebron, R 1999,”Connecting the Design of Software to The Design of Work.” Communications of the ACM 42, no. 1 p38-46.
- Cris, K. 1999, “UML 2001,” A Standardization Odyssey.” Communications of the ACM 42, No. 11 p 29-37.
- Constantine, L. L., and Lockwood, L. A. D. 2001, “Structure and Style in Use Cases for User Interfaces.” In M. van Harmelan, Ed., Object Modeling and User Interface Design: Addison Wesley, Boston.
- Case Diagram & Use Case Specification week4.
- Dennis, A., Wixom, B. and Tegarden, D. 2005,” Chapter 8: Behavioral Modeling John Wiley & Sons, Inc Copyright Systems Analysis and Design with UML Version2.0,Second Edition.
- Electronic Government Directorate (Strategic Planning & Architecture) Version: Draft 2005
- Fowler, M. 1997, Analysis Patterns: Reusable Object Models., An Introduction to object-Oriented analysis with conceptual models, Addison-Wesley.
- Grant, L. 1999, “Designing Component-Based Frameworks Using Patterns in the UML.”Communications of the ACM 42, no. 11p 38-45.
- Grover, V., Kettinger ,W. J. 2000, Process Think: Winning Perspectives for Business Change in the Information Age. p.168.
- Kaukolu, M. K. 2006,”Hub of the semantic corporate intranet. In SemWiki Workshop, ESWC 2006, pages 31–42,
- Kendall, K. E. & Kendall, J. E. 1999,”Systems analysis and design, Upper Saddle River, NJ, Prentice-Hall.
- Meyer, B. 1997, Object-oriented software construction. Prentice Hall.
- Phalp, K. Cox, K. and Shepperd, M. 2001,”Comparing use-case writing guidelines. roc. Workshop on Requirements Engineering: Foundation of Software Quality (REFSQ’01), pages 101–112.
- Salvendy, G. 2001, Handbook of Industrial Engineering: Technology and Operations Management. p.508.
- Satzinger, J., Jackson, R. & Burd, S. 2004, “Systems analysis and design in a changing World” 3rd ed., Boston: Thomson Learning, User Interface Prototypes Agile modeling
- Wires-Brock, R., Wilkerson, B. and Wiener. L. 1990,”Designing Object Oriented Software. Prentice Hall, A down-to-earth introduction to the object-oriented Programming and design.