Introduction
Computer security is a popular term used in modern information age. The term is used persistently to address issues about safety of information systems and networks. As the use of computer networks gains much recognition in the society; there is an urgent need to address the security issues of information stored on such systems.
Computers without any security policies or measures can make a network susceptible to threats, attacks or may even disable network activities within minutes. Similarly, it may take much effort and time to recover a compromised resource.
Internet has provided more opportunities for individuals, organizations and governments. However, its simplicity of access has made it insecure for privacy, retrieval and distribution of information. Several protocols used to guarantee security on the internet have proved ineffective; hence tools to eavesdrop or “sniff” passwords on the network are often exploited by malicious hackers. Applications which broadcast unencrypted passwords across the network are equally vulnerable.
Clients and server applications depend on client and server software’s to be “truthful” on issues of user identity using their applications. Other applications depend largely on the client to limit its operations to those connected with what it is obliged to do, with limited or otherwise no enforcement by the server.
To address the above mentioned issues, Kerberos was viewed as a solution. Kerberos is a unique network security mechanism which uses cryptography. Cryptography mechanism allows a client to verify its identity to the server and vice versa over the unprotected network connection.
Kerberos
Kerberos is a modern security mechanism which is used to safeguard communications occurring over insecure network. It achieves this through proving the authenticity of nodes communicating to one another. In other words, it is a computer network authentication protocol that works using the basic of “tickets” to use computers communicating over unprotected networks to verify their uniqueness to one another in a protected mode.
Kaufman et al (1995) offers another definition of Kerberos. He asserts that Kerberos may designate a set of free software that was published by the Massachusetts Institute of Technology that implemented the Kerberos protocol. The primary objective of designing Kerberos was safeguarding client-server by providing a mutual authentication facility. That is, both the server and the node identify each other’s while communicating.
Kerberos messages are secure against replay attacks and eavesdropping. The technology is based on symmetric key cryptography and demands a trusted third-party. Correspondingly, this security mechanism may employ a public key cryptography by using asymmetric key cryptography during the process of authentication (Kaufman et al, 1995).
Kerberos uses the symmetric Needham-Schroeder protocol. It also utilizes the trusted party known as the Key Distribution Center (KDC). The KDC contains two logically distinct parts, the Ticket Granting Server (TGS), and the Authentication Server (AS). The KDC keeps a database of private keys and element on the network regardless of whether it is a node or a server.
The node and the server share the private or secret key known to the KDC and to the nodes and servers. The authenticities of this key act as proof of an element’s identity. According to Neuman and Ts’o (1994), for communications reasons, the KDC releases a session key which the parties communicating employ to encrypt the contents they are broadcasting. The security of the Kerberos protocol depends entirely on temporal assertions of validity referred to as Kerberos Tickets (Neuman and Ts’o, 1994).
Elements of Kerberos Protocol Tools
Kerberos uses different types of elements of network security to accomplish or manage authentication between the services and users. These elements are important. Without them, the objective of safeguarding network resources would be fruitless. Some of the most important elements are described below.
Client and Servers Tickets
Client and servers are the primary elements of Kerberos. According to Neuman et al (2005), the client designates a system or a person that wants to access the network or web enabled services. The server on the other hand uses the Kerberos authentication service to ascertain clients have valid access to the program or an application they wish.
Tickets are useful in the Kerberos authentication service (Neuman and Ts’o, 1994). They contain information that is essential for identifying the client to the server. Kerberos encrypt the information contained in the ticket to ensure the illegal access is not allowed.
Port
A characteristic that Kerberos tools have in all Kerberos system administration is the port. Kerberos have by default port 88.This suggests that when communication tools are developed; the passwords, log on IDs and user IDs have to communicate through this port.
If accurate combination of passwords and user IDs is verified by the authentication server, then access or log- in is granted through this port. Network administration can therefore give access to files, database, programs and emails, among other services when they link the encryption keys with this port.
Encryption
Encryption is a typical element of all Kerberos enabled tools. Encryption illustrates anything inputted by a keyboard or read on a file and translated into a coded format. The encrypted message makes it unreadable, unrecognized or unutilized by any program or person that is not permitted to do so.
A more significant feature of encryption is that no password is stored in an encrypted format. Each encryption algorithm uses a precise key length that can alter an imputed unencrypted password that is entered in an encrypted one to grant strengthened protection.
Active Directory Trusts and Domains
They are Kerberos tools available for windows server. It is a graphical interface feature that Microsoft Corporation has made it available for network administrators. It assists network administrators in viewing all trusted and domain relationships so they can enforce protection levels within these domains. The tools can be employed for all trusted and related activities such as varying and viewing trusts.
Active Directory Computers and Users
They are Microsoft management console tools which contain the administration tool pack. The administration tool pack uses the Kerberos protocol. The characteristic of Active Directory Computers and Users is that they include the ability of controlling, configuring and publishing information from the Active Directory. All administrative roles in domain controllers that need authentication are encrypted.
How Kerberos Authentication Works
Kerberos succeeds its security operations in various ways. Each activity follows one another in succession. The process of authenticating begins when a client computer makes a formal request to access or use the server. The client requests the authentication service to generate a ticket containing client credentials and sends the information to the server together with session information (Kaufman et al, 1995).
