Introduction
Internet can be defined as computer networks interconnection using a standard protocol to provide information to the entire world irrespective of where one is at any time (Garcia 32). The networks compose of public computers, learning institutions computers, business enterprises computers and private organization computers for local and global scope.
Earlier the internet was being referred to as the information super highway, its’ main aim of was to avail limitless information to everyone who needs it as fast as possible. Internet censorship refers to the act of controlling information access through the internet. Main motives of internet censorship vary from one website to another (“Research profiles.” 1).
Main reasons are children protection from harmful and explicit material, enabling grown up avoid contents that may compromise their community and personal standards, imposition of a moral framework in adult communication through the internet, and blocking of information material that is illegal to possess according to the government of a particular country under consideration.
The government uses various techniques to censor internet depending on the content they want to restrict. It does so through the use of program software called web filters or censor ware.
Internet censorship
Main techniques for internet censorship include, IP blocking technique, this target website hosted by a common server. The entire websites hosted by that particular IP address are blocked (“Research profiles” 1).Whenever one tries to access them he/she is denied the access rights. Filtering domain name server (DNS) method, in this method the domain name is not resolved hence one is unable to access the site. This method uses software that restrict resolving of the domain name, as a result the target website is unavailable.
Packet filtering method, this technique uses keywords in filtering the content to be accessed, if the keyword is detected the site content is blocked. Another method is through the use of the uniform resource locator (URL), it uses keywords to block censored site from access. When one try to access a website the uniform resource locator is checked if it consists of the restricting keyword, if the keyword is found in the URL the site become unavailable.
Reasons for censorship
Different government censors the internet due to different reasons, some may be reasonable and varied, while others are misuse of the power by the government. This has created a controversial situation of whether the government should carry out internet censorship or not (Kenny 1).
Different people have different views depending on the perspective one look the situation from, each any everyone has reason and evidence to support his/her theory. The positive aspects of internet censorship by the government around the world are immense.
World internet censorship ratings
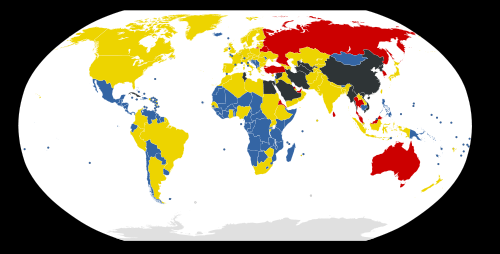
- Blue – No censorship;
- Yellow – Some censorship;
- Red – Country under surveillance from Reporters without Borders;
- Grey – Internet black holes (most heavily censored nations).
The rule makers and enforcers should work hand in hand. Their Failure to cooperate leads the rule amounting to nothing. The social contract theory was developed by the philosopher Thomas Hobbes; it argues that without rules and a systematic way of enforcing them the efforts amount to nothing. It uses the concept of cooperation between involved parties, they mutually resolve to follow laid down guidelines.
The guidelines are the rules set to benefit the people socially. All agree there should be rules laid down and the government should ensure they are enforced to all irrespective of one position. This theory was develop due to no man has authority over others naturally, hence there was need to establish contracts based on covenants. For censorship to be effective the law enforces and the designers should be one body (Eid 1).
Currently there are many unethical action been carried out, since the enforcers have absconded their duties. Regulations that govern the internet ethic are no longer being observed while the law enforces are enforcing new rules at will without consulting. Recently the government of Afghanistan censored interactive sites without even consulting. This shows there is a link between the enforcers and the law makers.
The rules are desirable if the effect s of their consequences is positive. If the consequences are negative then the rule is undesirable. The theory of rule utilitarianism was developed as a result of weaknesses in the act utilitarianism theory.
The morals theory argues that an action is morally right, if the consequences of an action results to an increase in the level of happiness. The theory uses the rules when explaining the moral values of an individual contrary to the act utilitarianism which uses the principle of utility (“Introduction to Content Filtering” 7).
It tries to exploit the fact that the rules are universally adoptable, hence result to immense happiness. Rule utilitarianism and Kantianism are similar in that they use the rule to base their argument. The difference between the two is that rule utilitarian emphasis on the action consequences while the Kantianism emphasizes on the action motive. It encourages universal adoption of an action that will increase the pleasure of the affected subjects.
In the year 2003 August, a worm by the name of blaster infected computer system using windows operating system .The worm exploited a security loophole in the windows operating system. It resulted to excess network traffic and also disabled some of the networks. The infection resulted to computer rebooting itself continually. Another worm named Nachi was developed to exploit the same loophole, but did not infect those immune to the blaster worm.
On contrary Nachi worm accessed the computer in the network to destroy blaster worm copies and also to download patches of windows to fix the loophole problem. According to the computer ethics introduction of harmful malware in a network is unethical and prohibited. According to the rule utilitarian it was morally correct since the consequences of the action increased pleasure to the affected subject.
Impact on the society
The consequences of an action do not matter. What matters are the actions themselves. The act utilitarianism theory was developed by philosophers Jeremy Bentham and John Stuart Mill.
This contradicted the earlier theory of Kantianism. It based its’ argument on the fact that an action is termed to be good if the result benefit a person and undesirable if the action harm someone. The theory was founded on the principle of utility, where the action is gauged to be right or wrong depending on the effect on the level of happiness on the concerned party.
This theory measures the morality by determining the rise or fall of happiness on the concerned party. Attitude behind an action is not relevant in this argument, what is of more concern is the consequences of the actions. Being in this context is used to refer to anything that may experiences happiness and sadness. From the definition the being not only refers to the humans but also other mammals. It is hard to measure utility thus several attribute have been selected to weigh the effect of an action on the pain and pleasure (Carter 1).