The client and Kerberos use the client information such as the password to validate the information. The Kerberos then broadcasts an encrypted ticket to the server with a password known to the server and Kerberos. Strebe (2002) notes the server validates the information to verify the source and the identity of the user.
It can also use the timestamp of the ticket to establish the validity of the request. The lifetime of a ticket lasts a few minutes; this is to ensure the process occurs in the shortest time possible for security purposes (Bellovin and Merrit, 1990). In understanding how Kerberos achieves these roles, the writer will list and describes each packet that is involved between client and application server and clients and the KDC during the process of authentication.
Stage 1
Authentication Server Request, AS_REQ
According to Neuman et al (2005) this phase is known as the initial authentication request. The client requests the KDC for a Ticket Granting Ticket. The request, in the form of a message is unencrypted.
Stage 2
Authentication Server Reply, AS_REP
When a preceding request arrives, the AS checks whether the reply contains TGT, which is encrypted with the TGS private key, and the session key encrypted with the secret key from the requesting user (Neuman et al, 2005). If one of the two keys fail to exist, an error message is posted to the client, otherwise, the AS process the reply. The processing is carried out using the following format.
- It randomly fixes a session key which acts as a secret key and shares it with the client and the TGS
- It also establishes the TGT inserting the requesting user’s principal, which is the service principal.
- Lastly, it creates and dispatches the reply that contains the ticket produced earlier and encrypted using the secret key for the service. The timestamp, lifetime, service principal and session keys are encrypted using the secret key labeled for the user invoking the service.
Stage 3
Ticket Granting Server Reply, TGS_REP
At this stage, the user who is authentic, and wants to access the service in context but does not have a valid ticket, sends a request as the Ticket Granting Server replies to the Ticket Granting Service (Neuman et al, 2005). The Ticket Granting Service model is as explained below;
- It fixes an authenticator with the client machine, user principal, and timestamp and encrypts with the session key common with the TGS.
- It also establishes a request packet that contains; the Ticket Granting Ticket, which is already encrypted with the key of the Ticket Granting Service; the service principal which the ticket is needed and lifetime unencrypted; and the authenticator.
When the previous requests arrive, the TGS’ initial step is to verify the principal of the requested service is present in the KDC database. If present, it opens the TGT by using the key and extracts the session key. It uses the key to decrypt the authenticator. To achieve service ticket, the following criterion has to be met.
- The TGT should not have expired.
- The principal contained in the authenticator should match the one available in the TGT.
- The authenticator should be available in the replay cache and should not have been expired.
Stage 4
Application Request, AP_REQ
When the client has credentials to access the service, that is the session key and the ticket, it can request the application server for a right of entry to network resources through the Application Request message. It should be noted that unlike other messages where the KDC is involved, the Application Request is not standard. It varies based on the application in context.
Stage 5
Pre-Authentication
As represented in Authentication Server Reply, before distributing a ticket, the KDC verifies the principal of the asking service provider and others are available in the database (Strebe, 2002). If the request is from an illegal user, TGT cannot be invoked because of the password, thus it is difficult to release a session key for creating a legitimate authenticator.
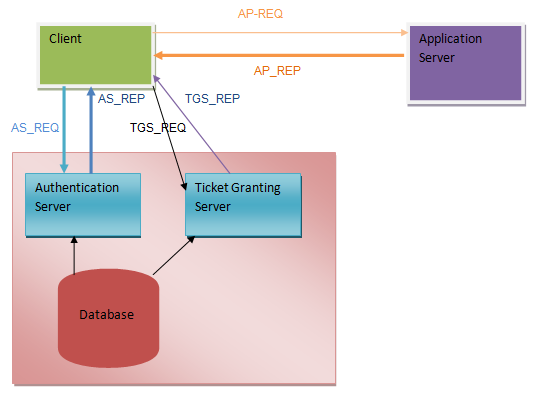
Kerberos Operation (Author, 2011)
Protecting Application Data
As explained earlier, Kerberos provides the services of authentication only; an assurance the authenticated element is a dynamic partaker in an exchange. According to Jablon (1996) a derivative of Kerberos authentication protocol is the swap of the session key between the client and the server (Tanenbaum, 2003).
The session key may consequently be used by a program or an application to provide privacy and integrity of communication. The Kerberos describes two types of messages, private and safe messages to summarize data that need to be protected (Strebe, 2002). However, the application is at liberty to use a suitable method to a particular data being relayed.
Success of Kerberos
Kerberos has achieved notable success in network security issues. This is in contrast with other similar security tools providing security services.
Password protection
Kerberos does not allow a user’s password to be sent across the network either under encryption or in plain text. Rather, the protocol depends on keys that are transmitted through encryption. Hence the keys cannot be intercepted (Jablon, 1996). For example, when the security of the network is tampered, Kerberos makes it likely for trespassers to construe the content of network transmissions. Similarly, target services and user authentications remain safe.
Client/Server Authentication
Kerberos allows the client and server to authenticate to each other. Communication can break or fail if they are not able to authenticate.