Intensity measures the experience extent, certainty measures the likelihood, and duration measures the experience length, extent measures the number of being affected, purity measures the concentration of pain or pleasure, and fecundity measures the ability replicate the experience.
Freedom without limit is always abused; most internet users do not observe the internet rules set aside to govern access of information. Almost all government censors sensitive government information or the information is not availed to the internet users.
The explicit material in the internet should be restricted to avoid underage from accessing them. Most of the Muslim dominant countries pornographic materials have been completely censored. This ensures the young ones are protected from obscene materials. The action of the government is essential to maintain a morally upright generation in censoring some materials. Due to the complex internet network the government cannot leave the censoring action to parents or private companies, it has to undertake the action itself.
The will motivating an action should be the basis of judging an action whether morally right or wrong. An action may not be moral but the motive was moral.
The Kantianism` theory was developed by a philosopher named Immanuel Kant. His argument was, people action and deeds should be based on moral laws which are universally acceptable. Citing the bible examples to support his theory, he believed for any supreme moral law to hold it must be based upon some reasoning. Someone who is a Kantian should be able to state something whether it is good or bad and qualify it using specific and varied reasoning. It entails more than arguing whether something is morally right or wrong.
The main reasoning was something may be morally right, yet it can be used wrongly to harm others or cause conflict. In this world there are barely good things without need to qualify them to be good. Only good will can be termed to be good, since there is no need to qualify it to be good. An action cannot be termed to be good simply due to the beneficial results; something good is good irrespective of the outcome from the action.
What we are meant to do is more important than what we do. We should act out of morals instilled in use rather than what we feel we should do, our moral should be the driving force upon our actions. The oppressive regime use this theory to suppress it citizen and deprive them information access. They censor interactive sites to intimidate those opposing their agenda. Late 2009 China censored interactive site especially in Tibet area. This was meant to curb growing defiance against the government
It is hard to say that the consequences of an action do not matter; what’s matter is the action itself. People are more concerned in the results not the way the results have been achieved. Kantianism theory advocate that the motive is what’s matters not he actual result of the actions. If you have a granary infested with rats, there are different ways to remedy the situation.
If you burn down the whole granary it is an option but at what cost. As much as the motive of an action is good the consequence are dire. As much as the government may have good motives and intention in censoring the internet, caution should be taken to ensure the consequences do not outweigh the gains.
The Kantianism theory should not be employed much in censoring as it may result to undesirable dire consequences. January this year the Iran government censored all interactive site, in a mission to curb government critics who were using them to sell their ideas. In addition they also banned women right websites; this caused more harm than good. It also denied the woman their rights to voice out their view; such school of thought belongs to the Stone Age where women were considered inferior.
Error analyses of filters
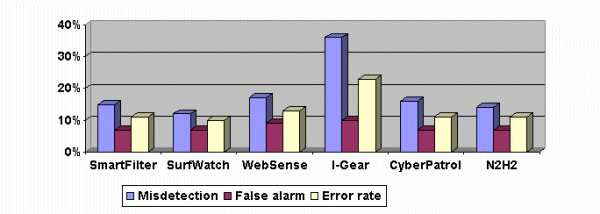
Conclusion
Government Internet censorship is not meant to suppress the society of information access, although it may result not unanticipated negative result. Every government actions to censor internet access are meant for the better of its citizen. But there are isolated cases, where the government censors internet access using unvaried bases.
This may result the country citizen being left behind in the fast growing global village. The reason for censoring internet should be clearly defined and measures put in place to protect the law from being abused. The law should also clearly define the method and modes to be used in censoring to avoid safe site from being blocked due to criterion used to block.
From the theories discussed above, it is clear from the different approaches the main objective of all is the effect of censoring to the people. They all agree if censoring result to positive effect then it is worthy but if it is harmful then it is harmful to the same people it ought to be protecting.
Irrespective of the reasons behind the censoring of the internet the result should be positive, it should not affect the people’s majority negatively. Whether it uses the rules, consequences of the action or the will motivating the action, the moral effect should be upheld at all times. Internet should be used for moral upright or justifiable action at all time. The internet ethos should be upheld and observed by all internet users indiscriminately of their position.
Error analysis of filters for the distinct data set
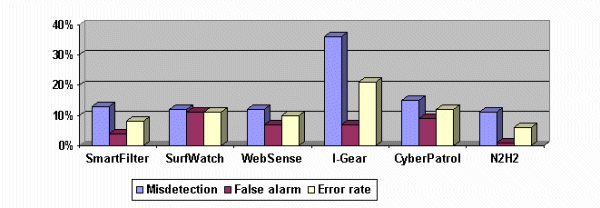
Complete censoring of the internet is contrary to the objective of having it and unhealthy to the people. The main aim of the internet is information sharing among the users and all information about any subject across the world should be accessible from anywhere in the world (Edelman 2).
Censoring result to discriminated information sharing and result to the internet falling short of its main objective. This hurt many sector in the world from business to entertainment. Although internet censoring is essential, it should be done up to a certain level where it cause more good than harm to the people.
Works Cited
Carter, Wendy. “How to write a thesis statement.” 2003. Web.
Edelman, Benjamin. “Documentation of Internet Filtering in Saudi Arabia.” 2010. Web.
Eid, Gamal. “The Internet in the Arab World A Space for Repression?” Reports and Press Releases. The Arabic Network for Human Rights Information. 2004. Web.
Garcia_Murillo, M. “Assessing the impact of Internet Telephony on the deployment of telecommunications infrastructure.” 2010. Web.
Introduction to Content Filtering. “What is this service?” 2010. Web.
Kenny, Aaron. “Inside Internet Filtering.” 2009. Web.
Kuwait. “Research profiles.” 2010. Web.
Saudi Arabia. “Research Profiles.” 2010. Web.