Client/Server Ticket Certification
Kerberos timestamps the tickets that pass from the server to client and from client to server, it also encompasses lifetime information besides common authentication. Hence the period of authentication is restricted (Bellovin and Merrit, 1990). The time spent by the user during implementation may be altered by design but the limit is less to ensure that replay attacks are not contained. By limiting time, the strategy makes communication secure.
Reusability and Durability
Kerberos protocol authentication is reusable and durable. When a user authenticates using the Kerberos protocol, the authentication can be reused during the lifetime of the ticket. This is to imply that it is feasible to remain valid through the protocol without re-entering a username and password over the network.
Session Key Generation
The Kerberos protocol uses a dual key encryption method. The product of the service session key provides a unique link between the client and the service that is safe. This unique “secret” link is used as the encryption key during client/server communication (Bellovin and Merrit, 1990). This adds security to Kerberos communication.
Internet Standard
The Kerberos protocol depends on the open internet platform. It is not restricted to authentication mechanisms or proprietary codes. This enables developers to depend on open and free reference implementation of a public method. Similarly, inexpensive commercial implementations can be developed separately or bought.
Ubiquity
Kerberos is widely embraced and trusted by security experts, developers and cryptologists. Hence, new breaches are likely to be noted and resolved instantaneously. This is in contrast with proprietary systems. Kerberos has substantial investments hence its security mechanism is difficult to overcome. Besides, the strength of Kerberos is anchored on numbers.
Failures of Kerberos Protocol
Though Kerberos cancels or guards against severe and common security threats, it may be challenging to implement. This is because of various reasons:
Knowledge in Implementation
According to Bellovin and Merrit (1990) Kerberos protocol was developed to be used for a single user client system. In cases where a client acts as a multi user system, the Kerberos authentication mechanism may be compromised to various replay attacks and ticket stealing.
The general protection of a multi user client system such as memory protection, file system protection among others maybe a restricting reason of Kerberos authentication (Bellovin and Merrit, 1990). No knowledge or cleverness in implementing a Kerberos authentication can substitute system administration practices Kerberos server and client systems.
Support of Proprietary Software
Kerberos utilizes mutual authentication model. It is important for client and servers to be deliberated with Kerberos authentication. Some proprietary applications also support Kerberos. Besides, various legacy systems were deliberated and maintained programs. However, they were not designed with third party authentication tools in mind (Kohl et al, 1994). This means that they need to be rewritten to embrace Kerberos authentication.
Server Attacks
The Kerberos authentication method is susceptible to severe attacks against ticket granting service and the initial ticketing service, KDC. The whole authentication mechanism depends on the “faithfulness” of the KDC (Kohl et al, 1994). Hence any person who can compromise authenticating users can compromise the authentication of users of the system depending on the KDC. Thus, this needs efficient system administration practices while managing the Kerberos KDC.
All Nothing Strategy
Kerberos can be an all nothing strategy when utilized in a network. An encrypted password communicated over the network to a non-Kerberos enabled aware the service is in danger. Hence, the networks accrue no benefit from using Kerberos. To make a network secure with Kerberos, a person must use Kerberos enabled version on all clients and server applications that communicates the passwords unencrypted.
Conclusion
The Kerberos protocol provides the needed security to protect communications occurring over a network. Without its strength, computer networks would be at risk against threats and attacks.
Precisely, without the facts of the identity of an element or individual identity requesting an operation, it is challenging to make a decision whether an operation should be denied or granted. Kerberos achieves network security by using shared key cryptography. This makes both the client and server access the same password or key to positively recognize the user.
Perhaps, this strength of the Kerberos helps to manage passwords for many users by granting services that assist in coordinating passwords between the services and the users they desire to use. The conventional authentication strategies are not a guarantee for use on networks where attackers can easily check network traffic and seize passwords. Kerberos uses strong authentication approach that does not divulge passwords, hence supporting network security.
References
Bellovin, S., M., & Merritt, M., 1990, Limitations of the Kerberos Authentication system. Computer Communication Review 20(5), pp. 119-132.
Jablon, D., 1996, Strong Password-only Authenticated Key Exchange. Computer Communication Review 26(5), pp. 5-26.
Kaufman, C., Perlman, R., & Speciner, M., 1995, Network Security: Private Communication in a Public World, Prentice-Hall, New Jersey.
Kohl, J., T., Neuman, B., C., & Ts’o, T., 1994, “The Evolution of the Kerberos Authentication System”. Distributed Open Systems. IEEE Computer Society Press. Washington.
Neuman, B., C., & Ts’o, T., 1994. “Kerberos: An Authentication Service for Computer Networks”. IEEE Communications, 32(9), pp. 33–81.
Neuman, B., C., Yu, T., Hartman, S., & Raeburn, K., 2005, The Kerberos Network Authentication Service (V5). Available at; https://www.ietf.org/
Strebe, M., 2002, Network Security Jump-Start: Computer and Network Security Basics. John Wiley and Sons, New Jersey.
Tanenbaum, A., S., 2003, Computer Networks, Prentice Hall PTR, New Jersey.